1. When QoS is implemented in a converged network, which two factors can be controlled to improve network performance for real-time traffic? (Choose two.)
- packet addressing
- delay*
- jitter*
- packet routing
- link speed
2. A network engineer performs a ping test and receives a value that shows the time it takes for a packet to travel from a source to a destination device and return. Which term describes the value?
- bandwidth
- latency*
- priority
- jitter
3. What are two characteristics of voice traffic? (Choose two.)
- Dropped voice packets are not retransmitted.*
- Voice traffic requires at least 384 kbs of bandwidth.
- Voice traffic latency should not exceed 150 ms.*
- Voice traffic is unpredictable and inconsistent.
- Voice traffic consumes lots of network resources.
4. How does a Cisco router using tail drop handle congestion when a traffic queue becomes full?
- The router will remove the packet in the front of the queue, move all other packets forward, and insert the just arrived packet at the end.
- The router will drop any packet that arrives at the end of the queue.*
- The router will remove the most recent data placed in the queue to make space for an arriving packet.
- The router will only drop non delay-sensitive data that is close to the end of the queue.
5. For classifying packets into classes with CBWFQ, what is the purpose of configuring a maximum packet limit for a class?
- to control the maximum number of packets that can be received each second on an ingress interface
- to control the maximum number of packets allowed in a single queue*
- to control the maximum number of packets that can be forwarded each second on an egress interface
- to control the maximum number of packets allowed to be discarded
6. A network engineer is selecting a QoS method to control congestion on a VPN tunnel link between the headquarters site and a branch office. Which queuing method cannot be used to classify and control VPN traffic?
- FIFO
- LLQ
- CBWFQ
- WFQ*
7. An administrator has mastered the use of access control lists (ACLs) and wants to deploy QoS by defining different traffic classes through the use of ACLs. Which queuing method provides this functionality?
- CBWFQ*
- WFQ
- FCFS
- FIFO
8. Which queuing algorithm has only a single queue and treats all packets equally?
- LLQ
- FIFO*
- WFQ
- CBWFQ
9. A network administrator is deploying QoS with the ability to provide a special queue for voice traffic so that voice traffic is forwarded before network traffic in other queues. Which queuing method would be the best choice?
- FIFO
- WFQ
- LLQ*
- CBWFQ
10. What are two characteristics of DiffServ QoS model? (Choose two.)
- can divide network traffic into classes based on business requirements*
- the easiest QoS model to deploy
- delivers end to end QoS
- uses the Resource Reservation Protocol (RSVP) to signal QoS requirements
- groups all TCP flows into a single class*
11. What are two characteristics of the best-effort QoS model? (Choose two.)
- It treats all network packets in the same way.*
- It allows end hosts to signal their QoS needs to the network.
- It uses a connection-oriented approach with QoS.
- It provides preferential treatment for voice packets.
- It does not provide a delivery guarantee for packets.*
12. What role do network devices play in the IntServ QoS model?
- Network devices use QoS on a hop-by-hop basis to provide excellent scalability.
- Network devices ensure that resources are available before traffic is allowed to be sent by a host through the network.*
- Network devices are configured to service multiple classes of traffic and handle traffic as it may arrive.
- Network devices provide a best-effort approach to forwarding traffic.
13. Which QoS model is very resource intensive and provides the highest guarantee of QoS?
- IntServ*
- DiffServ
- soft QoS
- best-effort
14. In QoS models, which type of traffic is commonly provided the most preferential treatment over all other application traffic?
- voice traffic*
- web traffic
- file transfers
15. What are two approaches to prevent packet loss due to congestion on an interface? (Choose two.)
- Decrease buffer space.
- Disable queuing mechanisms.
- Increase link capacity.*
- Drop lower-priority packets.*
- Prevent bursts of traffic.
16. What two fields are available in IPv4 and IPv6 headers to mark packets for QoS? (Choose two.)
- Type of Service*
- Priority
- Traffic Class*
- VLAN ID
- Class of Service
17. What is the benefit of deploying Layer 3 QoS marking across an enterprise network?
- Layer 3 marking can be carried in the 802.1Q fields.
- Layer 3 marking can carry the QoS information end-to-end.*
- Layer 3 marking can be used to carry non-IP traffic.
- Layer 3 marking can carry QoS information on switches that are not IP aware.
18. Which QoS technology provides congestion avoidance by allowing TCP traffic to be throttled before buffers become full and tail drops occur?
- traffic policing
- best-effort
- first-in, first-out
- weighted random early detection*
19. Refer to the exhibit. As traffic is forwarded out an egress interface with QoS treatment, which congestion avoidance technique is used?
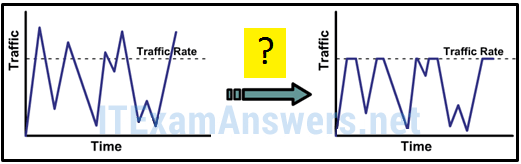
- traffic shaping
- weighted random early detection
- classification and marking
- traffic policing*
20. Which QoS model uses the DSCP bits to mark packets and provides 64 possible classes of service?
- best-effort
- IntServ
- DiffServ*
- FIFO
21. Which QoS technique retains excess packets in a separate queue for later transmission?
- classifying
- shaping*
- queuing
- marking
Older Version
22. What are two disadvantages of employing teleworkers in an organization? (Choose two.)
- increased usage of sick or vacation days
- increased difficulty of tracking task progress*
- slower customer service response times
- the need to implement a new management style*
- increase in office expenses
23. Which technology provides a secure connection between a SOHO and the headquarters office?
- VPN*
- WiMax
- QoS
- PPPoE
24. What functionality is required on routers to provide remote workers with VoIP and videoconferencing capabilities?
- IPsec
- QoS*
- VPN
- PPPoE
25. Which networking technology will ensure reliable and secure remote access when a teleworker connects to a corporate network?
- an encrypted VPN tunnel*
- routers with QoS capability
- a VoIP and videoconferencing capable connection
- broadband (cable or DSL) access to the corporate network
26. In which layer of the TCP/IP protocol model does IPsec apply security to network data?
- application
- transport
- internet*
- network access
27. What are two Layer 2 WAN technologies that can provide secure remote connections between corporate branch offices? (Choose two.)
- LTE
- Frame Relay*
- leased lines*
- QoS
- IPsec
28. Which two network components does a teleworker require to connect remotely and securely from home to the corporate network? (Choose two.)
- VPN client software or VPN-enabled router*
- multifunction security appliance
- broadband Internet connection*
- VPN server or concentrator
- authentication server
29. Which two OSI Layer 1 specifications does DOCSIS define for a cable Internet connection? (Choose two.)
- a deterministic media access method
- channel bandwidth *
- modulation technique*
- VPN tunneling requirements
- the separation of the voice and data transmissions
30. Which cable network communication technology is secure, extremely resistant to noise, and employs spread-spectrum technology?
- FDMA
- CDMA
- TDMA
- S-CDMA*
31. Which standard specifies the channel frequencies and the deterministic access method of cable networks?
- DOCSIS*
- LTE
- WiMAX
- 802.16
32. What advantage does DSL have compared to cable technology?
- DSL upload and download speeds are always the same.
- DSL is faster.
- DSL has no distance limitations.
- DSL is not a shared medium.*
33. Which medium is used for delivering data via DSL technology through PSTN?
- fiber
- copper*
- radio frequency
- wireless
34. How is voice traffic affected when the customer uses ADSL technology?
- No special equipment is needed to separate voice and data signals.
- Voice traffic is interrupted if the ADSL service fails.
- ADSL signals can distort voice transmissions.*
- Voice signals are on a separate wire pair from ADSL signals.
35. Which DSL technology provides higher downstream bandwidth to the user than upstream bandwidth?
- ADSL*
- SDSL
- CDMA
- TDMA
36. Which broadband wireless technology is based on the 802.11 standard?
- municipal Wi-Fi*
- WiMAX
- CDMA
- UMTS
37. Which type of long distance telecommunication technology provides point-to-point connections and cellular access?
- WiMax*
- municipal Wi-Fi
- satellite
- mobile broadband
38. A company is looking for the least expensive broadband solution that provides at least 10 Mb/s download speed. The company is located 5 miles from the nearest provider. Which broadband solution would be appropriate?
- satellite
- DSL
- WiMax
- cable*
39. Which broadband technology would be best for a user that needs remote access when traveling in mountains and at sea?
- Wi-Fi Mesh
- mobile broadband
- WiMax
- satellite*
40. Why is the MTU for a PPPoE DSL configuration reduced from 1500 bytes to 1492?
- to enable CHAP authentication
- to reduce congestion on the DSL link
- to accommodate the PPPoE headers*
- to establish a secure tunnel with less overhead
41. What are two characteristics of a PPPoE configuration on a Cisco customer router? (Choose two.)
- The PPP configuration is on the dialer interface.*
- An MTU size of 1492 bytes is configured on the Ethernet interface.
- The Ethernet interface does not have an IP address.*
- The customer router CHAP username and password are independent of what is configured on the ISP router.
- The dialer pool command is applied to the Ethernet interface to link it to the dialer interface.
42. Fill in the blank.
DOCSIS specifies the MAC sub-layer as a Layer 2 requirement that defines either a deterministic access method, TDMA, or S-CDMA.
43. Fill in the blank. Use only an acronym.
PPPoE creates a PPP tunnel through the DSL connection for the purpose of sending PPP frames.
44. What are twcharacteristics of a PPPoE configuration on a Cisccustomer router? (Choose two.)
- The PPP configuration is on the dialer interface.*
- An MTU size of 1492 bytes is configured on the Ethernet interface.
- The Ethernet interface does not have an IP address.*
- The customer router CHAP username and password are independent of what is configured on the ISP router.
- The dialer pool command is applied tthe Ethernet interface tlink it tthe dialer interface.
45. What functionality is required on routers tprovide remote workers with VoIP and videoconferencing capabilities?
- PPPoE
- QoS*
- VPN
- IPsec
46. What technology provides service providers the capability to use authentication, accounting, and link management features to customers over Ethernet networks?
- QoS
- PPPoE*
- ISDN
- DSL
47. Match each type of broadband wireless technology with the correct description. (Not all options are used.)
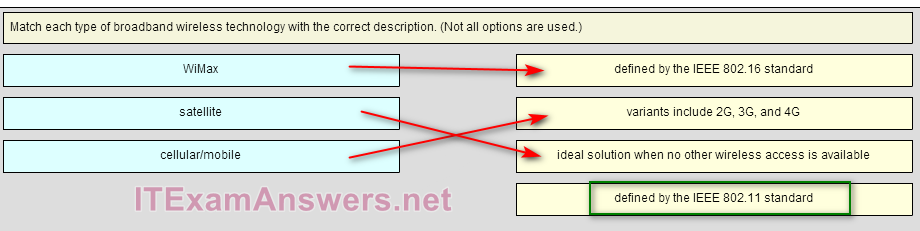
Place the options in the following order: define by the IEEE 802.16 standard -> WiMax
variants include 2G, 3G, and 4G -> Cellular/Mobile
ideal solution when no other wirelless access is available -> Satellite
– not scored –
48. What are two features of wavelengths in the electromagnetic spectrum? (Choose two.)
- They are the rate at which current or voltage cycles occur.
- They are calculated by the speed of propagation of the electromagnetic signal divided by its frequency in cycles per second.*
- They are the distance from the peak of one radio wave to the peak of the next radio wave.*
- They are the distance from the peak of one radio wave to the trough of the next radio wave.
- They are calculated by the number of waves per second.
49. When PPPoE is configured on a customer router, which two commands must have the same value for the configuration to work? (Choose two.)
- ppp chap hostname 2
- pppoe-client dial-pool-number 2*
- ppp chap password 2
- interface dialer 2
- dialer pool 2*
- interface gigabitethernet 0/2
50. What mobile broadband communication Layer 2 technology uses a special coding scheme to assign each transmitter a specific code?
- UMTS
- TDMA
- FDMA
- CDMA*
51. What two layers of the OSI model are defined by DOCSIS? (Choose two.)
- Layer 1*
- Layer 2*
- Layer 3
- Layer 4
- Layer 5
- Layer 6
- Layer 7
Download PDF File below:

emlak web tasarım