New Version:
1. The buffers for packet processing and the running configuration file are temporarily stored in which type of router memory?
- flash
- NVRAM
- RAM
- ROM
2. Refer to the exhibit. A company has an internal network of 192.168.10.0/24 for their employee workstations and a DMZ network of 192.168.3.0/24 to host servers. The company uses NAT when inside hosts connect to outside network. A network administrator issues the show ip nat translations command to check the NAT configurations. Which one of source IPv4 addresses is translated by R1 with PAT
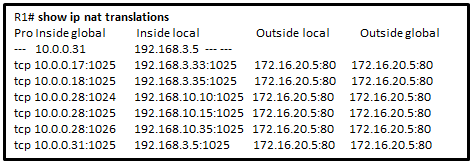
- 10.0.0.31
- 192.168.3.5
- 192.168.3.33
- 192.168.10.35
- 172.16.20.5
3. Refer to the exhibit. This network has two connections to the ISP, one via router C and one via router B. The serial link between router A and router C supports EIGRP and is the primary link to the Internet. If the primary link fails, the administrator needs a floating static route that avoids recursive route lookups and any potential next-hop issues caused by the multiaccess nature of the Ethernet segment with router B. What should the administrator configure?
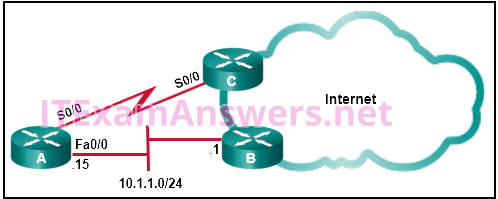
- Create a static route pointing to Fa0/0 with an AD of 1.
- Create a static route pointing to 10.1.1.1 with an AD of 95.
- Create a static route pointing to 10.1.1.1 with an AD of 1.
- Create a fully specified static route pointing to Fa0/0 with an AD of 1.
- Create a fully specified static route pointing to Fa0/0 with an AD of 95.
4. Which type of inter-VLAN communication design requires the configuration of multiple subinterfaces?
- legacy inter-VLAN routing
- routing for the management VLAN
- router on a stick
- routing via a multilayer switch
5. After sticky learning of MAC addresses is enabled, what action is needed to prevent dynamically learned MAC addresses from being lost in the event that an associated interface goes down?
- Reboot the switch.
- Copy the running configuration to the startup configuration.
- Shut down the interface then enable it again with the no shutdown command.
- Configure port security for violation protect mode.
6. A network technician is configuring port security on switches. The interfaces on the switches are configured in such a way that when a violation occurs, packets with unknown source addresses are dropped and no notification is sent. Which violation mode is configured on the interfaces?
- off
- restrict
- protect
- shutdown
7. A technician is configuring a switch to allow access both to IP phones and to PCs on interface Fa0/12. The technician enters the interface command mls qos trust cos. What is the reason for including that command?
- It is used in conjuction with STP PortFast to ensure that interface Fa0/12, in case of a shutdown, regains an “up” state immediately.
- It is used to verify service levels and to ensure that congestion over serial interfaces is minimized for voice traffic.
- It is used to set the trusted state of an interface to allow classification of traffic for QoS based on the CoS value of the IP phone.
- It is used to provide higher categories of security for voice and video traffic.
8. What is the minimum configuration for a router interface that is participating in IPv6 routing?
- to have only a link-local IPv6 address
- to have both a link-local and a global unicast IPv6 address
- to have both an IPv4 and an IPv6 address
- to have a self-generated loopback address
- to have only an automatically generated multicast IPv6 address
9. Refer to the exhibit. Assuming that the routing tables are up to date and no ARP messages are needed, after a packet leaves H1, how many times is the L2 header rewritten in the path to H2?
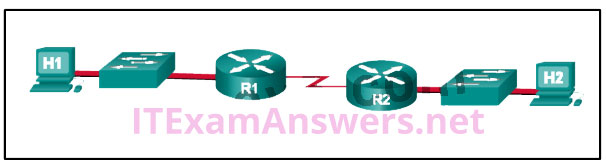
- 1
- 2
- 3
- 4
- 5
- 6
10. What command will enable a router to begin sending messages that allow it to configure a link-local address without using an IPv6 DHCP server?
- a static route
- the ipv6 route ::/0 command
- the ipv6 unicast-routing command
- the ip routing command
11. Which switching method provides error-free data transmission?
- fragment-free
- fast-forward
- integrity-checking
- store-and-forward
12. Which problem is evident if the show ip interface command shows that the interface is down and the line protocol is down?
- A cable has not been attached to the port.
- There is an IP address conflict with the configured address on the interface.
- The no shutdown command has not been issued on the interface.
- An encapsulation mismatch has occurred.
13. A company security policy requires that all MAC addressing be dynamically learned and added to both the MAC address table and the running configuration on each switch. Which port security configuration will accomplish this?
- auto secure MAC addresses
- dynamic secure MAC addresses
- static secure MAC addresses
- sticky secure MAC addresses
14. Refer to the exhibit. A small business uses VLANs 8, 20, 25, and 30 on two switches that have a trunk link between them. What native VLAN should be used on the trunk if Cisco best practices are being implemented?
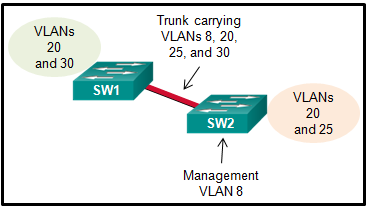
- 1
- 5
- 8
- 20
- 25
- 30
15. A network administrator is configuring an ACL with the command access-list 10 permit 172.16.32.0 0.0.15.255. Which IPv4 address matches the ACE?
- 172.16.20.2
- 172.16.26.254
- 172.16.45.2
- 172.16.48.5
16. The PT initialization was skipped. You will not be able to view the PT activity.
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which code is displayed on the web browser?
- Inter-VLANonfigured!
- It works!
- Welldone!
- Grea
17. Which command is issued in the VTY line configuration mode to apply a standard ACL that will control Telnet access to a router?
- access-group 11 in
- access-class 11 in
- access-list 11 in
- access-list 110 in
18. Which series of commands will cause access list 15 to restrict Telnet access on a router?
- R1(config)# line vty 0 4
R1(config-line)# ip access-group 15 in - R1(config)# int gi0/0
R1(config-if)# ip access-group 15 in - R1(config)# line vty 0 4
R1(config-line)# access-class 15 in - R1(config)# int gi0/0
R1(config-if)# access-class 15 in
19. Which three statements accurately describe VLAN types? (Choose three).
- A management VLAN is any VLAN that is configured to access management features of the switch.
- A data VLAN is used to carry VLAN management data and user-generated traffic.
- Voice VLANs are used to support user phone and e-mail traffic on a network.
- VLAN 1 is always used as the management VLAN.
- After the initial boot of an unconfigured switch, all ports are members of the default VLAN.
- An 802.1Q trunk port, with a native VLAN assigned, supports both tagged and untagged traffic.
20. A client is using SLAAC to obtain an IPv6 address for its interface. After an address has been generated and applied to the interface, what must the client do before it can begin to use this IPv6 address?
- It must send a DHCPv6 INFORMATION-REQUEST message to request the address of the DNS server.
- It must send an ICMPv6 Router Solicitation message to determine what default gateway it should use.
- It must send a DHCPv6 REQUEST message to the DHCPv6 server to request permission to use this address.
- It must send an ICMPv6 Neighbor Solicitation message to ensure that the address is not already in use on the network.
21. Which DHCP IPv4 message contains the following information?
Destination address: 255.255.255.255
Client IPv4 address: 0.0.0.0
Default gateway address: 0.0.0.0
Subnet mask: 0.0.0.0
- DHCPACK
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
22. A network administrator is implementing DHCPv6 for the company. The administrator configures a router to send RA messages with M flag as 1 by using the interface command ipv6 nd managed-config-flag. What effect will this configuration have on the operation of the clients?
- Clients must use the information that is contained in RA messages.
- Clients must use all configuration information that is provided by a DHCPv6 server.
- Clients must use the prefix and prefix length that are provided by RA messages and obtain additional information from a DHCPv6 server.
- Clients must use the prefix and prefix length that are provided by a DHCPv6 server and generate a random interface ID.
23. Refer to the exhibit. The users on the LAN network of R1 cannot receive an IPv6 address from the configured stateful DHCPv6 server. What is missing from the stateful DHCPv6 configuration on router R1?
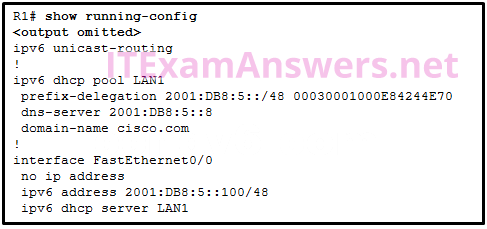
- The FA0/0 interface is missing the command that informs the clients to use stateful DHCPv6.
- IPv6 has not been enabled globally on router R1.
- The DHCPv6 pool has not been bound to the LAN interface.
- The DHCPv6 pool does not match the IPv6 address configured on interface FA0/0.
24. Refer to the exhibit. NAT is configured on R1 and R2. The PC is sending a request to the web server. What IPv4 address is the source IP address in the packet between R2 and the web server?
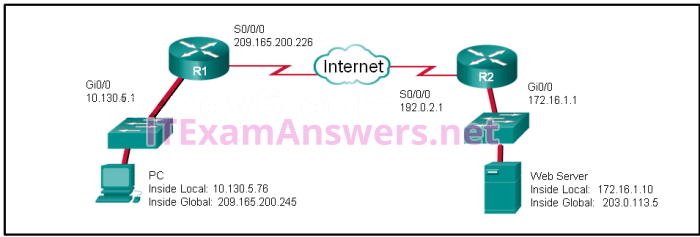
- 10.130.5.76
- 209.165.200.245
- 172.16.1.10
- 203.0.113.5
- 192.0.2.1
- 172.16.1.1
25. Refer to the exhibit. R1 is configured for NAT as displayed. What is wrong with the configuration?
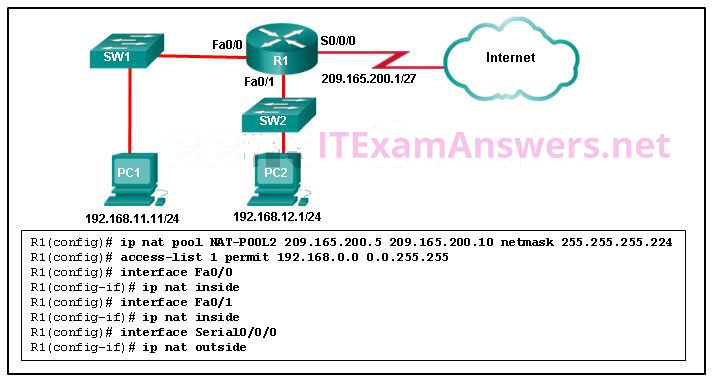
- NAT-POOL2 is not bound to ACL 1.
- Interface Fa0/0 should be identified as an outside NAT interface.
- The NAT pool is incorrect.
- Access-list 1 is misconfigured.
26. A network engineer is configuring PAT on a router and has issued the command:
ip nat source list 1 interface serial 0/1/0 overload
Which additional command is required to specify addresses from the 192.168.128.0/18 network as the inside local addresses?
- ip nat inside source list 1 pool INSIDE_NAT_POOL
- access-list 1 permit 192.168.128.0 0.0.127.255
- access-list 1 permit 192.168.128.0 255.255.192.0
- access-list 1 permit 192.168.128.0 0.0.63.255
- ip nat inside source static 192.168.128.0 209.165.200.254
27. Refer to the exhibit. If the IP addresses of the default gateway router and the DNS server are correct, what is the configuration problem?
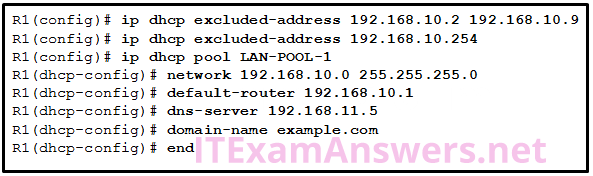
- The DNS server and the default gateway router should be in the same subnet.
- The IP address of the default gateway router is not contained in the excluded address list.
- The default-router and dns-server commands need to be configured with subnet masks.
- The IP address of the DNS server is not contained in the excluded address list.
28. Fill in the blank.
In IPv6, all routes are level ___ ultimate routes.Correct Answer: 1*
29. Fill in the blank.
The acronym ___ describes the type of traffic that requires a separate VLAN, strict QoS requirements, and a one-way overall delay less than 150 ms across the network. These restrictions help to ensure traffic quality.Correct Answer: voip*
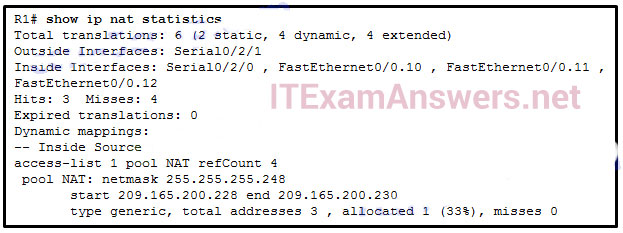
30. Refer to the exhibit. A network administrator has just configured address translation and is verifying the configuration. What three things can the administrator verify? (Choose three.)
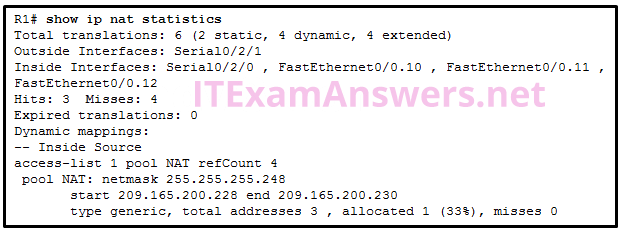
- Address translation is working.
- Three addresses from the NAT pool are being used by hosts.
- The name of the NAT pool is refCount.
- A standard access list numbered 1 was used as part of the configuration process.
- Two types of NAT are enabled.
- One port on the router is not participating in the address translation.
31. Which destination do Cisco routers and switches use by default when sending syslog messages for all severity levels?
- NVRAM
- nearest syslog server
- console
- RAM
32. Which requirement should be checked before a network administrator performs an IOS image upgrade on a router?
- The desired IOS image file has been downloaded to the router.
- There is sufficient space in flash memory.
- The old IOS image file has been deleted.
- The FTP server is operational.
33. A network administrator configures a router with the command sequence:
R1(config)# boot system tftp://c1900-universalk9-mz.SPA.152-4.M3.bin R1(config)# boot system rom
What is the effect of the command sequence?
- The router will load IOS from the TFTP server. If the image fails to load, it will load the IOS image from ROM.
- The router will search and load a valid IOS image in the sequence of flash, TFTP, and ROM.
- The router will copy the IOS image from the TFTP server and then reboot the system.
- On next reboot, the router will load the IOS image from ROM.
34. Which three software packages are available for Cisco IOS Release 15.0?
- Unified Communications
- DATA
- Enterprise Services
- Advanced IP Services
- IPVoice
- Security
35. What two license states would be expected on a new Cisco router once the license has been activated? (Choose two.)
- License State: Active, In Use
- License State: Active, Registered
- License Type: ipbasek9
- License Type: Temporary
- License State: On
- License Type: Permanent
36. Which type of static route typically uses the distance parameter in the ip route global configuration command?
- summary static route
- default static route
- floating static route
- standard static route
37. Refer to the exhibit. Which type of IPv6 static route is configured in the exhibit?
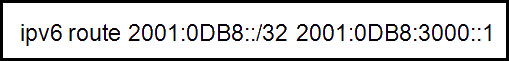
- fully specified static route
- recursive static route
- directly attached static route
- floating static route
38. Refer to the exhibit. Which route was configured as a static route to a specific network using the next-hop address?
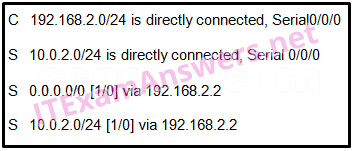
- C 192.168.2.0/24 is directly connected, Serial0/0/0
- S 0.0.0.0/0 [1/0] via 192.168.2.2
- S 10.0.2.0/24 [1/0] via 192.168.2.2
- S 10.0.2.0/24 is directly connected, Serial 0/0/0
39. A network administrator has entered the following command:
ip route 192.168.10.64 255.255.255.192 serial0/0/1
When the network administrator enters the command show ip route, the route is not in the routing table. What should the administrator do next?
- Re-enter the command using a network number rather than a usable IP address.
- Verify that the serial 0/0/1 interface is active and available.
- Re-enter the command using the correct mask.
- Verify that the 192.168.10.64 network is active within the network infrastructure.
40. Refer to the exhibit. How did the router obtain the last route that is shown?
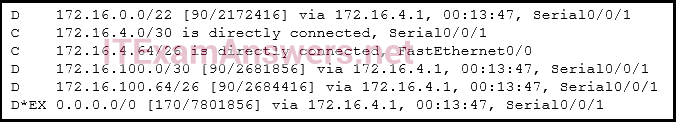
- The ip route command was used.
- The ipv6 route command was used.
- Another router in the same organization provided the default route by using a dynamic routing protocol.
- The ip address interface configuration mode command was used in addition to the network routing protocol configuration mode command.
41. To enable RIP routing for a specific subnet, the configuration command network 192.168.5.64 was entered by the network administrator. What address, if any, appears in the running configuration file to identify this network?
- 192.168.5.64
- 192.168.5.0
- 192.168.0.0
- No address is displayed.
42. Refer to the exhibit. What is the administrative distance value that indicates the route for R2 to reach the 10.10.0.0/16 network?
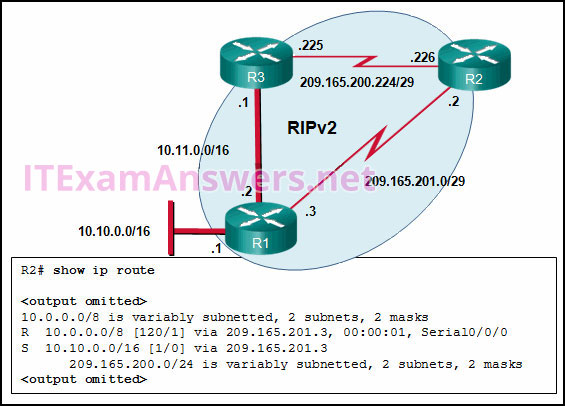
- 1
- 120
- 0
- 2
43. Refer to the exhibit. Which type of route is 172.16.0.0/16?
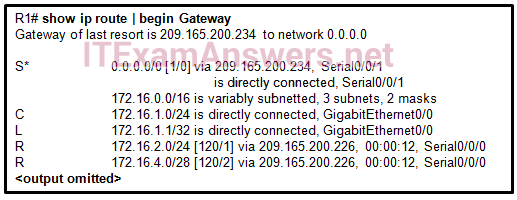
- ultimate route
- level 1 parent route
- child route
- default route
44. What is the name of the layer in the Cisco borderless switched network design that would have more switches deployed than other layers in the network design of a large organization?
- data link
- core
- network access
- access
- network
45. What is a function of the distribution layer?
- high-speed backbone connectivity
- interconnection of large-scale networks in wiring closets
- network access to the user
- fault isolation
46. Which network design principle focuses on the capability of on-demand seamless network expansion in a switched network?
- flexibility
- modularity
- resiliency
- hierarchical
47. A lab in a network management software company is configuring a testing environment to verify the performance of new software with different network connectivity speeds, including FastEthernet, GigabitEthernet, and 10 GigabitEthernet, and with copper and fiber optic connections. Which type of switch should the software company purchase to perform the tests?
- fixed configuration
- access layer
- modular configuration
- stackable
48. What two license conditions would be expected on a new Cisco router once the license has been activated? (Choose two.)
- License Type: Permanent
- License Type: ipbasek9
- License Type: Temporary
- License State: On
- License State: Active, In Use
- License State: Active, Registered
49. In an IPv6 routing table, all routing table entries are classified as which type of routes?
- level 2 child routes
- level 1 parent routes
- level 1 ultimate routes
- level 1 network routes
50. Which type of traffic requires a separate VLAN, strict QoS requirements, and a one-way overall delay of less than 150 ms across the network?
- video
- POP/IMAP
- HTTP
- VoIP
51. What information is added to the switch table from incoming frames?
- destination MAC address and incoming port number
- destination IP address and incoming port number
- source MAC address and incoming port number
- source IP address and incoming port number
52. Which statement correctly describes how a LAN switch forwards frames that it receives?
- Cut-through frame forwarding ensures that invalid frames are always dropped.
- Only frames with a broadcast destination address are forwarded out all active switch ports.
- Frame forwarding decisions are based on MAC address and port mappings in the CAM table.
- Unicast frames are always forwarded regardless of the destination MAC address.
Older Version
53. How will a router handle static routing differently if Cisco Express Forwarding is disabled?
- It will not perform recursive lookups.
- Serial point-to-point interfaces will require fully specified static routes to avoid routing inconsistencies.
- Ethernet multiaccess interfaces will require fully specified static routes to avoid routing inconsistencies.
- Static routes that use an exit interface will be unnecessary.
54. Refer to the exhibit. R1 was configured with the static route command ip route 209.165.200.224 255.255.255.224 S0/0/0 and consequently users on network 172.16.0.0/16 are unable to reach resources on the Internet. How should this static route be changed to allow user traffic from the LAN to reach the Internet?
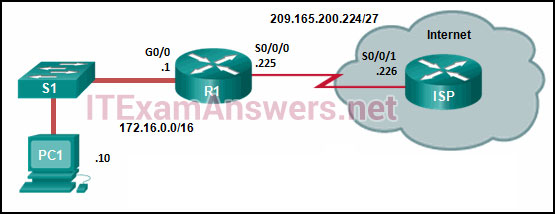
- Add the next-hop neighbor address of 209.165.200.226.
- Change the exit interface to S0/0/1.
- Change the destination network and mask to 0.0.0.0 0.0.0.0.
- Add an administrative distance of 254
55. In a routing table which route can never be an ultimate route?
- parent route
- child route
- level one route
- level two route
56. Refer to the exhibit. In the routing table entry, what is the administrative distance?
![]()
- 24
- 120
- 2
- 12
57. How many classful networks are summarized by the static summary route ip route 192.168.32.0 255.255.248.0 S0/0/0?
- 2
- 4
- 8
- 16
58. Refer to the exhibit. An administrator is trying to configure PAT on R1, but PC-A is unable to access the Internet. The administrator tries to ping a server on the Internet from PC-A and collects the debugs that are shown in the exhibit. Based on this output, what is most likely the cause of the problem?
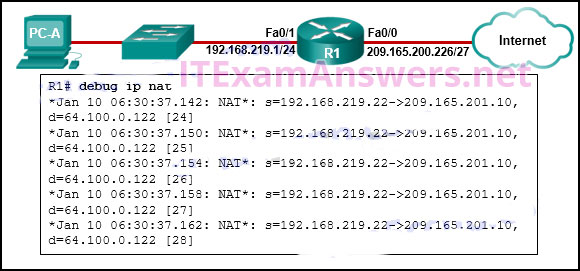
- The address on Fa0/0 should be 64.100.0.1.
- The NAT source access list matches the wrong address range.
- The inside global address is not on the same subnet as the ISP.
- The inside and outside NAT interfaces have been configured backwards.
59. Refer to the exhibit. A PC at address 10.1.1.45 is unable to access the Internet. What is the most likely cause of the problem?
- The NAT pool has been exhausted.
- The wrong netmask was used on the NAT pool.
- Access-list 1 has not been configured properly.
- The inside and outside interfaces have been configured backwards.
60. What is a disadvantage when both sides of a communication use PAT?
- Host IPv4 addressing is complicated.
- End-to-end IPv4 traceability is lost.
- The flexibility of connections to the Internet is reduced.
- The security of the communication is negatively impacted.
61. A small company has a web server in the office that is accessible from the Internet. The IP address 192.168.10.15 is assigned to the web server. The network administrator is configuring the router so that external clients can access the web server over the Internet. Which item is required in the NAT configuration?
- an IPv4 address pool
- an ACL to identify the local IPv4 address of the web server
- the keyword overload for the ip nat inside source command
- the ip nat inside source command to link the inside local and inside global addresses
62. A college student is studying for the Cisco CCENT certification and is visualizing extended access lists. Which three keywords could immediately follow the keywords permit or deny as part of an extended access list? (Choose three.)
- www
- tcp
- udp
- icmp
- telnet
- ftp
63. What is meant by the term “best match” when applied to the routing table lookup process?
- network match
- supernet match
- exact match
- longest match
64. Which three advantages are provided by static routing? (Choose three.)
- Static routing does not advertise over the network, thus providing better security.
- Configuration of static routes is error-free.
- Static routes scale well as the network grows.
- Static routing typically uses less network bandwidth and fewer CPU operations than dynamic routing does.
- The path a static route uses to send data is known.
- No intervention is required to maintain changing route information.
65. A network administrator is implementing a distance vector routing protocol between neighbors on the network. In the context of distance vector protocols, what is a neighbor?
- routers that are reachable over a TCP session
- routers that share a link and use the same routing protocol
- routers that reside in the same area
- routers that exchange LSAs
66. Refer to the exhibit. The student on the H1 computer continues to launch an extended ping with expanded packets at the student on the H2 computer. The school network administrator wants to stop this behavior, but still allow both students access to web-based computer assignments. What would be the best plan for the network administrator?
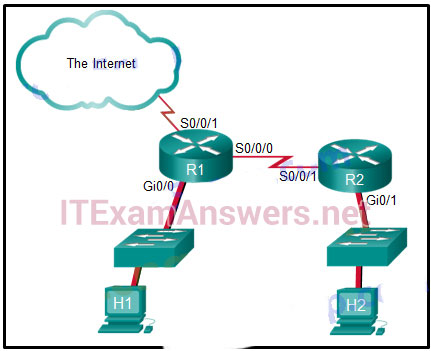
- Apply an outbound extended ACL on R1 S0/0/1.
- Apply an outbound standard ACL on R2 S0/0/1.
- Apply an inbound standard ACL on R1 Gi0/0.
- Apply an inbound extended ACL on R2 Gi0/1.
- Apply an inbound extended ACL on R1 Gi0/0.
67. What is associated with link-state routing protocols?
- low processor overhead
- poison reverse
- routing loops
- split horizon
- shortest-path first calculations
68. How is the router ID for an OSPFv3 router determined?
- the highest IPv6 address on an active interface
- the lowest MAC address on an active interface
- the highest IPv4 address on an active interface
- the highest EUI-64 ID on an active interface
69. An administrator attempts to change the router ID on a router that is running OSPFv3 by changing the IPv4 address on the router loopback interface. Once the IPv4 address is changed, the administrator notes that the router ID did not change. What two actions can the administrator take so that the router will use the new IPv4 address as the router ID? (Choose two.)
- Shut down and re-enable the loopback interface.
- Reboot the router.
- Copy the running configuration to NVRAM.
- Clear the IPv6 OSPF process.
- Disable and re-enable IPv4 routing.
70. Refer to the exhibit. Which would be chosen as the router ID of R2?
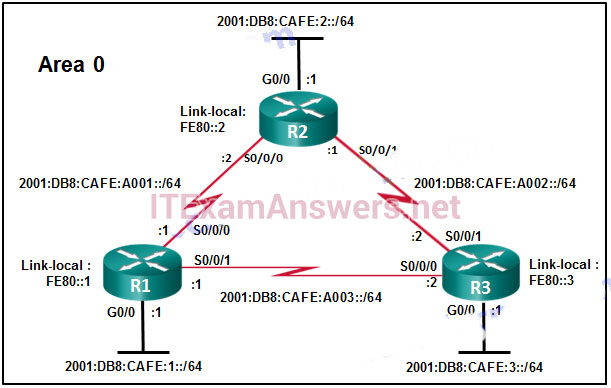
- 2001:DB8:CAFE:2::/64
- LLA: FE80::2
- 2001:DB8:CAFE:A001::/64
- The router ID has to be manually configured.
71. Which two pieces of information are required when creating a standard access control list? (Choose two.)
- destination address and wildcard mask
- source address and wildcard mask
- subnet mask and wildcard mask
- access list number between 100 and 199
- access list number between 1 and 99
72. Which two keywords can be used in an access control list to replace a wildcard mask or address and wildcard mask pair? (Choose two.)
- most
- host
- all
- any
- some
- gt
73. What is the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
- The first 28 bits of a supplied IP address will be ignored.
- The last four bits of a supplied IP address will be ignored.
- The first 32 bits of a supplied IP address will be matched.
- The first 28 bits of a supplied IP address will be matched.
- The last five bits of a supplied IP address will be ignored.
- The last four bits of a supplied IP address will be matched.
74. An administrator created and applied an outbound Telnet extended ACL on a router to prevent router-initiated Telnet sessions. What is a consequence of this configuration?
- The ACL will not work as desired because an outbound ACL cannot block router-initiated traffic.
- The ACL will work as desired as long as it is applied to the correct interface.
- The ACL will not work because only standard ACLs can be applied to vty lines.
- The ACL will work as long as it will be applied to all vty lines.
75. A network administrator is testing IPv6 connectivity to a web server. The network administrator does not want any other host to connect to the web server except for the one test computer. Which type of IPv6 ACL could be used for this situation?
- only a standard ACL
- a standard or extended ACL
- only an extended ACL
- an extended, named, or numbered ACL
- only a named ACL
76. What does an OSPF area contain?
- routers that share the same router ID
- routers whose SPF trees are identical
- routers that have the same link-state information in their LSDBs
- routers that share the same process ID
77. What is the effect of entering the network 192.168.10.1 0.0.0.0 area 0 command in router configuration mode?
- The interface with the IPv4 address 192.168.10.1 will be a passive interface.
- OSPF advertisements will include the network on the interface with the IPv4 address 192.168.10.1.
- This command will have no effect because it uses a quad zero wildcard mask.
- OSPF advertisements will include the specific IPv4 address 192.168.10.1.
78. What is the order of packet types used by an OSPF router to establish convergence?
- Hello, LSAck, LSU, LSR, DBD
- LSAck, Hello, DBD, LSU, LSR
- Hello, DBD, LSR, LSU, LSAck
- LSU, LSAck, Hello, DBD, LSR
79. What best describes the operation of distance vector routing protocols?
- They use hop count as their only metric.
- They only send out updates when a new network is added.
- They send their routing tables to directly connected neighbors.
- They flood the entire network with routing updates.
80. What is an advantage of using dynamic routing protocols instead of static routing?
- easier to implement
- more secure in controlling routing updates
- fewer router resource overhead requirements
- ability to actively search for new routes if the current path becomes unavailable
81. Refer to the exhibit. R1 and R2 are OSPFv3 neighbors. Which address would R1 use as the next hop for packets that are destined for the Internet?
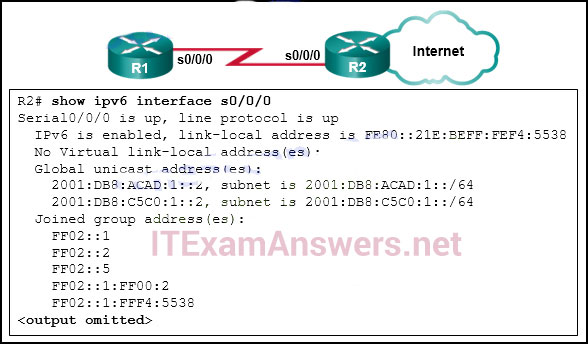
- FF02::5
- 2001:DB8:ACAD:1::2
- 2001:DB8:C5C0:1::2
- FE80::21E:BEFF:FEF4:5538
82. Refer to the exhibit. What address will be used as the router ID for the OSPFv3 process?
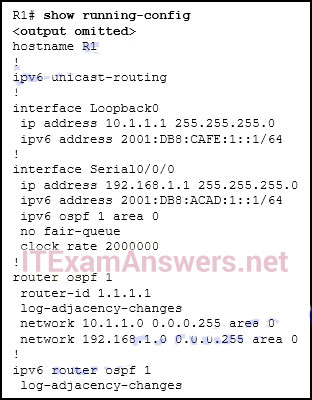
- 1.1.1.1
- 10.1.1.1
- 192.168.1.1
- 2001:DB8:CAFE:1::1
- 2001:DB8:ACAD:1::1
83. Which network design may be recommended for a small campus site that consists of a single building with a few users?
- a network design where the access and core layers are collapsed into a single layer
- a collapsed core network design
- a three-tier campus network design where the access, distribution, and core are all separate layers, each one with very specific functions
- a network design where the access and distribution layers are collapsed into a single layer
84. When does a switch use frame filtering?
- The destination MAC address is for a host on a different network segment from the source of the traffic.
- The destination MAC address is for a host on the same network segment as the source of the traffic.
- The destination MAC address is for a host with no entry in the MAC address table.
- The destination MAC address is for a host on a network supported by a different router.
85. Which command will verify the status of both the physical and the virtual interfaces on a switch?
- show running-config
- show ip interface brief
- show startup-config
- show vlan
86. Refer to the exhibit. A network administrator is investigating a lag in network performance and issues the show interfaces fastethernet 0/0 command. Based on the output that is displayed, what two items should the administrator check next? (Choose two.)
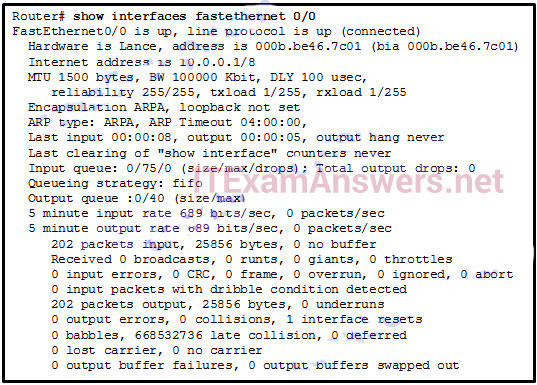
- cable lengths
- damaged cable termination
- duplex settings
- electrical interference
- incorrect cable types
87. Which command would be best to use on an unused switch port if a company adheres to the best practices as recommended by Cisco?
- shutdown
- ip dhcp snooping
- switchport port-security mac-address sticky
- switchport port-security violation shutdown
- switchport port-security mac-address sticky mac-address
88. Which two commands should be implemented to return a Cisco 3560 trunk port to its default configuration? (Choose two.)
- S1(config-if)# no switchport trunk allowed vlan
- S1(config-if)# no switchport trunk native vlan
- S1(config-if)# switchport mode dynamic desirable
- S1(config-if)# switchport mode access
- S1(config-if)# switchport access vlan 1
89. Which two methods can be used to provide secure management access to a Cisco switch? (Choose two.)
- Configure all switch ports to a new VLAN that is not VLAN 1.
- Configure specific ports for management traffic on a specific VLAN.
- Configure SSH for remote management.
- Configure all unused ports to a “black hole.”
- Configure the native VLAN to match the default VLAN.
90. Refer to the exhibit. A network administrator is configuring inter-VLAN routing on a network. For now, only one VLAN is being used, but more will be added soon. What is the missing parameter that is shown as the highlighted question mark in the graphic?
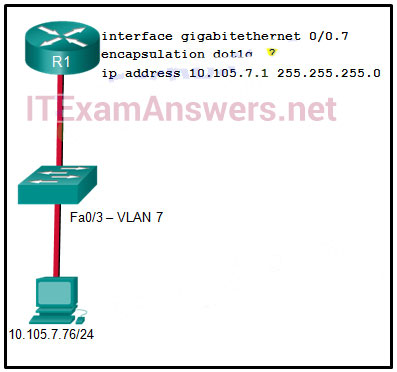
- It identifies the subinterface.
- It identifies the VLAN number.
- It identifies the native VLAN number.
- It identifies the type of encapsulation that is used.
- It identifies the number of hosts that are allowed on the interface.
91. Refer to the exhibit. A Layer 3 switch routes for three VLANs and connects to a router for Internet connectivity. Which two configurations would be applied to the switch? (Choose two.)
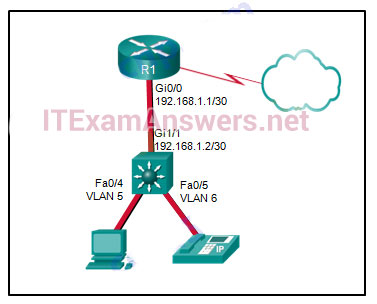
- (config)# interface gigabitethernet 1/1
(config-if)# no switchport
(config-if)# ip address 192.168.1.2 255.255.255.252 - (config)# interface vlan 1
(config-if)# ip address 192.168.1.2 255.255.255.0
(config-if)# no shutdown - (config)# interface gigabitethernet1/1
(config-if)# switchport mode trunk - (config)# interface fastethernet0/4
(config-if)# switchport mode trunk - (config)# ip routing
92. Fill in the blank.
Using router-on-a-stick inter-VLAN routing, how many subinterfaces have to be configured to support 10 VLANs? 10
93. Refer to the exhibit. Inter-VLAN communication between VLAN 10, VLAN 20, and VLAN 30 is not successful. What is the problem?
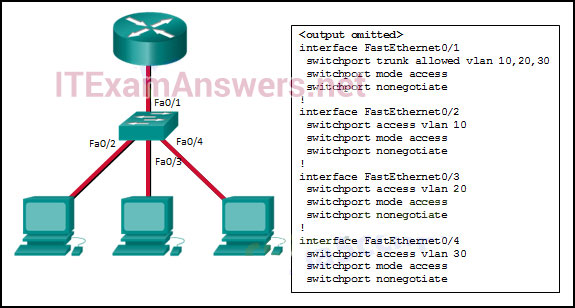
- The access interfaces do not have IP addresses and each should be configured with an IP address.
- The switch interface FastEthernet0/1 is configured as an access interface and should be configured as a trunk interface.
- The switch interface FastEthernet0/1 is configured to not negotiate and should be configured to negotiate.
- The switch interfaces FastEthernet0/2, FastEthernet0/3, and FastEthernet0/4 are configured to not negotiate and should be configured to negotiate.
94. When routing a large number of VLANs, what are two disadvantages of using the router-on-a-stick inter-VLAN routing method rather than the multilayer switch inter-VLAN routing method? (Choose two.)
- Multiple SVIs are needed.
- A dedicated router is required.
- Router-on-a-stick requires subinterfaces to be configured on the same subnets.
- Router-on-a-stick requires multiple physical interfaces on a router.
- Multiple subinterfaces may impact the traffic flow speed.
95. Which two statements are characteristics of routed ports on a multilayer switch? (Choose two.)
- They are not associated with a particular VLAN.
- The interface vlan <vlan number> command has to be entered to create a VLAN on routed ports.
- They support subinterfaces, like interfaces on the Cisco IOS routers.
- They are used for point-to-multipoint links.
- In a switched network, they are mostly configured between switches at the core and distribution layers.
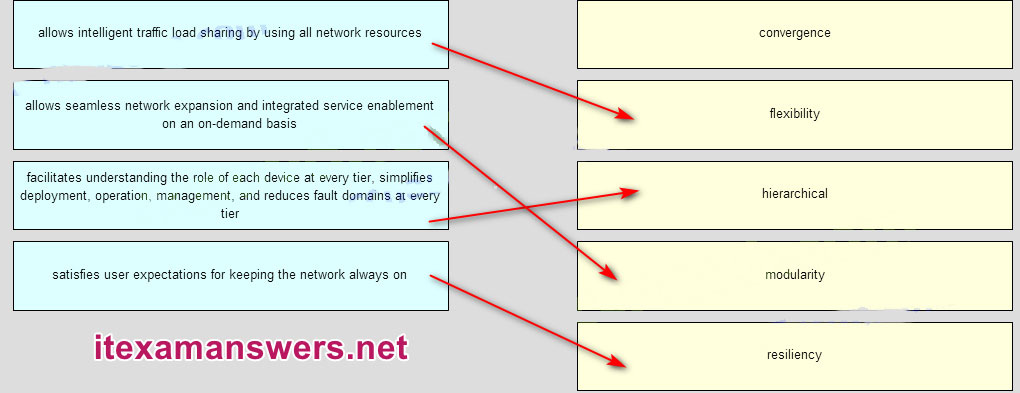
96. Match the borderless switched network guideline description to the principle. (Not all options are used.)
97. Fill in the blank. Do not use abbreviations.
The duplex full command configures a switch port to operate in the full-duplex mode.
98. Launch PT. Hide and Save PT
Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
To verify that the SVI is configured correctly, answer this question: Which ping command completed successfully?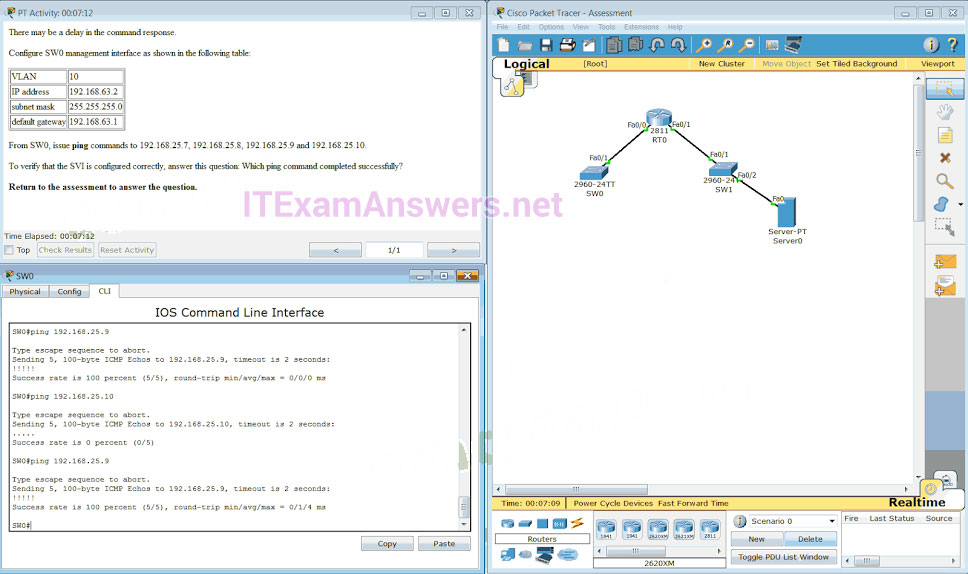
- ping 192.168.25.9
- ping 192.168.25.10
- ping 192.168.25.7
- ping 192.168.25.8
CONFIGURATION
SW0(config)#interface vlan 10
SW0(config-if)#ip address 192.168.63.2 255.255.255.0
SW0(config-if)#exit
SW0(config)#ip default-gateway 192.168.63.1
SW0(config)#end
99. Which command will create a static default route on R1 to send all traffic to the Internet and use serial 0/0 as the exit interface?
- R1(config)# ip route 255.255.255.255 0.0.0.0 serial 0/0
- R1(config)# ip route 0.0.0.0 255.255.255.0 serial 0/0
- R1(config)# ip route 0.0.0.0 255.255.255.255 serial 0/0
- R1(config)# ip route 0.0.0.0 0.0.0.0 serial 0/0
100. What is a result of connecting two or more switches together?
- The number of collision domains is reduced.
- The size of the broadcast domain is increased.
- The number of broadcast domains is increased.
- The size of the collision domain is increased.
101. What is meant by the term “best match” when applied to the routing table lookup process?
- exact match
- longest match
- network match
- supernet match
102. A router with two LAN interfaces, two WAN interfaces, and one configured loopback interface is operating with OSPF as its routing protocol. What does the router OSPF process use to assign the router ID?
- the highest IP address that is configured on the WAN interfaces
- the IP address of the interface that is configured with priority 0
- the highest IP address on the LAN interfaces
- the OSPF area ID that is configured on the interface with the highest IP address
- the loopback interface IP address
103. Order the DHCP process steps. (Not all options are used.)

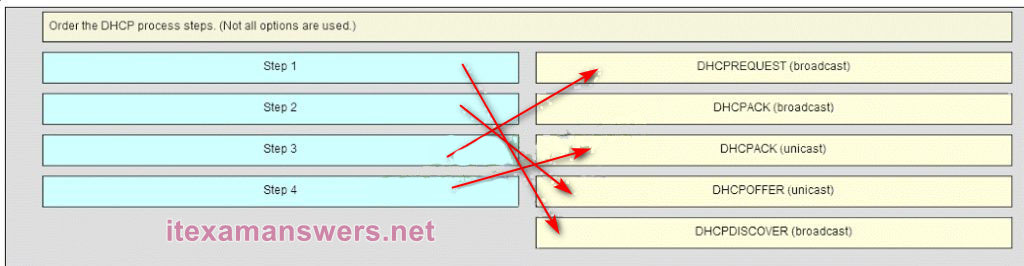
Place the options in the following order:
Step 3
– target left blank –
Step 4 *
Step 2 *
Step 1*
104. Refer to the exhibit. Host A has sent a packet to host B. What will be the source MAC and IP addresses on the packet when it arrives at host B?
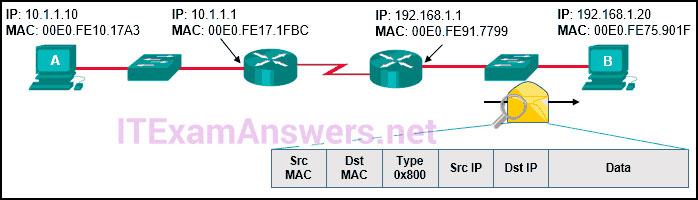
- Source MAC: 00E0.FE10.17A3
Source IP: 10.1.1.10 - Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.1 - Source MAC: 00E0.FE91.7799
Source IP: 192.168.1.1 - Source MAC: 00E0.FE91.7799
Source IP: 10.1.1.10 - Source MAC: 00E0.FE10.17A3
Source IP: 192.168.1.1
105. An administrator is trying to remove configurations from a switch. After using the command erase startup-config and reloading the switch, the administrator finds that VLANs 10 and 100 still exist on the switch. Why were these VLANs not removed?
- These VLANs cannot be deleted unless the switch is in VTP client mode.
- These VLANs are default VLANs that cannot be removed.
- These VLANs can only be removed from the switch by using the no vlan 10 and no vlan 100 commands.
- Because these VLANs are stored in a file that is called vlan.dat that is located in flash memory, this file must be manually deleted.
106. In which type of attack does a malicious node request all available IP addresses in the address pool of a DHCP server in order to prevent legitimate hosts from obtaining network access?
- CAM table overflow
- DHCP snooping
- MAC address flooding
- DHCP starvation
107. Refer to the exhibit.
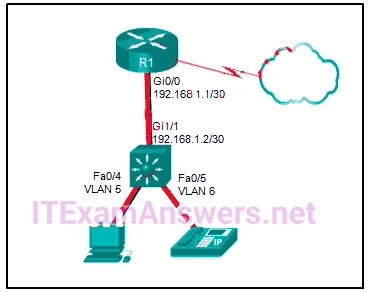
A Layer 3 switch routes for three VLANs and connects to a router for Internet connectivity. Which two configurations would be applied to the switch? (Choose two.)
- (config)# interface gigabitethernet1/1
(config-if)# switchport mode trunk
(config)# interface fastethernet0/4
(config-if)# switchport mode trunk - (config)# interface gigabitethernet 1/1
(config-if)# no switchport
(config-if)# ip address 192.168.1.2 255.255.255.252 - (config)# interface vlan 1
(config-if)# ip address 192.168.1.2 255.255.255.0
(config-if)# no shutdown - (config)# ip routing
108. Which characteristic is unique to EIGRP?
- EIGRP supports classless routing.
- EIGRP supports loop-free autosummarization.
- EIGRP supports both IPv4 and IPv6.
- EIGRP supports unequal-cost load balancing.
109. Match the router memory type that provides the primary storage for the router feature. (Not all options are used.)
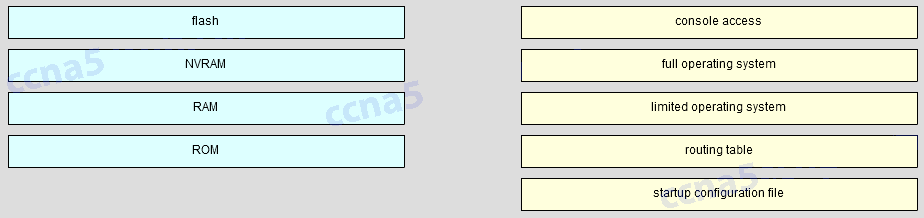
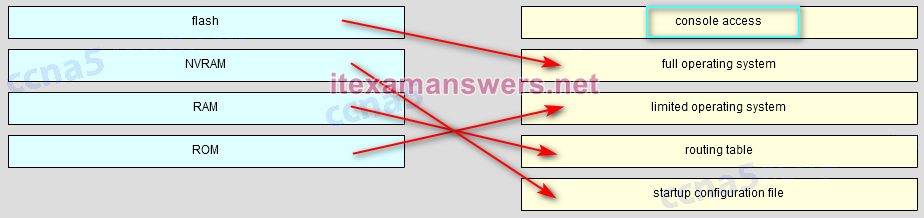
Place the options in the following order.
— not scored —
full operating system -> flash
limited operating system -> ROM
routing table -> RAM
startup configuration file -> NVRAM
Download PDF File below:*

-> Question 47 is incomplete.
It says “Choose two”.
The correct answers are:
* (config)# ip routing
* (config)# interface gigabitethernet 1/1
(config-if)# no switchport
(config-if)# ip address 192.168.1.2 255.255.255.252
-> Question 31 is wrong.
The correct answer is:
* The router ID has to be manually configured.