New Version:
1. On which switch interface would an administrator configure an IP address so that the switch can be managed remotely?
- FastEthernet0/1
- VLAN 1
- vty 0
- console 0
2. Which two issues might cause excessive runt and giant frames in an Ethernet network? (Choose two.)
- native VLAN mismatch
- damaged cable connector
- a malfunctioning NIC
- excessive collisions
- using the incorrect cable type
- incorrectly configured auto-MDIX feature
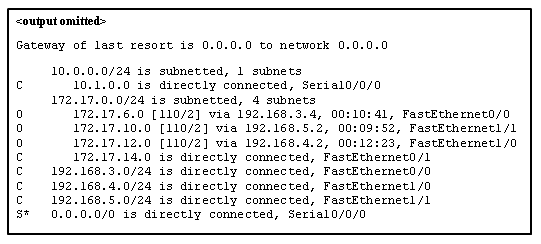
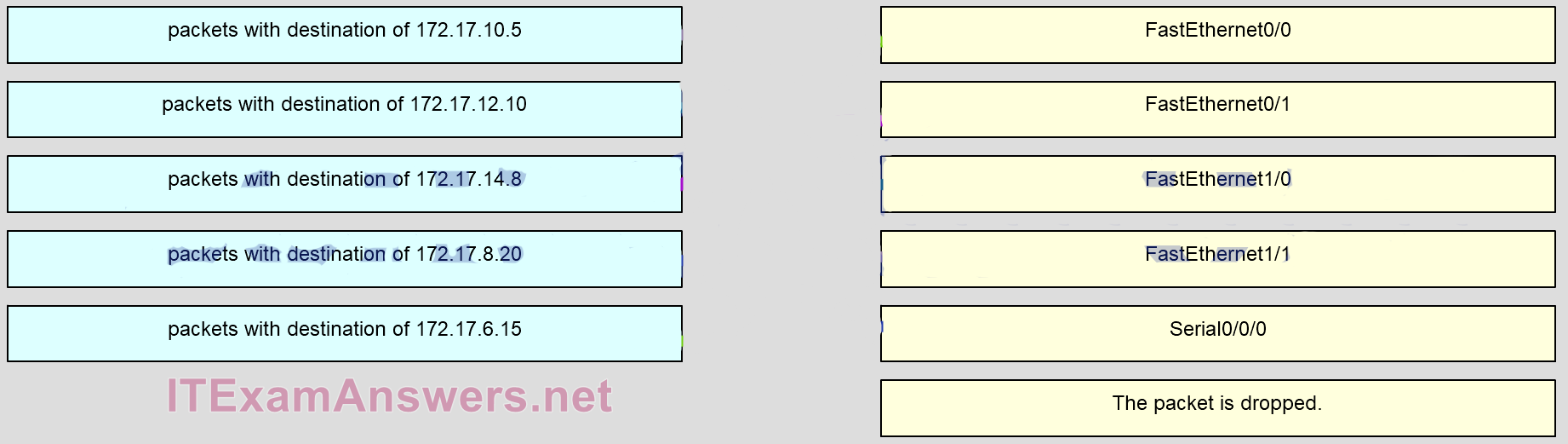
3. Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
4. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Which task has to be performed on Router 1 for it to establish an OSPF adjacency with Router 2?
- Issue the clear ip ospf process command.
- Remove the passive interface command from interface FastEthernet 0/0.
- Add the network 10.0.1.0 0.0.0.255 area 0 command to the OSPF process.
- Change the subnet mask of interface FastEthernet 0/0 to 255.255.255.0.
5. Refer to the exhibit. A network administrator is reviewing port and VLAN assignments on switch S2 and notices that interfaces Gi0/1 and Gi0/2 are not included in the output. Why would the interfaces be missing from the output?
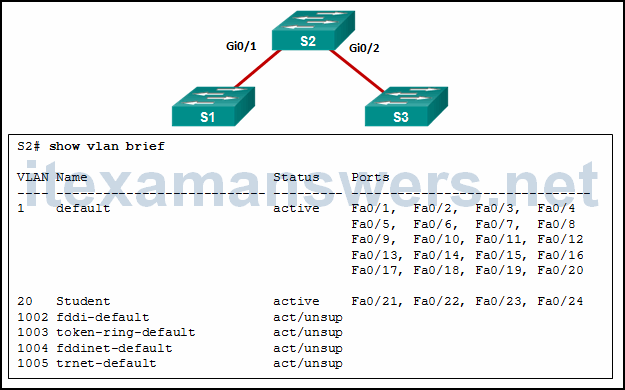
- There is a native VLAN mismatch between the switches.
- There is no media connected to the interfaces.
- They are administratively shut down.
- They are configured as trunk interfaces.
6. Which address type is not supported in IPv6?
- private
- multicast
- unicast
- broadcast
7. Which feature on a Cisco router permits the forwarding of traffic for which there is no specific route?
- next-hop
- gateway of last resort
- route source
- outgoing interface
8. A network administrator is using the router-on-a-stick model to configure a switch and a router for inter-VLAN routing. What configuration should be made on the switch port that connects to the router?
- Configure the port as an access port and a member of VLAN1.
- Configure the port as an 802.1q trunk port.
- Configure the port as a trunk port and assign it to VLAN1.
- Configure it as a trunk port and allow only untagged traffic.
9. Refer to the exhibit. A ping to PC3 is issued from PC0, PC1, and PC2 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?
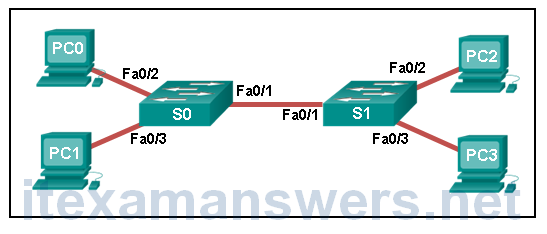
- just PC0 and PC1 MAC addresses
- just the PC0 MAC address
- PC0, PC1, and PC2 MAC addresses
- just the PC1 MAC address
- just the PC2 MAC address
10. A network administrator is designing an IPv4 addressing scheme and requires these subnets.
1 subnet of 100 hosts
2 subnets of 80 hosts
2 subnets of 30 hosts
4 subnets of 20 hosts
Which combination of subnets and masks will provide the best addressing plan for these requirements?
- 9 subnets of 126 hosts with a 255.255.255.128 mask
- 3 subnets of 126 hosts with a 255.255.255.128 mask
6 subnets of 30 hosts with a 255.255.255.224 mask - 3 subnets of 126 hosts with a 255.255.255.192 mask
6 subnets of 30 hosts with a 255.255.255.240 mask - 1 subnet of 126 hosts with a 255.255.255.192 mask
2 subnets of 80 hosts with a 255.255.255.224 mask
6 subnets of 30 hosts with a 255.255.255.240 mask
11. A network administrator has been allocated the IPv4 10.10.240.0/20 block of addresses for a LAN. Two devices on two different, but contiguous, subnets on the LAN have been assigned the addresses 10.10.247.1/21 and 10.10.248.10/24, respectively. The administrator has to create a third subnet from the remaining address range. To optimize the use of this address space, the new subnet will follow on directly from the existing subnets. What is the first available host address in the next available subnet?
- 10.10.248.17
- 10.10.249.1
- 10.10.250.1
- 10.10.255.17
12. When creating an IPv6 static route, when must a next-hop IPv6 address and an exit interface both be specified?
- when CEF is enabled
- when the static route is a default route
- when the next hop is a link-local address
- when the exit interface is a point-to-point interface
13. Refer to the exhibit. A network engineer is troubleshooting host connectivity on a LAN that uses a first hop redundancy protocol. Which IPv4 gateway address should be configured on the host?
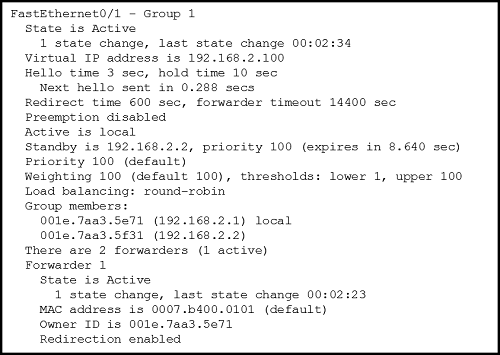
- 192.168.2.0
- 192.168.2.1
- 192.168.2.2
- 192.168.2.100
14. How many /30 subnets can be created from one /27 subnet?
- 2
- 4
- 6
- 8
15. Fill in the blank.
When port security is enabled, a switch port uses the default violation mode of shutdown until specifically configured to use a different violation mode.
16. Refer to the exhibit. What protocol can be configured on gateway routers R1 and R2 that will allow traffic from the internal LAN to be load balanced across the two gateways to the Internet?
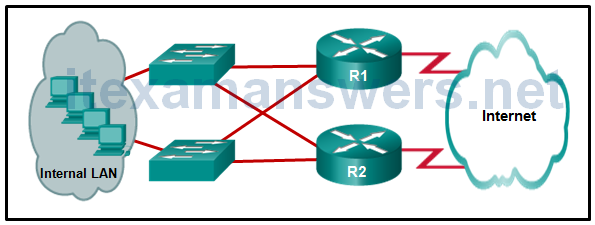
CCNA ICND2 019
- STP
- PVST
- PVST+
- GLBP
17. What is the purpose of setting the native VLAN separate from data VLANs?
- The native VLAN is for carrying VLAN management traffic only.
- The security of management frames that are carried in the native VLAN can be enhanced.
- A separate VLAN should be used to carry uncommon untagged frames to avoid bandwidth contention on data VLANs.
- The native VLAN is for routers and switches to exchange their management information, so it should be different from data VLANs.
18. Refer to the exhibit. All the routers that are displayed are part of the EIGRP domain. Assuming EIGRP metric weights are not altered in the configurations, which path will a packet take that originates from a host on the 192.168.1.0/24 network and is going to a host on the 192.168.2.0/24 network?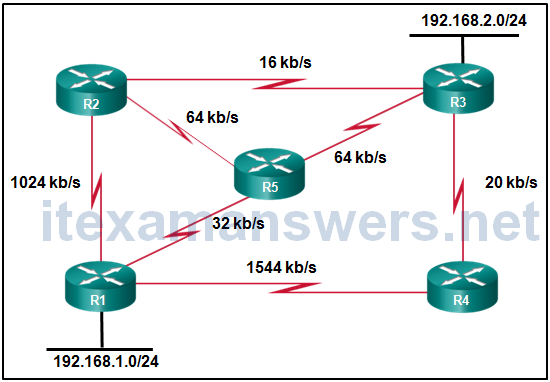
- R1, R4, R3
- R1, R5, R3
- R1, R2, R3
- R1, R2, R5, R3
19. If no bridge priority is configured in PVST, which criteria is considered when electing the root bridge?
- lowest IP address
- lowest MAC address
- highest IP address
- highest MAC address
20. Refer to the exhibit. A network administrator is configuring EIGRP AS 20 on Router_2 and has received the error that is shown. What is the cause of the error?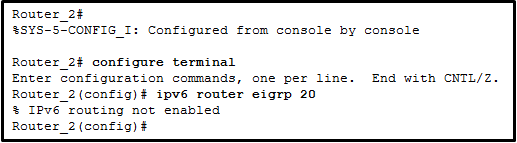
- The autonomous system (AS) number is not the same as the number on other routers in this network.
- The IPv6 routing process cannot be implemented until IPv6 routing is enabled.
- The EIGRPv6 interface configuration is incomplete.
- The passive-interface default command has been implemented for EIGRPv6.
21. Refer to the exhibit. Router R1 has recently been configured to operate in an IPv6 only network and is connected via interface Gigabit Ethernet 0/0 to router R2. R2 is configured correctly, but will not form a neighbor relationship with R1 What is the problem?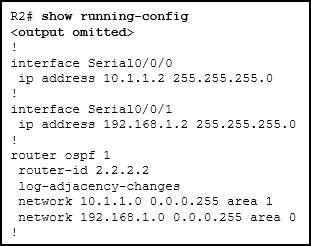
- The IP address is missing on interface Gigabit Ethernet 0/0.
- The command ipv6 unicast-routing has not been implemented.
- The router ID has not been created on router R1.
- The EIGRPv6 process has not been activated on interface Gigabit Ethernet 0/0.
22. Which is a characteristic of EtherChannel?
- Which is a characteristic of EtherChannel?
- STP will not block redundant EtherChannel bundles between two switches.
- STP treats all interfaces in a bundle as a single logical link.
- EtherChannel configuration is applied to each physical port.
23. Refer to the exhibit. Based on this configuration, which two OSPF router roles are assumed by R2? (Choose two.)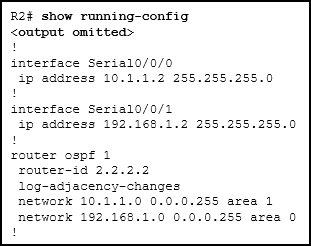
- backbone router
- internal router
- designated router
- area border router
- autonomous system boundary router
24. An administrator wants to replace the configuration file on a Cisco router by loading a new configuration file from a TFTP server. What two things does the administrator need to know before performing this task? (Choose two.)
- router IP address
- TFTP server IP address
- name of the configuration file that is currently stored on the router
- name of the configuration file that is stored on the TFTP server
- configuration register value
25. What is the most likely cause when the output of the show interface command shows that a switch interface is up but the line protocol is down?
- A cable is not attached to the interface.
- An incorrect default gateway has been configured.
- An encapsulation type mismatch exists.
- An incorrect cable type has been attached to the interface.
26. What are two WAN connection enhancements that are achieved by implementing PPPoE? (Choose two.)
- Encapsulating Ethernet frames within PPP frames is an efficient use of bandwidth.
- DSL CHAP features are included in PPPoE.
- PPP enables the ISP to assign an IP address to the customer WAN interface.
- An Ethernet link supports a number of data link protocols.
- CHAP enables customer authentication and accounting.
27. Refer to the exhibit. A network administrator is reviewing the configuration of switch S1. Which protocol has been implemented to group multiple physical ports into one logical link?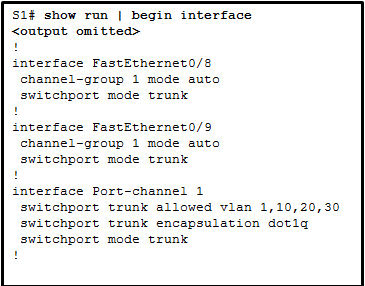
- PAgP
- DTP
- LACP
- STP
28. Fill in the blank. Use only an acronym. PPPoE creates a PPP tunnel through the DSL connection for the purpose of sending PPP frames.
29. Refer to the exhibit. Host A sends a data packet to host B. What will be the addressing information of the data packet when it reaches host B?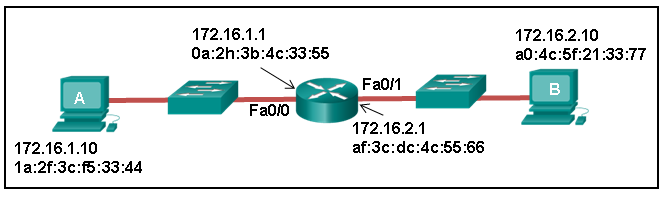
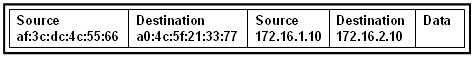
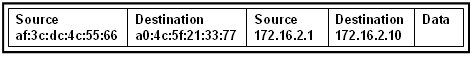
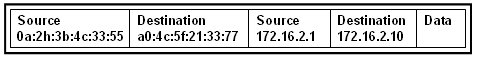
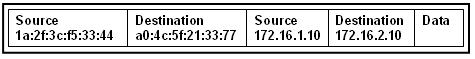
The correct answer is option 1
30. What two STP features are incorporated into Rapid PVST+? (Choose two.)
- UplinkFast
- PortFast
- BPDU guard
- BPDU filter
- BackboneFast
- loop guard
31. What are two load-balancing methods in the EtherChannel technology? (Choose two.)
- combination of source port and IP to destination port and IP
- source IP to destination IP
- source port to destination port
- combination of source MAC and IP to destination MAC and IP
- source MAC to destination MAC
32. Which WAN technology can serve as the underlying network to carry multiple types of network traffic such as IP, ATM, Ethernet, and DSL?
- ISDN
- MPLS
- Frame Relay
- Ethernet WAN
33. Which WAN connectivity method would be used in a remote location where there are no service provider networks?
- cable
- VPN
- VSAT
- WiMAX
34. How many 64 kb/s voice channels are combined to produce a T1 line?
- 8
- 16
- 24
- 32
35. Refer to the exhibit. All the displayed switches are Cisco 2960 switches with the same default priority and operating at the same bandwidth. Which three ports will be STP designated ports? (Choose three.)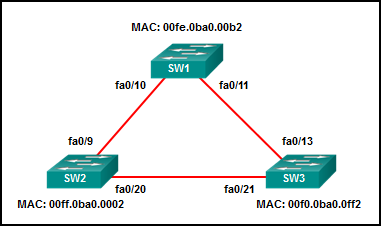
- fa0/9
- fa0/10
- fa0/11
- fa0/13
- fa0/20
- fa0/21
36. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Why are users in the OSPF network not able to access the Internet?
- The default route is not redistributed correctly from router R1 by OSPF.
- The interface that is connected to the ISP router is down.
- The OSPF network statements are misconfigured on routers R2 and R3.
- The OSPF timers that are configured on routers R1, R2, and R3 are not compatible.
- The network statement is misconfigured on router R1.
37. Refer to the exhibit. Which interface on switch S1 should be configured as a DHCP snooping trusted port to help mitigate DHCP spoofing attacks?
- G0/23
- G0/1
- G0/24
- G0/22
38. An administrator who is troubleshooting connectivity issues on a switch notices that a switch port configured for port security is in the err-disabled state. After verifying the cause of the violation, how should the administrator re-enable the port without disrupting network operation?
- Reboot the switch.
- Issue the no shutdown command on the interface.
- Issue the no switchport port-security command, then re-enable port security.
- Issue the no switchport port-security violation shutdown command on the interface.
39. Refer to the exhibit. Routers R1 and R2 have been configured for PPP using CHAP as the authentication protocol, but the link will not go to the up and up state. What configuration error has been made?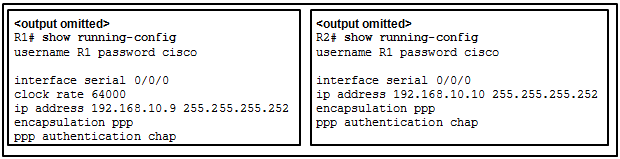
- R1 has an incorrect username.
- Both routers are missing the ppp pap sent-username command.
- One of the routers needs a different password for the specified username.
- One of the router IP addresses needs to be changed to be on the same network.
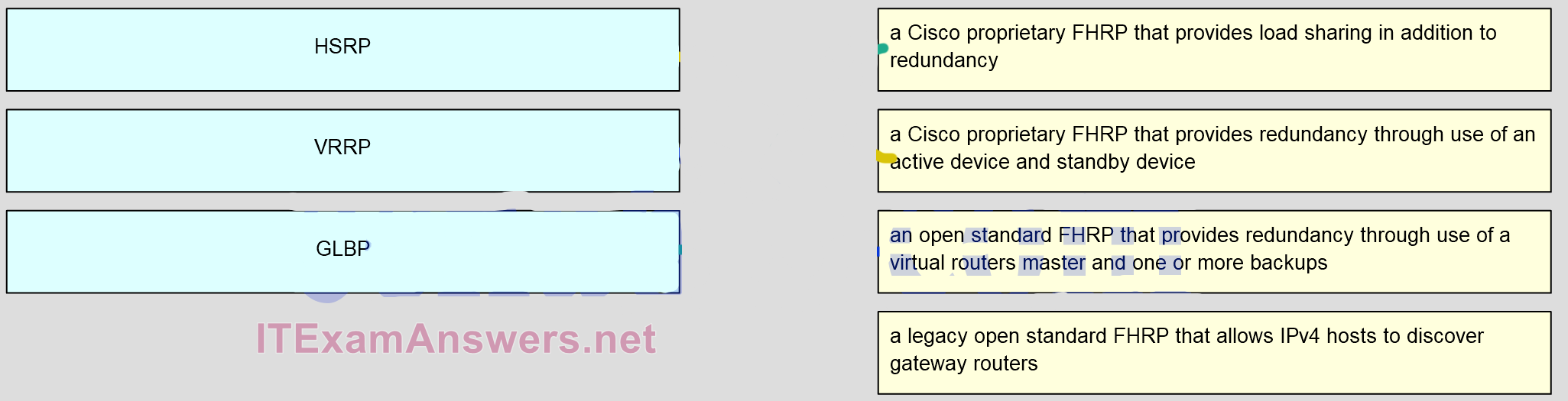
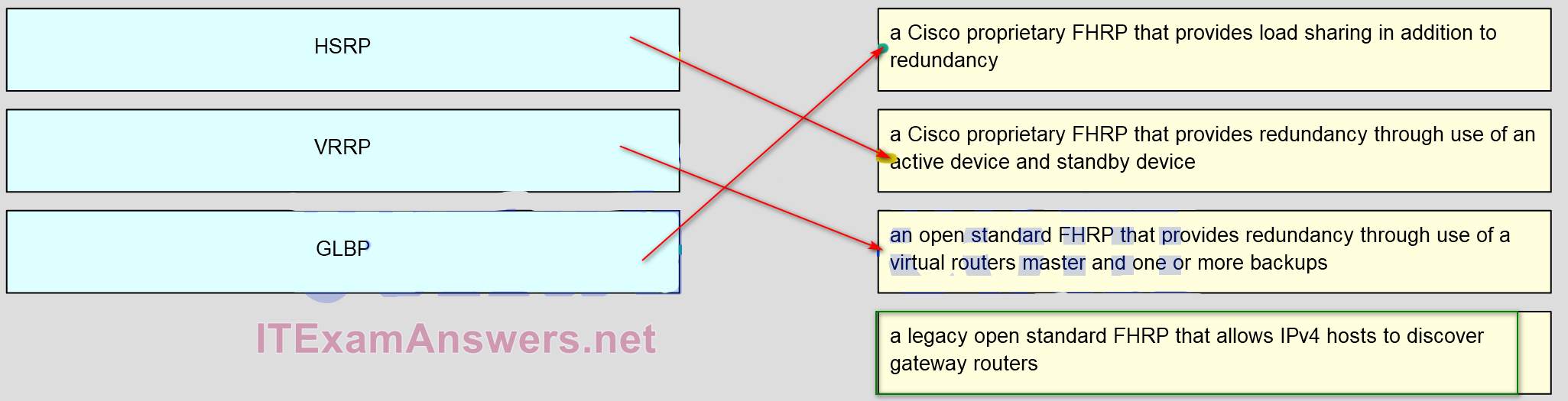
40. Match the FHRP protocols to their description. (Not all options are used.)
41. Which three statements characterize UDP? (Choose three.)
- UDP provides basic connectionless transport layer functions.
- UDP provides connection-oriented, fast transport of data at Layer 3.
- UDP relies on application layer protocols for error detection.
- UDP is a low overhead protocol that does not provide sequencing or flow control mechanisms.
- UDP relies on IP for error detection and recovery.
- UDP provides sophisticated flow control mechanisms.
42. What are two reasons why an administrator might choose to use static routing rather than dynamic routing? (Choose two.)
- Static routing is easier to maintain in large networks.
- Static routing is more secure.
- Static routing is more scalable.
- Static routing uses less router processing and bandwidth.
- Static routing does not require complete knowledge of the whole network.
43. Refer to the exhibit. A network administrator issues the show lldp neighbors command to display information about neighboring devices. What can be determined based on the information?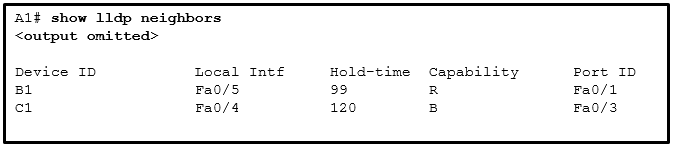
- Device B1 is a WLAN access point.
- Device C1 is a switch.
- Device A1 is connected to the port Fa0/5 on device B1.
- Device C1 is connected to device B1 through the port Fa0/3.44.
44. How will a router handle static routing differently if Cisco Express Forwarding is disabled?
- It will not perform recursive lookups.
- Serial point-to-point interfaces will require fully specified static routes to avoid routing inconsistencies.
- Ethernet multiaccess interfaces will require fully specified static routes to avoid routing inconsistencies.
- Static routes that use an exit interface will be unnecessary.
45. An OSPFv3 router has no IPv4 addresses configured and the router ID has not been manually set. What is the result of this configuration?
- OSPFv3 will not start.
- The highest IPv6 address of a loopback interface will be used as the router ID.
- The highest IPv6 address of a physical interface will be used as the router ID.
- The router will automatically generate a router ID using the MAC address of one of the interfaces.
46. What type of installation is needed to view syslog messages?
- A syslog server must be installed on a workstation.
- A syslog client must be installed on a workstation.
- A syslog server must be installed on a router.
- Because any network equipment can interpret syslog messages, nothing special is needed to view them.
47. Which two things should a network administrator modify on a router to perform password recovery? (Choose two.)
- system ROM
- the startup configuration file
- the system image file
- the configuration register value
- the NVRAM file system
48. What effect does the default-information originate command have on a Cisco router that is configured for RIP?
- Any routes that are learned from a neighboring router will propagate to other adjacent routers.
- Any static route that is learned from a neighboring router will propagate to other adjacent routers.
- Any dynamic route that is learned from a neighboring router will propagate to other adjacent routers.
- Any default static route that is configured on the router will propagate to other adjacent routers.
49. What information can be verified through the show ip dhcp binding command?
- the number of IP addresses remaining in the DHCP pool
- the IPv4 addresses that have been excluded from the DHCPv4 pool
- that DHCPv4 discover messages are still being received by the DHCP server
- the IPv4 addresses that are assigned to hosts by the DHCP server
50. Refer to the exhibit. A network administrator has added a new subnet to the network and needs hosts on that subnet to receive IPv4 addresses from the DHCPv4 server.
What two commands will allow hosts on the new subnet to receive addresses from the DHCP4 server? (Choose two.)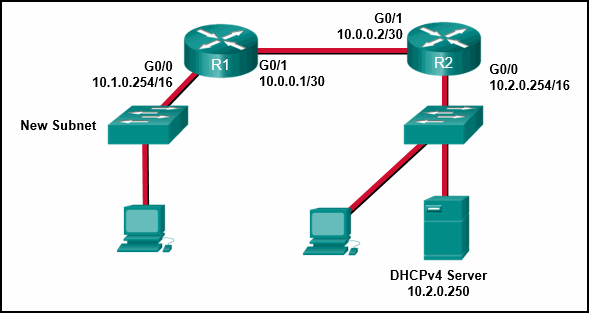
- R1(config)# interface G0/0
- R1(config-if)# ip helper-address 10.2.0.250
- R2(config)# interface G0/0
- R2(config-if)# ip helper-address 10.2.0.250
- R1(config-if)# ip helper-address 10.1.0.254
- R1(config)# interface G0/1
51. What are three characteristics of the CSMA/CD process? (Choose three.)
- Devices can be configured with a higher transmission priority.
- A jam signal indicates that the collision has cleared and the media is not busy.
- A device listens and waits until the media is not busy before transmitting.
- The device with the electronic token is the only one that can transmit after a collision.
- All of the devices on a segment see data that passes on the network medium.
- After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.
52. Which ACE would permit traffic from hosts only on the 192.168.8.0/22 subnet?
- permit 192.168.8.0 0.0.7.255
- permit 192.168.0.0 0.0.15.255
- permit 192.168.8.0 0.0.3.255
- permit 192.168.8.0 255.255.248.0
53. Refer to the exhibit. Static NAT is being configured to allow PC 1 access to the web server on the internal network. What two addresses are needed in place of A and B to complete the static NAT configuration? (Choose two.)
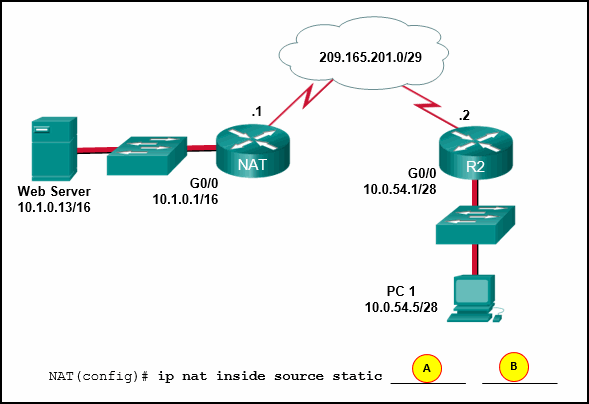
- A = 209.165.201.2
- A = 10.1.0.13
- B = 209.165.201.1
- B = 209.165.201.7
- B = 10.0.254.5
54. What is the purpose of the overload keyword in the ip nat inside source list 1 pool NAT_POOL overload command?
- It allows many inside hosts to share one or a few inside global addresses.
- It allows a pool of inside global addresses to be used by internal hosts.
- It allows external hosts to initiate sessions with internal hosts.
- It allows a list of internal hosts to communicate with a specific group of external hosts.
55. Refer to the exhibit. Which source address is being used by router R1 for packets being forwarded to the Internet?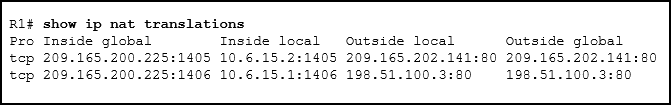
- 198.51.100.3
- 209.165.202.141
- 10.6.15.2
- 209.165.200.225
56. Which three layers of the OSI model map to the application layer of the TCP/IP model? (Choose three.)
- application
- presentation
- session
- data link
- transport
- network
57. Which address prefix range is reserved for IPv4 multicast?
- 240.0.0.0 – 254.255.255.255
- 224.0.0.0 – 239.255.255.255
- 169.254.0.0 – 169.254.255.255
- 127.0.0.0 – 127.255.255.255
58. Which IPv6 prefix is reserved for communication between devices on the same link?
- FC00::/7
- 2001::/32
- FE80::/10
- FDFF::/7
59. Refer to the exhibit. A network administrator needs to add an ACE to the TRAFFIC-CONTROL ACL that will deny IP traffic from the subnet 172.23.16.0/20. Which ACE will meet this requirement?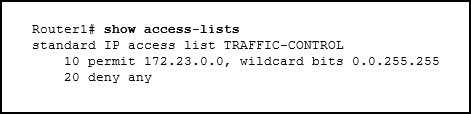
- 15 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.15.255
- 30 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.255.255
60. Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose two.)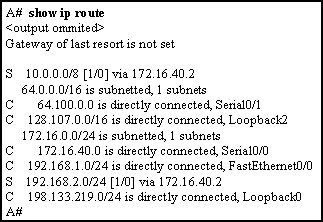
- 10.0.0.0/8
- 64.100.0.0/16
- 128.107.0.0/16
- 172.16.40.0/24
- 192.168.1.0/24
- 192.168.2.0/24
61. Refer to the exhibit. Which three events will occur as a result of the configuration shown on R1? (Choose three.)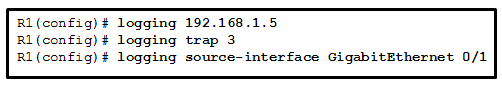
- Messages that are sent to the syslog server will be limited to levels 3 or lower.
- Messages that are sent to the syslog server will be limited to levels 3 and higher.
- Only traffic that originates from the GigabitEthernet 0/1 interface will be monitored.
- Messages that are sent to the syslog server will use 192.168.1.5 as the destination IP address.
- The syslog messages will contain the IP address the GigabitEthernet 0/1 interface.
- For multiple occurrences of the same error, only the first three messages will be sent to the server.
62. Which protocol defines port-based authentication to restrict unauthorized hosts from connecting to the LAN through publicly accessible switch ports?
- 802.1x
- RADIUS
- TACACS+
- SSH
63. Which two protocols are used to provide server-based AAA authentication? (Choose two.)
- SSH
- TACACS+
- RADIUS
- 802.1x
- SNMP
64. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function of TCP or UDP in this situation? (Choose three.)
- The UDP destination port number identifies the application or service on the server which will handle the data.
- TCP is the preferred protocol when a function requires lower network overhead.
- UDP segments are encapsulated within IP packets for transport across the network.
- The source port field identifies the running application or service that will handle data returning to the PC.
- The TCP source port number identifies the sending host on the network.
- The TCP process running on the PC randomly selects the destination port when establishing a session with the server.
65. Which type of IPv6 address refers to any unicast address that is assigned to multiple hosts?
- unique local
- global unicast
- link-local
- anycast
66. Refer to the exhibit. A network technician issues the command show vlan to verify the VLAN configuration. Based on the output, which port should be assigned with native VLAN?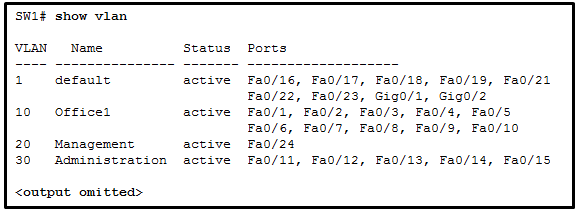
- Gig0/1
- Fa0/12
- Fa0/20
- Fa0/24
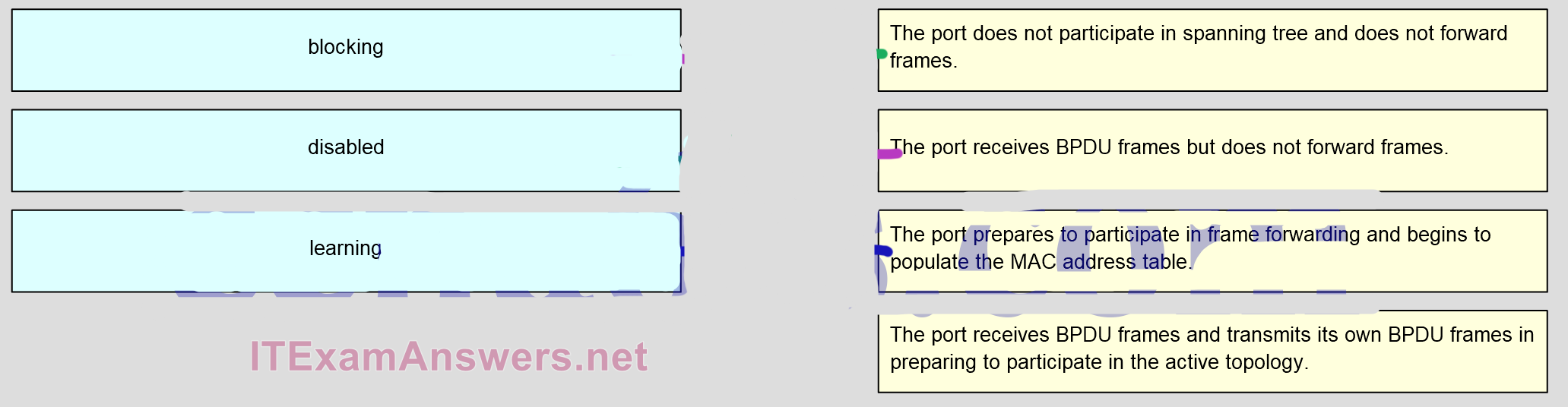
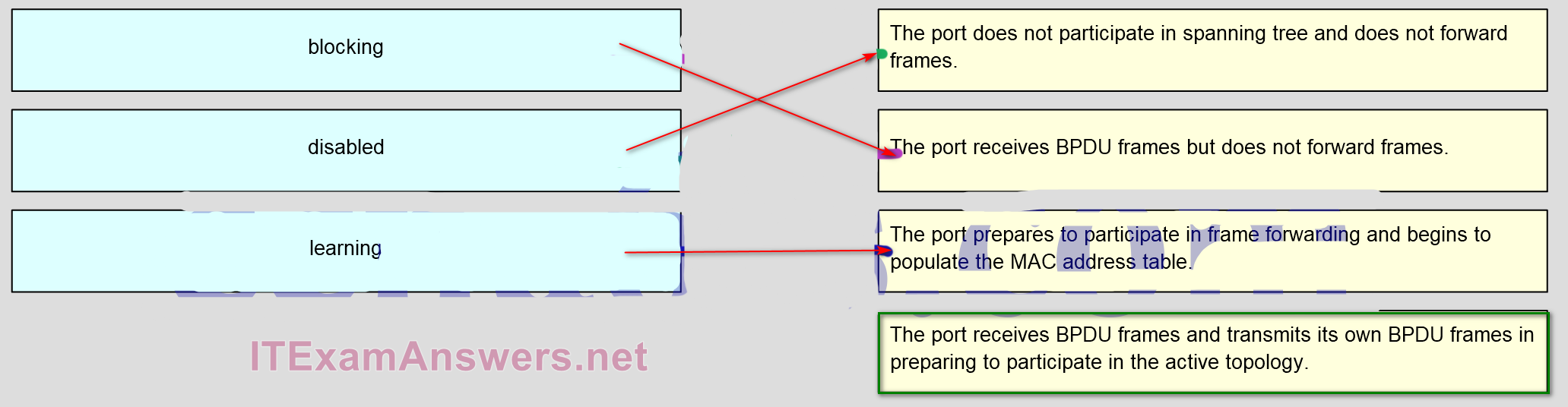
67. Match the port state with its condition. (Not all options are used.)
68. An IT security specialist enables port security on a switch port of a Cisco switch. What is the default violation mode in use until the switch port is configured to use a different violation mode?
- shutdown
- disabled
- restrict
- protect
69. Which technology supports CHAP authentication over a dialer interface?
- GRE
- PPPoE
- eBGP
- VPN
70. Which two issues can cause both runts and giants in Ethernet networks? (Choose two.)
- a malfunctioning NIC
- CRC errors
- electrical interference on serial interfaces
- half-duplex operations
- using the incorrect cable type
71. Which three STP states were replaced with the RSTP discarding state? (Choose three.)
- listening
- learning
- blocking
- disabled
- forwarding
72. What is the value used to determine which port on a non-root bridge will become a root port in a STP network?
- the highest MAC address of all the ports in the switch
- the lowest MAC address of all the ports in the switch
- the VTP revision number
- the path cost
73. Refer to the exhibit. Users on the R1 LAN and R2 LAN are unable to communicate. Based on the IPv6 addressing of the network displayed, what is the problem?
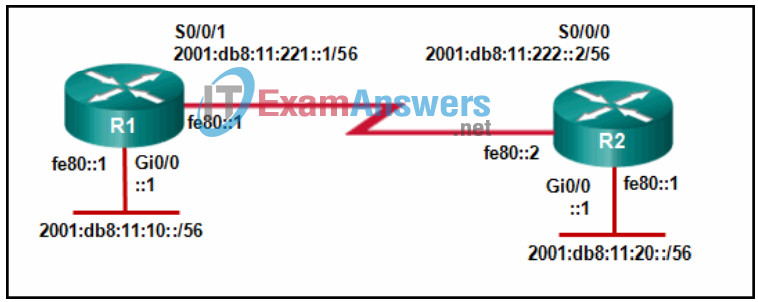
- R1 has a link-local address conflict with interfaces Gi0/0 and S0/0/1.
- The serial interfaces on R1 and R2 are on different subnets.
- A link-local and global unicast address cannot both be configured on an interface.
- The LAN interfaces on R1 and R2 are on the same subnet.
74. Which statement describes the Cisco License Manager?
- It is a free, standalone software application for deploying Cisco software licenses across the network.
- It is a web-based portal for getting and registering individual software licenses.
- It is a centralized TFTP server that enables control of the number and revision level of Cisco IOS images.
- It is an organized collection of processes and components used to activate Cisco IOS software feature sets by obtaining and validating Cisco software licenses.
75. After a license has been purchased and installed, what is the next step that is required before it is activated?
- Reboot the router.
- Copy the running configuration to NVRAM.
- Copy the running configuration to flash.
- Issue the license boot module technology-package command.
76. Refer to the exhibit. A network engineer is preparing to upgrade the IOS system image on a Cisco 2901 router. Based on the output shown, how much space is available for the new image?
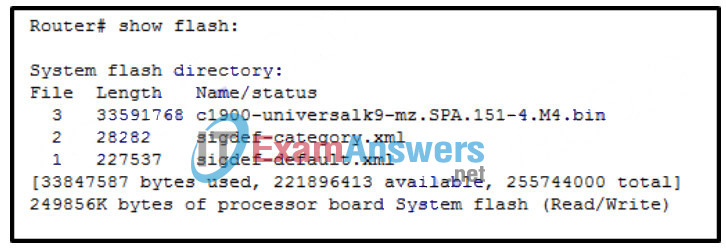
- 25574400 bytes
- 249856000 bytes
- 221896413 bytes
- 33591768 byte
77. What are the only two roles that permit an OSPF router to be configured for summarization? (Choose two.)
- backbone router
- internal router
- designated router
- area border router
- autonomous system boundary router
78. Which two addresses represent valid destination addresses for an OSPFv3 message? (Choose two.)
- FF02::5
- 224.0.0.5
- FF02::A
- FE80::42
- 2001:db8:acad:1::1
79. Refer to the exhibit. Which address will R1 use as the source address for all OSPFv3 messages that will be sent to neighbors?
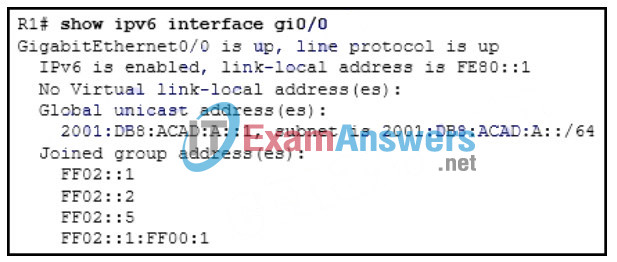
- FE80::1
- 2001:DB8:ACAD:A::1
- FF02::1
- FF02::5
80. When OSPFv2 neighbors are establishing adjacencies, in which state do they elect a DR and BDR router?
- Exchange state
- Init state
- Two-Way state
- Loading state
81. A network administrator has just changed the router ID on a router that is working in an OSPFv2 environment. What should the administrator do to reset the adjacencies and use the new router ID?
- Configure the network statements.
- Change the interface priority.
- Issue the clear ip ospf process privileged mode command.
- Change the OSPFv2 process ID.
82. When a link failure occurs on a network running EIGRP, how does DUAL determine a replacement route to a destination router?
- DUAL examines the neighbor table to find the closest adjacency.
- DUAL examines the routing table to find a feasible successor route.
- DUAL examines the topology table to find a feasible successor route.
- DUAL immediately sends queries to neighboring routers to build a new routing table.
83. Refer to the exhibit. Router R2 has recently been configured and connected via interface Gigabit Ethernet 0/0 to router R1. R1 is configured correctly, but fails to establish a neighbor relationship with R2. What is the problem?
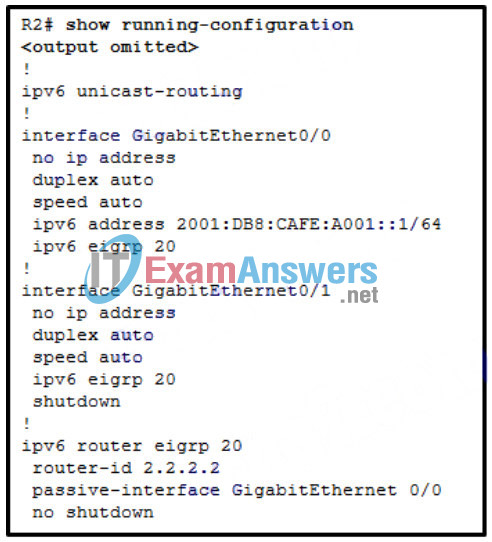
- The command ipv6 unicast-routing should be implemented in the router configuration mode.
- The command ipv6 unicast-routing has not been implemented.
- The EIGRPv6 process has not been activated on interface Gigabit Ethernet 0/0.
- The passive-interface command is preventing hello packets from being sent.
84. Which two aspects of the configuration of EIGRP for IPv6 differ from its configuration for IPv4? (Choose two.)
- For IPv6 no router ID is required for the EIGRP routing process to start.
- No network command is needed to enable EIGRP for IPv6.
- IPv6 requires a global unicast address on EIGRP interfaces.
- For IPv6, the autonomous system values on routers in a domain running EIGRP do not have to match.
- EIGRP on IPv6 is configured directly on router interfaces.
85. Which EIGRP route would have the preferred administrative distance?
- a summary route
- an internal route
- an external route that is redistributed from RIP
- an external route that is redistributed from OSPF
86. Refer to the exhibit. Which two networks contain feasible successors? (Choose two.)
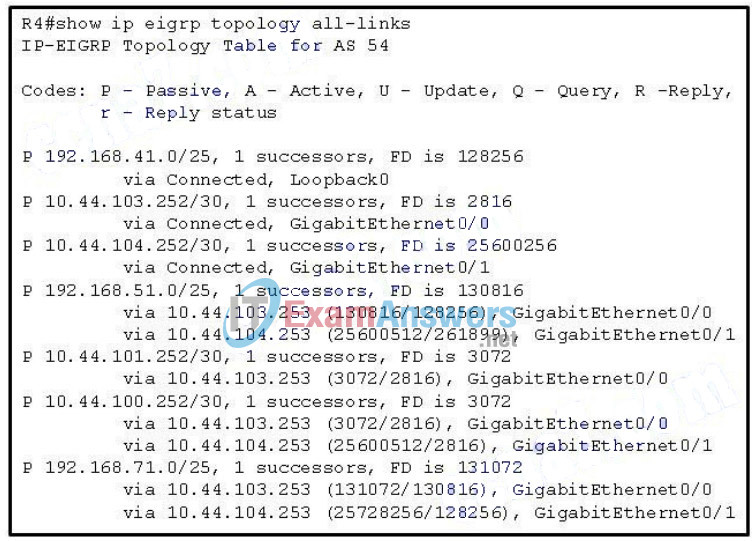
- 192.168.71.0
- 192.168.51.0
- 10.44.100.252
- 10.44.104.253
- 10.44.101.252
87. Which three metric weights are set to zero by default when costs in EIGRP are being calculated? (Choose three.)
- k1
- k2
- k3
- k4
- k5
- k6
88. Refer to the exhibit. An administrator is examining the message in a syslog server. What can be determined from the message?
- This is a notification message for a normal but significant condition.
- This is an alert message for which immediate action is needed.
- This is an error message for which warning conditions exist.
- This is an error message indicating the system is unusable.
89. What are two characteristics of SNMP community strings? (Choose two.)
- A vulnerability of SNMPv1, SNMPv2, and SNMPv3 is that they send the community strings in plaintext.
- Commonly known community strings should be used when configuring secure SNMP.
- If the manager sends one of the correct read-only community strings, it can get information and set information in an agent.
- SNMP read-only community strings can be used to get information from an SNMP-enabled device.
- SNMP read-write community strings can be used to set information on an SNMP-enabled device.
90. Which management protocol can be used securely with Cisco devices to retrieve or write to variables in a MIB?
- SNMP version 1
- SNMP version 2
- SNMP version 2c
- SNMP version 3
91. What is an SNMP management agent?
- a computer loaded with management software and used by an administrator to monitor a network
- a database that a device keeps about network performance
- software that is installed on devices managed by SNMP
- a communication protocol that is used by SNMP
92. What are three parameters that are used by NetFlow to classify traffic? (Choose three.)
- ingress interface
- TOS field
- egress interface
- number of packets
- number of bytes
- port number
93. Refer to the exhibit. R1 and R2 are connected to the same LAN segment and are configured to run OSPFv3. They are not forming a neighbor adjacency. What is the cause of the problem?
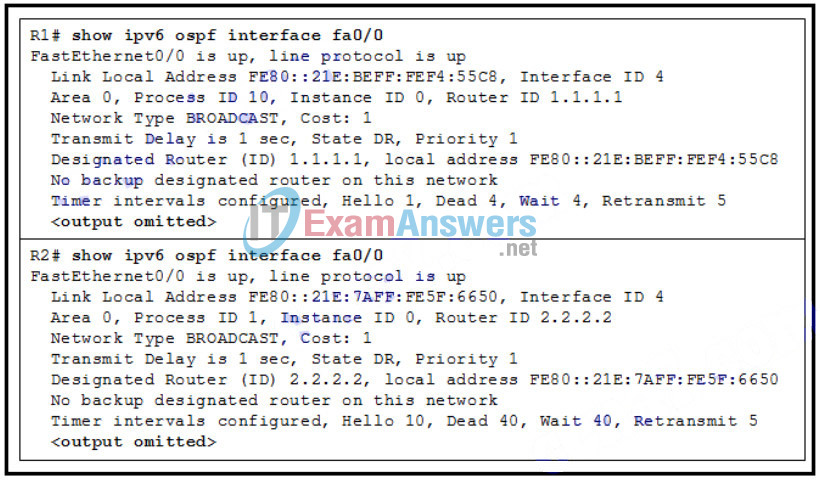
- The IPv6 addresses of R1 and R2 are not in the same subnet.
- The OSPFv3 process IDs of R1 and R2 are different.
- The timer intervals of R1 and R2 do not match.
- The priority value of both R1 and R2 is 1.
94. Refer to the exhibit. A network technician has added router R0 to an existing network that contains router R1. R0 is configured with EIGRP and is connected to R1 via the Fa0/0 interface of each router. After completing an analysis of the network, the technician notices that the routes to the networks that are supported by routers R0 and R1 are not being exchanged. What is a possible cause for this failure?
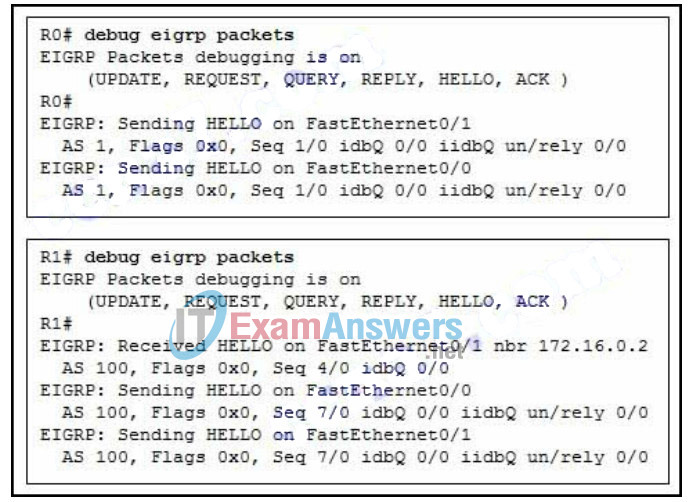
- R0 was configured with the wrong autonomous system number.
- FastEthernet interfaces on R0 are in a shutdown state.
- Interface Fa0/0 on R0 is configured as a passive interface.
- Interface Fa0/0 on R1 is configured as a passive interface.
95. A network administrator is troubleshooting router RA in an EIGRP autonomous system. The administrator needs to obtain the IP addresses of the other routers with which router RA has established adjacencies. It is also important to obtain information of the queue counts on the neighbor routers. What command will do this?
- show ip eigrp interfaces
- show ip eigrp neighbors
- show cdp neighbor details
- show ip eigrp topology all-links
96. Refer to the exhibit. Inter-VLAN communication between VLAN 10, VLAN 20, and VLAN 30 is not successful. What is the problem?
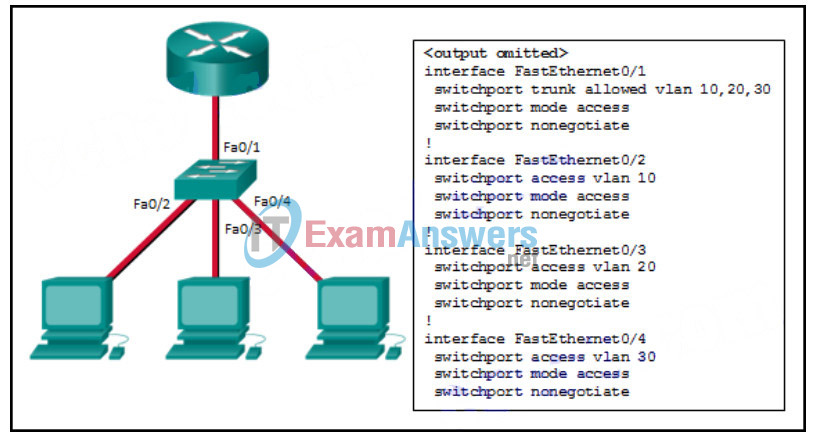
- The access interfaces do not have IP addresses and each should be configured with an IP address.
- The switch interface FastEthernet0/1 is configured as an access interface and should be configured as a trunk interface.
- The switch interface FastEthernet0/1 is configured to not negotiate and should be configured to negotiate.
- The switch interfaces FastEthernet0/2, FastEthernet0/3, and FastEthernet0/4 are configured to not negotiate and should be configured to negotiate.
97. Refer to the exhibit. While planning an upgrade, a network administrator uses the Cisco NetFlow utility to analyze data flow in the current network. What generated the most packets?
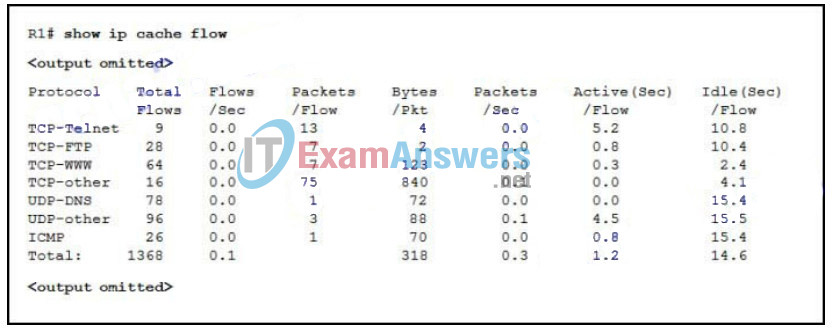
- ICMP
- TCP-Telnet
- TCP-other
- UDP-DNS
- UDP-other
98. What two encryption algorithms are used in IPsec VPNs? (Choose two.)
- DH
- PSK
- IKE
- AES
- 3DES
99. Which three statements describe the building blocks that make up the IPsec protocol framework? (Choose three.)
- IPsec uses encryption algorithms and keys to provide secure transfer of data.
- IPsec uses Diffie-Hellman algorithms to encrypt data that is transferred through the VPN.
- IPsec uses 3DES algorithms to provide the highest level of security for data that is transferred through a VPN.
- IPsec uses secret key cryptography to encrypt messages that are sent through a VPN.
- IPsec uses Diffie-Hellman as a hash algorithm to ensure integrity of data that is transmitted through a VPN.
- IPsec uses ESP to provide confidential transfer of data by encrypting IP packets.
100. Which statement describes cable?
- Delivering services over a cable network requires downstream frequencies in the 50 to 860 MHz range, and upstream frequencies in the 5 to 42 MHz range.
- The cable subscriber must purchase a cable modem termination system (CMTS).
- Each cable subscriber has dedicated upstream and downstream bandwidth.
- Cable subscribers may expect up to 27 Mbps of bandwidth on the upload path.
101. The output of the show ip interface brief command indicates that Serial0 is up but the line protocol is down. What are two possible causes for the line protocol being in the down state? (Choose two.)
- The clock rate is not set on the DTE.
- An incorrect default gateway is set on the router.
- A network is missing from the routing protocol configuration.
- The encapsulation on the Serial0 interface is incorrect.
- Keepalives are not being sent by the remote device.
102. An administrator issued the following commands on router R1:
R1(config)# logging 192.168.10.2 R1(config)# logging trap 5
What conclusion can be drawn from this configuration?
- The only messages that appear on the syslog server are those with severity level of 4 or lower.
- Messages with severity level of 6 or higher appear only on the router console output.
- The only messages that appear on the syslog server are those with severity level of 5.
- Messages with severity level of 5 or lower appear on the router console output and are sent to the syslog server.
103. Fill in the blank.
A spanning-tree network that has all of the switched ports in either a blocking or forwarding state is considered a converged network.
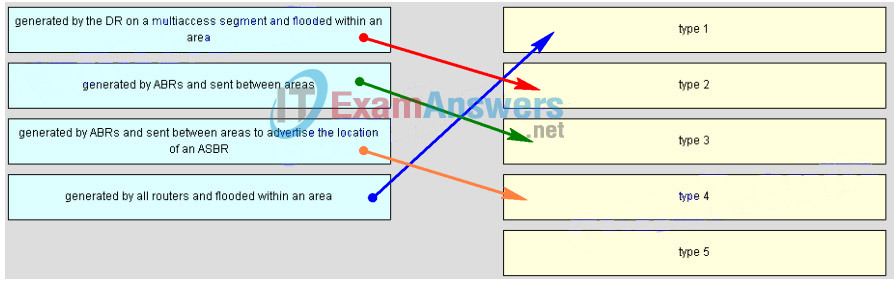
104. Match each description to its corresponding LSA type. (Not all options are used.)

An IT security specialist enables port security on a switch port of a Cisco switch. What is the default violation mode in use until the switch port is configured to use a different violation mode?
-shutdown
-disabled
-protect
-restrict
Added, thanks for sharing!
Which technology supports CHAP authentication over a dialer interface?
GRE
PPPoE **Answer**
eBGP
VPN
Which two issues can cause both runts and giants in Ethernet networks? (Choose two.)
using the incorrect cable type
half-duplex operations
a malfunctioning NIC
electrical interference on serial interfaces
CRC errors
An IT security specialist enables port security on a switch port of a Cisco switch. What is the default violation mode in use until the switch port is configured to use a different violation mode?
1. Disabled
2. Protect
3. Shutdown
4. Restrict
hope you guys could help with ccnp.