1. Refer to the exhibit. Based on the command output shown, what is the status of the EtherChannel?
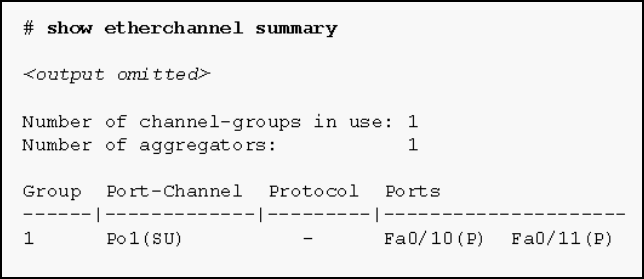
- The EtherChannel is dynamic and is using ports Fa0/10 and Fa0/11 as passive ports.
- The EtherChannel is down as evidenced by the protocol field being empty.
- The EtherChannel is partially functional as indicated by the P flags for the FastEthernet ports.
- The EtherChannel is in use and functional as indicated by the SU and P flags in the command output.*
2. Refer to the exhibit. A network engineer is troubleshooting host connectivity on a LAN that uses a first hop redundancy protocol. Which IPv4 gateway address should be configured on the host?
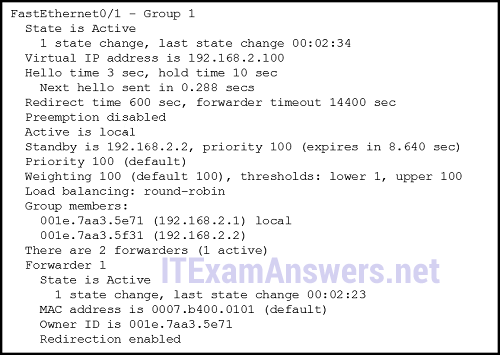
- 192.168.2.0
- 192.168.2.1
- 192.168.2.2
- 192.168.2.100*
3. What is the purpose of HSRP?
- It provides a continuous network connection when a router fails.*
- It prevents a rogue switch from becoming the STP root.
- It prevents malicious hosts from connecting to trunk ports.
- It enables an access port to immediately transition to the forwarding state.
4. Refer to the exhibit. An EtherChannel was configured between switches S1 and S2, but the interfaces do not form an EtherChannel. What is the problem?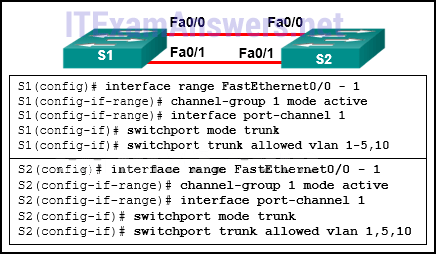
- The switch ports have to be configured as access ports with each port having a VLAN assigned.
- The interface port-channel number has to be different on each switch.
- The switch ports were not configured with speed and duplex mode.
- The EtherChannel was not configured with the same allowed range of VLANs on each interface.*
5. What is an advantage of using LACP?
- increases redundancy to Layer 3 devicesdecreases the amount of configuration that is needed on a switch for EtherChannel
- allows automatic formation of EtherChannel links*
- provides a simulated environment for testing link aggregation
- decreases the chance of a spanning-tree loop
6. What is a requirement to configure a trunking EtherChannel between two switches?
- The participating interfaces must be assigned the same VLAN number on both switches.
- The participating interfaces must be on the same module on a switch.
- The participating interfaces must be physically contiguous on a switch.
- The allowed range of VLANs must be the same on both switches.*
7. A network administrator would like to ensure that router R1 is always elected the active router for an HSRP group. Which set of commands would ensure the required results?
- R1(config-if)# ip address 192.168.1.250 255.255.255.0
R1(config-if)# standby 1 ip 192.168.1.1
R1(config-if)# no shutdown - R1(config-if)# ip address 192.168.1.100 255.255.255.0
R1(config-if)# standby 1 ip 192.168.1.1
R1(config-if)# standby 1 priority 255
R1(config-if)# standby 1 preempt
R1(config-if)# no shutdown* - R1(config-if)# ip address 192.168.1.100 255.255.255.0
R1(config-if)# standby 1 ip 192.168.1.1
R1(config-if)# standby 1 priority 1
R1(config-if)# no shutdown - R1(config-if)# ip address 192.168.1.100 255.255.255.0
R1(config-if)# standby 1 ip 192.168.1.1
R1(config-if)# standby 1 priority 150
R1(config-if)# no shutdown
8. Refer to the exhibit. A network administrator configured routers R1 and R2 as part of HSRP group 1. After the routers have been reloaded, a user on Host1 complained of lack of connectivity to the Internet The network administrator issued the show standby brief command on both routers to verify the HSRP operations. In addition, the administrator observed the ARP table on Host1. Which entry should be seen in the ARP table on Host1 in order to gain connectivity to the Internet?
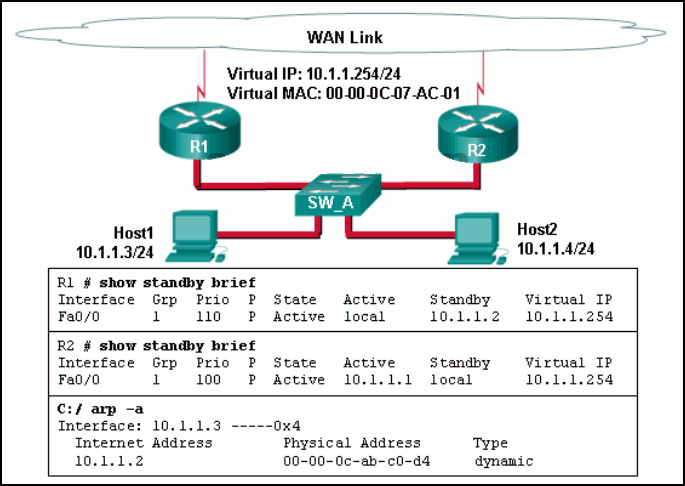
- the virtual IP address of the HSRP group 1 and the MAC address of R1
- the virtual IP address of the HSRP group 1 and the MAC address of R2
- the virtual IP address and the virtual MAC address for the HSRP group 1*
- the IP address and the MAC address of R1
9. Fill in the blank. In FHRP operation, two or more routers are represented as a single virtual router.
10. What is a best practice to use before beginning an EtherChannel implementation?
- Enable each of the affected interfaces.
- Assign affected interfaces to the management VLAN.
- Shut down each of the affected interfaces.*
- Assign affected interfaces to VLAN 1.
- Assign affected interfaces to an unused VLAN.
11. Which statement describes an EtherChannel implementation?
- EtherChannel operates only at Layer 2.
- A trunked port can be part of an EtherChannel bundle.*
- EtherChannel can support up to a maximum of ten separate links.
- PAgP cannot be used in conjunction with EtherChannel.
12. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What are two reasons why the ping messages that are issued from Laptop0 towards Laptop1 are failing? (Choose two.)
- The two interfaces on each of the switches belong to different VLANs.*
- The interface VLAN 1 is shut down on both switches.
- The channel group mode is not set correctly on the switches.
- The wrong cable types are connecting the two switches.
- The channel group should be configured as a trunk on each switch.*
13. Refer to the exhibit. A network administrator issued the show etherchannel summary command on the switch S1. What conclusion can be drawn?
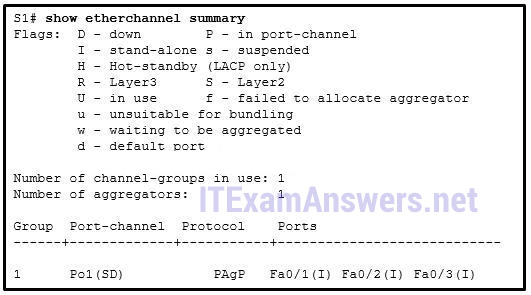
- The EtherChannel is not functional.*
- The EtherChannel is suspended.
- FastEthernet ports Fa0/1, Fa0/2, and Fa0/3 do not join the EtherChannel.
- The port aggregation protocol PAgP is misconfigured.
14. Which PAgP mode combination will establish an EtherChannel?
- switch 1 set to desirable; switch 2 set to desirable.*
- switch 1 set to auto; switch 2 set to auto.
- switch 1 set to on; switch 2 set to desirable.
- switch 1 set to auto; switch 2 set to on.
15. Refer to the exhibit. What statement is true about the output of the show standby command?
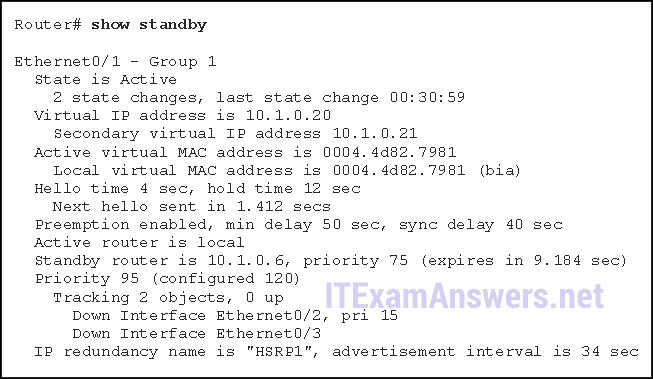
- The current priority of this router is 120.
- This router is tracking two properly operating interfaces.
- This router is in the HSRP down state because its tracked interfaces are down.
- The router is currently forwarding packets.*
16. Which three options must match in order to establish an EtherChannel between two directly connected switches? (Choose three.)
- duplex settings of the interfaces that are used for EtherChannel*
- port security settings on the interfaces that used for EtherChannel
- VLAN memberships of the interfaces that are used for EtherChannel*
- speed of the interfaces that are used for EtherChannel*
- domain names on the switches
- port numbers that are used for the EtherChannel
17. Which two protocols are used to implement EtherChannel? (Choose two.)
- Link Aggregation Control Protocol*
- Spanning Tree Protocol
- Port Aggregation Protocol*
- Cisco Discovery Protocol
- Rapid Spanning Tree Protocol
18. In FHRP terminology, what represents a set of routers that present the illusion of a single router to hosts?
- virtual router*
- forwarding router
- standby router
- default gateway
19. Which command must be used on SW2 to enable this EtherChannel?
- SW2(config-if-range)# channel-group 1 mode desirable*
- SW2(config-if-range)# channel-group 1 mode auto
- SW2(config-if-range)# channel-group 1 mode passive
- SW2(config-if-range)# channel-group 1 mode active
20. An EtherChannel link using LACP was formed between two switches, S1 and S2. While verifying the configuration, which mode combination could be utilized on both switches?
- S1-on and S2-active
- S1-passive and S2-passive
- S1-on and S2-passive
- S1-passive and S2-active*
21. Which statement describes a characteristic of EtherChannel?
- It can bundle mixed types of 100 Mb/s and 1Gb/s Ethernet links.
- It consists of multiple parallel links between a switch and a router.
- It can combine up to a maximum of 4 physical links.
- It is made by combining multiple physical links that are seen as one link between two switches.*
22. Refer to the exhibit. Which switching technology would allow each access layer switch link to be aggregated to provide more bandwidth between each Layer 2 switch and the Layer 3 switch?

- HSRP
- EtherChannel*
- trunking
- PortFast
23. Which statement is true regarding the use of PAgP to create EtherChannels?
- It requires more physical links than LACP does.
- It mandates that an even number of ports (2, 4, 6, etc.) be used for aggregation.
- It is Cisco proprietary.*
- It increases the number of ports that are participating in spanning tree.
- It requires full duplex.
24. Refer to the exhibit. A network administrator has decided that an EtherChannel between ports 0/1 and 0/2 on switches S1 and S2 would help performance. After making the configuration, the administrator notices no performance gain. Based on the output that is shown, what two possible assumptions could a network administrator make? (Choose two.)
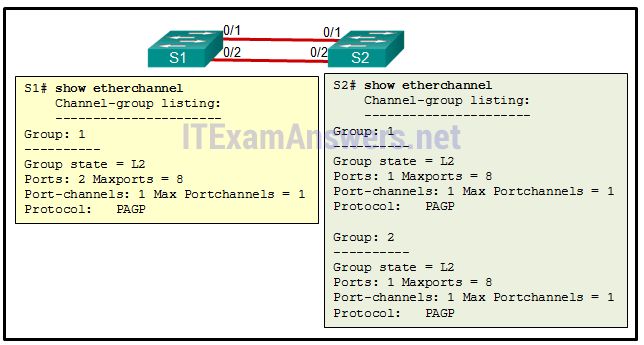
- Switch S2 did not use a compatible EtherChannel mode.
- The EtherChannel bundle is working.
- One of the ports on S2 was not configured correctly.*
- LACP and PAgP were both used to form the EtherChannel.
- The EtherChannel bundle is not working.*
- Switch S2 must be configured so that the maximum number of port channels is increased.
25. Which nonproprietary protocol provides router redundancy for a group of routers which support IPv4 LANs?
- GLBP
- SLB
- VRRPv2*
- HSRP
26. A network administrator is configuring an EtherChannel link between switches SW1 and SW2 by using the command SW1(config-if-range)# channel-group 1 mode passive. Which command must be used on SW2 to enable this EtherChannel?
- SW2(config-if-range)# channel-group 1 mode desirable
- SW2(config-if-range)# channel-group 1 mode auto
- SW2(config-if-range)# channel-group 1 mode passive
- SW2(config-if-range)# channel-group 1 mode active*
27. Match the description to the correct command. (Not all options are used.)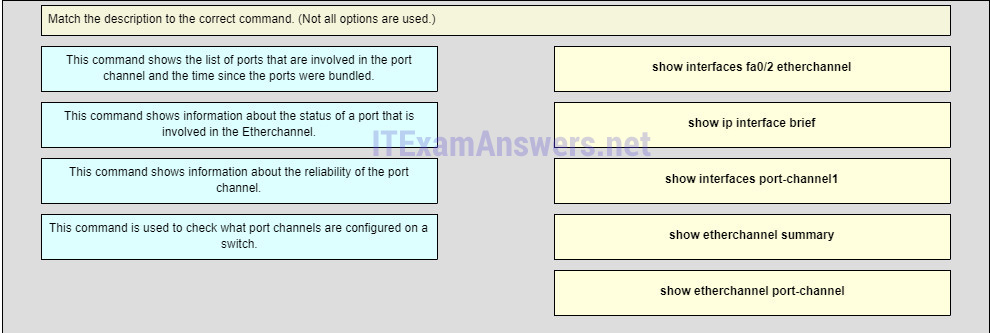
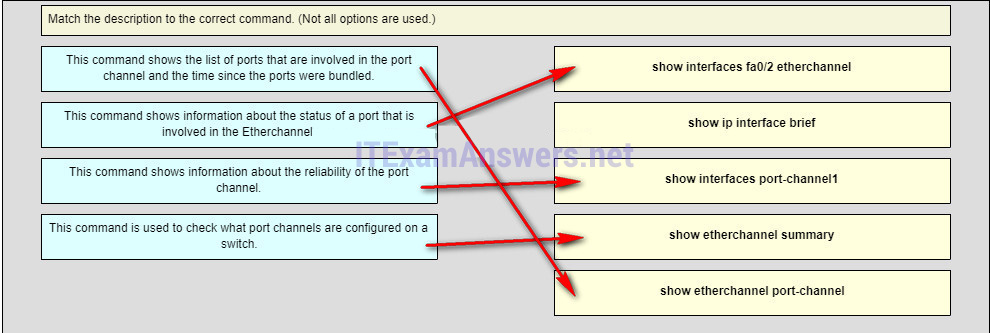
Older Version
28. Which IEEE wireless standard is known as WiGig and operates using a tri-band solution in the 2.4, 5, and 60 GHz ranges?
- 802.11g
- 802.11n
- 802.11ac
- 802.11ad*
29. Which two roles are typically performed by a wireless router that is used in a home or small business? (Choose two.)
- repeater
- access point*
- WLAN controller
- Ethernet switch*
- RADIUS authentication server
30. A supervisor needs wireless access in the construction office during the construction of a new building. The construction office is in the new building and directly across the road from headquarters. What could be used to satisfy this requirement of needing a narrow area of coverage?
- multiple MIMO antennas
- omnidirectional
- rubber duck
- Yagi*
31. A student uses a laptop to upload an assignment to a file server. Which wireless frame type did the laptop send to locate and associate with the campus access point?
- beacon frame
- control frame
- data frame
- management frame*
32. During which stage of establishing connectivity between a WLAN client and an AP does the client learn the MAC address of the AP?
- discovery
- probing
- association*
- encryption
- authentication
33. For which discovery mode will an AP generate the most traffic on a WLAN?
- passive mode*
- open mode
- mixed mode
- active mode
34. What is the purpose of the Distributed Coordination Function in an IEEE 802.11 WLAN environment?
- It allows a client to detect whether or not a channel is clear prior to transmission.*
- It is used in a full-duplex environment to detect collisions.
- It is used to send data over a half-duplex connection.
- It allows the client to change transmission channels.
35. What is an advantage of SSID cloaking?
- It provides free Internet access in public locations where knowing the SSID is of no concern.
- Clients will have to manually identify the SSID to connect to the network.*
- SSIDs are very difficult to discover because APs do not broadcast them.
- It is the best way to secure a wireless network.
36. If three 802.11b access points need to be deployed in close proximity, which three frequency channels should be used? (Choose three.)
- 1*
- 3
- 5
- 6*
- 8
- 11*
37. Which three Wi-Fi standards operate in the 2.4GHz range of frequencies? (Choose three.)
- 802.11a
- 802.11b *
- 802.11g *
- 802.11n*
- 802.11ac
38. An employee connects wirelessly to the company network using a cell phone. The employee then configures the cell phone to act as a wireless access point that will allow new employees to connect to the company network. Which type of security threat best describes this situation?
- cracking
- denial of service
- rogue access point*
- spoofing
39. Which security mode is the least secure choice when a home wireless router is configured?
- WPA
- WPA2
- WEP*
- WPA2-Personal
40. Which parameter is commonly used to identify a wireless network name when a home wireless AP is being configured?
- ad hoc
- BESS
- ESS
- SSID*
41. A company has recently implemented an 802.11n wireless network. Some users are complaining that the wireless network is too slow. Which solution is the best method to enhance the performance of the wireless network?
- Replace the wireless NICs on the computers that are experiencing slow connections.
- Split the traffic between the 2.4 GHz and 5 GHz frequency bands.*
- Disable DHCP on the access point and assign static addresses to the wireless clients.
- Upgrade the firmware on the wireless access point.
42. Fill in the blank. Do not use abbreviations.
Ad hoc wireless topologies sometimes can use a feature called tethering to enable a smartphone to create a personal hotspot.
43. Fill in the blank.
A network administrator discovers a rogue AP in the network. The rogue AP is capturing traffic and then forwarding it on to the legitimate AP. This type of attack is known as a man-in -the -middle attack.
44. Fill in the blank. Use the acronym.
Which encryption protocol is used by the WPA2 shared key authentication technique? AES*
45. Which organization certifies vendors for adherence to the 802.11 standards to improve interoperability of 802.11 products?
- FCC
- IEEE
- ITU-R
- Wi-Fi Alliance*
46. What type of wireless antenna is best suited for providing coverage in large open spaces, such as hallways or large conference rooms?
- omnidirectional*
- directional
- Yagi
- dish
47. Which feature of 802.11n wireless access points allows them to transmit data at faster speeds than previous versions of 802.11 Wi-Fi standards did?
- SPS
- WPS
- MIMO*
- MITM
48. What is a difference between Cisco APs that operate in a home environment and Cisco APs that operate in a corporate environment?
- Autonomous APs are used only in the home environment, and they incorporate the functions of a router, switch, and AP into one device.
- Controller-based APs are used in the corporate environment, and they are server-dependent devices that require an initial configuration to operate.
- Cisco corporate APs do not support PoE.
- Some corporate AP models can operate in either autonomous mode or controller-based mode.*
49. Which type of wireless topology is created when two or more Basic Service Sets are interconnected by Ethernet?
- IBISS
- BSS
- WiFi Direct
- ESS*
- ad hoc WLAN
50. Which type of management frame may regularly be broadcast by an AP?
- beacon*
- probe request
- authentication
- probe response
51. Which statement defines the control frame operation between two stations?
- A station sends an RTS frame as the first step in a three-way handshake that is required before sending data frames.
- A station responds to an RTS frame with an ACK frame, thus providing permission for the requesting station to send a data frame.
- If the sending station does not receive an ACK frame within a predetermined period of time, the sending station will drop the connection.
- After receiving a data frame, the receiving station will send an ACK frame to the sending station if no errors are found.*
52. A administrator wishes to extend the range of the existing IEEE 802.11n network without changing the AP. What can the administrator do to accomplish this?
- Upgrade the firmware on the AP.
- Split the wireless traffic between the 802.11n 2.4 GHz band and the 5 GHz band.
- Deploy a Wi-Fi Range Extender.*
- Change to WPA2 authentication.
53. Launch PT Hide and Save PT. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What is the SSID of the connected network and which message is displayed in the browser window?
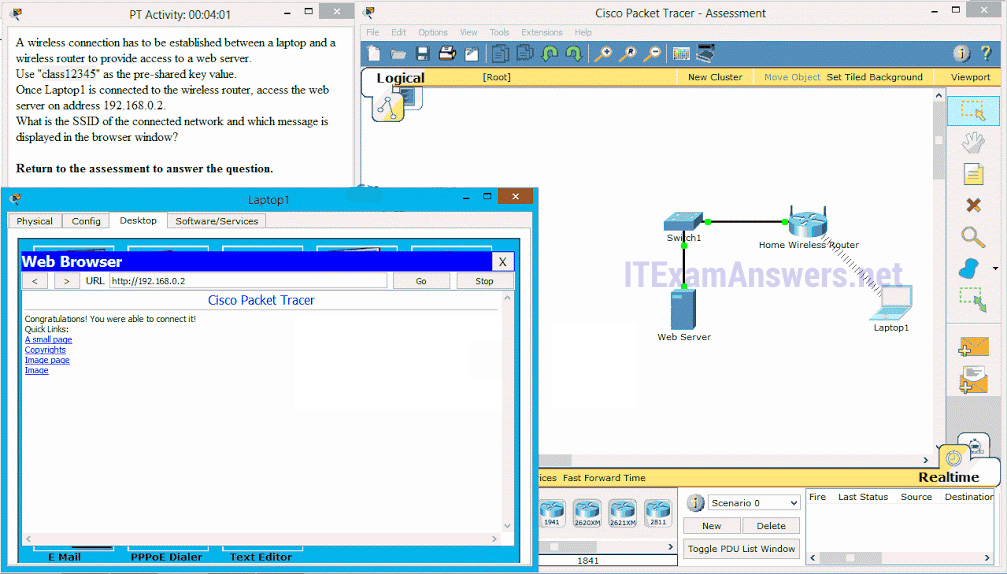
- SSID: Home-Network
Message: Well done! - SSID: Home-Network
Message: Good job! - SSID: Home-Net
Message:Congratulations! You did it! - SSID: Home-Net
Message:Congratulations! You were able to connect it!*
54. Match the type of attack to its description. (Not all options are used.)
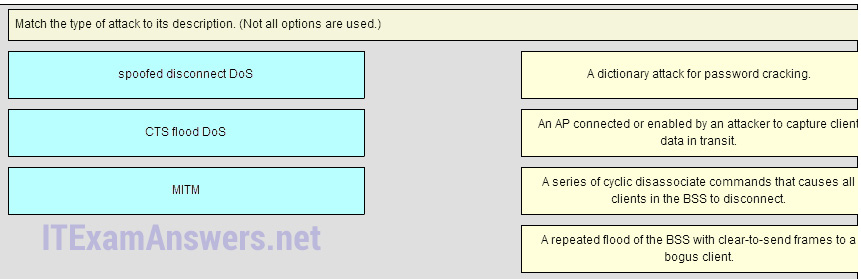
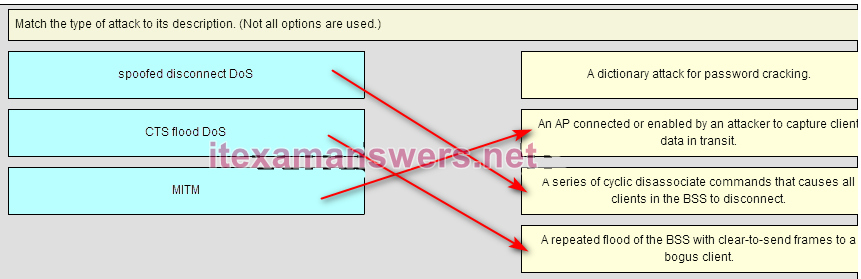
Place the options in the following order:
– not scored –
MITM -> AN AP connected or enabled by an attacker to capture client data in transit.
spoofed disconnct DoS -> A series of cyclic dissasociate commands that causes all clients in the BSS to disconnect.
CTS flood DoS -> A repeated flood of the BSS with clear-to-send frames to a bogus client.
55. Place the following actions in the order in which they occur in a shared key authentication process. (Not all options are used.)
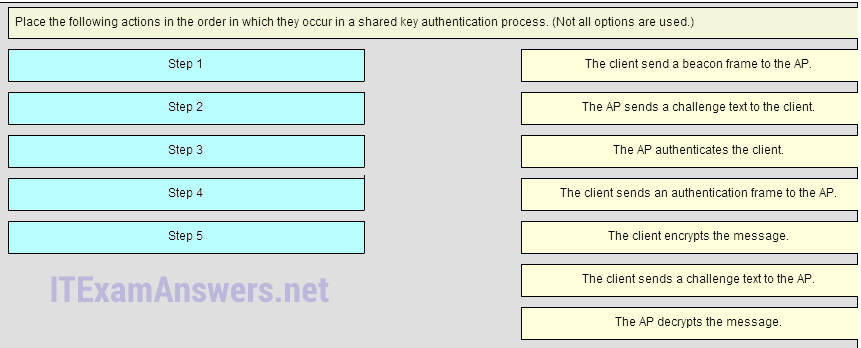
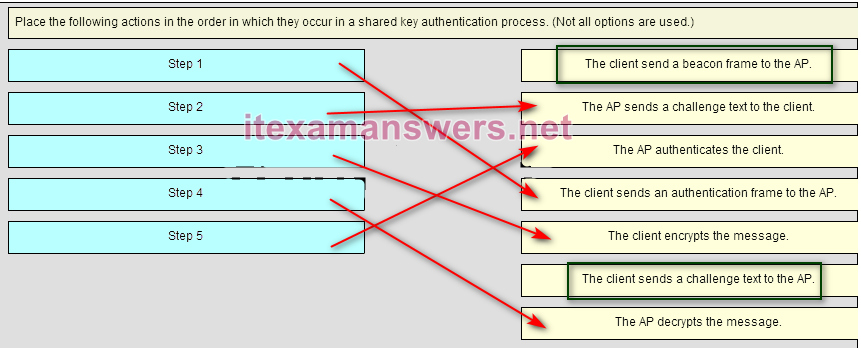
Place the options in the following order:
– not scored –
Step 2 -> The AP send a challenge text to the client.
Step 5 -> The AP authenticates the client.
Step 1 -> The client sends an authentication frame to the AP.
Step 3 -> The client encrypts the message.
– not scored –
Step 4 -> The AP decypts the message.
56. A WLAN user wants to allocate an optimal amount of bandwidth to a specific online game. What is a Linksys Smart Wi-Fi tool that will allow the user to do this?
- Widgets
- Speed Test
- Media Prioritization*
- Bandwidth Prioritization
Download PDF File below:

An EtherChannel link using LACP was formed between two switches, S1 and S2. While verifying the configuration, which mode combination could be utilized on both switches?
A network administrator is configuring an EtherChannel link between switches SW1 and SW2 by using the command SW1(config-if-range)# channel-group 1 mode passive . Which command must be used on SW2 to enable this EtherChannel?
SW2(config-if-range)# channel-group 1 mode active
SW2(config-if-range)# channel-group 1 mode desirable
SW2(config-if-range)# channel-group 1 mode auto
SW2(config-if-range)# channel-group 1 mode passive
active
thank you so much dear
I have tried the drying serums before and they’re superior specially as problems, but my
skin is not indeed wet because location forever after.