1. How many bits are in an IPv4 address?
- 32
- 64
- 128
- 256
2. Which two parts are components of an IPv4 address? (Choose two.)
- subnet portion
- network portion
- logical portion
- host portion
- physical portion
- broadcast portion
3. What does the IP address 172.17.4.250/24 represent?
- network address
- multicast address
- host address
- broadcast address
4. What is the purpose of the subnet mask in conjunction with an IP address?
- to uniquely identify a host on a network
- to identify whether the address is public or private
- to determine the subnet to which the host belongs
- to mask the IP address to outsiders
5. What subnet mask is represented by the slash notation /20?
- 255.255.255.248
- 255.255.224.0
- 255.255.240.0
- 255.255.255.0
- 255.255.255.192
6. A message is sent to all hosts on a remote network. Which type of message is it?
- limited broadcast
- multicast
- directed broadcast
- unicast
7. What are three characteristics of multicast transmission? (Choose three.)
- The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.
- A single packet can be sent to a group of hosts.
- Multicast transmission can be used by routers to exchange routing information.
- The range of 224.0.0.0 to 224.0.0.255 is reserved to reach multicast groups on a local network.
- Computers use multicast transmission to request IPv4 addresses.
- Multicast messages map lower layer addresses to upper layer addresses.
8. Which three IP addresses are private ? (Choose three.)
- 10.1.1.1
- 172.32.5.2
- 192.167.10.10
- 172.16.4.4
- 192.168.5.5
- 224.6.6.6
9. Which two IPv4 to IPv6 transition techniques manage the interconnection of IPv6 domains? (Choose two.)
- trunking
- dual stack
- encapsulation
- tunneling
- multiplexing
10. Which of these addresses is the shortest abbreviation for the IP address:
3FFE:1044:0000:0000:00AB:0000:0000:0057?
- 3FFE:1044::AB::57
- 3FFE:1044::00AB::0057
- 3FFE:1044:0:0:AB::57
- 3FFE:1044:0:0:00AB::0057
- 3FFE:1044:0000:0000:00AB::57
- 3FFE:1044:0000:0000:00AB::0057
11. What type of address is automatically assigned to an interface when IPv6 is enabled on that interface?
- global unicast
- link-local
- loopback
- unique local
12. What are two types of IPv6 unicast addresses? (Choose two.)
- multicast
- loopback
- link-local
- anycast
- broadcast
13. What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- a subnet ID that is used to identify networks inside of the local enterprise site
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- an interface ID that is used to identify the local host on the network
14. An administrator wants to configure hosts to automatically assign IPv6 addresses to themselves by the use of Router Advertisement messages, but also to obtain the DNS server address from a DHCPv6 server. Which address assignment method should be configured?
- SLAAC
- stateless DHCPv6
- stateful DHCPv6
- RA and EUI-64
15. Which protocol supports Stateless Address Autoconfiguration (SLAAC) for dynamic assignment of IPv6 addresses to a host?
- ARPv6
- DHCPv6
- ICMPv6
- UDP
16. Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source
- the destination device is reachable through the network
- the average time it takes each router in the path between source and destination to respond
17. What is the purpose of ICMP messages?
- to inform routers about network topology changes
- to ensure the delivery of an IP packet
- to provide feedback of IP packet transmissions
- to monitor the process of a domain name to IP address resolution
18. What is indicated by a successful ping to the ::1 IPv6 address?
- The host is cabled properly.
- The default gateway address is correctly configured.
- All hosts on the local link are available.
- The link-local address is correctly configured.
- IP is properly installed on the host.
19. A user is executing a tracert to a remote device. At what point would a router, which is in the path to the destination device, stop forwarding the packet?
- when the router receives an ICMP Time Exceeded message
- when the RTT value reaches zero
- when the host responds with an ICMP Echo Reply message
- when the value in the TTL field reaches zero
- when the values of both the Echo Request and Echo Reply messages reach zero
20. What is the binary equivalent of the decimal number 232?
- 11101000
- 11000110
- 10011000
- 11110010
21. What is the decimal equivalent of the binary number 10010101?
- 149
- 157
- 168
- 192
22. What field content is used by ICMPv6 to determine that a packet has expired?
- TTL field
- CRC field
- Hop Limit field
- Time Exceeded field
23. Fill in the blank.
The decimal equivalent of the binary number 10010101 is 149
24. Fill in the blank.
The binary equivalent of the decimal number 232 is 11101000
25. Fill in the blank.
What is the decimal equivalent of the hex number 0x3F? 63
26. Match each description with an appropriate IP address. (Not all options are used.)
Question
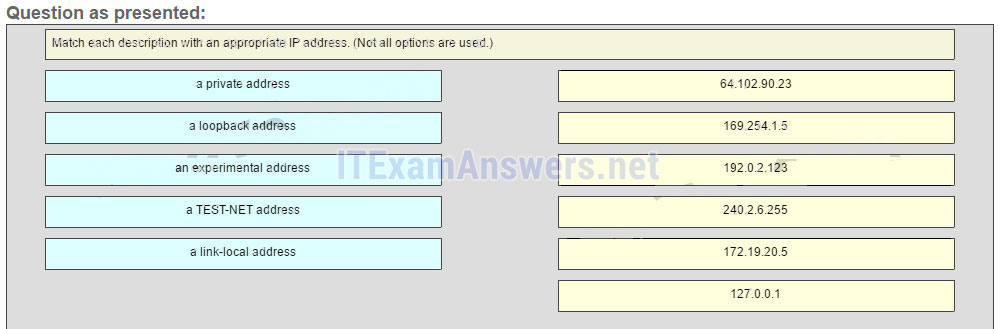
Answer
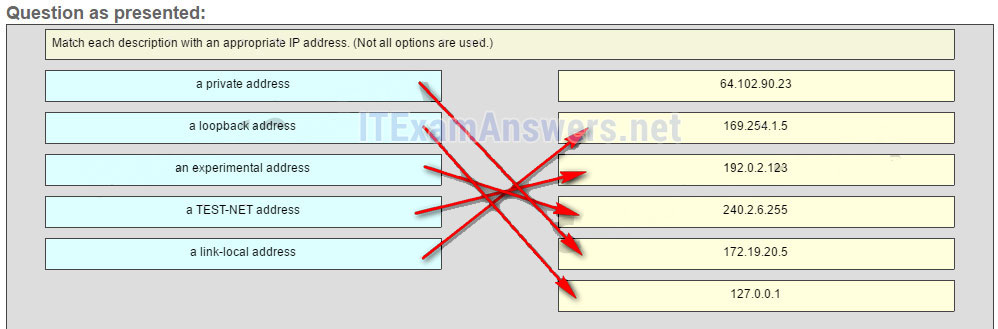
169.254.1.5 -> a link-local address
192.0.2.123 -> a TEST-NET address
240.2.6.255 -> an experimental address
172.19.20.5 -> a private address
127.0.0.1 -> a loopback address
Older Versions
27. What is a socket?
- the combination of the source and destination IP address and source and destination Ethernet address
- the combination of a source IP address and port number or a destination IP address and port number
- the combination of the source and destination sequence and acknowledgment numbers
- the combination of the source and destination sequence numbers and port numbers
28. A host device needs to send a large video file across the network while providing data communication to other users. Which feature will allow different communication streams to occur at the same time, without having a single data stream using all available bandwidth?
- window size
- multiplexing
- port numbers
- acknowledgments
29. A host device sends a data packet to a web server via the HTTP protocol. What is used by the transport layer to pass the data stream to the proper application on the server?
- sequence number
- acknowledgment
- source port number
- destination port number
30. What is a beneficial feature of the UDP transport protocol?
- acknowledgment of received data
- fewer delays in transmission
- tracking of data segments using sequence numbers
- the ability to retransmit lost data
31. Which scenario describes a function provided by the transport layer?
- A student is using a classroom VoIP phone to call home. The unique identifier burned into the phone is a transport layer address used to contact another network device on the same network.
- A student is playing a short web-based movie with sound. The movie and sound are encoded within the transport layer header.
- A student has two web browser windows open in order to access two web sites. The transport layer ensures the correct web page is delivered to the correct browser window.
- A corporate worker is accessing a web server located on a corporate network. The transport layer formats the screen so the web page appears properly no matter what device is being used to view the web site.
32. What is the complete range of TCP and UDP well-known ports?
- 0 to 255
- 0 to 1023
- 256 – 1023
- 1024 – 49151
33. What does a client application select for a TCP or UDP source port number?
- a random value in the well-known port range
- a random value in the range of the registered ports
- a predefined value in the well-known port range
- a predefined value in the range of the registered ports
34. Compared to UDP, what factor causes additional network overhead for TCP communication?
- network traffic that is caused by retransmissions
- the identification of applications based on destination port numbers
- the encapsulation into IP packets
- the checksum error detection
35. Which transport layer feature is used to guarantee session establishment?
- UDP ACK flag
- TCP 3-way handshake
- UDP sequence number
- TCP port number
36. Which two flags in the TCP header are used in a TCP three-way handshake to establish connectivity between two network devices? (Choose two.)
- ACK
- FIN
- PSH
- RST
- SYN
- URG
37. Which factor determines TCP window size?
- the amount of data to be transmitted
- the number of services included in the TCP segment
- the amount of data the destination can process at one time
- the amount of data the source is capable of sending at one time
38. During a TCP session, a destination device sends an acknowledgment number to the source device. What does the acknowledgment number represent?
- the total number of bytes that have been received
- one number more than the sequence number
- the next byte that the destination expects to receive
- the last sequence number that was sent by the source
39. A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the server send before it requires an acknowledgment from the PC?
- 1 segment
- 10 segments
- 100 segments
- 1000 segments
40. Which two TCP header fields are used to confirm receipt of data?
- FIN flag
- SYN flag
- checksum
- sequence number
- acknowledgment number
41. What happens if the first packet of a TFTP transfer is lost?
- The client will wait indefinitely for the reply.
- The TFTP application will retry the request if a reply is not received.
- The next-hop router or the default gateway will provide a reply with an error code.
- The transport layer will retry the query if a reply is not received.
42. What does a client do when it has UDP datagrams to send?
- It just sends the datagrams.
- It queries the server to see if it is ready to receive data.
- It sends a simplified three-way handshake to the server.
- It sends to the server a segment with the SYN flag set to synchronize the conversation.
43. A technician wishes to use TFTP to transfer a large file from a file server to a remote router. Which statement is correct about this scenario?
- The file is segmented and then reassembled in the correct order by TCP.
- The file is segmented and then reassembled in the correct order at the destination, if necessary, by the upper-layer protocol.
- The file is not segmented, because UDP is the transport layer protocol that is used by TFTP.
- Large files must be sent by FTP not TFTP.
44. Fill in the blank.
During a TCP session, the SYN flag is used by the client to request communication with the server.
45. Fill in the blank using a number.
A total of 4 messages are exchanged during the TCP session termination process between the client and the server.
46. Refer to the exhibit. Consider a datagram that originates on the PC and that is destined for the web server. Match the IP addresses and port numbers that are in that datagram to the description. (Not all options are used.)
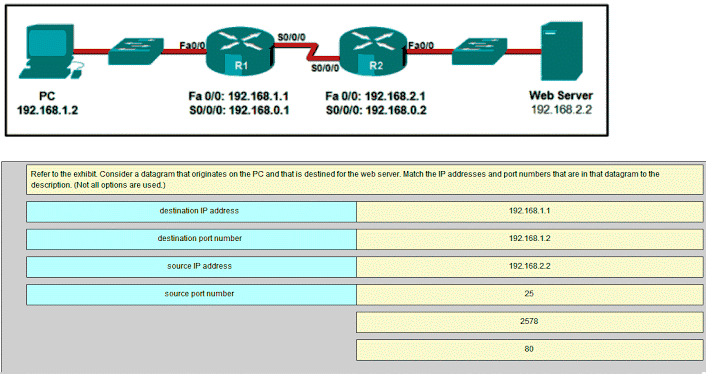
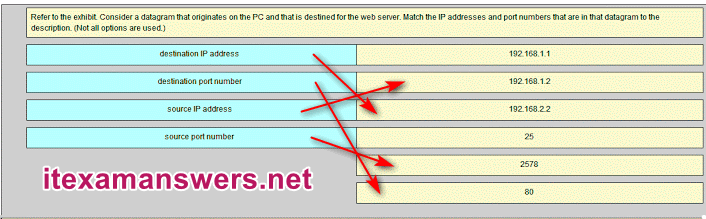
192.168.1.2 -> source IP address
192.168.2.2 -> destination IP address
2578 -> source port number
80 -> destination port number
47. Match the characteristic to the protocol category. (Not all options are used.)
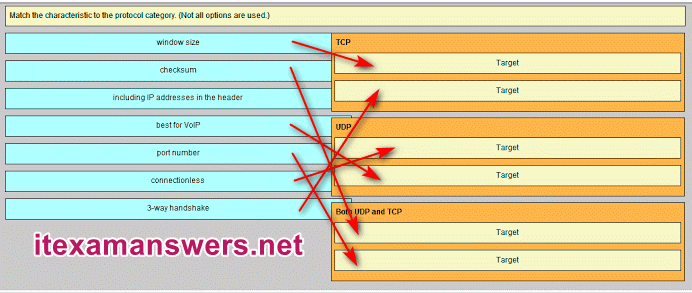
TCP -> window size
TCP -> 3-way handshake
UDP -> connectionless
UDP -> best for VoIP
Both UDP and TCP -> checksum
Both UDP and TCP -> port number
48. Match each application to its connectionless or connection-oriented protocol.
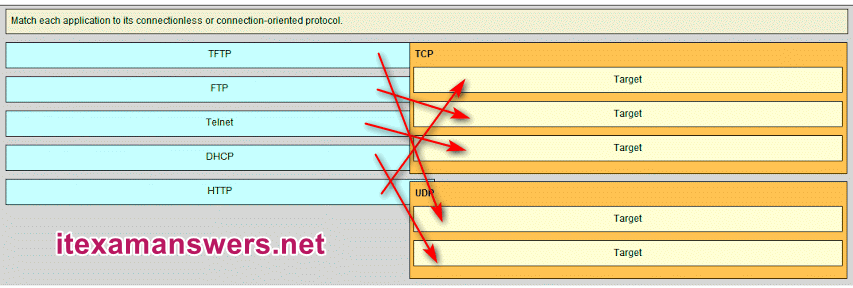
TCP -> HTTP
TCP -> FTP
TCP -> TELNET
UDP -> TFTP
UDP -> DHCP

Tank u
What is the decimal equivalent of the hex number 0x3F?
63
77
87
93
thanks
how can i get these solutions in PDF of all chaptes.
C’est suffisant de cliquer sur “j’aime” pour la page ccnav6.com
thank uuu
hi ♥♥♥