1. The buffers for packet processing and the running configuration file are temporarily stored in which type of router memory?
- flash
- NVRAM
- RAM
- ROM
2. How does implementing STP allow for a scalable network design?
- It eliminates Layer 2istic of a defaul loops from redundant links.
- It provides failover services when duplicate network equipment is used.
- It prevents local traffic from propagating to other parts of the network.
- It filters broadcasts and other undesirable traffic from the network.
3. A home user is looking for an ISP connection that provides high speed digital transmission over regular phone lines. What ISP connection type should be used?
- DSL
- dial-up
- satellite
- cell modem
- cable modem
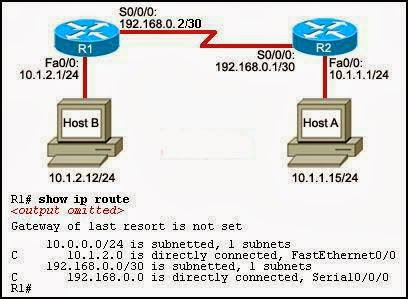
4. What is a characteristic of a default static route?
- It uses a single network address to send multiple static routes to one destination address.
- It backs up a route already discovered by a dynamic routing protocol.
- It identifies the gateway IP address to which the router sends all IP packets for which it does not have a learned or static route.
- It is configured with a higher administrative distance than is the original dynamic routing protocol.
5. Which three pairs of trunking modes will establish a functional trunk link between two Cisco switches? (Choose three.)
- dynamic desirable – dynamic auto
- dynamic auto – dynamic auto
- access – trunk
- dynamic desirable – dynamic desirable
- dynamic desirable – trunk
- access – dynamic auto
6. On which switch interface would an administrator configure an IP address so that the switch can be managed remotely?
- FastEthernet0/1
- VLAN 1
- vty 0
- console 0
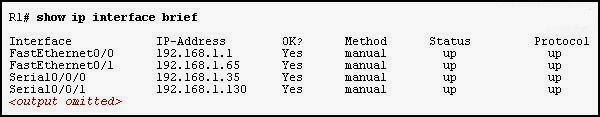
7. Which statement describes a route that has been learned dynamically?
- It is identified by the prefix C in the routing table.
- It has an administrative distance of 1.
- It is automatically updated and maintained by routing protocols.
- It is unaffected by changes in the topology of the network.
8. Refer to the exhibit. Which switch will be the root bridge after the election process is complete?
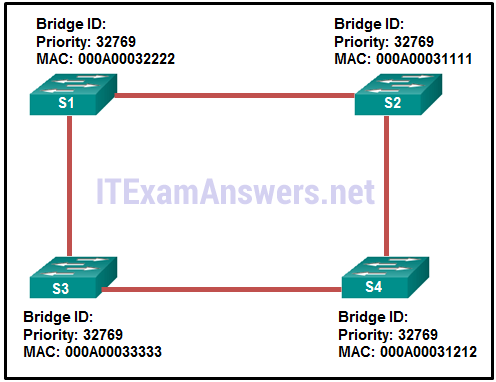
- S1
- S2
- S3
- S4
9. What three application layer protocols are part of the TCP/IP protocol suite? (Choose three.)
- DNS
- PPP
- ARP
- NAT
- FTP
- DHCP
10. In addition to the cable length, what two factors could interfere with the communication carried over UTP cables? (Choose two.)
- bandwidth
- electromagnetic interference
- size of the network
- crosstalk
- signal modulation technique
11. Which information does a switch use to keep the MAC address table information current?
- the source MAC address and the incoming port
- the source and destination MAC addresses and the incoming port
- the source MAC address and the outgoing port
- the destination MAC address and the outgoing port
- the source and destination MAC addresses and the outgoing port
- the destination MAC address and the incoming port
12. A network engineer has been tasked with connecting two large autonomous systems (AS) together over the Internet. Which routing protocol should be selected?
- IS-IS
- EIGRP
- OSPFv2
- BGP
13. What important information is examined in the Ethernet frame header by a Layer 2 device in order to forward the data onward?
- source MAC address
- source IP address
- destination MAC address
- destination IP address
- Ethernet type
14. What are two reasons to implement passive interfaces in the EIGRP configuration of a Cisco router? (Choose two.)
- to provide increased network security
- to shut down unused interfaces
- to exclude interfaces from load balancing
- to avoid unnecessary update traffic
- to mitigate attacks coming from the interfaces
15. Which two functions are primary functions of a router? (Choose two.)
- packet forwarding
- flow control
- microsegmentation
- path selection
- domain name resolution
16. Which two devices allow hosts on different VLANs to communicate with each other? (Choose two.)
- router
- Layer 3 switch
- repeater
- Layer 2 switch
- hub
17. An EIGRP router loses the route to a network. Its topology table contains two feasible successors to the same network. What action will the router take?
- The DUAL algorithm is recomputed to find an alternate route.
- The router uses the default route.
- The router will query neighbors for an alternate route.
- The best alternative backup route is immediately inserted into the routing table.
18. What three blocks of addresses are defined by RFC 1918 for private network use? (Choose three.)
- 192.168.0.0/16
- 169.254.0.0/16
- 239.0.0.0/8
- 172.16.0.0/12
- 10.0.0.0/8
- 100.64.0.0/14
19. Which two pieces of information are required when creating a standard access control list? (Choose two.)
- destination address and wildcard mask
- access list number between 1 and 99
- access list number between 100 and 199
- source address and wildcard mask
- subnet mask and wildcard mask
20. Question as presented:
21. Which criterion is preferred by the router to choose a router ID?
- the router-id rid command
- the IP address of the highest configured loopback interface on the router
- the IP address of the highest active interface on the router
- the IP address of the highest active OSPF-enabled interface
22. A network administrator is entering the command ipv6 unicast-routing to start configuring DHCPv6 operation on a router. Which statement describes the function of this command?
- It is required to configure stateless DHCPv6 server on the router.
- It is required to configure stateful DHCPv6 server on the router.
- It is required for sending ICMPv6 RA messages.
- It is required for enabling DNS service in DHCPv6 configurations.
23. What three services are provided by the transport layer? (Choose three.)
- encryption of data
- path determination
- bit transmission
- flow control
- error recovery
- connection establishment
- data representation
24. Which TCP/IP model layer is closest to the end user?
- internet
- transport
- application
- network access
25. When applied to a router, which command would help mitigate brute-force password attacks against the router?
- service password-encryption
- login block-for 60 attempts 5 within 60
- exec-timeout 30
- banner motd $Max failed logins = 5$
26. Which circumstance would result in an enterprise deciding to implement a corporate WAN?
- when its employees become distributed across many branch locations
- when the enterprise decides to secure its corporate LAN
- when the network will span multiple buildings
- when the number of employees exceeds the capacity of the LAN
27. A corporation is searching for an easy and low cost solution to provide teleworkers with a secure connection to headquarters. Which solution should be selected?
- leased line connection
- site-to-site VPN over the Internet
- dial-up connection
- remote access VPN over the Internet
28. Which three statements are true about PPP? (Choose three.)
- PPP can only be used between two Cisco devices.
- PPP uses LCPs to agree on format options such as authentication, compression, and error detection.
- PPP carries packets from several network layer protocols in LCPs.
- PPP uses LCPs to establish, configure, and test the data-link connection.
- PPP can use synchronous and asynchronous circuits.
29. A network administrator is configuring a PPP link with the commands:
R1(config-if)# encapsulation ppp
R1(config-if)# ppp quality 70
What is the effect of these commands?
- The NCP will send a message to the sending device if the link usage reaches 70 percent.
- The PPP link will not be established if more than 30 percent of options cannot be accepted.
- The LCP establishment phase will not start until the bandwidth reaches 70 percent or more.
- The PPP link will be closed down if the link quality drops below 70 percent.
30. What is the protocol that provides ISPs the ability to send PPP frames over DSL networks?
- CHAP
- ADSL
- LTE
- PPPoE
31. Refer to the exhibit. All routers are successfully running the BGP routing protocol. How many routers must use EBGP in order to share routing information across the autonomous systems?
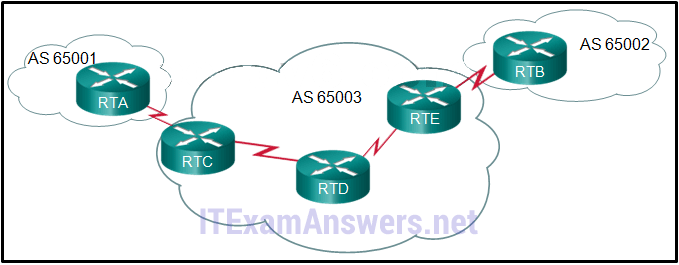
- 2
- 4
- 5
- 3
32. Which three values or sets of values are included when creating an extended access control list entry? (Choose three.)
- destination subnet mask and wildcard mask
- source address and wildcard mask
- source subnet mask and wildcard mask
- destination address and wildcard mask
- access list number between 100 and 199
- default gateway address and wildcard mask
- access list number between 1 and 99
33. Which pillar of the Cisco IoT System allows data to be analyzed and managed at the location where it is generated?
- fog computing
- application enhancement platform
- network connectivity
- data analytics
34. What two protocols are supported on Cisco devices for AAA communications? (Choose two.)
- HSRP
- RADIUS
- VTP
- TACACS+
- LLDP
35. What guideline is generally followed about the placement of extended access control lists?
- They should be placed as close as possible to the source of the traffic to be denied.
- They should be placed as close as possible to the destination of the traffic to be denied.
- They should be placed on the fastest interface available.
- They should be placed on the destination WAN link.
36. What network monitoring tool copies traffic moving through one switch port, and sends the copied traffic to another switch port for analysis?
- SPAN
- SNMP
- syslog
- 802.1X
37. Question as presented:
38. Which type of QoS marking is applied to Ethernet frames?
- DSCP
- CoS
- ToS
- IP precedence
39. Users are reporting longer delays in authentication and in accessing network resources during certain time periods of the week. What kind of information should network engineers check to find out if this situation is part of a normal network behavior?
- debug output and packet captures
- network configuration files
- the network performance baseline
- syslog records and messages
40. Which feature sends simulated data across the network and measures performance between multiple network locations?
- IP SLA
- LLDP
- SPAN
- syslog
Older Version
41. When is a dial-up connection used to connect to an ISP?
- when a cellular telephone provides the service
- when a high-speed connection is provided over a cable TV network
- when a satellite dish is used
- when a regular telephone line is used
42. Why would a network administrator use the tracert utility?
- to determine the active TCP connections on a PC
- to check information about a DNS name in the DNS server
- to identify where a packet was lost or delayed on a network
- to display the IP address, default gateway, and DNS server address for a PC
43. Refer to the exhibit. Which type of IPv6 static route is configured in the exhibit?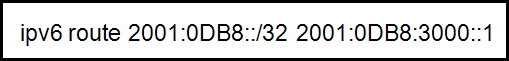
- directly attached static route
- recursive static route
- fully specified static route
- floating static route
44. Which range of link-local addresses can be assigned to an IPv6-enabled interface?
- FEC0::/10
- FDEE::/7
- FEBF::/10
- FF00::/8
45. A high school in New York (school A) is using videoconferencing technology to establish student interactions with another high school (school B) in Russia. The videoconferencing is conducted between two end devices through the Internet. The network administrator of school A configures the end device with the IP address 192.168.25.10. The administrator sends a request for the IP address for the end device in school B and the response is 192.168.25.10. The administrator knows immediately that this IP will not work. Why?
- This is a loopback address.
- This is a link-local address.
- This is a private IP address.
- There is an IP address conflict.
46. What field content is used by ICMPv6 to determine that a packet has expired?
- TTL field
- CRC field
- Hop Limit field
- Time Exceeded field
47. What is the subnet address for the address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15::0
- 2001:DB8:BC15:A::0
- 2001:DB8:BC15:A:1::1
- 2001:DB8:BC15:A:12::0
48. Which two conditions would cause a router to drop a packet? (Choose two.)
- No inbound ACL exists on the interface where the packet enters the router.
- The ACL that is affecting the packet does not contain at least one deny ACE.
- The packet source address does not match the source as permitted in a standard inbound ACE.
- No outbound ACL exists on the interface where the packet exits the router.
- No routing table entry exists for the packet destination, but the packet matches a permitted address in an outbound ACL.
49. Which definition describes a supernet route?
- a route that has a subnet mask equal to that of the classful mask
- a network address with a mask less than the classful mask
- a static route with the address 0.0.0.0/0
- a default route with a local exit interface
50. Refer to the exhibit. Which route or routes will be advertised to the router ISP if autosummarization is enabled?
- 10.0.0.0/8
- 10.1.0.0/16
- 10.1.0.0/28
- 10.1.1.0/24
51. Which information does a switch use to populate the MAC address table?
- the destination MAC address and the incoming port
- the destination MAC address and the outgoing port
- the source and destination MAC addresses and the incoming port
- the source and destination MAC addresses and the outgoing port
- the source MAC address and the incoming port
- the source MAC address and the outgoing port
52. What is the purpose of setting the native VLAN separate from data VLANs?
- The native VLAN is for carrying VLAN management traffic only.
- The security of management frames that are carried in the native VLAN can be enhanced.
- A separate VLAN should be used to carry uncommon untagged frames to avoid bandwidth contention on data VLANs.
- The native VLAN is for routers and switches to exchange their management information, so it should be different from data VLANs.
53. A network contains multiple VLANs spanning multiple switches. What happens when a device in VLAN 20 sends a broadcast Ethernet frame?
- All devices in all VLANs see the frame.
- Devices in VLAN 20 and the management VLAN see the frame.
- Only devices in VLAN 20 see the frame.
- Only devices that are connected to the local switch see the frame.
54. Which security mode is the least secure choice when a home wireless router is configured?
- WPA
- WPA2
- WEP
- WPA2-Personal
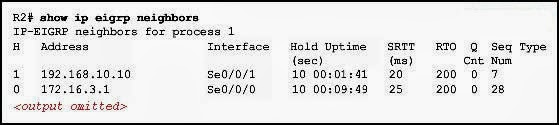
55. Refer to the exhibit. The IPv6 access list LIMITED_ACCESS is applied on the S0/0/0 interface of R1 in the inbound direction. Which IPv6 packets from the ISP will be dropped by the ACL on R1?
- HTTPS packets to PC1
- ICMPv6 packets that are destined to PC1
- packets that are destined to PC1 on port 80
- neighbor advertisements that are received from the ISP router
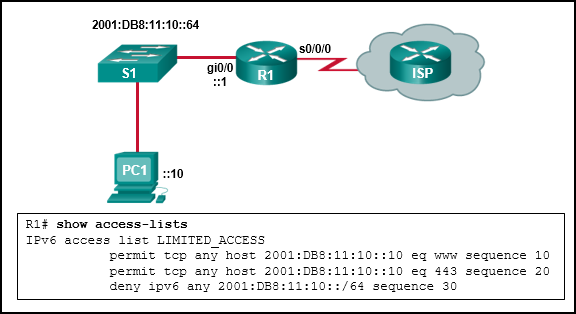
56. Refer to the exhibit. The network engineer for the company that is shown wants to use the primary ISP connection for all external connectivity. The backup ISP connection is used only if the primary ISP connection fails. Which set of commands would accomplish this goal?
- ip route 198.133.219.24 255.255.255.252
ip route 64.100.210.80 255.255.255.252 - ip route 198.133.219.24 255.255.255.252
ip route 64.100.210.80 255.255.255.252 10 - ip route 0.0.0.0 0.0.0.0 s0/0/0
ip route 0.0.0.0 0.0.0.0 s0/1/0 - ip route 0.0.0.0 0.0.0.0 s0/0/0
ip route 0.0.0.0 0.0.0.0 s0/1/0 10
57. What is the most likely scenario in which the WAN interface of a router would be configured as a DHCP client to be assigned a dynamic IP address from an ISP?
- There is a web server for public access on the LAN that is attached to the router.
- The router is also the gateway for a LAN.
- It is a SOHO or home broadband router.
- The router is configured as a DHCP server.
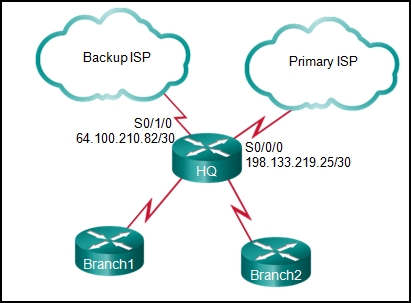
58. Refer to the exhibit. A network administrator has attempted to implement a default route from R1 to the ISP and propagate the default route to EIGRP neighbors. Remote connectivity from the EIGRP neighbor routers to the ISP connected to R1 is failing. Based on the output from the exhibit, what is the most likely cause of the problem?
- The command default-information originate has not been issued on R1.
- There are no EIGRP neighbor relationships on R1.
- The ip route command must specify a next-hop IP address instead of an exit interface when creating a default route.
- The command redistribute static has not been issued on R1.
- The network statement for the ISP connection has not been issued.
59. Refer to the exhibit. Which two networks contain feasible successors? (Choose two.)
- 192.168.71.0
- 192.168.51.0
- 10.44.100.252
- 10.44.104.253
- 10.44.101.252
60. Refer to the exhibit. NAT with overload is configured on router R1 and uses the NAT pool of addresses 209.165.201.9 through 209.165.201.10. What type of route would the ISP need in order for communication to occur between hosts in Company ABC and the Internet?

- Because the ISP has knowledge of the directly connected 200.0.0.1 network, no route is needed.
- A static route from the ISP is needed that uses the network number 172.16.0.0 and the mask 255.255.0.0.
- A default route from the ISP is needed that uses either the exit interface of S0/0/0 or the 200.0.0.1 IP address.
- A default route from the ISP is needed that uses either the exit interface of S0/0/1 or the 200.0.0.2 IP address.
- A static route from the ISP is needed that uses the network number 209.165.201.8 and the mask 255.255.255.252.
61. A network administrator enters the command ipv6 router ospf 64 in global configuration mode. What is the result of this command?
- The router will be assigned an autonomous system number of 64.
- The router will be assigned a router ID of 64.
- The reference bandwidth will be set to 64 Mb/s.
- The OSPFv3 process will be assigned an ID of 64.
62. Which three statements describe the similarities between OSPFv2 and OSPFv3? (Choose three.)
- They both are link-state protocols.
- They both use the exit interface address as the source address when sending OSPF messages.
- They both share the concept of multiple areas.
- They both support IPsec for authentication.
- They both use the same DR/BDR election process.
- They both have unicast routing enabled by default.
63. Match the description to the access method. (Not all options are used.)
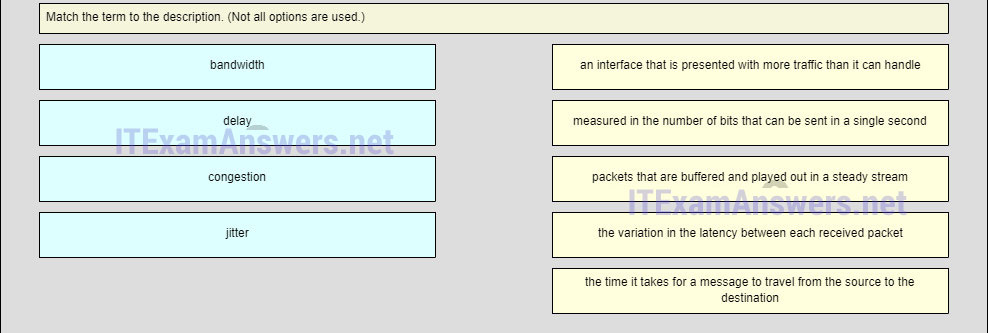
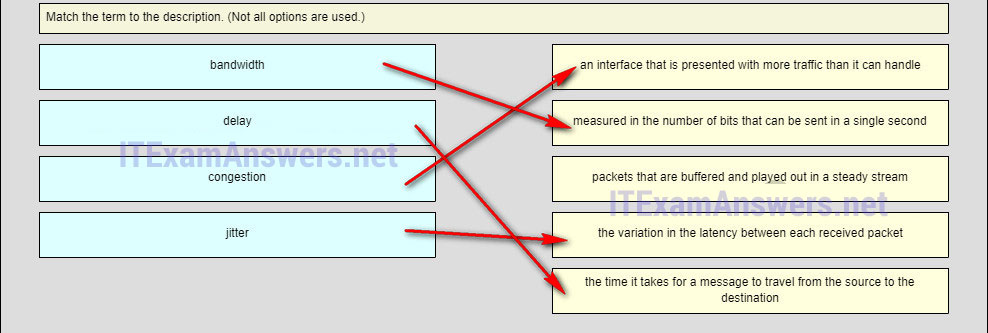
64. Match each description with the corresponding TCP mechanism. (Not all options are used.)
65. Match the description with the correct category. (Not all options are used.)

66. Refer to the exhibit. R1 is configured for NAT as displayed. What is wrong with the configuration?
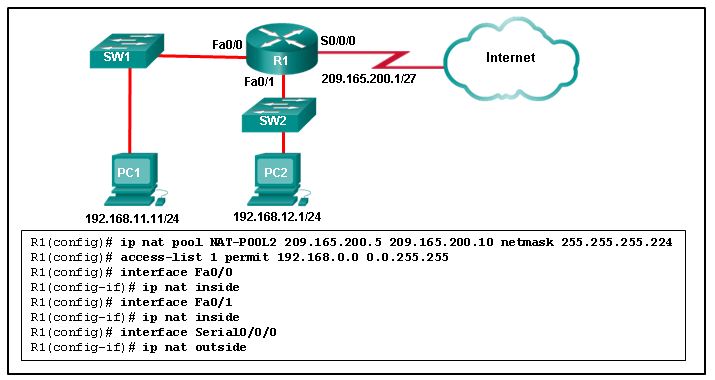
- Access-list 1 is misconfigured.
- NAT-POOL2 is not bound to ACL 1.
- Interface Fa0/0 should be identified as an outside NAT interface.
- The NAT pool is incorrect.
67. Which two statements about NetFlow are true? (Choose two.)
- NetFlow can be used to create baseline documentation.
- NetFlow can be used to collect performance indicators such as interface errors, CPU usage, and memory usage.
- NetFlow can be used to monitor traffic statistics, including packet payload content.
- NetFlow is a Cisco-specific feature that enables the collection of detailed traffic profiles.
- NetFlow is a network monitoring and event reporting tool.
- NetFlow traffic collectors use a “pull” based model to acquire traffic statistics from ports of interest.
68. What benefit does NAT64 provide?
- It allows sites to use private IPv6 addresses and translates them to global IPv6 addresses.
- It allows sites to connect multiple IPv4 hosts to the Internet via the use of a single public IPv4 address.
- It allows sites to connect IPv6 hosts to an IPv4 network by translating the IPv6 addresses to IPv4 addresses.
- It allows sites to use private IPv4 addresses, and thus hides the internal addressing structure from hosts on public IPv4 networks.
69. What are three benefits of using Frame Relay for WAN connectivity? (Choose three.)
- QoS support using the IP precedence field
- one physical interface that can be used for several circuits
- integrated encryption
- mature technology
- reasonable cost
- seamless direct connectivity to an Ethernet LAN
70. What is one advantage to designing networks in building block fashion for large companies?
- failure isolation
- increased network access time
- coarse security control
- fewer required physical resources
71. What is an IPsec protocol that provides data confidentiality and authentication for IP packets?
- CHAP
- ESP
- RSA
- IKE
- PSK
- AP
72. Refer to the exhibit. Which two statements describe the results of entering these commands? (Choose two.)
- R1 will send system messages of levels 0 (emergencies) to level 4 (warnings) to a server.
- R1 will not send critical system messages to the server until the command debug all is entered.
- R1 will reset all the warnings to clear the log.
- R1 will output the system messages to the local RAM.
- The syslog server has the IPv4 address 192.168.10.10.
73. Refer to the exhibit. Based on the output that is shown, what type of NAT has been implemented?
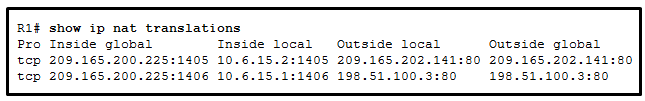
- dynamic NAT with a pool of two public IP addresses
- PAT using an external interface
- static NAT with one entry
- static NAT with a NAT pool
74. Which type of long distance telecommunication technology provides point-to-point connections and cellular access?
- WiMax
- municipal Wi-Fi
- satellite
- mobile broadband
75. What are two advantages of packet switching over circuit switching? (Choose two.)
- The communication costs are lower.
- There are fewer delays in the data communications processes.
- Multiple pairs of nodes can communicate over the same network channel.
- A dedicated secure circuit is established between each pair of communicating nodes.
- A connection through the service provider network is established quickly before communications start.
76. Which two components of a WAN would more likely be used by an ISP? (Choose two.)
- CO
- CPE
- demarcation point
- DTE
- toll network
77. Which two characteristics describe time-division multiplexing? (Choose two.)
- Traffic is allocated bandwidth across a single wire based on preassigned time slots.
- Bandwidth is allocated to channels based on whether a station has data to transmit.
- Encoding technology provides high data throughput in a minimum RF spectrum by supporting parallel data transmission.
- Depending on the configured Layer 2 protocol, data is transmitted across two or more channels via the use of time slots.
- Data capacity across a single link increases as bits from multiple sources are transmitted using interleaved slices of time.
78. What is the protocol that provides ISPs the ability to send PPP frames over DSL networks?
- PPPoE
- CHAP
- PSK
- LTE
- PAP
79. Fill in the blank.
IPsec operates at the network layer of the OSI model.
80. Match the characteristic to the correct PPP authentication protocol. (Not all options are used.)