1. What is an example of an M2M connection in the IoT?
- A user sends an email over the Internet to a friend.
- Sensors in a warehouse communicate with each other and send data to a server block in the cloud.*
- Redundant servers communicate with each other to determine which server should be active or standby.
- An automated alarm system in a campus sends fire alarm messages to all students and staff.
2. What is the term for the extension of the existing Internet structure to billions of connected devices?
- M2M
- digitization
- IoT*
- SCADA
3. Which statement describes the Cisco IoT System?
- It is a switch operating system to integrate many Layer 2 security features.
- It is an advanced routing protocol for cloud computing.
- It is an infrastructure to manage large scale systems of very different endpoints and platforms.*
- It is a router operating system combining IOS and Linux for fog computing.
4. Which three network models are described in the fog computing pillar of the Cisco IoT System? (Choose three.)
- fog computing*
- client/server*
- P2P
- cloud computing*
- peer-to-peer
- enterprise WAN
5. Which IoT pillar extends cloud connectivity closer to the network edge?
- network connectivity pillar
- fog computing pillar*
- management and automation pillar
- application enablement platform pillar
6. Which cybersecurity solution is described in the security pillar of the Cisco IoT System to address the security of power plants and factory process lines?
- IoT network security
- cloud computing security
- operational technology specific security*
- IoT physical security
7. Which cloud computing opportunity would provide the use of network hardware such as routers and switches for a particular company?
- infrastructure as a service (IaaS)*
- software as a service (SaaS)
- browser as a service (BaaS)
- wireless as a service (WaaS)
8. What technology allows users to access data anywhere and at any time?
- Cloud computing*
- virtualization
- micromarketing
- data analytics
9. The exhibit is not required to answer the question. The exhibit shows a fog covering trees on the side of a mountain.What statement describes Fog computing?

- It requires Cloud computing services to support non-IP enabled sensors and controllers.
- It supports larger networks than Cloud computing does.
- It creates a distributed computing infrastructure that provides services close to the network edge.*
- It utilizes a centralized computing infrastructure that stores and manipulates big data in one very secure data center.
10. Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?
- ITaaS
- SaaS
- PaaS
- IaaS*
11. Which cloud model provides services for a specific organization or entity?
- a public cloud
- a hybrid cloud
- a private cloud*
- a community cloud
12. How does virtualization help with disaster recovery within a data center?
- improvement of business practices
- supply of consistent air flow
- support of live migration*
- guarantee of power
13. What is a difference between the functions of Cloud computing and virtualization?
- Cloud computing separates the application from the hardware whereas virtualization separates the OS from the underlying hardware.*
- Cloud computing requires hypervisor technology whereas virtualization is a fault tolerance technology.
- Cloud computing utilizes data center technology whereas virtualization is not used in data centers.
- Cloud computing provides services on web-based access whereas virtualization provides services on data access through virtualized Internet connections.
14. Which two business and technical challenges does implementing virtualization within a data center help businesses to overcome? (Choose two.)
- physical footprint*
- server hardware needs
- virus and spyware attacks
- power and air conditioning*
- operating system license requirements
15. When preparing an IoT implementation, what type of network will devices be connected to in order to share the same infrastructure and facilitate communications, analytics, and management?
- converged*
- video
- telephone
- VoIP
16. Which type of Hypervisor is implemented when a user with a laptop running the Mac OS installs a Windows virtual OS instance?
- virtual machine
- bare metal
- type 2*
- type 1
17. Which statement describes the concept of cloud computing?
- separation of operating system from hardware
- separation of management plane from control plane
- separation of application from hardware*
- separation of control plane from data plane
18. Which is a characteristic of a Type 2 hypervisor?
- best suited for enterprise environments
- installs directly on hardware
- does not require management console software*
- has direct access to server hardware resources
19. Which is a characteristic of a Type 1 hypervisor?
- does not require management console software
- installed directly on a server*
- installed on an existing operating system
- best suited for consumers and not for an enterprise environment
20. How is the control plane modified to operate with network virtualization?
- Control plane redundancy is added to each network device.
- The control plane on each device is interconnected to a dedicated high-speed network.
- A hypervisor is installed in each device to allow multiple instances of the control plane.
- The control plane function is consolidated into a centralized controller.*
21. Which technology virtualizes the network control plane and moves it to a centralized controller?
- IaaS
- SDN*
- fog computing
- cloud computing
22. Which two layers of the OSI model are associated with SDN network control plane functions that make forwarding decisions? (Choose two.)
- Layer 1
- Layer 2*
- Layer 3*
- Layer 4
- Layer 5
23. What pre-populates the FIB on Cisco devices that use CEF to process packets?
- the adjacency table
- the routing table*
- the DSP
- the ARP table
24. Which type of hypervisor would most likely be used in a data center?
- Type 1*
- Hadoop
- Nexus
- Type 2
25. What component is considered the brains of the ACI architecture and translates application policies?
- the Application Network Profile endpoints
- the Nexus 9000 switch
- the hypervisor
- the Application Policy Infrastructure Controller*
26. Fill in the blank.
In an IoT implementation, devices will be connected to a
network to share the same infrastructure and to facilitate communications, analytics, and management.
Correct Answer: converged
27. Fill in the blank.
In a scenario where a user with a laptop running the Mac OS installs a Windows virtual OS instance, the user is implementing a Type
hypervisor.
Correct Answer: 2
Older Version
28. A network design engineer is planning the implementation of a cost-effective method to interconnect multiple networks securely over the Internet. Which type of technology is required?
- a GRE IP tunnel
- a leased line
- a VPN gateway*
- a dedicated ISP
29. What is one benefit of using VPNs for remote access?
- lower protocol overhead
- ease of troubleshooting
- potential for reduced connectivity costs*
- increased quality of service
30. How is “tunneling” accomplished in a VPN?
- New headers from one or more VPN protocols encapsulate the original packets.*
- All packets between two hosts are assigned to a single physical medium to ensure that the packets are kept private.
- Packets are disguised to look like other types of traffic so that they will be ignored by potential attackers.
- A dedicated circuit is established between the source and destination devices for the duration of the connection.
31. Two corporations have just completed a merger. The network engineer has been asked to connect the two corporate networks without the expense of leased lines. Which solution would be the most cost effective method of providing a proper and secure connection between the two corporate networks?
- Cisco AnyConnect Secure Mobility Client with SSL
- Cisco Secure Mobility Clientless SSL VPN
- Frame Relay
- remote access VPN using IPsec
- site-to-site VPN*
32. Which two scenarios are examples of remote access VPNs? (Choose two.)
- A toy manufacturer has a permanent VPN connection to one of its parts suppliers.
- All users at a large branch office can access company resources through a single VPN connection.
- A mobile sales agent is connecting to the company network via the Internet connection at a hotel.*
- A small branch office with three employees has a Cisco ASA that is used to create a VPN connection to the HQ.
- An employee who is working from home uses VPN client software on a laptop in order to connect to the company network.*
33. Which statement describes a feature of site-to-site VPNs?
- The VPN connection is not statically defined.
- VPN client software is installed on each host.
- Internal hosts send normal, unencapsulated packets.*
- Individual hosts can enable and disable the VPN connection.
34. What is the purpose of the generic routing encapsulation tunneling protocol?
- to provide packet level encryption of IP traffic between remote sites
- to manage the transportation of IP multicast and multiprotocol traffic between remote sites*
- to support basic unencrypted IP tunneling using multivendor routers between remote sites
- to provide fixed flow-control mechanisms with IP tunneling between remote sites
35. Which remote access implementation scenario will support the use of generic routing encapsulation tunneling?
- a mobile user who connects to a router at a central site
- a branch office that connects securely to a central site
- a mobile user who connects to a SOHO site
- a central site that connects to a SOHO site without encryption*
36. Refer to the exhibit. A tunnel was implemented between routers R1 and R2. Which two conclusions can be drawn from the R1 command output? (Choose two.)
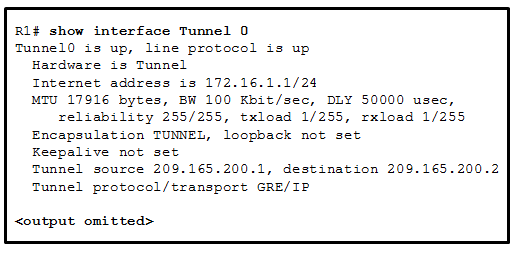
- This tunnel mode is not the default tunnel interface mode for Cisco IOS software.
- This tunnel mode provides encryption.
- The data that is sent across this tunnel is not secure.*
- This tunnel mode does not support IP multicast tunneling.
- A GRE tunnel is being used.*
37. Refer to the exhibit. Which IP address would be configured on the tunnel interface of the destination router?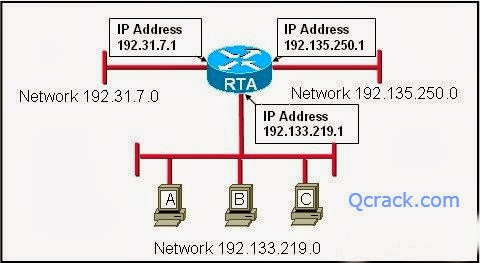
- 172.16.1.1
- 172.16.1.2*
- 209.165.200.225
- 209.165.200.226
38. Which statement correctly describes IPsec?
- IPsec works at Layer 3, but can protect traffic from Layer 4 through Layer 7.*
- IPsec uses algorithms that were developed specifically for that protocol.
- IPsec implements its own method of authentication.
- IPsec is a Cisco proprietary standard.
39. Which function of IPsec security services allows the receiver to verify that the data was transmitted without being changed or altered in any way?
- anti-replay protection
- authentication
- data integrity*
- confidentiality
40. Which statement describes a characteristic of IPsec VPNs?
- IPsec is a framework of Cisco proprietary protocols.
- IPsec can secure traffic at Layers 1 through 3.
- IPsec encryption causes problems with routing.
- IPsec works with all Layer 2 protocols.*
41. What is an IPsec protocol that provides data confidentiality and authentication for IP packets?
- AH
- ESP*
- RSA
- IKE
42. What two encryption algorithms are used in IPsec VPNs? (Choose two.)
- DH
- PSK
- IKE
- AES *
- 3DES*
43. Which algorithm is an asymmetrical key cryptosystem?
- RSA*
- AES
- 3DES
- DES
44. Which two algorithms use Hash-based Message Authentication Code for message authentication? (Choose two.)
- 3DES
- DES
- AES
- MD5 *
- SHA*
45. Which three statements describe the building blocks that make up the IPsec protocol framework? (Choose three.)
- IPsec uses encryption algorithms and keys to provide secure transfer of data.*
- IPsec uses Diffie-Hellman algorithms to encrypt data that is transferred through the VPN.
- IPsec uses 3DES algorithms to provide the highest level of security for data that is transferred through a VPN.
- IPsec uses secret key cryptography to encrypt messages that are sent through a VPN.*
- IPsec uses Diffie-Hellman as a hash algorithm to ensure integrity of data that is transmitted through a VPN.
- IPsec uses ESP to provide confidential transfer of data by encrypting IP packets.*
46. A network design engineer is planning the implementation of an IPsec VPN. Which hashing algorithm would provide the strongest level of message integrity?
- SHA-1
- MD5
- AES
- 512-bit SHA*
47. What is the purpose of utilizing Diffie-Hellman (DH) algorithms as part of the IPsec standard?
- DH algorithms allow unlimited parties to establish a shared public key that is used by encryption and hash algorithms.
- DH algorithms allow two parties to establish a shared secret key that is used by encryption and hash algorithms.*
- DH algorithms allow unlimited parties to establish a shared secret key that is used by encryption and hash algorithms.
- DH algorithms allow two parties to establish a shared public key that is used by encryption and hash algorithms.
48. What is the purpose of a message hash in a VPN connection?
- It ensures that the data cannot be read in plain text.
- It ensures that the data has not changed while in transit.*
- It ensures that the data is coming from the correct source.
- It ensures that the data cannot be duplicated and replayed to the destination.
49. Which Cisco VPN solution provides limited access to internal network resources by utilizing a Cisco ASA and provides browser-based access only?
- clientless SSL VPN*
- client-based SSL VPN
- SSL
- IPsec
50. What key question would help determine whether an organization should use an SSL VPN or an IPsec VPN for the remote access solution of the organization?
- Is a Cisco router used at the destination of the remote access tunnel?
- What applications or network resources do the users need for access?
- Are both encryption and authentication required?
- Do users need to be able to connect without requiring special VPN software?*
51. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What problem is preventing the hosts from communicating across the VPN tunnel?
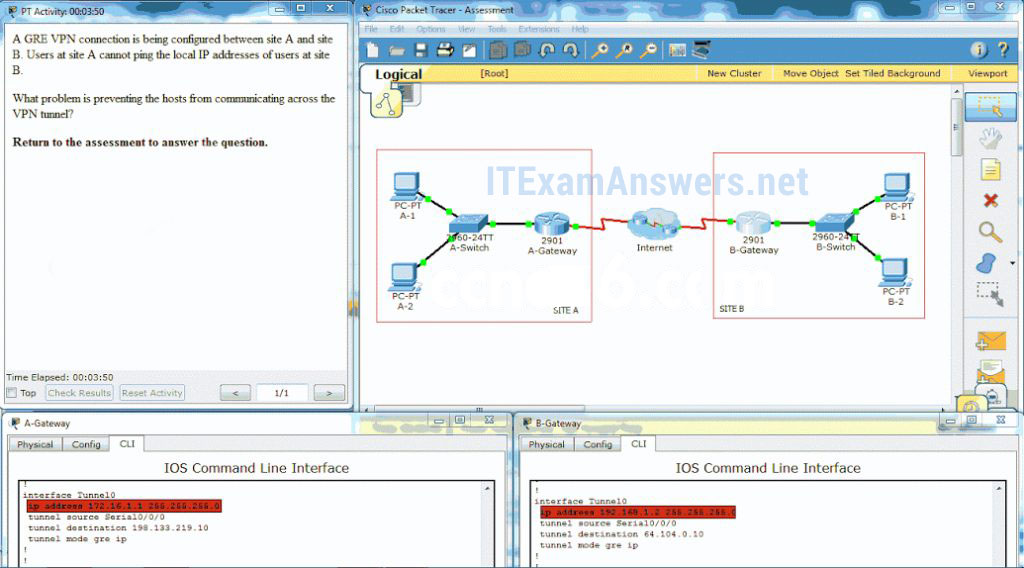
- The EIGRP configuration is incorrect.
- The tunnel destinations addresses are incorrect.
- The tunnel IP addresses are incorrect.*
- The tunnel source interfaces are incorrect
52. Which critical function that is provided by IPsec ensures that data has not been changed in transit between the source and destination?
- integrity*
- anti-replay protection
- confidentiality
- authentication
53. Which service of IPsec verifies that secure connections are formed with the intended sources of data?
- encryption
- authentication*
- confidentiality
- data integrity
54. Fill in the blank.
“__GRE__” is a site-to-site tunnel protocol developed by Cisco to allow multiprotocol and IP multicast traffic between two or more sites.
55. What is an advantage of using the Cisco Secure Mobility Clientless SSL VPN?
- Security is provided by prohibiting network access through a browser.
- Any device can connect to the network without authentication.
- Clients do not require special software.*
- Clients use SSH to access network resources.
56. How can the use of VPNs in the workplace contribute to lower operating costs?
- VPNs prevents connectivity to SOHO users.
- VPNs can be used across broadband connections rather than dedicated WAN links.*
- VPNs require a subscription from a specific Internet service provider that specializes in secure connections.
- High-speed broadband technology can be replaced with leased lines.
57. Which two characteristics describe IPsec VPNs? (Choose two.)
- Key lengths range from 40 bits to 256 bits.
- IPsec authentication is one-way or two-way.
- Specific PC client configuration is required to connect to the VPN.*
- IPsec is specifically designed for web-enabled applications.
- IPsec authenticates by using shared secrets or digital certificates.*
Download PDF File below:
