CCNA Routing and Switching
Connecting Networks 6.0 – Chapter 5 Skills Integration Challenge
Chapter 5 SIC: Access Control List and SNMP Configuration
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button to submit your work.
Introduction
In this practice Packet Tracer Skills Based Assessment, you will:
- Configure SNMP community strings.
- Configure standard and extended IPv4 ACLs to filter network traffic.
- Configure an IPv6 ACLs to filter network traffic.
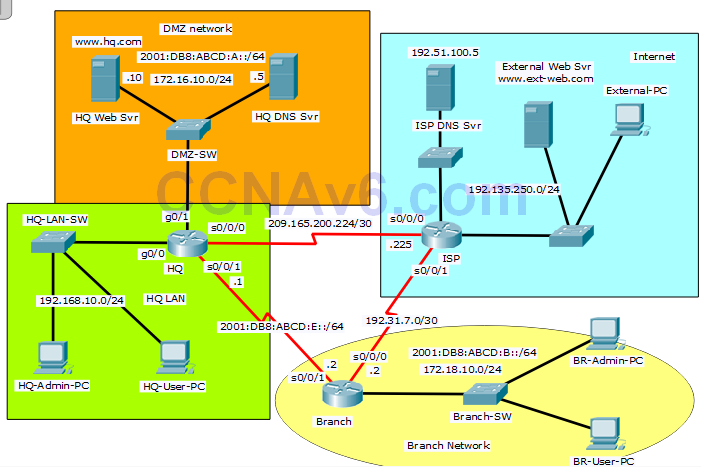
Addressing Table
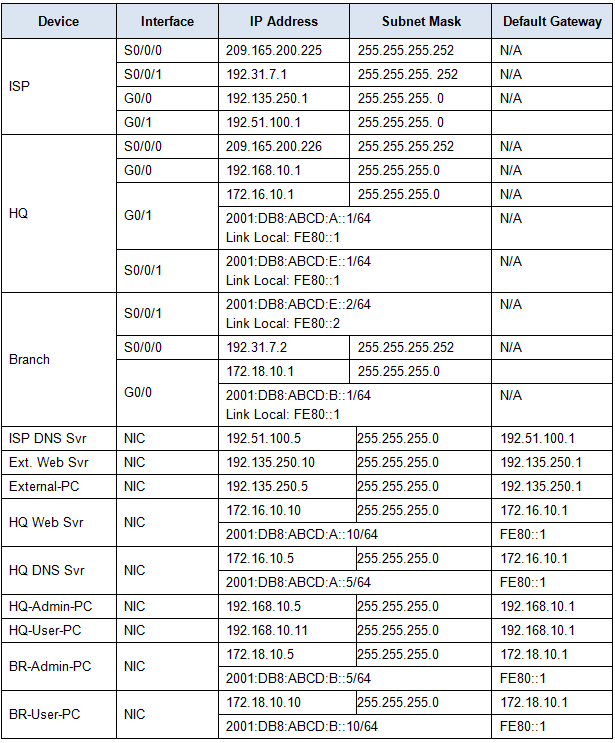
Step 1: Configure SNMP Community Strings on the HQ router.
a. Configure a Read Only SNMP community string hq-monitor.
b. Configure a Read/Write SNMP community string hq-inside.
Step 2: Configure an ACL for NAT on the HQ router.
a. Configure standard access list numbered 1 to allow NAT for hosts in network 192.168.10.0 /24.
Step 3: Configure a standard ACL to restrict remote access to the HQ router.
a. Configure a standard ACL numbered 12 to restrict remote access to HQ.
• Allow only the HQ-Admin-PC to access the HQ router remotely via VTY.
• All other remote connections should fail.
Step 4: Configure two extended ACLs to restrict access to SNMP operation on the HQ router.
a. Configure an extended ACL named SNMPACCESS.
• The SNMP operation runs UDP on port 161.
• Allow only the HQ-Admin-PC to access the HQ router for the SNMP connection.
• SNMP connections from other hosts on the HQ LAN should fail.
• Allow all other IP traffic.
• Apply this ACL on the HQ router, G0/0 interface.
b. Configure an extended ACL named SNMPDENY.
• Deny any hosts to make connections to SNMP on the HQ router.
• Allow all other IP traffic.
• Apply this ACL on the HQ router, G0/1 interface.
Step 5: Configure an extended ACL to restrict access to the HQ LAN from the Internet.
a. Configure an extended IPv4 ACL named INTOHQ.
• Allow any hosts from the Internet to access the HQ DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts from the Internet to access the HQ Web Svr. Only port 80 is needed.
• Allow return TCP traffic from the Internet that was initiated from the hosts in the HQ networks to pass (with the established keyword).
• Apply the ACL to the HQ S0/0/0 interface.
Step 6: Configure an extended ACL to restrict access to the DMZ network.
a. Configure an extended IPv4 ACL named IN-DMZ.
• Allow any hosts to access the HQ DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts to access the HQ Web Svr. Only port 80 is needed.
• Allow only the HQ-Admin-PC to have FTP access to the HQ Web Svr. There should be two ACEs, for ports 20 and 21.
• Apply the ACL to the HQ G0/1 interface.
Step 7: Configure an IPv6 ACL to restrict access to the DMZ network from the Branch Network. (Please note, the order of ACL statements is significant only because of the scoring need in Packet Tracer).
a. Configure an IPv6 ACL named DMZFTP.
• Deny any hosts in the Branch network to access the SNMP operation of the HQ router.
• Allow only BR-Admin-PC to have FTP access to the HQ Web Svr. There should be two ACEs, for ports 20 and 21.
• Allow any hosts in the Branch Network to access the HQ Web Svr. Only port 80 is needed.
• Apply the ACL to the HQ router S0/0/1 interface.
Step 8: Connectivity Tests
a. HQ-Admin-PC can access FTP service on HQ Web Svr.
b. HQ-User-PC cannot access FTP service on HQ Web Svr.
c. BR-Admin-PC can access FTP service on HQ Web Svr with its IPv6 address.
d. BR-User-PC cannot access FTP service on HQ Web Svr with its IPv6 address.
e. HQ-Admin-PC, HQ-User-PC, and External-PC can access HQ Web Svr with URL www.hq.com
f. HQ-Admin-PC, HQ-User-PC, and External-PC can access External Web Srv with URL www.ext-web.com
g. BR-Admin-PC and BR-User-PC can access HQ Web Svr with its IPv6 address
h. BR-Admin-PC and BR-User-PC can access External Web Srv with URL www.ext-web.com
A few things to keep in mind while completing this activity:
- Do not use the browser Backbutton or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessmentbutton to submit your work.
Introduction
In this practice Packet Tracer Skills Based Assessment, you will:
- Configure SNMP community strings.
- Configure standard and extended IPv4 ACLs to filter network traffic.
- Configure an IPv6 ACLs to filter network traffic.
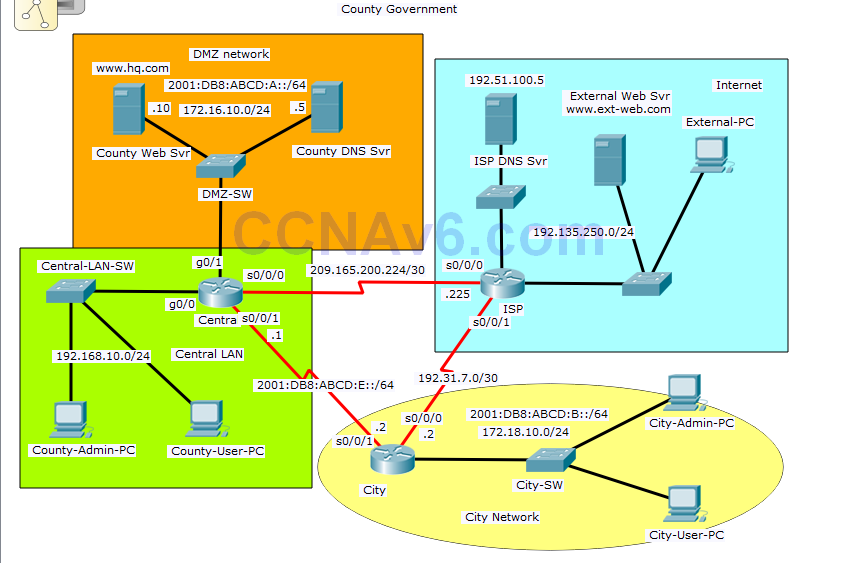
Addressing Table
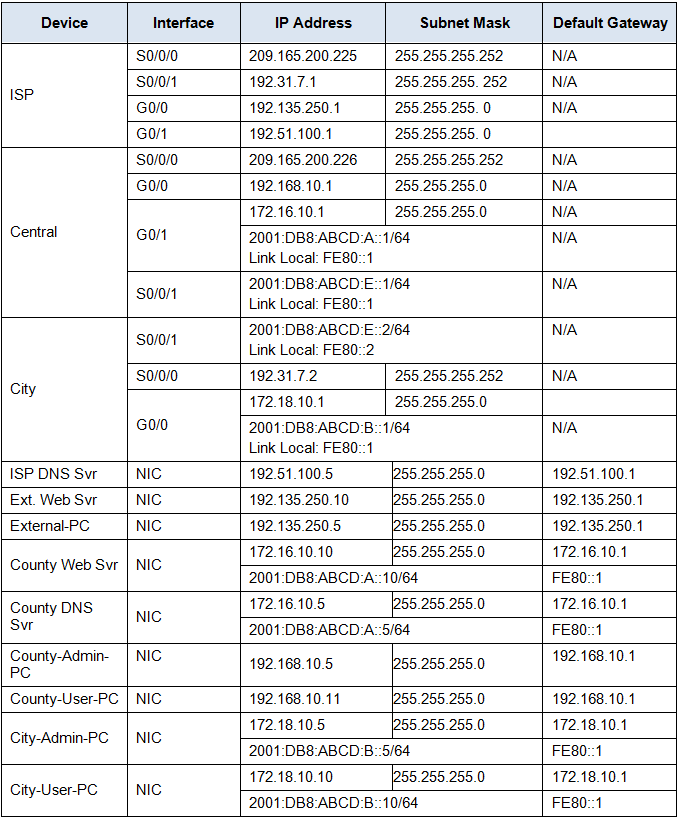
Step 1: Configure SNMP Community Strings on the Central router.
a. Configure a Read Only SNMP community string hq-monitor.
b. Configure a Read/Write SNMP community string hq-inside.
Step 2: Configure an ACL for NAT on the Central router.
a. Configure standard access list numbered 1 to allow NAT for hosts in network 192.168.10.0 /24.
Access-list 1 permit 192.168.10.0 0.0.0.255
Step 3: Configure a standard ACL to restrict remote access to the Central router.
a. Configure a standard ACL numbered 12 to restrict remote access to Central.
• Allow only the County-Admin-PC to access the Central router remotely via VTY.
• All other remote connections should fail.
Step 4: Configure two extended ACLs to restrict access to SNMP operation on the Central router.
a. Configure an extended ACL named SNMPACCESS.
• The SNMP operation runs UDP on port 161.
• Allow only the County-Admin-PC to access the Central router for the SNMP connection.
• SNMP connections from other hosts on the Central LAN should fail.
• Allow all other IP traffic.
• Apply this ACL on the Central router, G0/0 interface.
b. Configure an extended ACL named SNMPDENY.
• Deny any hosts to make connections to SNMP on the Central router.
• Allow all other IP traffic.
• Apply this ACL on the Central router, G0/1 interface.
Step 5: Configure an extended ACL to restrict access to the Central LAN from the Internet.
a. Configure an extended IPv4 ACL named INTOHQ.
• Allow any hosts from the Internet to access the County DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts from the Internet to access the County Web Svr. Only port 80 is needed.
• Allow return TCP traffic from the Internet that was initiated from the hosts in the Central networks to pass (with the establishedkeyword).
• Apply the ACL to the Central S0/0/0 interface.
Step 6: Configure an extended ACL to restrict access to the DMZ network.
a. Configure an extended IPv4 ACL named IN-DMZ.
• Allow any hosts to access the County DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts to access the County Web Svr. Only port 80 is needed.
• Allow only the County-Admin-PC to have FTP access to the County Web Svr. There should be two ACEs, for ports 20 and 21.
• Apply the ACL to the Central G0/1 interface.
Step 7: Configure an IPv6 ACL to restrict access to the DMZ network from the City Network. (Please note, the order of ACL statements is significant only because of the scoring need in Packet Tracer).
a. Configure an IPv6 ACL named DMZFTP.
• Deny any hosts in the Branch network to access the SNMP operation of the Central router.
• Allow only City-Admin-PC to have FTP access to the County Web Svr. There should be two ACEs, for ports 20 and 21.
• Allow any hosts in the City Network to access the County Web Svr. Only port 80 is needed.
• Apply the ACL to the Central router S0/0/1 interface.
Step 8: Connectivity Tests
a. County-Admin-PC can access FTP service on County Web Svr.
b. County-User-PC cannot access FTP service on County Web Svr.
c. City-Admin-PC can access FTP service on County Web Svr with its IPv6 address.
d. City-User-PC cannot access FTP service on County Web Svr with its IPv6 address.
e. County-Admin-PC, County-User-PC, and External-PC can access County Web Svr with URL www.hq.com
f. County-Admin-PC, County-User-PC, and External-PC can access External Web Srv with URL www.ext-web.com
g. City-Admin-PC and City-User-PC can access County Web Svr with its IPv6 address
h. City-Admin-PC and City-User-PC can access External Web Srv with URL www.ext-web.com
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any Exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button to submit your work.
Introduction
In this practice Packet Tracer Skills Based Assessment, you will:
- Configure SNMP community strings.
- Configure standard and extended IPv4 ACLs to filter network traffic.
- Configure an IPv6 ACLs to filter network traffic.
Addressing Table
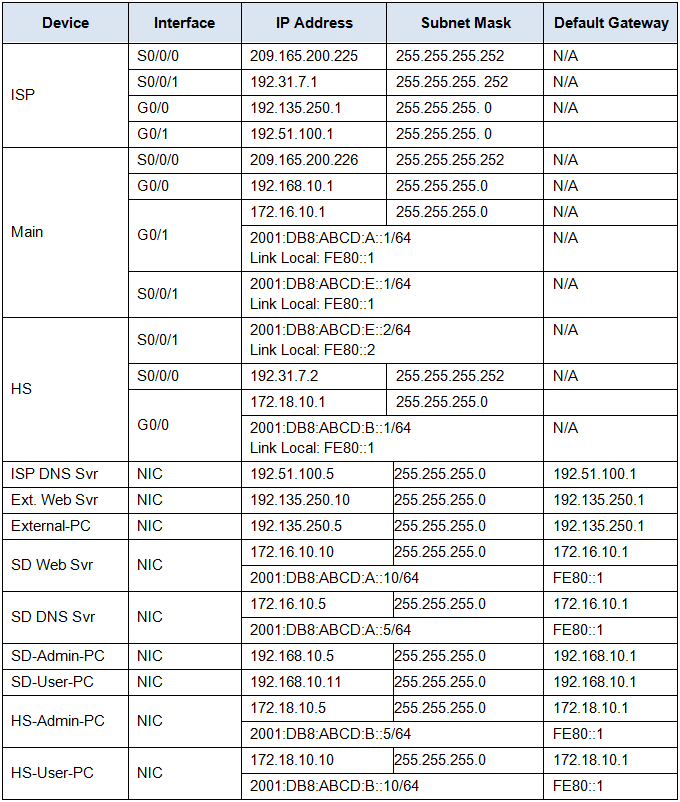
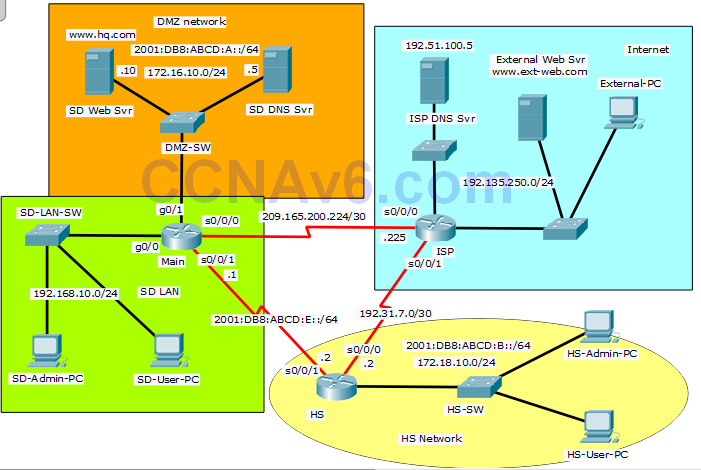
Step 1: Configure SNMP Community Strings on the Main router.
a. Configure a Read Only SNMP community string hq-monitor.
b. Configure a Read/Write SNMP community string hq-inside.
Step 2: Configure an ACL for NAT on the Main router.
a. Configure standard access list numbered 1 to allow NAT for hosts in network 192.168.10.0 /24.
Step 3: Configure a standard ACL to restrict remote access to the Main router.
a. Configure a standard ACL numbered 12 to restrict remote access to Main.
• Allow only the SD-Admin-PC to access the Main router remotely via VTY.
• All other remote connections should fail.
Step 4: Configure two extended ACLs to restrict access to SNMP operation on the Main router.
a. Configure an extended ACL named SNMPACCESS.
• The SNMP operation runs UDP on port 161.
• Allow only the SD-Admin-PC to access the Main router for the SNMP connection.
• SNMP connections from other hosts on the SD LAN should fail.
• Allow all other IP traffic.
• Apply this ACL on the Main router, G0/0 interface.
b. Configure an extended ACL named SNMPDENY.
• Deny any hosts to make connections to SNMP on the Main router.
• Allow all other IP traffic.
• Apply this ACL on the Main router, G0/1 interface.
Step 5: Configure an extended ACL to restrict access to the SD LAN from the Internet.
a. Configure an extended IPv4 ACL named INTOHQ.
• Allow any hosts from the Internet to access the SD DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts from the Internet to access the SD Web Svr. Only port 80 is needed.
• Allow return TCP traffic from the Internet that was initiated from the hosts in the Main networks to pass (with the established keyword).
• Apply the ACL to the Main S0/0/0 interface.
Step 6: Configure an extended ACL to restrict access to the DMZ network.
a. Configure an extended IPv4 ACL named IN-DMZ.
• Allow any hosts to access the SD DNS Svr. There should be two ACEs, one for TCP and the other UDP. Both use port 53.
• Allow any hosts to access the SD Web Svr. Only port 80 is needed.
• Allow only the SD-Admin-PC to have FTP access to the SD Web Svr. There should be two ACEs, for ports 20 and 21.
• Apply the ACL to the Main G0/1 interface.
Step 7: Configure an IPv6 ACL to restrict access to the DMZ network from the HS Network. (Please note, the order of ACL statements is significant only because of the scoring need in Packet Tracer).
a. Configure an IPv6 ACL named DMZFTP.
• Deny any hosts in the Branch network to access the SNMP operation of the Main router.
• Allow only HS-Admin-PC to have FTP access to the SD Web Svr. There should be two ACEs, for ports 20 and 21.
• Allow any hosts in the HS Network to access the SD Web Svr. Only port 80 is needed.
• Apply the ACL to the Main router S0/0/1 interface.
Step 8: Connectivity Tests
a. SD-Admin-PC can access FTP service on SD Web Svr.
b. SD-User-PC cannot access FTP service on SD Web Svr.
c. HS-Admin-PC can access FTP service on SD Web Svr with its IPv6 address.
d. HS-User-PC cannot access FTP service on SD Web Svr with its IPv6 address.
e. SD-Admin-PC, SD-User-PC, and External-PC can access SD Web Svr with URL www.hq.com
f. SD-Admin-PC, SD-User-PC, and External-PC can access External Web Srv with URL www.ext-web.com
g. HS-Admin-PC and HS-User-PC can access SD Web Svr with its IPv6 address
h. HS-Admin-PC and HS-User-PC can access External Web Srv with URL www.ext-web.com
Config script for Router: HQ / Main / Central (100%)
EN conf ter snmp-server community hq-monitor ro snmp-server community hq-inside rw access-list 1 permit 192.168.10.0 0.0.0.255 access-list 12 permit host 192.168.10.5 line vty 0 1 access-class 12 in exit ip access-list extended SNMPACCESS Permit udp host 192.168.10.5 host 192.168.10.1 eq 161 deny udp any host 192.168.10.1 eq 161 permit ip any any interface g0/0 ip access-group SNMPACCESS in exit ip access-list extended SNMPDENY deny udp any host 172.16.10.1 eq 161 permit ip any any interface g0/1 ip access-group SNMPDENY IN exit ip access-list extended INTOHQ permit tcp any host 172.16.10.5 eq 53 permit udp any host 172.16.10.5 eq 53 permit tcp any host 172.16.10.10 eq 80 permit tcp any any established interface s0/0/0 ip access-group INTOHQ IN exit ip access-list extended IN-DMZ permit udp any host 172.16.10.5 eq 53 permit tcp any host 172.16.10.5 eq 53 permit tcp any host 172.16.10.10 eq 80 permit tcp host 192.168.10.5 host 172.16.10.10 eq 20 permit tcp host 192.168.10.5 host 172.16.10.10 eq 21 interface g0/1 ip access-group IN-DMZ out exit ipv6 access-list DMZFTP deny udp any host 2001:DB8:ABCD:E::1 eq 161 permit tcp host 2001:DB8:ABCD:B::5 host 2001:DB8:ABCD:A::10 eq 20 permit tcp host 2001:DB8:ABCD:B::5 host 2001:DB8:ABCD:A::10 eq 21 permit tcp 2001:DB8:ABCD:B::/64 host 2001:DB8:ABCD:A::10 eq 80 int s0/0/1 ipv6 traffic-filter DMZFTP IN

Muchas gracias
BIG THANKS!!!