1. Which two definitions accurately describe the associated application layer protocol? (Choose two.)
- SMTP – transfers web pages from web servers to clients
- Telnet – provides remote access to servers and networking devices
- DNS – resolves Internet names to IP addresses
- FTP – transfers email messages and attachments
- HTTP – enables devices on a network to obtain IP addresses
2. The application layer of the TCP/IP model performs the functions of what three layers of the OSI model? (Choose three.)
- physical
- session
- network
- presentation
- data link
- transport
- application
3. Which layer in the TCP/IP model is used for formatting, compressing, and encrypting data?
- internetwork
- session
- presentation
- application
- network access
4. What are two characteristics of the application layer of the TCP/IP model? (Choose two.)
- responsibility for logical addressing
- responsibility for physical addressing
- the creation and maintenance of dialogue between source and destination applications
- closest to the end user
- the establishing of window size
5. A manufacturing company subscribes to certain hosted services from its ISP. The services that are required include hosted world wide web, file transfer, and e-mail. Which protocols represent these three key applications? (Choose three.)
- FTP
- HTTP
- DNS
- SNMP
- DHCP
- SMTP
6. What is an example of network communication that uses the client-server model?
- A user uses eMule to download a file that is shared by a friend after the file location is determined.
- A workstation initiates an ARP to find the MAC address of a receiving host.
- A user prints a document by using a printer that is attached to a workstation of a coworker.
- A workstation initiates a DNS request when the user types www.cisco.com in the address bar of a web browser.
7. Two students are working on a network design project. One student is doing the drawing, while the other student is writing the proposal. The drawing is finished and the student wants to share the folder that contains the drawing so that the other student can access the file and copy it to a USB drive. Which networking model is being used?
- peer-to-peer
- client-based
- master-slave
- point-to-point
8. What do the client/server and peer-to-peer network models have in common?
- Both models have dedicated servers.
- Both models support devices in server and client roles.
- Both models require the use of TCP/IP-based protocols.
- Both models are used only in the wired network environment.
9. What is an advantage for small organizations of adopting IMAP instead of POP?
- Messages are kept in the mail servers until they are manually deleted from the email client.
- When the user connects to a POP server, copies of the messages are kept in the mail server for a short time, but IMAP keeps them for a long time.
- IMAP sends and retrieves email, but POP only retrieves email.
- POP only allows the client to store messages in a centralized way, while IMAP allows distributed storage.
10. Which application layer protocol uses message types such as GET, PUT, and POST?
- DNS
- DHCP
- SMTP
- HTTP
- POP3
11. When retrieving email messages, which protocol allows for easy, centralized storage and backup of emails that would be desirable for a small- to medium-sized business?
- IMAP
- POP
- SMTP
- HTTPS
12. What is the function of the Nslookup utility?
- to manually query the name servers to resolve a given host name
- to view the network settings on a host
- to manually force a client to send a DHCP request
- to display all cached DNS entries on a host
13. What message type is used by an HTTP client to request data from a web server?
- POST
- ACK
- GET
- PUT
14. Which protocol is used by a client to communicate securely with a web server?
- SMB
- HTTPS
- SMTP
- IMAP
15. Which three statements describe a DHCP Discover message? (Choose three.)
- The source MAC address is 48 ones (FF-FF-FF-FF-FF-FF).
- The destination IP address is 255.255.255.255.
- The message comes from a server offering an IP address.
- The message comes from a client seeking an IP address.
- All hosts receive the message, but only a DHCP server replies.
- Only the DHCP server receives the message.
16. What part of the URL, http://www.cisco.com/index.html, represents the top-level DNS domain?
- .com
- www
- http
- index
17. Which two tasks can be performed by a local DNS server? (Choose two.)
- providing IP addresses to local hosts
- allowing data transfer between two network devices
- mapping name-to-IP addresses for internal hosts
- forwarding name resolution requests between servers
- retrieving email messages
18. Which phrase describes an FTP daemon?
- a diagnostic FTP program
- a program that is running on an FTP server
- a program that is running on an FTP client
- an application that is used to request data from an FTP server
19. Which statement is true about FTP?
- The client can choose if FTP is going to establish one or two connections with the server.
- The client can download data from or upload data to the server.
- FTP is a peer-to-peer application.
- FTP does not provide reliability during data transmission.
20. What is true about the Server Message Block protocol?
- Different SMB message types have a different format.
- Clients establish a long term connection to servers.
- SMB messages cannot authenticate a session.
- SMB uses the FTP protocol for communication.
21. Which application layer protocol is used to provide file-sharing and print services to Microsoft applications?
- HTTP
- SMTP
- DHCP
- SMB
22. Fill in the blank.
What is the acronym for the protocol that is used when securely communicating with a web server? HTTPS
23. Fill in the blank.
The HTTP message type used by the client to request data from the web server is the GET message.
24. Open the PT Activity.
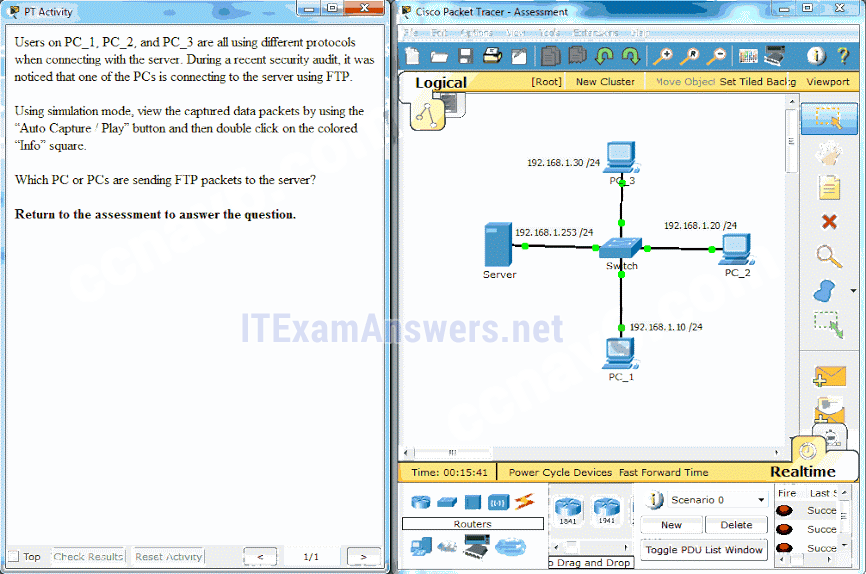
Perform the tasks in the activity instructions and then answer the question.Which PC or PCs are sending FTP packets to the server?
- PC_3
- PC_1
- PC_2
- PC_1 and PC_3
25. Fill in the blank.
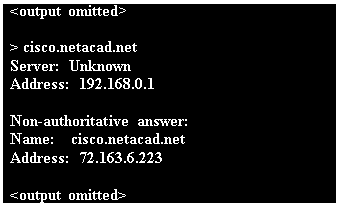
Refer to the exhibit. What command was used to resolve a given host name by querying the name servers?
nslookup
26. Match a statement to the related network model. (Not all options are used.)
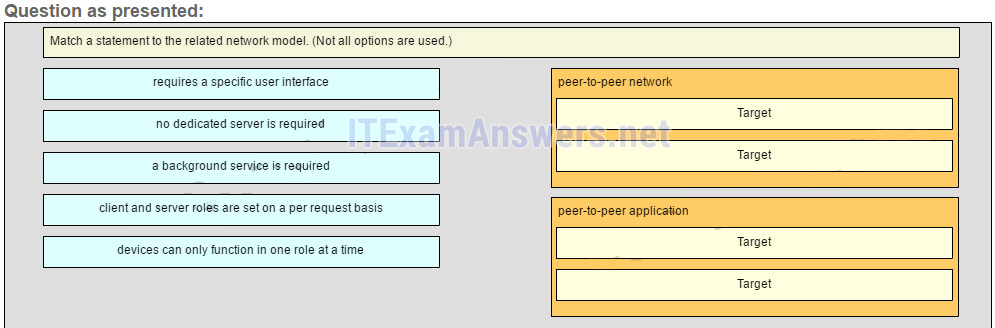
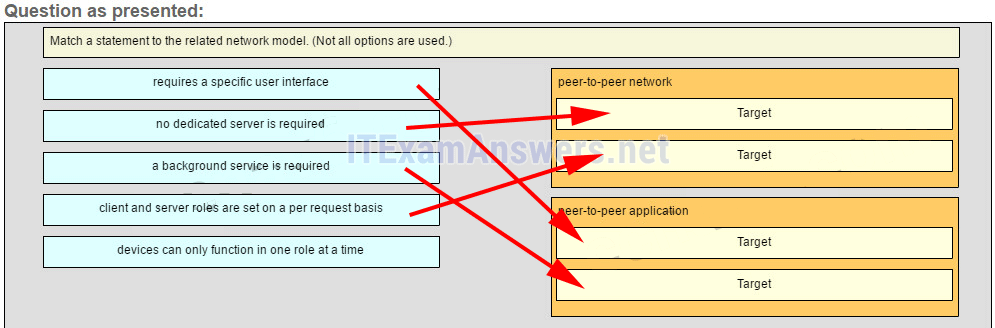
Place the options in the following order:peer-to-peer network
[+] no dedicated server is required
[+] client and server roles are set on a per request basis
peer-to-peer aplication
[#] requires a specific user interface
[#] a background service is required
27. Match the functions to the name of the application. (Not all options are used.)
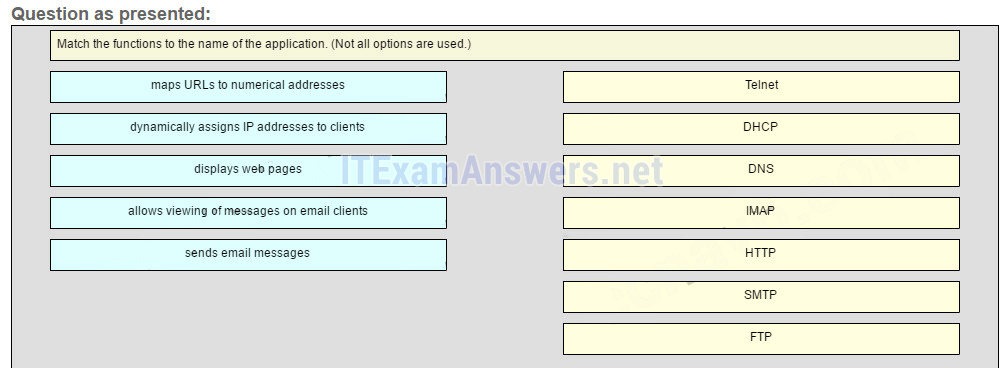
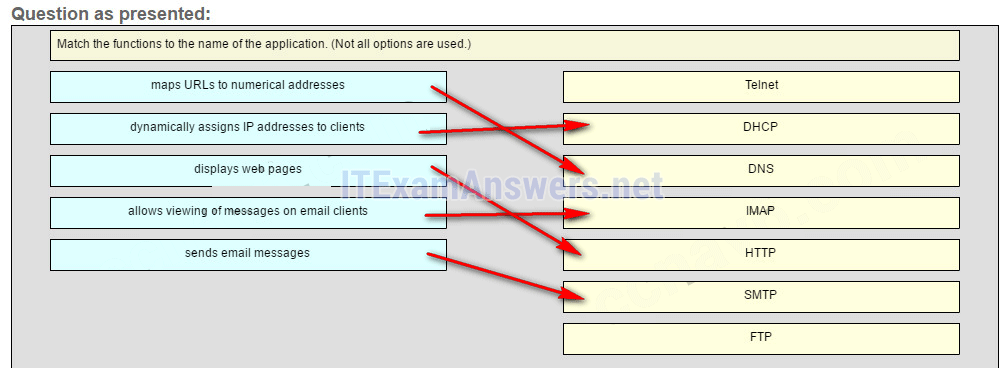
Place the options in the following order:
— not scored —
DHCP -> dynamically assigns IP address to clients
DNS -> maps URLs to numerical addresses
IMAP -> allows viewing of messages on email clients
HTTP -> displays web pages
SMTP -> sends email messages
— not scored —
Older Version
28. Which three layers of the OSI model provide similar network services to those provided by the application layer of the TCP/IP model? (Choose three.)
- physical layer
- session layer
- transport layer
- application layer
- presentation layer
- data link layer
29. Which two tasks are functions of the presentation layer? (Choose two.)
- compression
- addressing
- encryption
- session control
- authentication
30. Select three protocols that operate at the Application Layer of the OSI model. (Choose three.)
- ARP
- TCP
- DSL
- FTP
- POP3
- DHCP
31. A manufacturing company subscribes to certain hosted services from their ISP. The services required include hosted world wide web, file transfer, and e-mail. Which protocols represent these three key applications? (Choose three.)
- FTP
- HTTP
- DNS
- SNMP
- DHCP
- SMTP
32. What are two characteristics of peer-to-peer networks? (Choose two.)
- scalable
- one way data flow
- decentralized resources
- centralized user accounts
- resource sharing without a dedicated server
33. Which two actions are taken by SMTP if the destination email server is busy when email messages are sent? (Choose two.)
- SMTP sends an error message back to the sender and closes the connection.
- SMTP tries to send the messages at a later time.
- SMTP will discard the message if it is still not delivered after a predetermined expiration time.
- SMTP periodically checks the queue for messages and attempts to send them again.
- SMTP sends the messages to another mail server for delivery.
34. A DHCP-enabled client PC has just booted. During which two steps will the client PC use broadcast messages when communicating with a DHCP server? (Choose two.)
- DHCPDISCOVER
- DHCPACK
- DHCPOFFER
- DHCPREQUEST
- DHCPNAK
35. A user accessed the game site www.nogamename.com last week. The night before the user accesses the game site again, the site administrator changes the site IP address. What will be the consequence of that action for the user?
- The user will not be able to access the site.
- The user will access the site without problems.
- The user will have to modify the DNS server address on the local PC in order to access the site.
- The user will have to issue a ping to this new IP address to be sure that the domain name remained the same.
36. Which DNS server in the DNS hierarchy would be considered authoritative for the domain name records of a company named netacad?
- .com
- netacad.com
- mx.netacad.com
- www.netacad.com
37. When would it be more efficient to use SMB to transfer files instead of FTP?
- when downloading large files with a variety of formats from different servers
- when a peer-to-peer application is required
- when the host devices on the network use the Windows operating system
- when downloading large numbers of files from the same server
- when uploading the same file to multiple remote servers
38. Fill in the blank.
What is the acronym for the protocol that is used when securely communicating with a web server? HTTPS
39. Match the DNS record type to the corresponding description. (Not all options are used.)
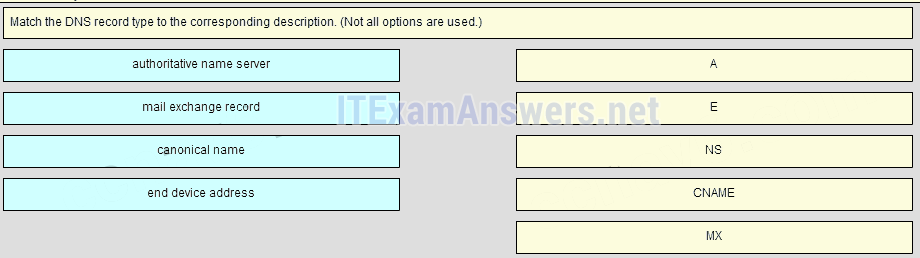
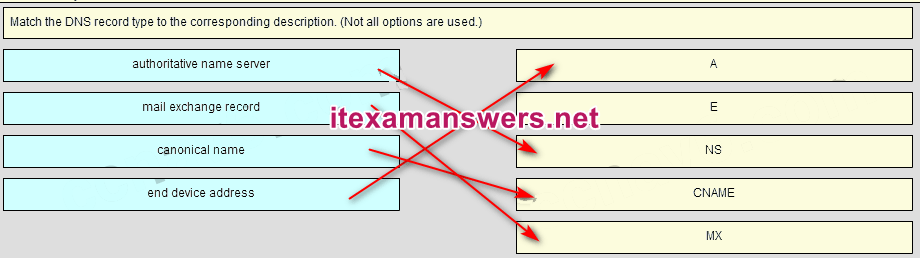
Place the options in the following order:
end device address
– not scored –
authoritative name server
canonical name
mail exchange record
40. Match the purpose with its DHCP message type. (Not all options are used.)
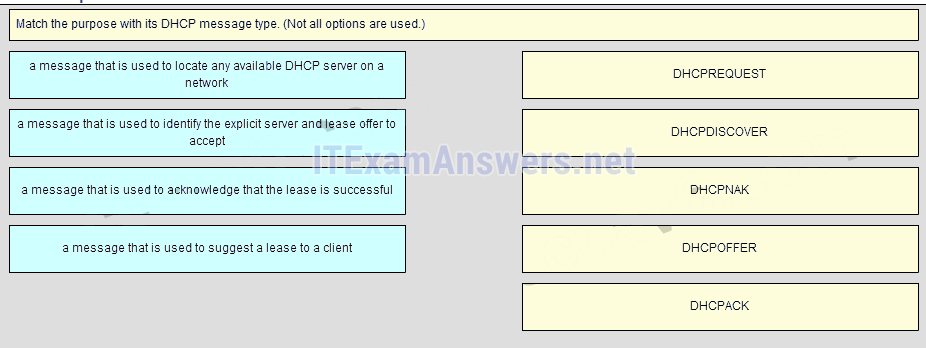
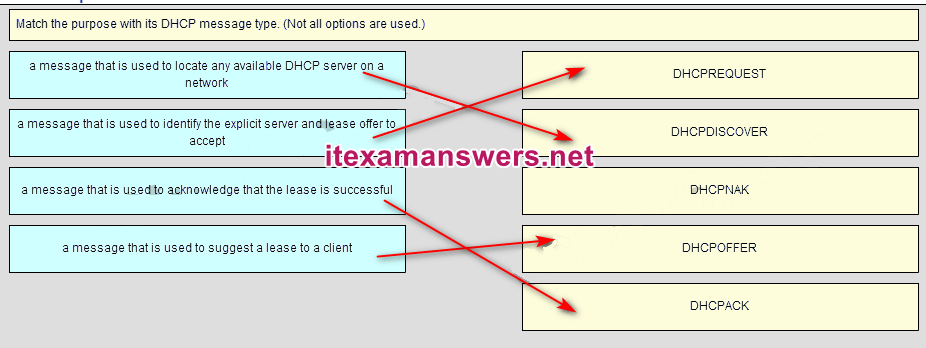
Place the options in the following order:
a message that is used to identify the explicit server and lease offer to accept
a message that is used to locate any available DHCP server on a network
– not scored –
a message that is used to suggest a lease to a client
a message that is used to acknowledge that the lease is successful
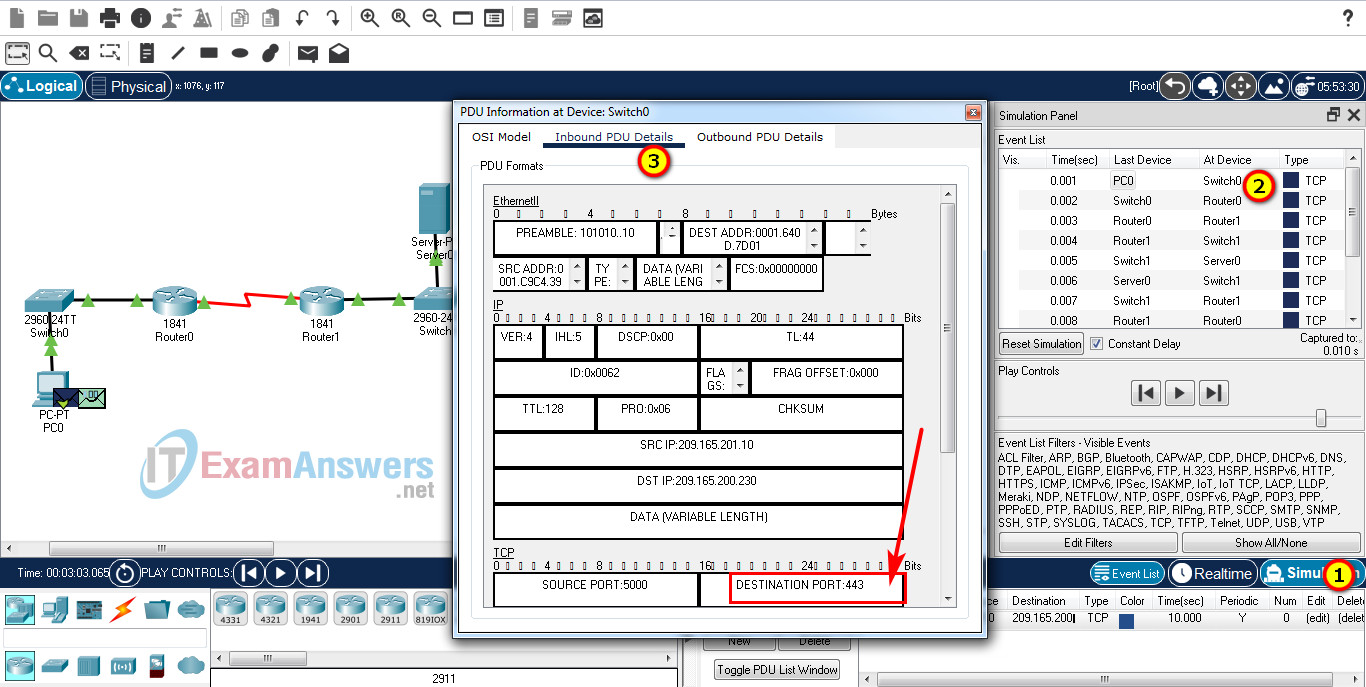
41. Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
What is the application layer service being requested from Server0 by PC0?
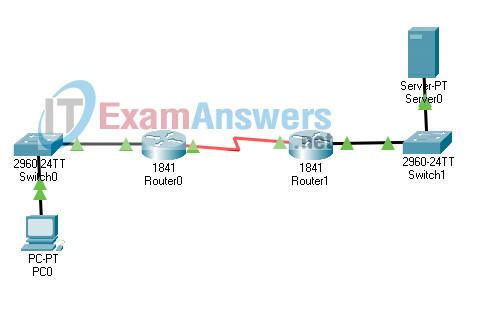
CCNA 1 System Test Course (Version 1.1) – System Test Exam PT
In the Simulation mode, capture the packets. What is the application layer service being requested from Server0 by PC0?
Return to the assessment to answer the question.
- FTP
- DNS
- HTTPS
- HTTP
- SMTP
Explanation: From the PDU, the destination port is 443, which means the service requested is HTTPS.
42. Which protocol is used by Windows for file and printer sharing?
- SMB
- SMTP
- HTTPS
- IMAP

thanks so much
Which protocol is used by Windows for file and printer sharing?
HTTPS
SMB
IMAP
SMTP
Navigation Bar
Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
What is the application layer service being requested from Server0 by PC0?
Thanks for sharing!
Which protocol or service allows network administrators to receive system messages that are provided by network devices?
-NetFlow
-syslog
-SNMP
-NTP
correct is syslog
hii raa
help me naku 100% ratala
very helpfull ,thank you so much
this is very toughest subject….
Something like that I have to be a good day today
Pizdiec useful website😂
thank you
What is a field in the data part of an Ethernet frame?
What is an example of network communication that uses the client-server model?
A workstation initiates an ARP to find the MAC address of a receiving host.
A user uses eMule to download a file that is shared by a friend after the file location is determined.
A workstation initiates a DNS request when the user types http://www.cisco.com in the address bar of a web browser.
A user prints a document by using a printer that is attached to a workstation of a coworker.
i appreciate you
tnx
This question can be worded as so in some exams:
New questions:
11 Which protocol is used by a client to communicate securely with a web server?
IMAP
SMB
SMTP
HTTPS
12 What message type is used by an HTTP client to request data from a web server?
PUT
ACK
POST
GET
What is the function of the Nslookup utility?
to view the network settings on a host
to manually force a client to send a DHCP request
to manually query the name servers to resolve a given host name
to display all cached DNS entries on a host
useful subject.
Very useful and important website.
yes!
kk alage tnx