Objectives
- Using Cisco Express Forwarding Switching
- Understanding Path Control
- Implementing Path Control Using Policy-Based Routing
- Implementing Path Control Using Cisco IOS IP SLAs
Using Cisco Express Forwarding Switching
- Describe the different switching mechanisms that a Cisco router uses
- Describe how Cisco Express Forwarding (CEF) works
- Describe how to verify that CEF is working
- Describe how to verify the content of the CEF tables
- Describe how to enable and disable CEF by interface and globally
Control and Data Plane
- A Layer 3 device employs a distributed architecture in which the control plane and data plane are relatively independent.
- For example, the exchange of routing protocol information is performed in the control plane by the route processor, whereas data packets are forwarded in the data plane by an interface micro-coded processor.
- The main functions of the control layer between the routing protocol and the firmware data plane microcode include the following:
- Managing the internal data and control circuits for the packet-forwarding and control functions.
- Extracting the other routing and packet-forwarding-related control information from Layer 2 and Layer 3 bridging and routing protocols and the configuration data, and then conveying the information to the interface module for control of the data plane.
- Collecting the data plane information, such as traffic statistics, from the interface module to the route processor.
- Handling certain data packets that are sent from the Ethernet interface modules to the route processor.
Cisco Switching Mechanisms
- Process switching
- Fast switching
- Cisco Express Forwarding
Process switching
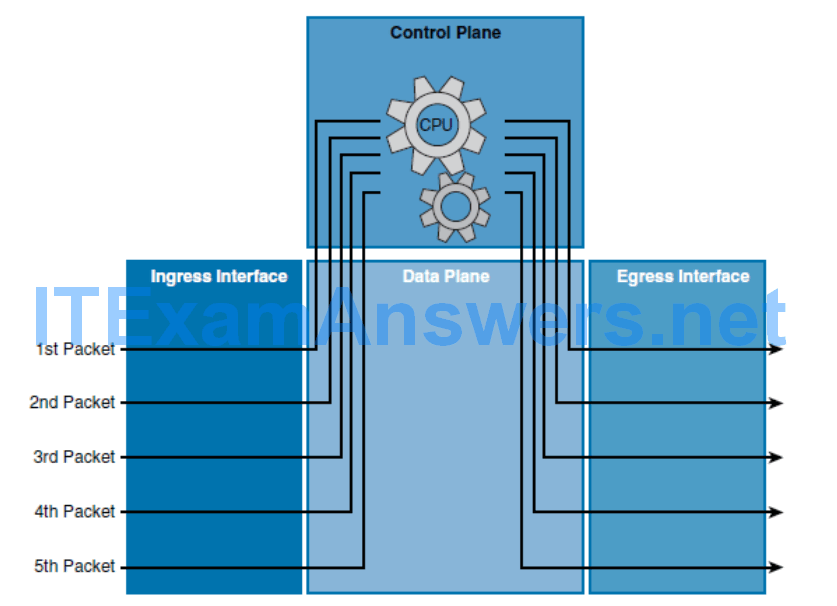
- This switching method is the slowest of the three methods.
- Every packet is examined by the CPU in the control plane and all forwarding decisions are made in software.
- When a packet arrives on the ingress interface, it is forwarded to the control plane where the CPU matches the destination address with an entry in its routing table.
- It then determines the exit interface and forwards the packet.
- The router does this for every packet, even if the destination is the same for a stream of packets.
- Process switching is the most CPU-intensive method that is available in Cisco routers. It greatly degrades performance and is generally used only as a last resort or during troubleshooting.
Fast switching
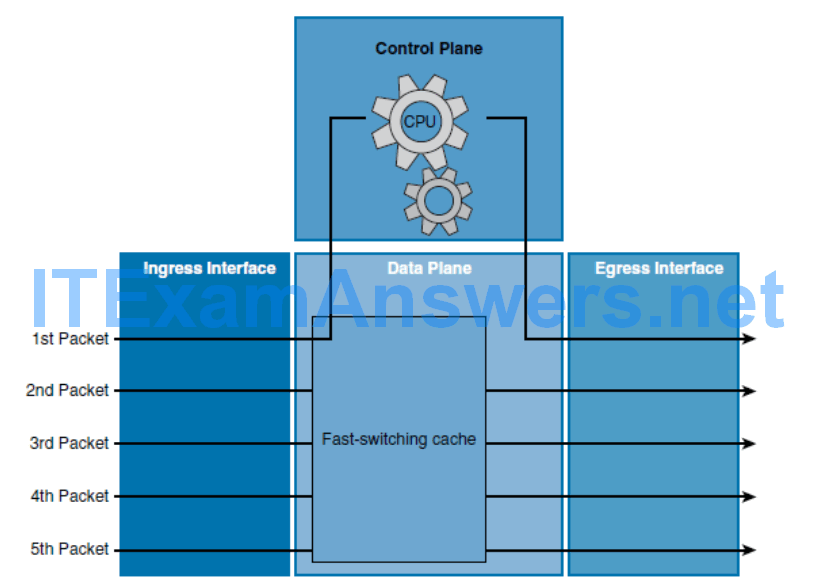
- This switching method is faster than process switching.
- With fast switching, the initial packet of a traffic flow is process switched.
- This means that it is examined by the CPU and the forwarding decision is made in software.
- However, the forwarding decision is also stored in the data plane hardware fast-switching cache.
- When subsequent frames in the flow arrive, the destination is found in the hardware fast-switching cache and the frames are then forwarded without interrupting the CPU.
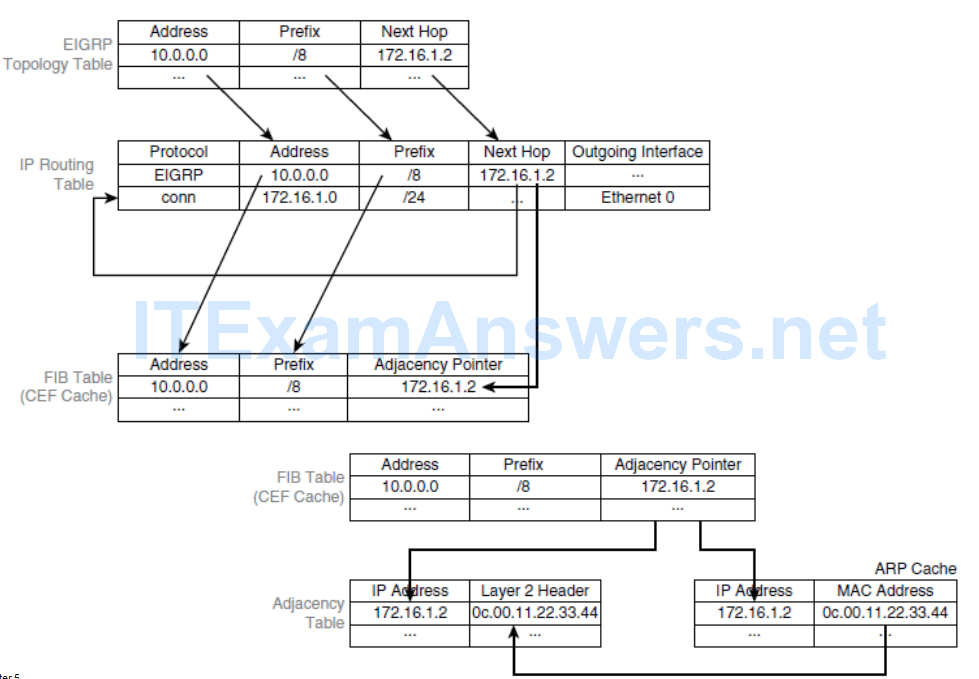
Cisco Express Forwarding
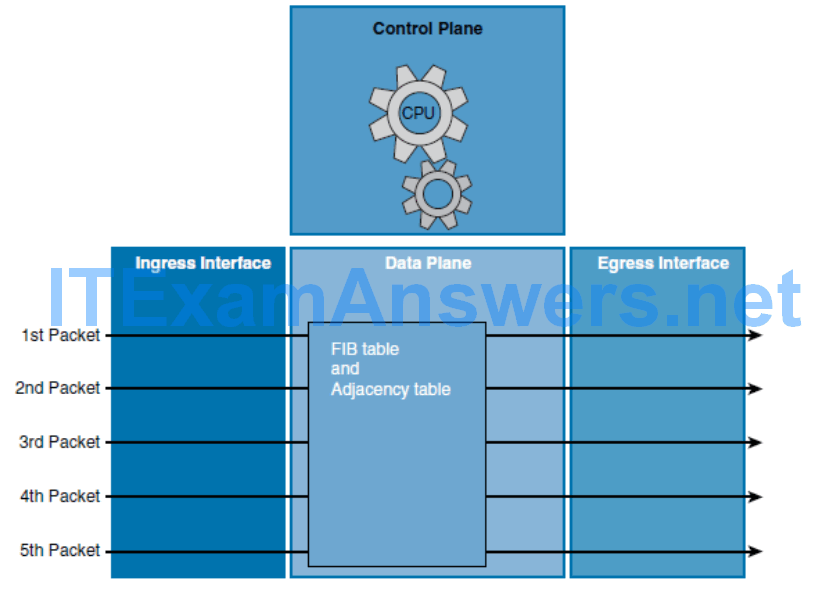
- This switching method is the fastest switching mode and is less CPU-intensive than fast switching and process switching.
- The control plane CPU of a CEF-enabled router creates two hardware-based tables called the Forwarding Information Base (FIB) table and an adjacency table using Layer 3 and 2 tables including the routing and Address Resolution Protocol (ARP) tables.
- When a network has converged, the FIB and adjacency tables contain all the information a router would have to consider when forwarding a packet.
- These two tables are then used to make hardware-based forwarding decisions for all frames in a data flow, even the first frame.
- The FIB contains precomputed reverse lookups and next-hop information for routes, including the interface and Layer 2 information.
- While CEF is the fastest switching mode, some limitations apply. Some features are not compatible with CEF. In some rare instances, too, the functions of CEF can actually degrade performance.
- Note Packets that cannot be CEF switched, such as packets destined to the router itself, are “punted.” This means that the packet will be fast switched or process switched.
Process and Fast Switching
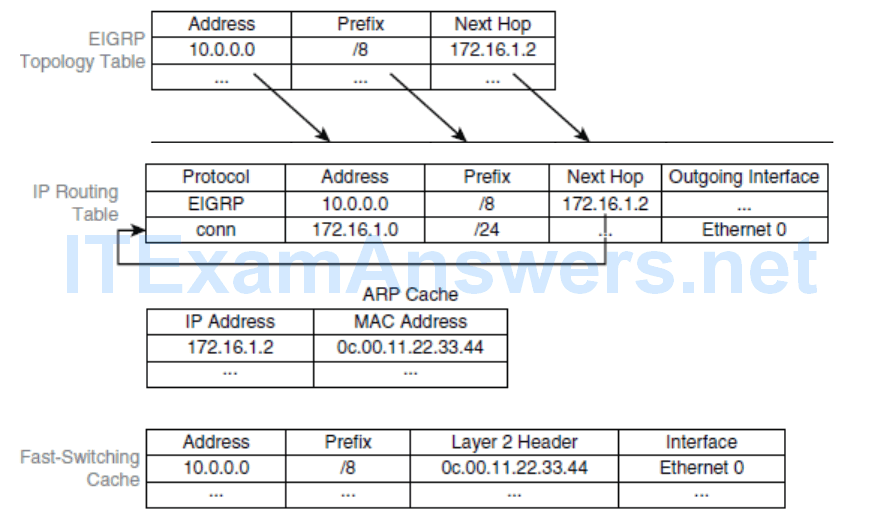
- When the first packet of a packet flow arrives for destination 10.0.0.0/8, the router initially looks for the destination in its fast-switching cache. Because the destination is not in the fast-switching cache, the router must perform process switching.
- Therefore, a full routing table lookup is performed. The process performs a recursive lookup to find the outgoing interface.
- Process switching might trigger an ARP request or find the Layer 2 address in the ARP cache. For example, the MAC address of 172.16.1.2 was found in the ARP cache, as shown in Figure 5-6
- Specifically, an entry is created in the fast-switching cache to ensure that the subsequent packets for the same destination prefix will be fast switched.
- All subsequent packets for the same destination are fast switched:
- The switching occurs in the interrupt code. (The packet is processed immediately.)
- Fast destination lookup is performed (no recursion).
- The encapsulation uses a pregenerated Layer 2 header that contains the destination IP Address and Layer 2 source MAC address. (No ARP request or ARP cache lookup is necessary.)
Cisco Express Forwarding
- CEF separates the control plane software from the data plane hardware, thereby achieving higher data throughput.
- The control plane is responsible for building the FIB table and adjacency tables in software.
- The data plane is responsible for forwarding IP unicast traffic using hardware.
CEF FIB Table
- The FIB is derived from the IP routing table and is arranged for maximum lookup throughput.
- CEF IP destination prefixes are stored from the most-specific to the least specific entry.
- The FIB lookup is based on the Layer 3 destination address prefix (longest match), so it matches the structure of CEF entries. When the CEF FIB table is full, a wildcard entry redirects frames to the Layer 3 engine.
- The FIB table is updated after each network change, but only once, and contains all known routes; there is no need to build a route cache by central-processing initial packets from each data flow.
- Each change in the IP routing table triggers a similar change in the FIB table because it contains all next-hop addresses that are associated with all destination networks.
CEF Adjancency Table
- CEF also caches Layer 2 next-hop addresses and frame header rewrite information for all FIB entries in the adjacency table.
- The adjacency table is derived from the ARP table, and it contains Layer 2 header rewrite (MAC) information for each next hop that is contained in the FIB.
- Each time that an adjacency entry is created (such as through ARP), a link-layer header for that adjacent node is precomputed and is stored in the adjacency table.
- CEF uses a specific process to build forwarding tables in the hardware and then uses the information from those tables to forward packets at line speed.
CEF Exceptions
- Not all packets can be CEF switched and processed in the hardware. When traffic cannot be processed in the hardware, it must be received by software processing of the Layer 3 engine.
- Some examples of IP exception packets are packets that have the following characteristics:
- They use IP header options.
- They have an expiring IP Time To Live (TTL) counter.
- They are forwarded to a tunnel interface.
- They arrive with unsupported encapsulation types.
- They are routed to an interface with unsupported encapsulation types.
- They exceed the maximum transmission unit (MTU) of an output interface and mustbe fragmented.
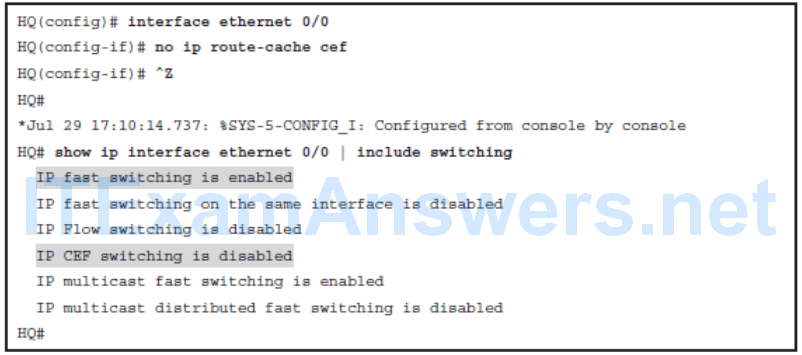
Enable and Disable CEF by Interface
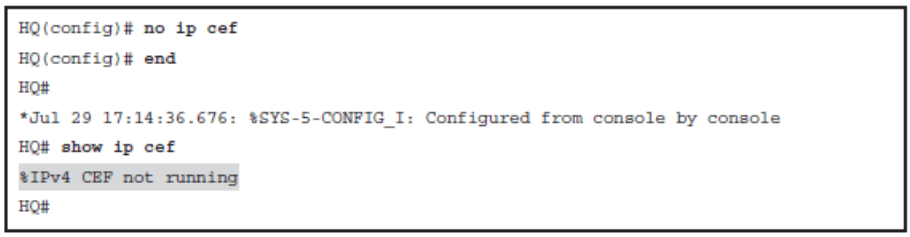
Enable and Disable CEF Globally
Understanding Path Control
- Identify the need for path control
- Describe how to use policy-based routing (PBR) to control path selection
- Describe how to use IP service-level agreement (IP SLA) to control path selection
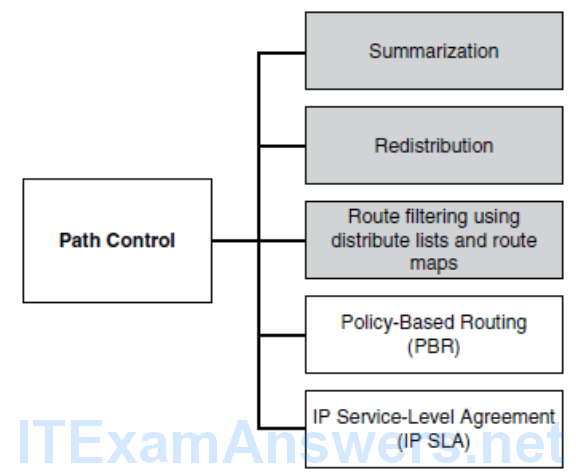
The Need for Path Control
- Path control tools can be used to change the default destination forwarding and optimize the path of the packets for some specific application.
- Other examples of path control include switching traffic to the backup link if there is a primary link failure, or forwarding some traffic to the backup link if the primary link is congested.
- Path control mechanisms can improve performance in such a situation.
- Similarly, load balancing can divide traffic among parallel paths.
- It is important to provide predictable and deterministic control over traffic patterns.
- Unfortunately, there is not a “one-command” solution to implement path control.
- Networks are designed to use redundancy to provide high availability. However, having redundancy does not guarantee resistance to failure.
- The use of multiple routing protocols and redundant connectivity options can result in inefficient paths for forwarding packets to their destinations.
- Each routing protocol has a different administrative distance, metric, and convergence time. Suboptimal routing often occurs after redistribution because redistribution resets the administrative distance and metric.
- Convergence time is also important. First, protocols converge in different ways from each other and for different network designs. Second, slow convergence can result in an application sending traffic timeouts before a backup path is found to a destination. Path control is required to avoid performance issues and to optimize paths.
The Need for Path Control
- You can use all of these tools as part of an integrated strategy to implement path control.
Implementing Path Control Using Policy-Based Routing
- PBR enables the administrator to define a routing policy other than basic destination-based routing using the routing table.
- With PBR, route maps can be used to match source and destination addresses, protocol types, and end-user applications.
- When a match occurs, a set command can be used to define items, such as the interface or next-hop address to which the packet should be sent.
PBR Features
Source-based transit-provider selection
- PBR policies can be implemented by ISPs and other organizations to route traffic that originates from different sets of users through different Internet connections across the policy routers.
QoS
- PBR policies can be implemented to provide quality of service (QoS) to differentiated traffic by setting the type of service (ToS) values in the IP packet headers in routers at the periphery of the network and then leveraging queuing mechanisms to prioritize traffic in the network’s core or backbone.
Cost savings
- PBR policies can be implemented to direct the bulk traffic associated with a specific activity to use a higher-bandwidth, high-cost link for a short time and to continue basic connectivity over a lower-bandwidth, low-cost link for interactive traffic.
Load sharing
- PBR policies can be implemented based on the traffic characteristics to distribute traffic among multiple paths.
PBR is a powerful and flexible tool that offers significant benefits in terms of implementing user-defined policies to control traffic in the internetwork.
PBR adds flexibility in a difficult-to-manage environment by providing the ability to route traffic that is based on network needs.
It also provides solutions in cases where legal, contractual, or political constraints dictate that traffic be routed through specific paths.
Steps for Configuring PBR
1.Enable PBR by configuring a route map using the route-map global configuration command.
2.Implement the traffic-matching configuration, specifying which traffic will be manipulated. This is done using the match commands within the route map.
3.Define the action for the matched traffic. This is done using the set commands within the route map.
4.Optionally, fast-switched PBR or CEF-switched PBR can be enabled.
5.Apply the route map to incoming traffic or to traffic locally generated on the router using the ip policy route-map interface configuration command.
Fast-switched PBR must be enabled manually. CEF-switched PBR is automatically enabled when CEF switching is enabled (which it is by default in recent IOS versions) and PBR is enabled.
6. Verify PBR configuration with basic connectivity and path verification commands, as well as policy routing show commands.
Configuring PBR – Route-Map
- If the statement is marked as permit , such as in route-map MY-MAP permit 10 , packets that meet all the match criteria are policy-based routed.
- If the statement is marked as deny , such as in route-map MY-MAP deny 10 , a packet meeting the match criteria is not policy-based routed. Instead, it is sent through the normal forwarding channels and destination-based routing is performed.
- If no match is found in the route map, the packet is not dropped. It is forwarded through the normal routing channel, which means that destination-based routing is performed.
PBR match Commands
PBR set Commands

Configuring PBR Example
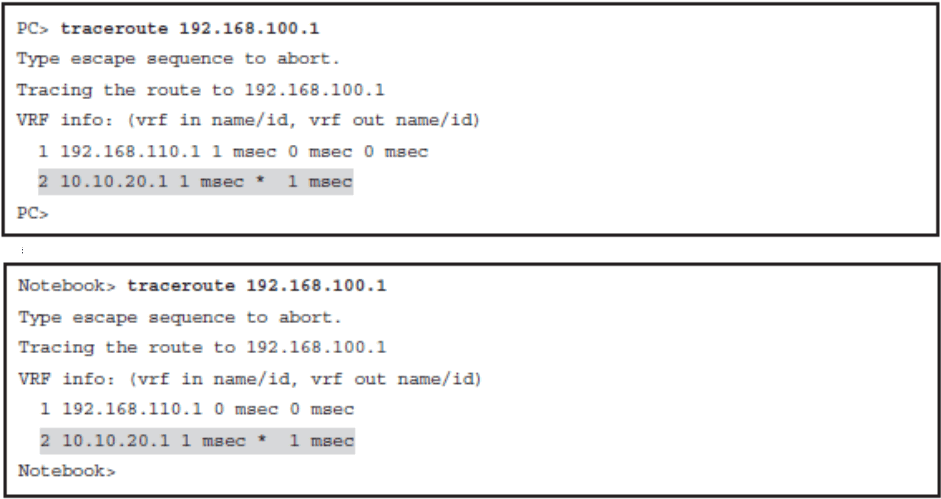
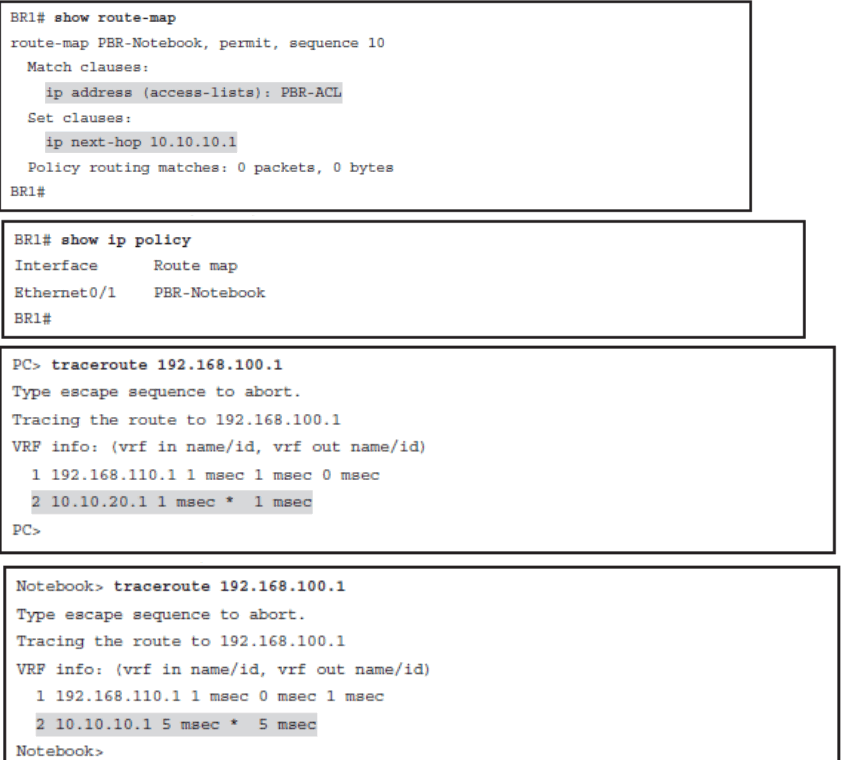
- Verify normal traffic paths as selected by the traditional destination-based routing
- Configure PBR to alter the traffic flow for one client station
- Verify both the PBR configuration and the new traffic path
Verify Normal Traffic Paths

Configure PBR to Alter the Traffic Flow from the Notebook
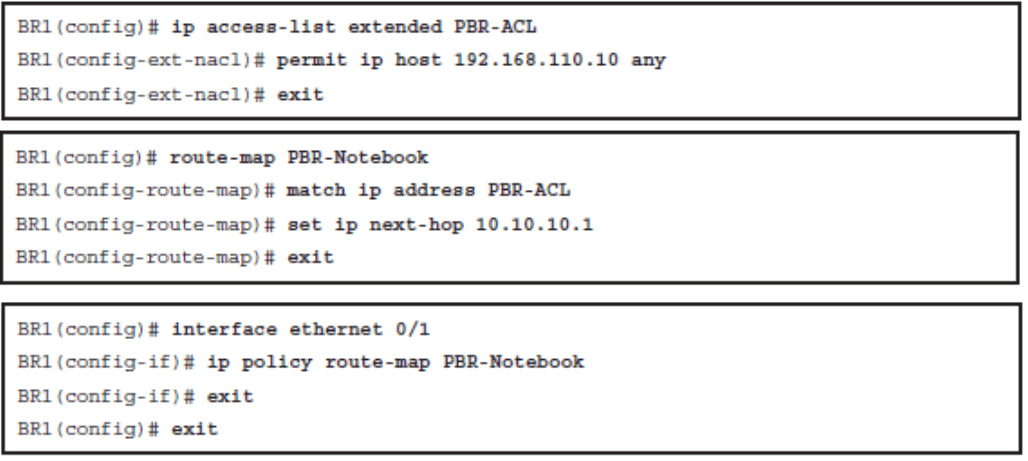

Verify the PBR Configuration and Traffic Path
Implementing Path Control Using Cisco IOS IP SLAs
- PBR is a static path control mechanism. It cannot respond dynamically to changes in network health.
IP SLA Features
- Cisco IOS IP SLAs perform network performance measurement within Cisco devices.
- The IP SLAs use active traffic monitoring (generation of traffic in a continuous, reliable, and predictable manner) for measuring network performance.
- Cisco IOS IP SLAs actively send simulated data across the network to measure performance between multiple network locations or across multiple network paths.
- The information collected includes data about response time, one-way latency, jitter, packet loss, voice-quality scoring, network resource availability, application performance, and server response time.
- In its simplest form, Cisco IOS IP SLAs verify whether a network element, such as an IP address on a router interface or an open TCP port on an IP host, is active and responsive.
Cisco IOS IP SLA Sources and Targets
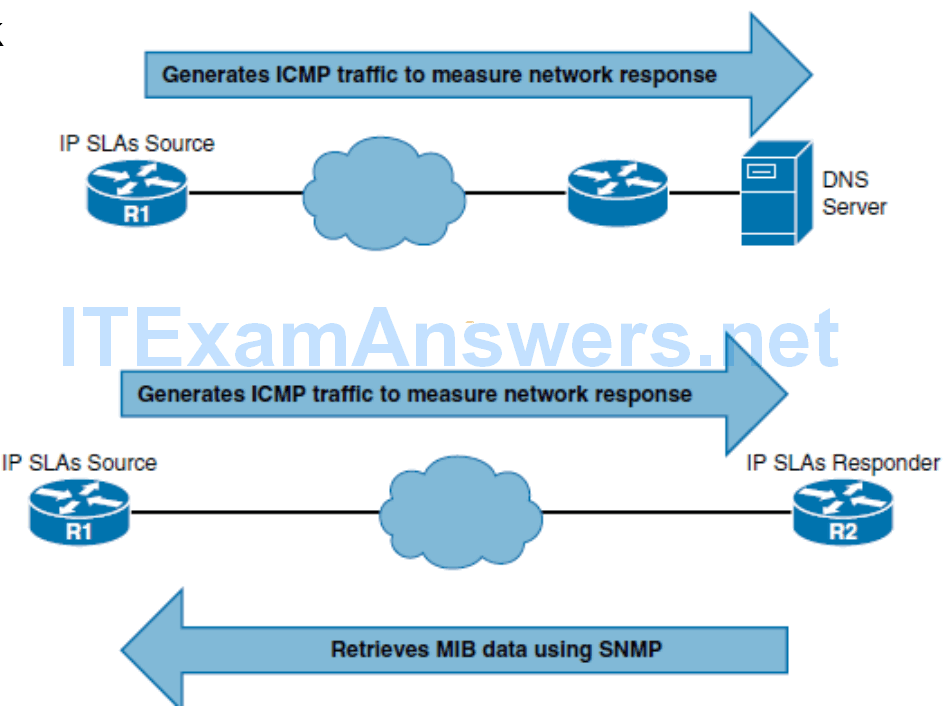
- However, the IP SLA responder can be configured to capture specific data that can be retrieved by the source using the CLI or through an SNMP tool that supports the operation of IP SLAs. The IP SLA measurement accuracy is improved when the target is an IP SLA responder.
Steps for Configuring IP SLAs
- Step 1. Define one or more IP SLA operations (or probes).
- Step 2. Define one or more tracking objects to track the state of IOS IP SLA operations.
- Step 3. Define the action associated with the tracking object.
Step 1. Configuring Cisco IOS IP SLA Operations
- Use the ip sla operation-number global configuration command to begin configuring a Cisco IOS IP SLA operation and to enter IP SLA configuration mode. The operationnumber is the identification number of the IP SLA operation to be configured.
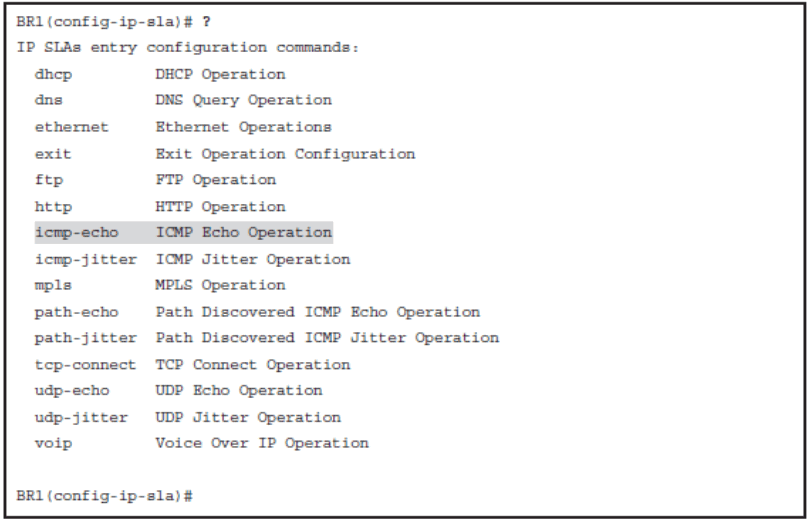
IP SLA icmp-echo
- The complete command syntax is icmp-echo { destination-ip-address | destinationhostname} [ source-ip { ip – address | hostname } | source-interface interface-name ].
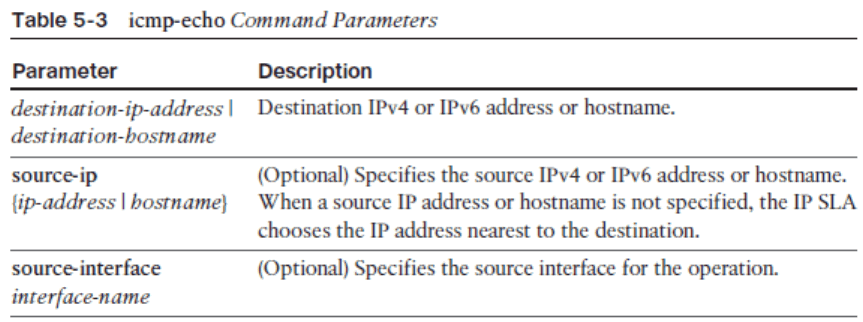
IP SLA ICMP Echo Configuration Mode Commands

Schedule the IP SLA Operation
- Once a Cisco IP SLA operation is configured, it needs to be scheduled using the ip sla schedule global configuration command.
ip sla schedule operation-number [ life { forever | seconds }] [ start-time { hh:mm [ :ss ] [ month day | day month ] | pending | now | after hh:mm:ss }] [ ageout seconds ] [ recurring ]
Step 2: Configuring Cisco IOS IP SLA Tracking Objects
- Use the track object-number ip sla operation-number { state | reachability } global configuration command to track the state of an IOS IP SLA operation, and enter track configuration mode.
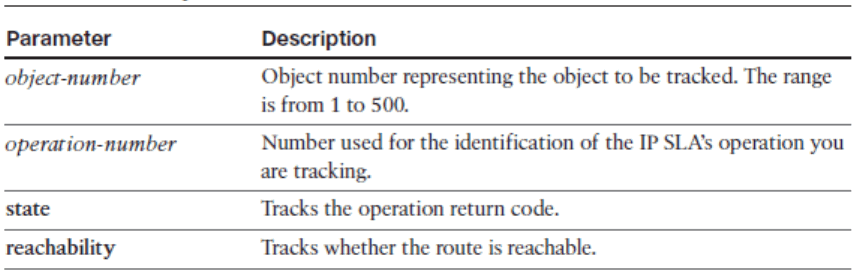
delay Command Parameters
- Once in IP SLA track configuration mode, use the optional delay { up seconds [ down seconds ] | [ up seconds ] down seconds } track configuration command to specify a period of time to delay communicating state changes of a tracked object.

Step 3: Defining an Action Associated with a Tracking Object
- Many types of actions can be associated with a tracked object.
- A simple path control action is to use the ip route prefix mask { ip-address | interface-type interface-number [ ip-address ]} [ track number ] global configuration command.
- The command can be used with the track keyword to establish a static route that tracks an object.
- To display configuration values including all defaults for all Cisco IOS IP SLA operations, or for a specified operation, use the show ip sla configuration [ operation ] command. The operation parameter is the number of the IP SLA operation for which the details will be displayed.
Configuring IP SLA Example
- The static route to ISP1a (ISP-1), which has been assigned an administrative distance of 2
- The static route to ISP2a (ISP-2), which has been assigned an administrative distance of 3
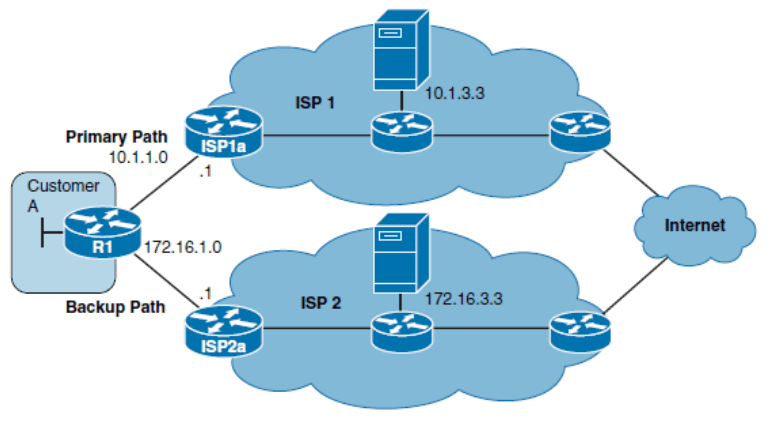
In the example, you will
- Configure an IP SLA operation with the ISP 1 DNS server
- Define a tracking object assign an action
- Configure an IP SLA operation with the ISP 2 DNS server
- Define a tracking object assign an action
Configure IP SLA and Track Object for ISP 1
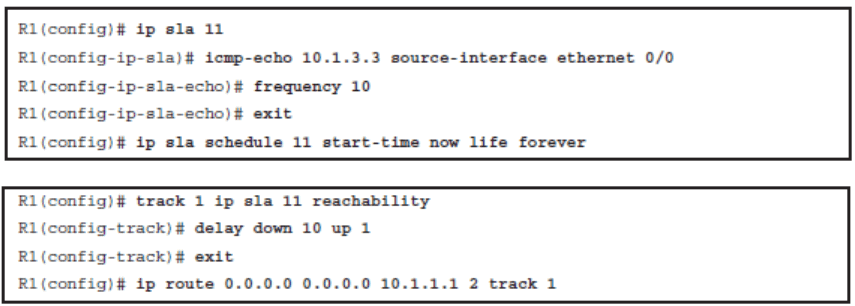
Configure IP SLA and Track Object for ISP 2
Configuring PBR and IP SLA Example
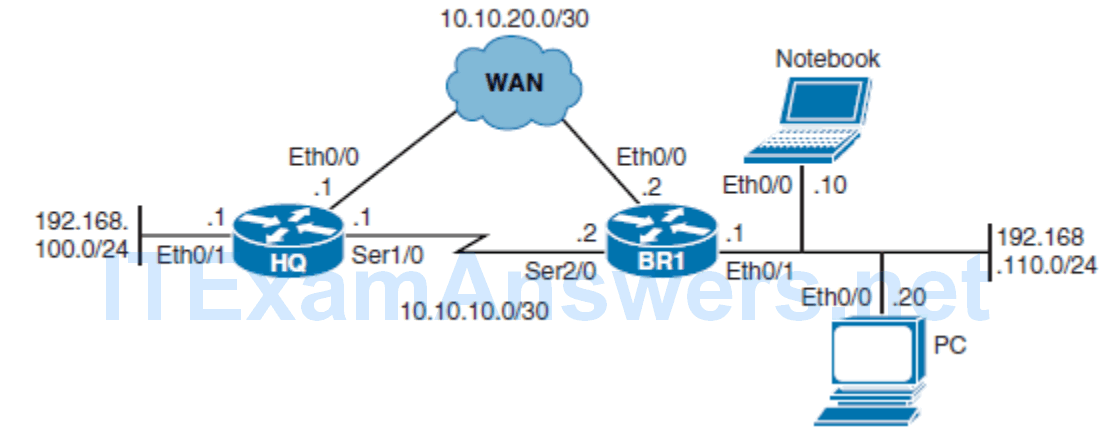
- In this scenario, traffic paths for the clients at first branch office (router BR1) will be optimized using PBR and IP SLA. EIGRP is already configured between HQ and BR1, and all traffic flows over the Ethernet WAN link because it has the lowest EIGRP metric route.
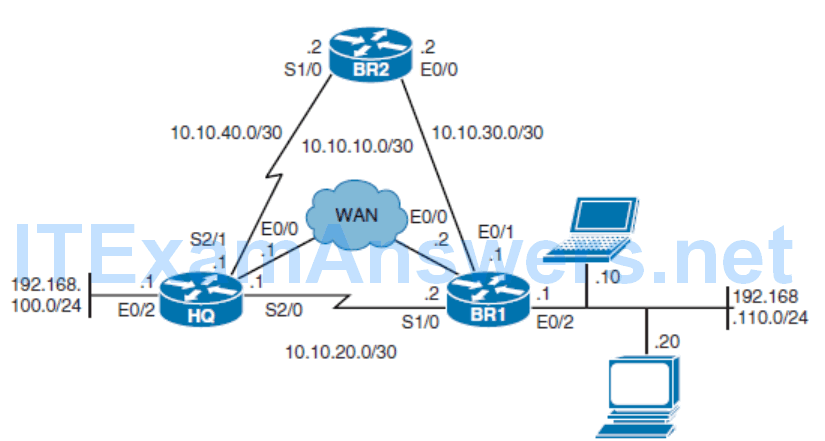
In the example, you will
The new network policy for BR1 dictates that
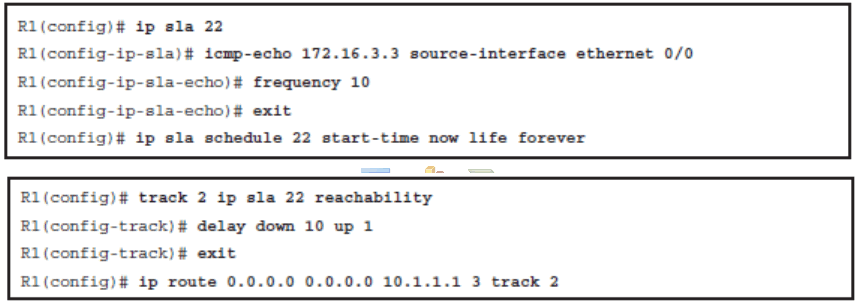
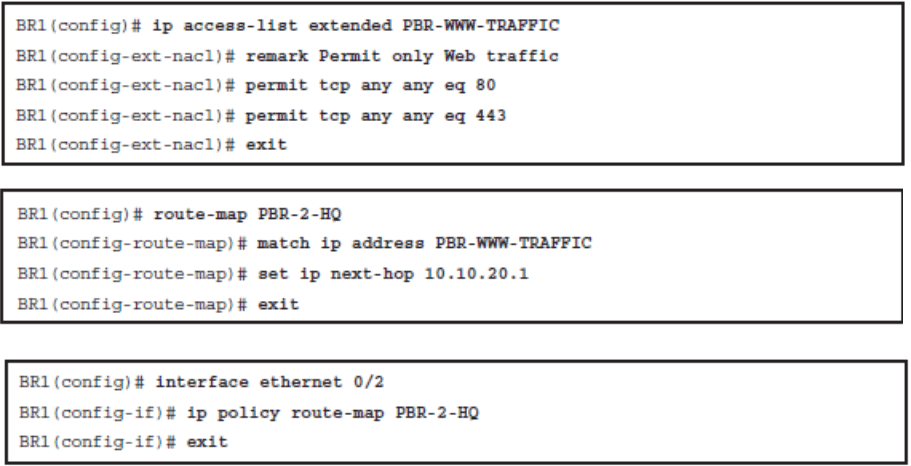
- Web traffic to the HQ site should be redirected over the serial link.
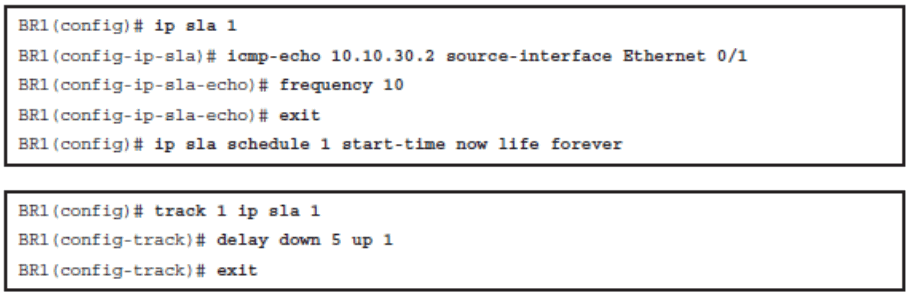
- All other traffic from Notebook should go via BR2 but only if BR2 is reachable.
In the example, you will
- Redirect web traffic from clients on the BR1 router going to the HQ router over the serial link using PBR
- Ensure that BR2 is reachable by using an IP SLA ICMP echo test to its WAN interface
- Redirect all other traffic from Notebook to router BR2 if BR2 is reachable
Redirecting Web Traffic from BR1 to HQ Using PBR
Ensuring That BR2 Is Reachable Using IP SLA
Redirect Traffic from Notebook to BR2 If Reachable
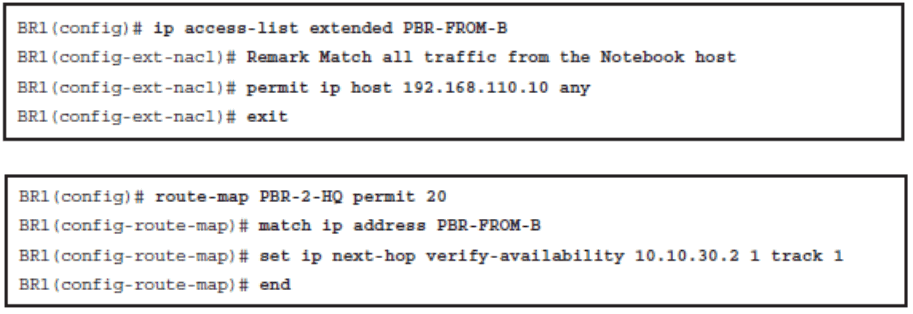
Verify Route Maps
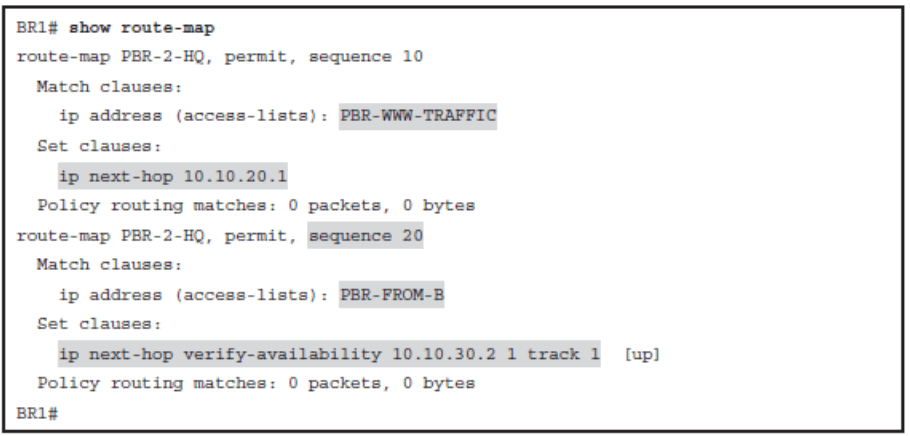
Verify That the Route Map Is Applied
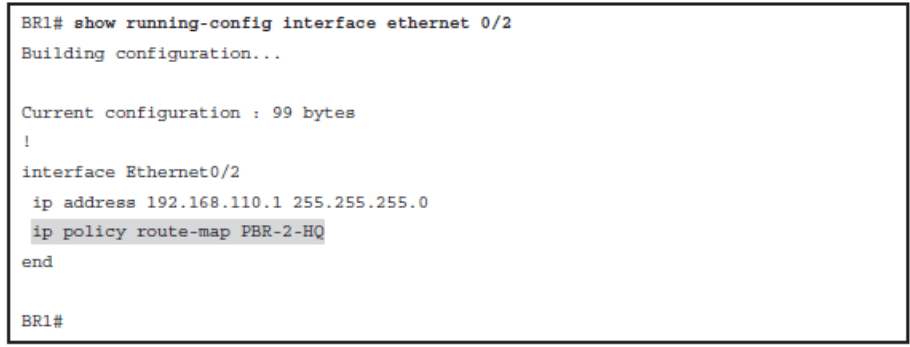
Verify IP SLA Operations
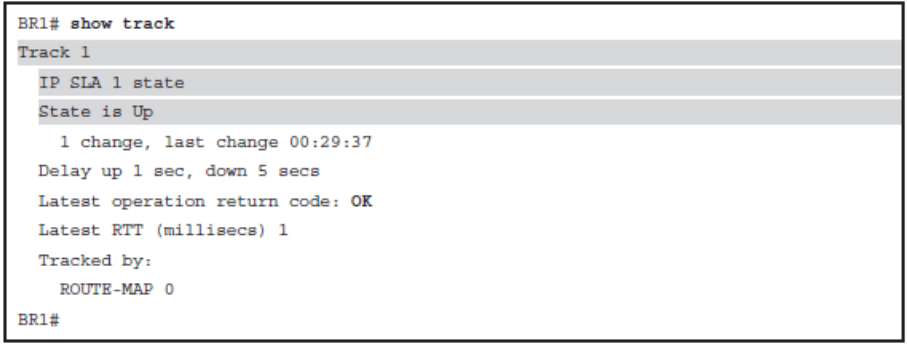
Verify Tracking Objects
Chapter 5 Summary
Packet-switching mechanisms on a Cisco IOS platform, including process switching, fast switching, and CEF switching.
Overview of path control tools, including PBR and Cisco IOS IP SLAs.
Using PBR to control path selection, providing benefits including source-based transit provider selection, QoS, cost savings, and load sharing. PBR is applied to incoming packets; enabling PBR causes the router to evaluate all packets incoming on the interface using a route map configured for that purpose.
Configuring and verifying PBR, including the following steps:
- Choose the path control tool to use; for PBR, route-map commands are used
- Implement the traffic-matching configuration, specifying which traffic will be manipulated; match commands are used within route maps
- Define the action for the matched traffic, using set commands within route maps
- Apply the route map to incoming traffic or to traffic locally generated on the router
- Verify path control results, using show commands
Cisco IOS IP SLAs, which use active traffic monitoring, generating traffic in a continuous, reliable, and predictable manner, to measure network performance. IOS IP SLAs can be used in conjunction with other tools, including the following:
- Object tracking, to track the reachability of specified objects
- Cisco IOS IP SLAs probes, to send different types of probes toward the desired objects
- Static routes with tracking options, as a simpler alternative to PBR
- Route maps with PBR, to associate the results of the tracking to the routing process
Cisco IOS IP SLA terminology, including the following:
- All the Cisco IOS IP SLA measurement probe operations are configured on the IP SLA source, either by the CLI or through an SNMP tool that supports IP SLA operation. The source sends probe packets to the target.
- There are two types of IP SLA operations: those in which the target device is running the IP SLA responder component, and those in which the target device is not running the IP SLA responder component (such as a web server or IP host).
- An IP SLA operation is a measurement that includes protocol, frequency, traps, and thresholds.
Configuring and verifying IOS IP SLAs.
