IoT Security 1.1 Chapter 4 Quiz Exam Answers 1. Why would an engineer only use very short-range radios to allow sensor data to travel from node to node until the data reaches the IoT gateway? increased bandwidth channel requirements power constraints high availability 2. A home owner recently …
IoT Security 1.1 Chapter 3 Quiz Answers 1. Which type of vulnerability is present when a programmer does not account for the size of the input that a user might enter? backdoor installation denial of service out of date firmware buffer overflow 2. Which type of memory media …
IoT Security 1.1 Chapter 2 Quiz Answers 1. Which domain of the ETSI model includes management functions such as data analytics and connectivity management? application M2M transport network 2. Which layer of the OSI model contains protocols used for process-to-process communications? physical data link transport application 3. What …
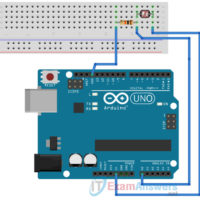
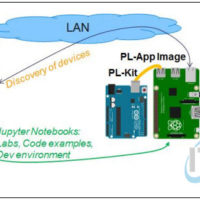
IoT Security 1.1 Chapter 1 Quiz Exam Answers 1. What tool is used by nefarious individuals or groups to accelerate reconnaissance of internet-connected devices? Shodan DoS Mirai DDoS 2. Which storage medium is used to hold the PL-App image on a Raspberry Pi? SSD µSD card HDD USB …
IoT Fundamentals Connecting Things Exam Answers Connecting Things Chapter 1 Quiz Answers Connecting Things Chapter 2 Quiz Answers Connecting Things Chapter 3 Quiz Answers Connecting Things Chapter 4 Quiz Answers Connecting Things Chapter 5 Quiz Answers Connecting Things Chapter 6 Quiz Answers IoT Connecting Things FINAL Exam Answers
The DevNet Associate course uses several virtual machines (VMs) to create the lab experiences. Use the links below to download the course specific VMs. Two labs are included in the course that detail the installation and setup steps for the VMs. Description File Name DevNet Associate VM DEVASC_VM.OVA …
6.4.1.7 Lab – Diagram Business Models (Instructor Version) Objectives In this lab, you will diagram an IoT business model. Background / Scenario The IoT is comprised of the networked connections between people, data, and things. These networked connections require the six pillars of the IoT in order to …
6.3.1.11 Lab – Record sunrise and sunset in Google Calendar using IFTTT (Instructor Version) Lab Topology Objectives Learn how to leverage public cloud services to integrate machines with cloud applications Background In this lab you will learn how to offload the complexity of working with various cloud applications …
6.3.1.9 Lab – Create a Sequence Diagram for Your Project (Answers) Topology Objectives Use WebSequenceDiagrams to Describe a Process Save, export, print, and share the diagram Background / Scenario WebSequenceDiagrams is a website which allows users to diagram interactions between objects. In this lab, you will create a …
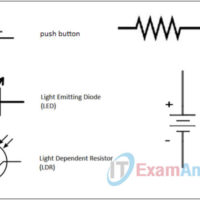
6.3.1.8 Lab – Draw an Electric Schematic for Your Project (Instructor Version) Objectives Identify the components to use Draw the circuit Background / Scenario Electronic schematics provide a way to visually represent a circuit before connecting all of the components. There are several common symbols available for representing …