Packet Tracer – Troubleshooting IPv6 ACLs (Instructor Version)
Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only.
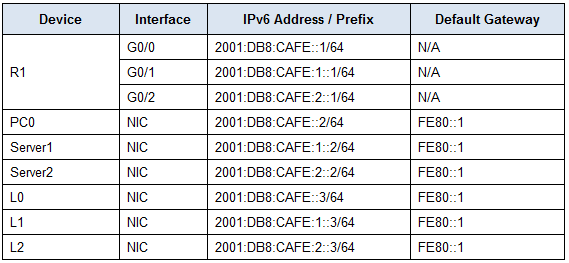
Topology
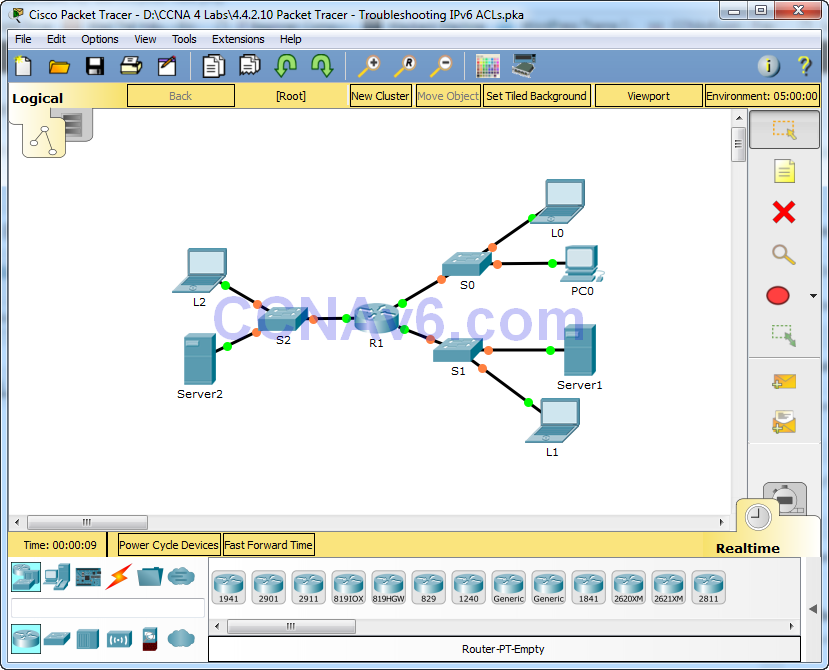
Addressing Table
Objectives
Part 1: Troubleshoot HTTP Access
Part 2: Troubleshoot FTP Access
Part 3: Troubleshoot SSH Access
Scenario
The following three polices have been implemented on the network:
· Hosts from the 2001:DB8:CAFÉ::/64 network do not have HTTP access to the other networks.
· Hosts from the 2001:DB8:CAFÉ:1::/64 network are prevented from access to the FTP service on Server2.
· Hosts from the 2001:DB8:CAFE:1::/64 and 2001:DB8:CAFE:2::/64 networks are prevented from accessing R1 via SSH.
No other restrictions should be in place. Unfortunately, the rules that have been implemented are not working correctly. Your task is to find and fix the errors related to the access lists on R1.
Note: To access R1 and the FTP servers, use the username user01 and password user01pass.
Part 1: Troubleshoot HTTP Access
Hosts from the 2001:DB8:CAFE::/64 network are intentionally unable to access the HTTP service, but should not be otherwise restricted.
Step 1: Determine the ACL problem.
As you perform the following tasks, compare the results to what you would expect from the ACL.
a. Using L0, L1, and L2, attempt to access HTTP services of Server1 and Server2.
b. Using L0, ping Server1 and Server2.
c. Using PC0, access the HTTPS services of Server1 and Server2.
d. View the running configuration on R1. Examine access list G0-ACCESS and its placement on the interfaces. Is the access list placed on the correct interface and in the correct direction? Is there any statement in the list that permits or denies traffic to other networks? Are the statements in the correct order?
e. Run other tests as necessary.
Step 2: Implement a solution.
Make adjustments to access lists to fix the problem.
R1(config)# ipv6 access-list G0-ACCESS R1(config-ipv6-acl)# permit ipv6 any any
Step 3: Verify the problem is resolved and document the solution.
If the problem is resolved, document the solution; otherwise return to Step 1.
No traffic is getting through because of the implicit deny any. Added a permit ipv6 any any to the G0-ACCESS.
Part 2: Troubleshoot FTP Access
Hosts from the 2001:DB8:CAFE:1::/64 network are prevented from accessing the FTP service of Server2, but no other restriction should be in place.
Step 1: Determine the ACL problem.
As you perform the following tasks, compare the results to the expectations of the ACL.
a. Using L0, L1, and L2, attempt to access FTP service of Server2.
PC> ftp 2001:db8:cafe:2::2
b. View the running configuration on R1. Examine access list G1-ACCESS and its placement on the interfaces. Is the access list placed on the correct port in the correct direction? Is there any statement in the list that permits or denies traffic to other networks? Are the statements in the correct order?
c. Run other tests as necessary.
Step 2: Implement a solution.
Make adjustments to access lists to fix the problem.
R1(config)# interface GigabitEthernet0/1 R1(config-if)# no ipv6 traffic-filter G1-ACCESS out R1(config-if)# ipv6 traffic-filter G1-ACCESS in
Step 3: Verify the problem is resolved and document the solution.
If the problem is resolved, document the solution; otherwise return to Step 1.
G1-ACCESS was applied outbound on G0/1. Removed as outbound and applied as inbound on G0/1.
Part 3: Troubleshoot SSH Access
Only the hosts from 2001:DB8:CAFE::/64 network are permitted remote access to R1 via SSH.
Step 1: Determine the ACL problem.
As you perform the following tasks, compare the results to what you would expect from the ACL.
a. From L0 or PC0, verify SSH access to R1.
b. Using L1 and L2, attempt to access R1 via SSH.
c. View the running configuration on R1. Examine access lists and their placements on the interfaces. Is the access list placed on the correct interface and in the correct direction? Is there any statement in the list that permits or denies traffic to other networks? Are the statements in the correct order?
d. Perform other tests, as necessary.
Step 2: Implement a solution.
Make adjustments to access lists to fix the problem.
R1(config)# no ipv6 access-list G2-ACCESS R1(config)# ipv6 access-list G2-ACCESS R1(config-ipv6-acl)# deny tcp 2001:DB8:CAFE:2::/64 any eq 22 R1(config-ipv6-acl)# permit ipv6 any any
Step 3: Verify that the problem is resolved and document the solution.
If the problem is resolved, document the solution: otherwise return to Step 1.
The access list G2-ACCESS allows all traffic because the order of the statements is wrong. Reorder the statements so that the permit ipv6 any any is the second statement
Suggested Scoring Rubric
Script
R1 Configuration
ipv6 access-list G0-ACCESS permit ipv6 any any no ipv6 access-list G2-ACCESS ipv6 access-list G2-ACCESS deny tcp 2001:DB8:CAFE:2::/64 any eq 22 permit ipv6 any any interface GigabitEthernet0/1 no ipv6 traffic-filter G1-ACCESS out ipv6 traffic-filter G1-ACCESS in
