5.1.2 Lab – Implement VTP (Answers)
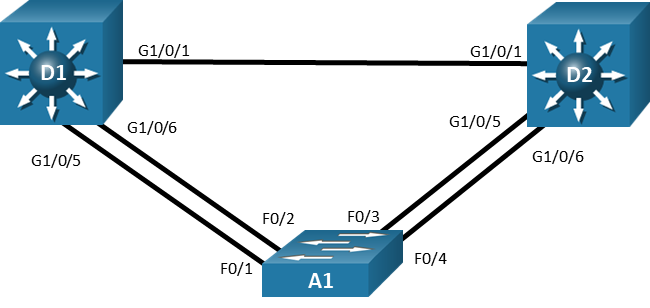
Topology
Objectives
- Part 1: Build the Network, Configure Basic Device Settings and Interface Addressing
- Part 2: Implement and Observe a VTPv2 Domain
- Part 3: Implement and Observe a VTPv3 Domain
Background / Scenario
VLAN Trunking Protocol (VTP) is a technology that manages the addition, deletion, and renaming of VLANs on the entire network from a single switch. Although not commonly used in modern networks that support programmability, VTP can be a useful tool as long as it is carefully managed.
A VTP domain, also called a VLAN management domain, consists of trunked switches that are under the same administrative control sharing the same VTP domain name. A switch can be in only one VTP domain, and VLAN database contents in the domain are globally synchronized. VLAN information is not propagated until a domain name is specified and trunks are set up between the devices.
There are three versions of VTP available; version 1 is the default. By default, versions 1 and 2 can support only normal-range VLANs. Version 3 can support normal and extended-range VLANs, as well as the synchronization of other databases, like MST. Support for VTP Version 3 on the Catalyst platform was added in IOS version 12.2(52)SE. Older IOS versions do not generally support VTP Version 3.
Switches operate in one of four VTP modes. The default VTP mode is server mode.
| VTP Mode | Description |
|---|---|
| VTP Server | You can create, modify, and delete VLANs, as well as specify other configuration parameters, such as VTP version and VTP pruning, for the entire VTP domain. VTP servers advertise their VLAN configuration to other switches in the same VTP domain and synchronize their VLAN configuration with other switches based on advertisements received over trunk links. VTP server is the default mode.
In VTP Server mode, VLAN configurations are only stored in the flash:vlan.dat file. While VLANs are manipulated in the configuration mode, the configuration commands do not appear in the running-config. |
| VTP Client | A VTP client behaves like a VTP server and transmits and receives VTP updates on its trunks, but you cannot create, change, or delete VLANs on a VTP client. VLANs are configured on another switch in the domain that is in server mode.
In VTP Client mode, learned VLANs are only stored in the flash:vlan.dat file. The configuration of VLANs does not appear in the running-config. |
| VTP Transparent | VTP transparent switches do not participate in VTP. A VTP transparent switch does not advertise, nor synchronize, its VLAN database based on received advertisements. However, transparent switches will forward received VTP messages under two circumstances; either the VTP domain name of the transparent switch is empty (not yet configured), or it matches the domain name in the received VTP messages.
In VTP Transparent mode, normal range VLAN configurations are stored both in flash:vlan.dat file and they are also present in the running-config. If extended range VLANs are used, they are stored in the flash:vlan.dat only if the switch is running VTP version 3. In Version 1 or 2, extended VLANs are stored in the running-config. |
| VTP Off | A switch in VTP Off mode functions in the same manner as a VTP transparent switch, except that it does not forward VTP advertisements on trunks. VTP off is only available on switches that support VTP version 3, although it is not necessary to run VTP version 3 on the switch to be able to put it into VTP Off mode.
In VTP Off mode, normal range VLAN configurations are stored both in flash:vlan.dat file and are also present in the running-config. Similar to Transparent mode, when using VTP version 3 both normal and extended range VLANs are stored in the flash:vlan.dat file. |
In this lab you will set up and observe the operation of VTP version 2 and VTP version 3.
Note: This lab is an exercise in deploying and verifying VTP and does not reflect networking best practices.
Note: The switches used with CCNP hands-on labs are Cisco 3650 with Cisco IOS XE release 16.9.4 (universalk9 image) and Cisco 2960+ with IOS release 15.2 (lanbase image). Other routers and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and the output produced might vary from what is shown in the labs.
Note: Ensure that the switches have been erased and have no startup configurations. If you are unsure contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 2 Switches (Cisco 3650 with Cisco IOS XE release 16.9.4 universal image or comparable)
- 1 Switch (Cisco 2960+ with Cisco IOS release 15.2 lanbase image or comparable)
- 1 PC (Windows with a terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Instructions
Part 1: Build the Network, Configure Basic Device Settings and Interface Addressing
In Part 1, you will set up the network topology and configure basic settings and interface addressing on routers.
Step 1: Cable the network as shown in the topology.
Attach the devices as shown in the topology diagram, and cable as necessary.
Step 2: Configure basic settings for each switch.
a. Console into each router, enter global configuration mode, and apply the basic settings using the following startup configurations.
Switch D1
hostname D1 banner motd # D1, Implement VTP # spanning-tree mode rapid-pvst line con 0 exec-timeout 0 0 logging synchronous exit interface range g1/0/1-24, g1/1/1-4, g0/0 shutdown exit interface range g1/0/1, g1/0/5-6 switchport mode trunk no shutdown exit
Switch D2
hostname D2 banner motd # D2, Implement VTP # spanning-tree mode rapid-pvst line con 0 exec-timeout 0 0 logging synchronous exit interface range g1/0/1-24, g1/1/1-4, g0/0 shutdown exit interface range g1/0/1, g1/0/5-6 switchport mode trunk no shutdown exit
Switch A1
hostname A1 banner motd # A1, Implement VTP # spanning-tree mode rapid-pvst line con 0 exec-timeout 0 0 logging synchronous exit interface range f0/1-24, g0/1-2 shutdown exit interface range f0/1-4 switchport mode trunk no shutdown exit
b. Set the clock on each switch to UTC time.
c. Save the running configuration to startup-config.
Part 2: Implement and Observe a VTPv2 Domain.
Step 1: Verify VTP status.
On D1, issue the command show vtp status.
D1# show vtp status
VTP Version capable : 1 to 3
VTP version running : 1
VTP Domain Name :
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : d8b1.9028.af80
Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00
Local updater ID is 0.0.0.0 (no valid interface found)
Feature VLAN:
--------------
VTP Operating Mode : Server
Maximum VLANs supported locally : 1005
Number of existing VLANs : 5
Configuration Revision : 0
MD5 digest : 0x57 0xCD 0x40 0x65 0x63 0x59 0x47 0xBD
0x56 0x9D 0x4A 0x3E 0xA5 0x69 0x35 0xBC
Because no VLAN configurations were made, all settings are the defaults. This switch is capable of running versions 1, 2, or 3 of VTP, and runs version 1 by default. All switches in the VTP domain must run the same VTP version. The number of existing VLANs is the five built-in VLANs. Different switches in the Catalyst family support different numbers of local VLANs. Lastly, note that the configuration revision is 0.
Multiple switches in the VTP domain can be in VTP Server mode. In VTPv1 and VTPv2, any of these server switches can be used to centrally manage VLANs for all other switches in the VTP domain.
The configuration revision number is compared amongst VTPv1 or VTPv2 switches. The VLAN database from the switch with the highest revision number is adopted by all the other switches in the VLAN management domain. Every time VLAN information is modified and saved in the VLAN database (vlan.dat), the revision number is increased by one when the user exits from VLAN Configuration mode.
VTP messages only pass over trunks between switches. They are not sent out of access ports.
Step 2: Configure and observe VTPv2 domain operations.
a. Configure D1 to operate in VTP Server mode and set the VTP domain name and VTP version 2. We will also set a VTP password, which provides some rudimentary protection against automatic VLAN database propagation. Because this password is set, VTPv2 will not allow other switches to automatically learn the domain name.
D1# config t
Enter configuration commands, one per line. End with CNTL/Z.
D1(config)# vtp domain CCNPv8
Changing VTP domain name from NULL to CCNPv8
D1(config)# vtp version 2
D1(config)# vtp mode server
Device mode already VTP Server for VLANS.
D1(config)# vtp password cisco123
Setting device VTP password to cisco123
D1(config)#
Jan 6 21:39:03.990: %SW_VLAN-6-VTP_DOMAIN_NAME_CHG: VTP domain name changed to CCNPv8.
b. On D1, create VLAN 2 and name it SecondVLAN, assign port g1/0/23 to that VLAN, and verify the VTP status again. Notice the revision number has incremented. Also, verify that the port is assigned to the VLAN.
D1# config t
Enter configuration commands, one per line. End with CNTL/Z.
D1(config)# vlan 2
D1(config-vlan)# name SecondVLAN
D1(config-vlan)# exit
D1(config)# interface g1/0/23
D1(config-if)# switchport mode access
D1(config-if)# switchport access vlan 2
D1(config-if)# no shutdown
D1(config-if)# end
D1# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/2, Gi1/0/3, Gi1/0/4
Gi1/0/7, Gi1/0/8, Gi1/0/9
Gi1/0/10, Gi1/0/11, Gi1/0/12
Gi1/0/13, Gi1/0/14, Gi1/0/15
Gi1/0/16, Gi1/0/17, Gi1/0/18
Gi1/0/19, Gi1/0/20, Gi1/0/21
Gi1/0/22, Gi1/0/24, Gi1/1/1
Gi1/1/2, Gi1/1/3, Gi1/1/4
2 SecondVLAN active Gi1/0/23
1002 fddi-default act/unsup
1003 trcrf-default act/unsup
1004 fddinet-default act/unsup
1005 trbrf-default act/unsup
D1# show vtp status
VTP Version capable : 1 to 3
VTP version running : 2
VTP Domain Name : CCNPv8
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : d8b1.9028.af80
Configuration last modified by 0.0.0.0 at 1-6-20 21:40:19
Local updater ID is 0.0.0.0 (no valid interface found)
Feature VLAN:
--------------
VTP Operating Mode : Server
Maximum VLANs supported locally : 1005
Number of existing VLANs : 6
Configuration Revision : 2
MD5 digest : 0x36 0x8B 0x44 0xC9 0x2A 0x7E 0x1E 0x36
0x88 0x18 0x43 0xB2 0xF5 0xEC 0x2F 0x12 #
c. On D1, create VLAN 2048.
Note: If you are working this lab on something other than an IOS XE based switch, you will not be allowed to create VLAN 2048 in VTP version 1 or 2 in Server mode.
D1# config t Enter configuration commands, one per line. End with CNTL/Z. D1(config)# vlan 2048 D1(config-vlan)# exit
d. Verify D2 and A1 have not learned about the new VLANs by examining the output of show vlan brief on each switch.
e. Configure D2 and A1 with the same VTP domain name, version and password as configured on D1.
f. Instead of waiting for the DTP update timer to expire, shut down and enable the interface g1/0/1 on D2 and f0/1 on A1 to force a DTP update, then verify that D2 and A1 now have the same VTP configuration revision number. However, they do not have the same VLAN database. D1 does not propagate information about extended VLANs (VLAN 2048) via VTP version 2. Notice from the output of show vlan brief that the only thing learned was the VLAN number and name; the port assignment was not propagated. Port assignments to VLANs still have to be done on per-switch basis.
D2# show vtp status | i VLANs|Revision
Maximum VLANs supported locally : 1005
Number of existing VLANs : 6
Configuration Revision : 2
D2# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/2, Gi1/0/3, Gi1/0/4
Gi1/0/7, Gi1/0/8, Gi1/0/9
Gi1/0/10, Gi1/0/11, Gi1/0/12
Gi1/0/13, Gi1/0/14, Gi1/0/15
Gi1/0/16, Gi1/0/17, Gi1/0/18
Gi1/0/19, Gi1/0/20, Gi1/0/21
Gi1/0/22, Gi1/0/23, Gi1/0/24
Gi1/1/1, Gi1/1/2, Gi1/1/3
Gi1/1/4
2 SecondVLAN active
1002 fddi-default act/unsup
1003 trcrf-default act/unsup
1004 fddinet-default act/unsup
1005 trbrf-default act/unsup
g. To demonstrate the main drawback to VTP, go to A1 and remove VLAN 2 with the no vlan 2 command. The command should complete successfully.
A1# config t
Enter configuration commands, one per line. End with CNTL/Z.
A1(config)# no vlan 2
A1(config)# end
A1# show vtp status | i Revision
Configuration Revision : 3
h. Go to D1 and see if VLAN 2 still exists. You will see that it does not. This is the main drawback to VTP version 2. Without careful control, an existing switch or newly added switch with the same VTP domain name information could overwrite the existing database, because it only compares the configuration revision number, instead of the Client / Server mode. Also, note the status of interface g1/0/23. It is not listed in the output of show vlan brief. The interface is unusable, because it is assigned to a VLAN that does not exist. Remember that the VLAN database contents and the port assignment to a VLAN are two separate things, and they are not synchronized.
D1# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/2, Gi1/0/3, Gi1/0/4
Gi1/0/7, Gi1/0/8, Gi1/0/9
Gi1/0/10, Gi1/0/11, Gi1/0/12
Gi1/0/13, Gi1/0/14, Gi1/0/15
Gi1/0/16, Gi1/0/17, Gi1/0/18
Gi1/0/19, Gi1/0/20, Gi1/0/21
Gi1/0/22, Gi1/0/24, Gi1/1/1
Gi1/1/2, Gi1/1/3, Gi1/1/4
1002 fddi-default act/unsup
1003 trcrf-default act/unsup
1004 fddinet-default act/unsup
1005 trbrf-default act/unsup
2048 VLAN2048 active
D1# show vtp status
VTP Version capable : 1 to 3
VTP version running : 2
VTP Domain Name : CCNPv8
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : d8b1.9028.af80
Configuration last modified by 0.0.0.0 at 1-6-20 21:57:29
Local updater ID is 0.0.0.0 (no valid interface found)
Feature VLAN:
--------------
VTP Operating Mode : Server
Maximum VLANs supported locally : 1005
Number of existing VLANs : 5
Configuration Revision : 3
MD5 digest : 0xBE 0xF6 0xBD 0x14 0xED 0xA1 0x19 0x6A
0x3D 0x1C 0x22 0xB5 0x5E 0xC5 0x2C 0xE3
i. On D1, recreate VLAN 2 with the name SecondVLAN2. Verify that the VTP configuration revision number increases, the VLAN appears in the database, and that g1/0/23 is listed in the show vlan brief output once again.
D1# config t Enter configuration commands, one per line. End with CNTL/Z. D1(config)# vlan 2 D1(config-vlan)# name SecondVLAN2 D1(config-vlan)# end D1# show vtp status | i Revision Configuration Revision : 4 D1# show vlan brief | i Gi1/0/23 2 SecondVLAN2 active Gi1/0/23
j. On A1, change the VTP mode to client, and then attempt to create VLAN 3. It will not be allowed. VTP Client mode prevents new VLANs from being created, modified, or deleted. But a VTP Client with a higher revision number will still overwrite a VTP Server switch database. The typical scenario is a switch using the same VTP information (domain, password) in a test network has a higher revision number and is placed on the production network without being cleared.
A1# config t
Enter configuration commands, one per line. End with CNTL/Z.
A1(config)# vtp mode client
Setting device to VTP Client mode for VLANS.
A1(config)# vlan 3
VTP VLAN configuration not allowed when device is in CLIENT mode.
k. On D2, change the VTP mode to transparent, then attempt to create VLAN 3 with the name ThirdVLAN. You will succeed. Verify that it is in the output of show vlan brief. Note the VTP configuration revision number.
D2# config t Enter configuration commands, one per line. End with CNTL/Z. D2(config)# vtp mode transparent Setting device to VTP Transparent mode for VLANS. D2(config)# vlan 3 D2(config-vlan)# name ThirdVLAN D2(config-vlan)# end D2# show vlan brief | i ThirdVLAN 3 ThirdVLAN active D2# show vtp status | i Domain|Revision VTP Domain Name : CCNPv8 Configuration Revision : 0
l. On D2, create VLAN 1111 with the name QuadOne. You will succeed. Verify that it is in the output of show vlan brief. Check to see what the VTP configuration revision number is.
D2# config t Enter configuration commands, one per line. End with CNTL/Z. D2(config)# vlan 1111 D2(config-vlan)# name QuadOne D2(config-vlan)# end D2# show vlan brief | i QuadOne 1111 QuadOne active D2# show vtp status | i Domain|Revision VTP Domain Name : CCNPv8 Configuration Revision : 0
m. Check D1 to see if VLAN 3 or VLAN 1111 has been learned. They will not have been. VTP Transparent switches keep to themselves in the VTP domain, and do not learn or propagate VLAN information from other switches.
n. On D1, shutdown interfaces g1/0/5 and g1/0/6, then create VLAN 4 with the name FourthVLAN. Verify that it is in the database, and that the VTP configuration revision number has incremented.
D1# show vtp status | i Revision Configuration Revision : 4 D1# config t Enter configuration commands, one per line. End with CNTL/Z. D1(config)# interface range g1/0/5-6 D1(config-if-range)# shutdown D1(config-if-range)# exit D1(config)# D1(config)# vlan 4 D1(config-vlan)# name FourthVLAN D1(config-vlan)# end D1# show vlan brief | i FourthVLAN 4 FourthVLAN active D1# show vtp status | i Revision Configuration Revision : 5
o. Check D2 and A1 to see if they have learned about the existence of VLAN 4. D1 sent a VTP message to D2, which forwarded the VTP message to A1 because they shared the same VTP domain name. A1 added the VLAN to its database and incremented its CR number to 5. Because D2 is in Transparent mode, it does not add the VLAN to its database.
D2# show vtp status | i Revision Configuration Revision : 0 A1# show vtp status | i Revision Configuration Revision : 5 A1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/5, Fa0/6 Fa0/7, Fa0/8, Fa0/9, Fa0/10 Fa0/11, Fa0/12, Fa0/13, Fa0/14 Fa0/15, Fa0/16, Fa0/17, Fa0/18 Fa0/19, Fa0/20, Fa0/21, Fa0/22 Fa0/23, Fa0/24, Gi0/1, Gi0/2 2 SecondVLAN2 active 4 FourthVLAN active 1002 fddi-default act/unsup 1003 trcrf-default act/unsup 1004 fddinet-default act/unsup 1005 trbrf-default act/unsup
Part 3: Implement and Observe a VTPv3 Domain
In this part of the lab you will configure VTP version 3 to operate across the rest of the switched network. VTP version 3 provides some significant benefits to the network administrator:
- The ability to create a primary server was added. In VTP versions 1 and 2, all VTP server switches are equal; any one of them may add, remove, or rename VLANs and change their state. In VTP version 3, only the primary server can do this. There can be only one primary server present in a VTP domain. The role of a primary server is to be in a runtime state. It is not a part of the configuration; rather, this state is requested in privileged EXEC mode and is relinquished whenever another switch attempts to become the primary server, or when the switch is reloaded.
- VTP version 3 has the ability to hide the VTP password. On a VTP version 1 or 2 switch, issuing the command show vtp password will show the password to you in plaintext. VTP version 3 allows you to specify that the password be hidden in the output, preventing the password from being inadvertently or maliciously divulged.
- VTP version 3 can propagate information about extended range VLANs; These are VLANs numbered between 1006 and 4094. To support these VLANs with VTP version 1 or 2, all switches have to be in Transparent or Off mode and the VLANs must be configured manually on a switch-by-switch basis.
- VTP version 3 only supports pruning for normal-range VLANs.
- VTP version 3 supports propagating Private VLAN information. As with extended-range VLANs, the lack of PVLAN support in VTP version 2 required that all switches be in Transparent mode and manually configured at each switch.
- VTP version 3 added support for opaque databases. In other words, VTP version 3 can transport more than just the VLAN database between switches. The only option at this time is to share the Multiple Spanning Tree (MSTP) database, but room was left for expansion.
- Regardless of the VTP operating mode, a VTP domain must first be set before configuring VTP version 3.
VTP version 3 is backwards compatible with VTP version 2 for normal range VLANs only; at the boundary of the two protocols, a VTP version 3 switch will send out both version 3 and version 2-compatible messages. Version 2 messages received by a version 3 switch are discarded.
Step 1: Configure and verify VTPv3 on D1.
a. On D1, change the VTP version to version 3 and verify the change.
D1# config t Enter configuration commands, one per line. End with CNTL/Z. D1(config)# vtp version 3 D1(config)# Jan 6 22:03:24.620: %SW_VLAN-6-OLD_CONFIG_FILE_READ: Old version 2 VLAN configuration file detected and read OK. Version 3 files will be written in the future. D1(config)# end D1# show vtp status VTP Version capable : 1 to 3 VTP version running : 3 VTP Domain Name : CCNPv8 VTP Pruning Mode : Disabled VTP Traps Generation : Disabled Device ID : d8b1.9028.af80 Feature VLAN: -------------- VTP Operating Mode : Server Number of existing VLANs : 7 Number of existing extended VLANs : 1 Maximum VLANs supported locally : 4096 Configuration Revision : 0 Primary ID : 0000.0000.0000 Primary Description : MD5 digest : Feature MST: -------------- VTP Operating Mode : Transparent D1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Gi1/0/2, Gi1/0/3, Gi1/0/4 Gi1/0/5, Gi1/0/6, Gi1/0/7 Gi1/0/8, Gi1/0/9, Gi1/0/10 Gi1/0/11, Gi1/0/12, Gi1/0/13 Gi1/0/14, Gi1/0/15, Gi1/0/16 Gi1/0/17, Gi1/0/18, Gi1/0/19 Gi1/0/20, Gi1/0/21, Gi1/0/22 Gi1/0/24, Gi1/1/1, Gi1/1/2 Gi1/1/3, Gi1/1/4 2 SecondVLAN2 active Gi1/0/23 4 FourthVLAN active 1002 fddi-default act/unsup 1003 trcrf-default act/unsup 1004 fddinet-default act/unsup 1005 trbrf-default act/unsup 2048 VLAN2048 active
b. On D1, try to create VLAN 6. You will not be allowed to do so. If you examine the output of show vtp status, you will see that the identification of the primary server is blank (all zeroes).
D1# show vtp status | i Primary
Primary ID : 0000.0000.0000
Primary Description
c. On D1, issue the privileged EXEC command vtp primary vlan. This makes D1 the primary for the VLAN database only. There is also a primary for MST, but that is not the focus of this lab (if you issue the vtp primary command with no additional parameters, VLAN is assumed.) Verify that the base mac-address for D1 is listed as the primary server id.
D1# vtp primary vlan This system is becoming primary server for feature vlan No conflicting VTP3 devices found. Do you want to continue? [confirm] D1# Jan 6 22:06:46.299: %SW_VLAN-4-VTP_PRIMARY_SERVER_CHG: d8b1.9028.af80 has become the primary server for the VLAN VTP feature D1# show vtp status | i Primary VTP Operating Mode : Primary Server Primary ID : d8b1.9028.af80 Primary Description : D1 D1# show hardware | i Base Base Ethernet MAC Address : d8:b1:90:28:af:80
Now we see that VTPv3 is working in that it allows for extended range VLANs while in Server mode, it is sending VTPv2-compatible messages at the domain boundary, and that D2 is still passing those messages along.
d. If you did not notice in the earlier output, verify the Configuration Revision number on D1, and then the number on A1. In this case, to cause a change at A1, D1 will have to have five revisions made to increment the revision number past what A1 currently has.
D1(config)# do show vtp status | i Revision Configuration Revision : 1 A1# show vtp status | i Revision Configuration Revision : 5
e. On D1, create the following VLANs.
- VLAN 6, named SixthVLAN
- VLAN 7, named SeventhVLAN
- VLAN 8, named EighthVLAN
- VLAN 9, named NinthVLAN
- VLAN 10, named TenthVLAN
- VLAN 11, named EleventhVLAN
f. Verify that they exist in the VLAN database and verify the configuration revision number is higher than the revision number A1 had in the previous step.
D1# show vlan brief | i Six|Seven|Eight|Nin|Ten|Elev 6 SixthVLAN active 7 SeventhVLAN active 8 EighthVLAN active 9 NinthVLAN active 10 TenthVLAN active 11 EleventhVLAN active D1# show vtp status | i Revision Configuration Revision : 7
Note: If the revision number does not increase past the number required, rename a VLAN and exit out of VLAN Configuration mode to increment the revision number by one. Repeat this step as needed.
g. Check A1 to see if it learned the new VLANs and verify that its configuration revision number matches that of D1. We will not check D2 because it is in Transparent mode.
A1# show vtp status | i Revision Configuration Revision : 7 A1# show vlan brief | i Six|Seven|Eight|Nin|Ten|Elev 6 SixthVLAN active 7 SeventhVLAN active 8 EighthVLAN active 9 NinthVLAN active 10 TenthVLAN active 11 EleventhVLAN active
h. On D1, create VLAN 2600 with the name HackerPub. Verify that it exists in the VLAN database and verify the configuration revision number.
D1# config t Enter configuration commands, one per line. End with CNTL/Z. D1(config)# vlan 2600 D1(config-vlan)# name HackerPub D1(config-vlan)# end D1# show vtp status | i Revision Configuration Revision : 8 D1# show vlan brief | i Hack 2600 HackerPub active
i. See if A1 learned VLAN 2600. You will see that it did not, because VTP version 2 does not support extended range VLANs.
A1# show vtp status | i Revision
Configuration Revision : 8
A1# show vlan brief | i Hack
Step 2: Configure and observe VTPv3 domain operations.
In this step we will update D2 and A1 to run VTPv3 and verify their behavior as a Transparent and Client switches in the VTP domain.
a. Configure D2 and A1 to operate using VTP version 3.
D2# config t Enter configuration commands, one per line. End with CNTL/Z. D2(config)# vtp version 3 D2(config)# end Jan 6 22:12:28.728: %SW_VLAN-6-OLD_CONFIG_FILE_READ: Old version 2 VLAN configuration file detected and read OK. Version 3 files will be written in the future. A1# config t Enter configuration commands, one per line. End with CNTL/Z. A1(config)# vtp version 3 A1(config)# end Jan 6 22:12:50.784: %SW_VLAN-6-OLD_CONFIG_FILE_READ: Old version 2 VLAN configuration file detected and read OK. Version 3 files will be written in the future.
b. Check the version and revision number on A1 and see that they have been updated to match D1. Verify that VLAN 2600 now exists in the VLAN database on A1.
A1# show vtp status | i version|Domain|Revision|Primary|Mode|Feature VTP version running : 3 VTP Domain Name : CCNPv8 VTP Pruning Mode : Disabled Feature VLAN: VTP Operating Mode : Client Configuration Revision : 8 Primary ID : d8b1.9028.af80 Primary Description : D1 Feature MST: VTP Operating Mode : Transparent Feature UNKNOWN: VTP Operating Mode : Transparent A1# show vlan brief | i Hack 2600 HackerPub active
c. Check the revision number on D2 and see that it has not changed, and that VLANs 6 through 11, and VLAN 2600 are not present in the VLAN database.
D2# show vtp status | i version|Domain|Revision|Primary|Mode|Feature
VTP version running : 3
VTP Domain Name : CCNPv8
VTP Pruning Mode : Disabled
Feature VLAN:
VTP Operating Mode : Transparent
Feature MST:
VTP Operating Mode : Transparent
Feature UNKNOWN:
VTP Operating Mode : Transparent
D2# show vlan brief | i Hack
D2# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Gi1/0/2, Gi1/0/3, Gi1/0/4
Gi1/0/7, Gi1/0/8, Gi1/0/9
Gi1/0/10, Gi1/0/11, Gi1/0/12
Gi1/0/13, Gi1/0/14, Gi1/0/15
Gi1/0/16, Gi1/0/17, Gi1/0/18
Gi1/0/19, Gi1/0/20, Gi1/0/21
Gi1/0/22, Gi1/0/23, Gi1/0/24
Gi1/1/1, Gi1/1/2, Gi1/1/3
Gi1/1/4
2 SecondVLAN2 active
3 ThirdVLAN active
1002 fddi-default act/unsup
1003 trcrf-default act/unsup
1004 fddinet-default act/unsup
1005 trbrf-default act/unsup
1111 QuadOne active
Device Configs – Final
Switch D1
D1# show run Building configuration... Current configuration : 8975 bytes ! version 16.9 no service pad service timestamps debug datetime msec service timestamps log datetime msec ! Call-home is enabled by Smart-Licensing. service call-home no platform punt-keepalive disable-kernel-core ! hostname D1 ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! no aaa new-model switch 1 provision ws-c3650-24ts ! ! login on-success log ! crypto pki trustpoint SLA-TrustPoint enrollment pkcs12 revocation-check crl ! license boot level ipservicesk9 ! diagnostic bootup level minimal ! spanning-tree mode rapid-pvst spanning-tree extend system-id ! redundancy mode sso ! transceiver type all monitoring ! class-map match-any system-cpp-police-topology-control description Topology control class-map match-any system-cpp-police-sw-forward description Sw forwarding, L2 LVX data, LOGGING class-map match-any system-cpp-default description Inter FED, EWLC control, EWLC data class-map match-any system-cpp-police-sys-data description Learning cache ovfl, High Rate App, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed class-map match-any system-cpp-police-punt-webauth description Punt Webauth class-map match-any system-cpp-police-l2lvx-control description L2 LVX control packets class-map match-any system-cpp-police-forus description Forus Address resolution and Forus traffic class-map match-any system-cpp-police-multicast-end-station description MCAST END STATION class-map match-any system-cpp-police-multicast description Transit Traffic and MCAST Data class-map match-any system-cpp-police-l2-control description L2 control class-map match-any system-cpp-police-dot1x-auth description DOT1X Auth class-map match-any system-cpp-police-data description ICMP redirect, ICMP_GEN and BROADCAST class-map match-any system-cpp-police-stackwise-virt-control description Stackwise Virtual class-map match-any non-client-nrt-class class-map match-any system-cpp-police-routing-control description Routing control and Low Latency class-map match-any system-cpp-police-protocol-snooping description Protocol snooping class-map match-any system-cpp-police-dhcp-snooping description DHCP snooping class-map match-any system-cpp-police-system-critical description System Critical and Gold Pkt ! policy-map system-cpp-policy ! interface GigabitEthernet0/0 vrf forwarding Mgmt-vrf no ip address shutdown negotiation auto ! interface GigabitEthernet1/0/1 switchport mode trunk ! interface GigabitEthernet1/0/2 switchport mode trunk shutdown ! interface GigabitEthernet1/0/3 switchport mode trunk shutdown ! interface GigabitEthernet1/0/4 switchport mode trunk shutdown ! interface GigabitEthernet1/0/5 switchport mode trunk shutdown ! interface GigabitEthernet1/0/6 switchport mode trunk shutdown ! interface GigabitEthernet1/0/7 shutdown ! interface GigabitEthernet1/0/8 shutdown ! interface GigabitEthernet1/0/9 shutdown ! interface GigabitEthernet1/0/10 shutdown ! interface GigabitEthernet1/0/11 shutdown ! interface GigabitEthernet1/0/12 shutdown ! interface GigabitEthernet1/0/13 shutdown ! interface GigabitEthernet1/0/14 shutdown ! interface GigabitEthernet1/0/15 shutdown ! interface GigabitEthernet1/0/16 shutdown ! interface GigabitEthernet1/0/17 shutdown ! interface GigabitEthernet1/0/18 shutdown ! interface GigabitEthernet1/0/19 shutdown ! interface GigabitEthernet1/0/20 shutdown ! interface GigabitEthernet1/0/21 shutdown ! interface GigabitEthernet1/0/22 shutdown ! interface GigabitEthernet1/0/23 switchport access vlan 2 switchport mode access ! interface GigabitEthernet1/0/24 shutdown ! interface GigabitEthernet1/1/1 shutdown ! interface GigabitEthernet1/1/2 shutdown ! interface GigabitEthernet1/1/3 shutdown ! interface GigabitEthernet1/1/4 shutdown ! interface Vlan1 no ip address shutdown ! ip forward-protocol nd ip http server ip http authentication local ip http secure-server ! control-plane service-policy input system-cpp-policy ! banner motd ^C D1, Implement VTP ^C ! line con 0 exec-timeout 0 0 logging synchronous stopbits 1 line aux 0 stopbits 1 line vty 0 4 exec-timeout 0 0 privilege level 15 password cisco123 logging synchronous login line vty 5 15 login ! end
Switch D2
D2# show run Building configuration... Current configuration : 8954 bytes ! version 16.9 no service pad service timestamps debug datetime msec service timestamps log datetime msec ! Call-home is enabled by Smart-Licensing. service call-home no platform punt-keepalive disable-kernel-core ! hostname D2 ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! no aaa new-model switch 1 provision ws-c3650-24ts ! login on-success log ! vtp domain CCNPv8 vtp mode transparent ! license boot level ipservicesk9 ! diagnostic bootup level minimal ! spanning-tree mode rapid-pvst spanning-tree extend system-id ! redundancy mode sso ! transceiver type all monitoring ! vlan 2 name SecondVLAN2 ! vlan 3 name ThirdVLAN ! vlan 1111 name QuadOne ! class-map match-any system-cpp-police-topology-control description Topology control class-map match-any system-cpp-police-sw-forward description Sw forwarding, L2 LVX data, LOGGING class-map match-any system-cpp-default description Inter FED, EWLC control, EWLC data class-map match-any system-cpp-police-sys-data description Learning cache ovfl, High Rate App, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed class-map match-any system-cpp-police-punt-webauth description Punt Webauth class-map match-any system-cpp-police-l2lvx-control description L2 LVX control packets class-map match-any system-cpp-police-forus description Forus Address resolution and Forus traffic class-map match-any system-cpp-police-multicast-end-station description MCAST END STATION class-map match-any system-cpp-police-multicast description Transit Traffic and MCAST Data class-map match-any system-cpp-police-l2-control description L2 control class-map match-any system-cpp-police-dot1x-auth description DOT1X Auth class-map match-any system-cpp-police-data description ICMP redirect, ICMP_GEN and BROADCAST class-map match-any system-cpp-police-stackwise-virt-control description Stackwise Virtual class-map match-any non-client-nrt-class class-map match-any system-cpp-police-routing-control description Routing control and Low Latency class-map match-any system-cpp-police-protocol-snooping description Protocol snooping class-map match-any system-cpp-police-dhcp-snooping description DHCP snooping class-map match-any system-cpp-police-system-critical description System Critical and Gold Pkt ! policy-map system-cpp-policy ! interface GigabitEthernet0/0 vrf forwarding Mgmt-vrf no ip address shutdown negotiation auto ! interface GigabitEthernet1/0/1 switchport mode trunk ! interface GigabitEthernet1/0/2 switchport mode trunk shutdown ! interface GigabitEthernet1/0/3 switchport mode trunk shutdown ! interface GigabitEthernet1/0/4 switchport mode trunk shutdown ! interface GigabitEthernet1/0/5 switchport mode trunk ! interface GigabitEthernet1/0/6 switchport mode trunk ! interface GigabitEthernet1/0/7 shutdown ! interface GigabitEthernet1/0/8 shutdown ! interface GigabitEthernet1/0/9 shutdown ! interface GigabitEthernet1/0/10 shutdown ! interface GigabitEthernet1/0/11 shutdown ! interface GigabitEthernet1/0/12 shutdown ! interface GigabitEthernet1/0/13 shutdown ! interface GigabitEthernet1/0/14 shutdown ! interface GigabitEthernet1/0/15 shutdown ! interface GigabitEthernet1/0/16 shutdown ! interface GigabitEthernet1/0/17 shutdown ! interface GigabitEthernet1/0/18 shutdown ! interface GigabitEthernet1/0/19 shutdown ! interface GigabitEthernet1/0/20 shutdown ! interface GigabitEthernet1/0/21 shutdown ! interface GigabitEthernet1/0/22 shutdown ! interface GigabitEthernet1/0/23 shutdown ! interface GigabitEthernet1/0/24 shutdown ! interface GigabitEthernet1/1/1 shutdown ! interface GigabitEthernet1/1/2 shutdown ! interface GigabitEthernet1/1/3 shutdown ! interface GigabitEthernet1/1/4 shutdown ! interface Vlan1 no ip address shutdown ! ip forward-protocol nd ip http server ip http authentication local ip http secure-server ! control-plane service-policy input system-cpp-policy ! banner motd ^C D2, Implement VTP ^C ! line con 0 exec-timeout 0 0 logging synchronous stopbits 1 line aux 0 stopbits 1 line vty 0 4 login line vty 5 15 login ! end
Switch A1
A1# show run Building configuration... Current configuration : 1678 bytes ! version 15.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname A1 ! boot-start-marker boot-end-marker ! no aaa new-model system mtu routing 1500 ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! interface FastEthernet0/1 switchport mode trunk ! interface FastEthernet0/2 switchport mode trunk ! interface FastEthernet0/3 switchport mode trunk ! interface FastEthernet0/4 switchport mode trunk ! interface FastEthernet0/5 shutdown ! interface FastEthernet0/6 shutdown ! interface FastEthernet0/7 shutdown ! interface FastEthernet0/8 shutdown ! interface FastEthernet0/9 shutdown ! interface FastEthernet0/10 shutdown ! interface FastEthernet0/11 shutdown ! interface FastEthernet0/12 shutdown ! interface FastEthernet0/13 shutdown ! interface FastEthernet0/14 shutdown ! interface FastEthernet0/15 shutdown ! interface FastEthernet0/16 shutdown ! interface FastEthernet0/17 shutdown ! interface FastEthernet0/18 shutdown ! interface FastEthernet0/19 shutdown ! interface FastEthernet0/20 shutdown ! interface FastEthernet0/21 shutdown ! interface FastEthernet0/22 shutdown ! interface FastEthernet0/23 shutdown ! interface FastEthernet0/24 shutdown ! interface GigabitEthernet0/1 shutdown ! interface GigabitEthernet0/2 shutdown ! interface Vlan1 ! ip http server ip http secure-server ! banner motd ^C A1, Implement VTP ^C ! line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 login line vty 5 15 login ! end
