Check answers here:
CCNPv8 ENCOR (Version 8.0) – FINAL EXAM Answers
Quiz-summary
0 of 159 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
Information
CCNP ENCOR v8 Final Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 159 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- Answered
- Review
-
Question 1 of 159
1. Question
1 pointsWhat is the IPv6 address used by OSPFv3 non-DR/BDR routers to send link-state updates and link-state acknowledgments?Correct
Incorrect
Hint
Non-DR/BDR routers send an update or link-state acknowledgment message to the DR and BDR by using the AllDRouters address FF02::6. -
Question 2 of 159
2. Question
1 pointsRefer to the exhibit. Both routers R1 and R2 are configured for OSPFv3 and are routing for both IPv4 and IPv6 address families. Which two destination addresses will R1 use to establish a full adjacency with R2? (Choose two.)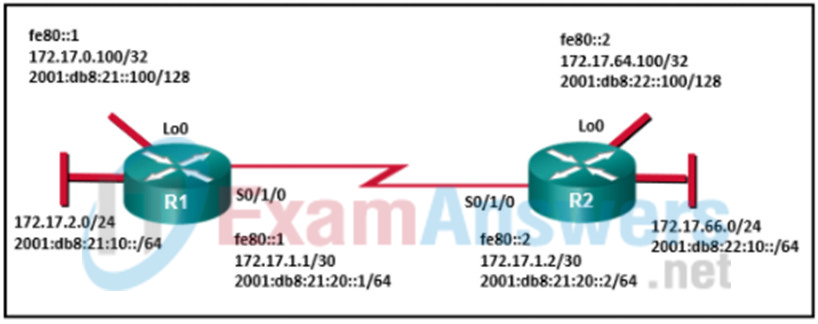 Correct
Correct
Incorrect
-
Question 3 of 159
3. Question
1 pointsOn an OSPF multiaccess network, which multicast address must a non-DR router use to send an LSU packet that contains new link-state information?Correct
Incorrect
-
Question 4 of 159
4. Question
1 pointsWhich configuration will prevent two directly connected Cisco routers from forming an OSPFv2 neighbor adjacency?Correct
Incorrect
-
Question 5 of 159
5. Question
1 pointsWhich type of OSPF link-state advertisement is a network LSA?Correct
Incorrect
-
Question 6 of 159
6. Question
1 pointsWhat advantage does WPA2 have over WPA?Correct
Incorrect
Hint
WPA2 uses the encryption algorithm AES (Advanced Encryption Standard) which is a stronger algorithm than WPA is, which uses TKIP (Temporal Key Integrity Protocol.) WPA was created to replace WEP (Wired Equivalent Privacy) which was easily compromised. However, the WPA TKIP had to take into account the older devices still using WEP on the network and as a result still had some of the WEP vulnerabilities. This was overcome with the creation of WPA2. -
Question 7 of 159
7. Question
1 pointsWhich situation is an example of EAP deployment?Correct
Incorrect
Hint
In a 802.1x WLAN environment, WPA2 with EAP (Extensible Authentication Protocol) allows for a back-end authentication server like Radius. In this environment, even though the supplicant is authenticated by the AP, the actual authentication process is carried out by the back-end Radius server through the WLAN controller. -
Question 8 of 159
8. Question
1 pointsWhich function is provided by the Cisco SD-Access Architecture controller layer?Correct
Incorrect
-
Question 9 of 159
9. Question
1 pointsMatch the Cisco SD-WAN solution component with the description. (Not all options are used.)Correct
Incorrect
Hint
- vManage Network Management System – configured with a public IP address so that all SD-WAN devices in the network can connect to it
- vSmart controller – enables centralized provisioning and simplifies network changes
- vBond orchestrator – authenticates each SD-WAN router that comes online
- non – supports standard router features, such as OSPF, BGP, ACLS, QoS, and routing policies
-
Question 10 of 159
10. Question
1 pointsRefer to the exhibit. A company adopts the hierarchical network model in the corporate LAN design. Layer 3 switches are deployed in the core and distribution layers. On which of the devices in this network should routing between workstation VLANs take place?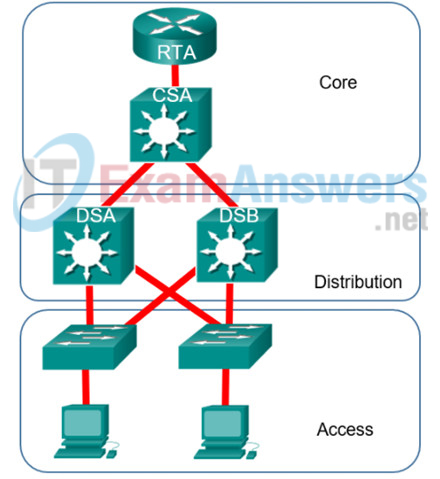 Correct
Correct
Incorrect
-
Question 11 of 159
11. Question
1 pointsRefer to the exhibit. A network administrator needs to implement inter-VLAN routing on a hierarchical network. On which devices should the inter-VLAN routing be configured?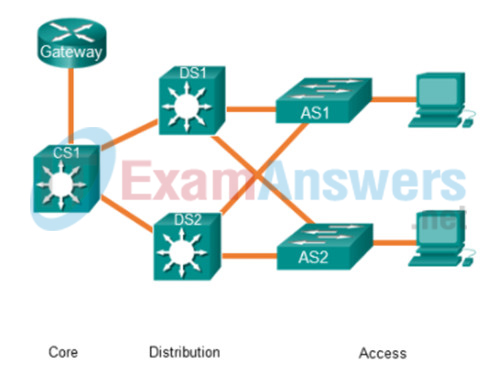 Correct
Correct
Incorrect
-
Question 12 of 159
12. Question
1 pointsWhich QoS model uses the DSCP bits to mark packets and provides 64 possible classes of service?Correct
Incorrect
Hint
The DiffServ model uses 6-bits known as the DiffServ Code Point (DSCP) bits to mark traffic and offers a maximum of 64 possible classes of service. Diffserv-aware routers can then implement per-hop behaviors (PHBs) that can control packet forwarding based on the specified class of service. -
Question 13 of 159
13. Question
1 pointsWhich type of QoS marking is applied to Ethernet frames?Correct
Incorrect
Hint
The class of service (CoS) marking allows a Layer 2 Ethernet frame to be marked with eight levels of priority (values 0–7). This marking can be used by QoS-enabled network devices to provide preferential traffic treatment. -
Question 14 of 159
14. Question
1 pointsWhich feature is used by an MST region to send VLAN information to a switch that runs PVST+?Correct
Incorrect
-
Question 15 of 159
15. Question
1 pointsWhat is a solution to mitigate the MST misconfiguration with improper VLAN assignment to the IST?Correct
Incorrect
-
Question 16 of 159
16. Question
1 pointsWhich three statements describe the building blocks that make up the IPsec protocol framework? (Choose three.)Correct
Incorrect
-
Question 17 of 159
17. Question
1 pointsRefer to the exhibit. What two commands are needed to complete the GRE tunnel configuration on router R1? (Choose two.)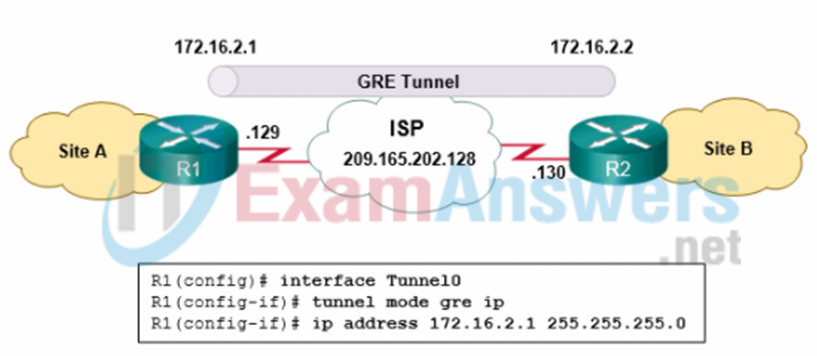 Correct
Correct
Incorrect
-
Question 18 of 159
18. Question
1 pointsWhat are two reasons for creating an OSPE network with multiple areas? (Choose two.)Correct
Incorrect
-
Question 19 of 159
19. Question
1 pointsOn what type of OSPF router is interarea route summarization configured?Correct
Incorrect
Hint
Interarea summarization is manually configured on Area Border Routers (ABRs). Because ABRs connect multiple areas, it is these routers that would summarize routes before injecting them into another area. ASBRs are configured with external route summarization. Backbone and intra-area routers have all interfaces in a single area and are not able to summarize routes into other areas. -
Question 20 of 159
20. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to a system that provides tools, such as breach detection, tracking, analysis, and surgical remediation, that organizations can use when advanced malware has slipped past other defenses?Correct
Incorrect
-
Question 21 of 159
21. Question
1 pointsRefer to the exhibit. What are the possible port roles for ports A, B, C, and D in this RSTP-enabled network?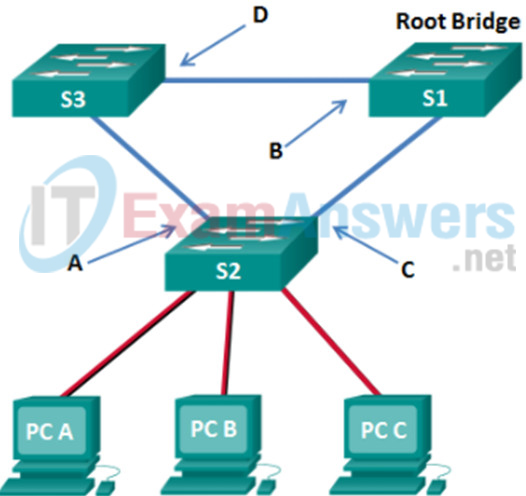 Correct
Correct
Incorrect
Hint
Because S1 is the root bridge, B is a designated port, and C and D root ports. RSTP supports a new port type, alternate port in discarding state, that can be port A in this scenario. -
Question 22 of 159
22. Question
1 pointsRefer to the exhibit. All the displayed switches are Cisco 2960 switches with the same default priority and operating at the same bandwidth. Which three ports will be STP designated ports? (Choose three.)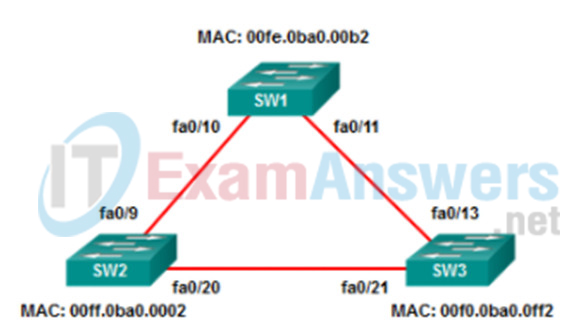 Correct
Correct
Incorrect
-
Question 23 of 159
23. Question
1 pointsWhich two statements describe characteristics of load balancing? (Choose two.)Correct
Incorrect
-
Question 24 of 159
24. Question
1 pointsRefer to the exhibit. Which type of IPv6 static route is configured in the exhibit? Correct
Correct
Incorrect
Hint
The route provided points to another address that must be looked up in the routing table. This makes the route a recursive static route. -
Question 25 of 159
25. Question
1 pointsA network administrator has noticed an unusual amount of traffic being received on a switch port that is connected to a college classroom computer. Which tool would the administrator use to make the suspicious traffic available for analysis at the college data center?Correct
Incorrect
-
Question 26 of 159
26. Question
1 pointsWhat are two benefits of using SNMP traps? (Choose two.)Correct
Incorrect
-
Question 27 of 159
27. Question
1 pointsHow will user traffic be forwarded between two laptops that are both connected to the same lightweight access point in a large enterprise topology?Correct
Incorrect
-
Question 28 of 159
28. Question
1 pointsA wireless engineer is deploying an autonomous Cisco access point. What must be configured on the access point to enable remote management?Correct
Incorrect
-
Question 29 of 159
29. Question
1 pointsWhich three protocols are components in the operation of 802.1x? (Choose three.)Correct
Incorrect
-
Question 30 of 159
30. Question
1 pointsMatch the security platform to the description. (Not all options are used.)Correct
Incorrect
-
Question 31 of 159
31. Question
1 pointsRefer to the exhibit. Which two conclusions can be derived from the output? (Choose two.)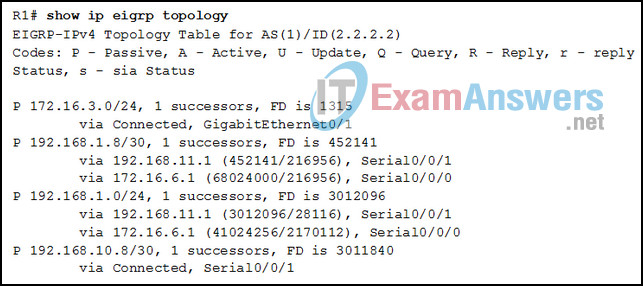 Correct
Correct
Incorrect
Hint
The second entry in the table indicates that there is one feasible successor (“1 successors”) for network 192.168.1.8/30. The last entry in the table shows that network 192.168.10.8/30 is directly connected, so it is not reachable through network 192.168.11.1. The third entry indicates that the reported distances for network 192.168.1.0 are 28116 and 2170112, not 41024256. This same entry shows that neighbor 172.16.6.1 is a feasible successor for network 192.168.1.0. The first entry indicates that R1 has only one successor, not two to network 172.16.3.0/24. -
Question 32 of 159
32. Question
1 pointsA new network administrator has been asked to verify the metrics that are used by EIGRP on a Cisco device. Which two EIGRP metrics are measured by using static values on a Cisco device? (Choose two.)Correct
Incorrect
Hint
Bandwidth and delay are static values that are not actually tracked by a device. Load and reliability are tracked dynamically by a device over a default period of time. MTU is not used for EIGRP metrics. -
Question 33 of 159
33. Question
1 pointsWhich factor can be used by an AP to improve the accuracy of locating a wireless client?Correct
Incorrect
Hint
To locate a device more accurately, an AP can use the received signal strength (RSS) of a client device as a measure of the distance between the two. -
Question 34 of 159
34. Question
1 pointsWhat is required by wireless clients that participate in Cisco centralized key management for intracontroller roaming?Correct
Incorrect
Hint
Cisco Centralized Key Management (CCKM): One controller maintains a database of clients and keys on behalf of its APs and provides them to other controllers and their APs as needed during client roams. CCKM requires Cisco Compatible Extensions (CCX) support from clients. -
Question 35 of 159
35. Question
1 pointsA wireless network engineer who is new to the Cisco lightweight architecture is becoming familiar with common baselines for the APs in the company. One particular AP shows no clients attached, but shows 30% channel utilization on the 2.4 GHz channel and 0% channel utilization on the 5 GHz channel. What is the issue, if any?Correct
Incorrect
-
Question 36 of 159
36. Question
1 pointsA network engineer that works for a company that uses lightweight APs is examining various performance factors for the wireless network in a particular area of the company. The engineer notices that one AP has an index value of 40 for air quality. What significance, if any, does this value provide?Correct
Incorrect
-
Question 37 of 159
37. Question
1 pointsIn which type of deployment is the Chef server hosted in the cloud?Correct
Incorrect
Hint
There are several types of deployment models for the Chef server. Chef Solo: The Chef server is hosted locally on the workstation. Chef Client and Server: This is a typical Chef deployment with distributed components. Hosted Chef: The Chef server is hosted in the cloud. Private Chef: All Chef components are within the same enterprise network. -
Question 38 of 159
38. Question
1 pointsWhat protocol is used by puppet masters to push configuration code to puppet agents?Correct
Incorrect
-
Question 39 of 159
39. Question
1 pointsWhat does BGP use to exchange routing updates with neighbors?Correct
Incorrect
Hint
BGP uses TCP port 179 to communicate with other routers. TCP allows for handling of fragmentation, sequencing, and reliability (acknowledgment and retransmission) of communication packets. -
Question 40 of 159
40. Question
1 pointsRefer to the exhibit. A network administrator issues the show bgp ipv4 unicast 172.16.0.0 command to check the route information in the BGP table. Which statement describes the characteristic of the advertisement of this route?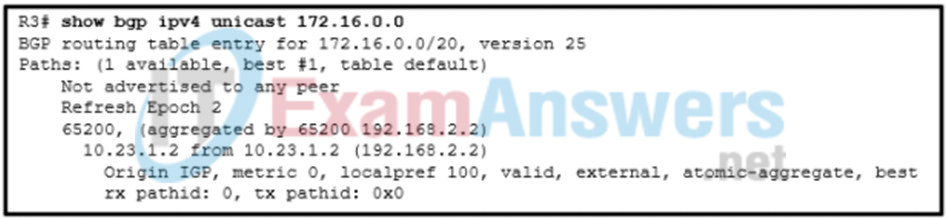 Correct
Correct
Incorrect
Hint
As indicated in the BGP table, the route is an aggregate route 172.16.0.0/20 learned from the neighbor 192.168.2.2. The atomic-aggregate attribute indicates loss of path attributes, such as AS_Path in this scenario. -
Question 41 of 159
41. Question
1 pointsWhat are three examples of hypervisors? (Choose three.)Correct
Incorrect
Hint
VMware vSphere, Microsoft HyperV, Citrix XenServer, and Red Hat Kernel-based Virtual Machine (KVM) are the most popular hypervisors in the server virtualization market -
Question 42 of 159
42. Question
1 pointsWhich two methods are used by a single-root I/O virtualization (SR-IOV) enabled switch to switch traffic between VNFs? (Choose two.)Correct
Incorrect
Hint
An SR-IOV-enabled pNIC supports two different modes for switching traffic between VNFs:- Virtual Ethernet Bridge (VEB): Traffic between VNFs attached to the same pNIC is hardware switched directly by the pNIC.
- Virtual Ethernet Port Aggregator (VEPA): Traffic between VNFs attached to the same pNIC is switched by an external switch.
-
Question 43 of 159
43. Question
1 pointsRefer to the exhibit. Spanning-tree port priorities are listed beneath each interface. The network administrator enters the spanning-tree vlan 1 root primary command on S4. What is the effect of the command?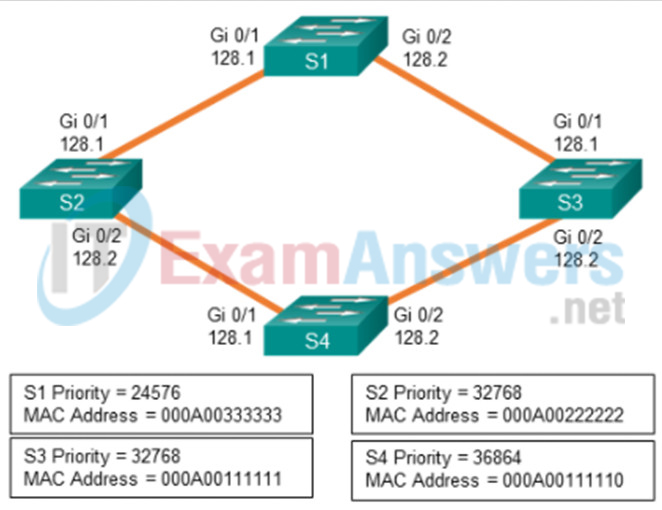 Correct
Correct
Incorrect
-
Question 44 of 159
44. Question
1 pointsNetwork users complain that the network is running very slowly. Upon investigation, a network technician discovers CPU spikes and exhausted memory resources on all the network devices. Also, numerous syslog messages are being generated that note continuous MAC address relearning. What is the most likely cause of the problem?Correct
Incorrect
-
Question 45 of 159
45. Question
1 pointsWhat type of signal requires little extra bandwidth because data is being sent at a relatively low bit rate?Correct
Incorrect
-
Question 46 of 159
46. Question
1 pointsWhich wireless technology can combine the use of multiple antennas and radio chains to receive multiple copies of degraded wireless signals and convert them into one usable reconstructed wireless signal?Correct
Incorrect
-
Question 47 of 159
47. Question
1 pointsAn administrator has configured an access list on R1 to allow SSH administrative access from host 172.16.1.100. Which command correctly applies the ACL?Correct
Incorrect
Hint
Administrative access over SSH to the router is through the vty lines. Therefore, the ACL must be applied to those lines in the inbound direction. This is accomplished by entering line configuration mode and issuing the access-class command. -
Question 48 of 159
48. Question
1 pointsWhat two additional features does a Layer 3 switch offer compared with a Layer 2 switch? (Choose two.)Correct
Incorrect
-
Question 49 of 159
49. Question
1 pointsWhat is true about TCAM lookups that are associated with CEF switching?Correct
Incorrect
-
Question 50 of 159
50. Question
1 pointsA network operator is testing a network management application that uses REST API to communicate with network devices. The operator received an HTTP response code 403 in a test step. What does this response code indicate?Correct
Incorrect
Hint
Most common HTTP status codes include:- 200 – OK (using GET or POST to exchange data with an API successfully)
- 201 – Created (creating resources by using a REST API call successfully)
- 400 – Bad Request (The request from the client is failed due to client-side issue.)
- 401 – Unauthorized (The client is not authenticated to access site or API call.)
- 403 – Forbidden (The access request is not granted based on the supplied credentials.)
- 404 – Not Found (The page requested at HTTP URL location does not exist or is hidden.)
-
Question 51 of 159
51. Question
1 pointsRefer to the exhibit. Which data format is used to describe the list of interfaces?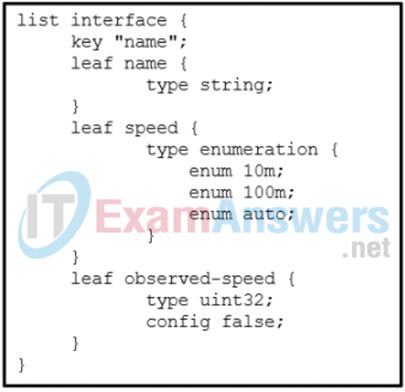 Correct
Correct
Incorrect
-
Question 52 of 159
52. Question
1 pointsRefer to the exhibit. Switch SW-A is to be used as a temporary replacement for another switch in the VTP Student domain. What two pieces of information are indicated from the exhibited output? (Choose two.)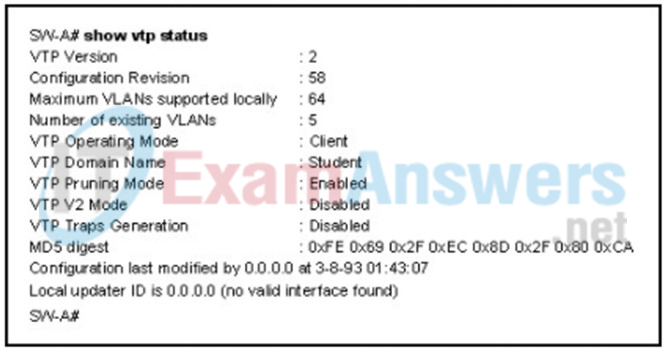 Correct
Correct
Incorrect
Hint
If a switch on the same VTP domain is added to the network and the switch has a higher configuration revision number, valid VLANs can be deleted and VLANs from the new switch can be sent to other switches in the VTP domain. This can result in loss of connectivity for some network devices. Always put a false domain name on a new switch and then change the VTP domain name to the correct one so the configuration revision number will be at 0 on the switch to be added. -
Question 53 of 159
53. Question
1 pointsWhich two mode combinations would result in the successful negotiation of an EtherChannel? (Choose two.)Correct
Incorrect
Hint
The combinations of modes that will form an EtherChannel are as follows: on/on, active/passive, active/active, desirable/auto, and desirable/desirable. -
Question 54 of 159
54. Question
1 pointsRefer to the exhibit. A network administrator configured routers R1 and R2 as part of HSRP group 1. After the routers have been reloaded, a user on Host1 complained of lack of connectivity to the Internet The network administrator issued the show standby brief command on both routers to verify the HSRP operations. In addition, the administrator observed the ARP table on Host1. Which entry should be seen in the ARP table on Host1 in order to gain connectivity to the Internet?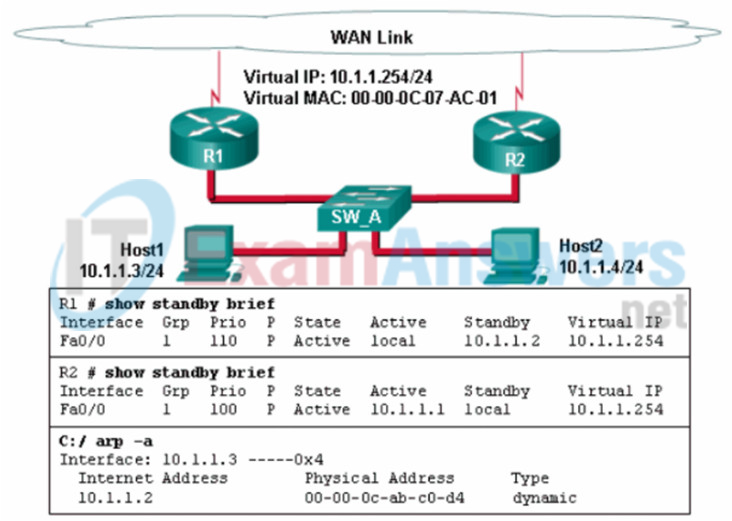 Correct
Correct
Incorrect
Hint
Hosts will send an ARP request to the default gateway which is the virtual IP address. ARP replies from the HSRP routers contain the virtual MAC address. The host ARP tables will contain a mapping of the virtual IP to the virtual MAC. – the IP address and the MAC address of R1 -
Question 55 of 159
55. Question
1 pointsA network engineer has issued the commandstandby 10 track 1 decrement 20on an SVI of a multilayer switch. What is the purpose of this command?Correct
Incorrect
-
Question 56 of 159
56. Question
1 pointsRefer to the exhibit. For which autonomous system would running BGP not be appropriate?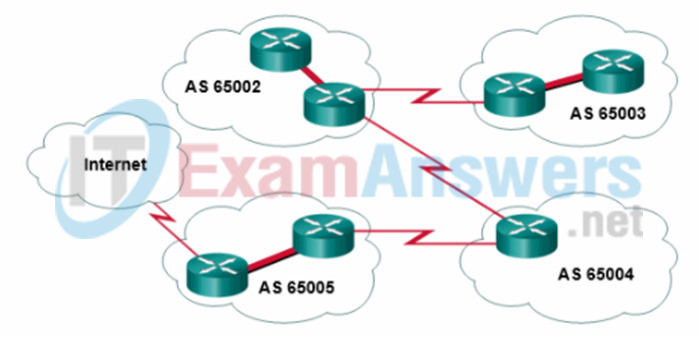 Correct
Correct
Incorrect
Hint
It is appropriate to use BGP when an autonomous system is multihomed, or has more than one connection to another autonomous system or to the Internet. BGP is not appropriate for single-homed autonomous systems. Autonomous system 65003 is a single-homed AS because it is only connected to one other autonomous system, 65002. -
Question 57 of 159
57. Question
1 pointsA network administrator is configuring an ACL to match networks for BGP route filtering. The administrator creates an ACEpermit ip 10.0.32.0 0.0.31.0 255.255.255.0 0.0.0.192. Which network matches the ACE?Correct
Incorrect
-
Question 58 of 159
58. Question
1 pointsHow does an RP MA announcement provide redundancy in a PIM domain configured with the auto-RP mechanism?Correct
Incorrect
-
Question 59 of 159
59. Question
1 pointsWhich two statements describe characteristics of shared trees for PIM distribution? (Choose two.)Correct
Incorrect
-
Question 60 of 159
60. Question
1 pointsA network administrator uses the spanning-tree portfast bpduguard default global configuration command to enable BPDU guard on a switch. However, BPDU guard is not activated on all access ports. What is the cause of the issue?Correct
Incorrect
-
Question 61 of 159
61. Question
1 pointsRefer to the exhibit. Router R1 has an OSPF neighbor relationship with the ISP router over the 192.168.0.32 network. The 192.168.0.36 network link should serve as a backup when the OSPF link goes down. The floating static route command ip route 0.0.0.0 0.0.0.0 S0/0/1 100 was issued on R1 and now traffic is using the backup link even when the OSPF link is up and functioning. Which change should be made to the static route command so that traffic will only use the OSPF link when it is up?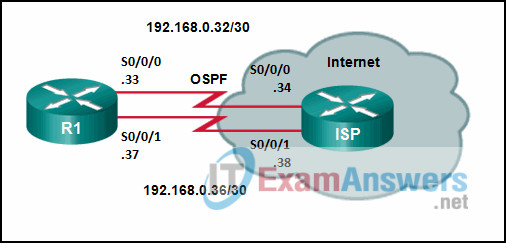 Correct
Correct
Incorrect
Hint
The problem with the current floating static route is that the administrative distance is set too low. The administrative distance will need to be higher than that of OSPF, which is 110, so that the router will only use the OSPF link when it is up. -
Question 62 of 159
62. Question
1 pointsWhich three functions are performed at the distribution layer of the hierarchical network model? (Choose three.)Correct
Incorrect
Hint
The primary function of the distribution layer is to aggregate access layer switches in a given building or campus. The distribution layer provides a boundary between the Layer 2 domain of the access layer and the Layer 3 domain of the core. On the Layer 2 side, it creates a boundary for Spanning Tree Protocol (STP), limiting propagation of Layer 2 faults. On the Layer 3 side, it provides a logical point to summarize IP routing information when it enters the core Layer. The summarization reduces IP route tables for easier troubleshooting and reduces protocol overhead for faster recovery from failures. -
Question 63 of 159
63. Question
1 pointsRefer to the exhibit. Which trunk link will not forward any traffic after the root bridge election process is complete?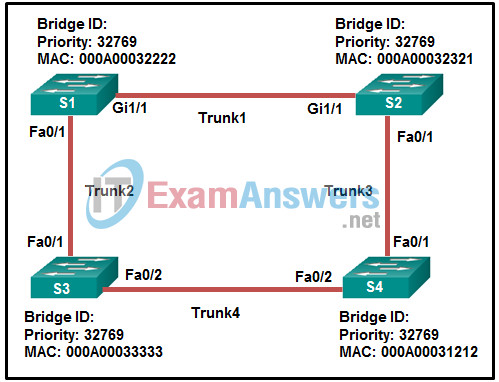 Correct
Correct
Incorrect
Hint
S4 has the lowest bridge ID, thus S4 is the root bridge. Because the path cost S1-S2-S4 is lower than the path cost S1-S3-S4, path S1-S2-S4 is the preferred path for S1 to reach S4. Thus, STP will set the S1 port Fa0/1 to a blocking state, and the trunk link Trunk2 will not forward any traffic. -
Question 64 of 159
64. Question
1 pointsWhich WLAN security protocol avoids attacks by strengthening the key exchange between clients and APs using a method known as Simultaneous Authentication of Equals?Correct
Incorrect
Hint
With WPA-Personal and WPA2-Personal modes, a malicious user can eavesdrop and capture the four-way handshake between a client and an AP. WPA3-Personal avoids such attacks by strengthening the key exchange between clients and APs through a method knows as SAE (Simultaneous Authentication of Equals). -
Question 65 of 159
65. Question
1 pointsWhat is the reason for a network engineer to alter the default reference bandwidth parameter when configuring OSPF?Correct
Incorrect
Hint
By default, Fast Ethernet, Gigabit, and 10 Gigabit Ethernet interfaces all have a cost of 1. Altering the default reference bandwidth alters the cost calculation, allowing each speed to be more accurately reflected in the cost. -
Question 66 of 159
66. Question
1 pointsWhich statement describes the Cisco Embedded Event Manager?Correct
Incorrect
Hint
The Cisco Embedded Event Manager (EEM) is a Cisco IOS tool that uses software applets to automate tasks on a Cisco device. EEM is completely contained within the local device and needs no external scripting or monitoring device. -
Question 67 of 159
67. Question
1 pointsWhat is JSON?Correct
Incorrect
Hint
JavaScript Object Notation (JSON) is a data format used by applications to store and transport data. -
Question 68 of 159
68. Question
1 pointsRefer to the exhibit. What can be concluded about network 192.168.4.0 in the R2 routing table?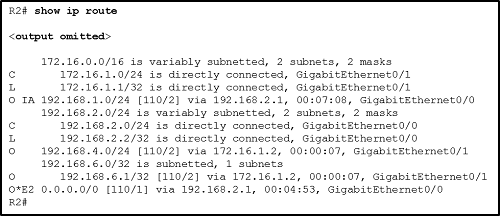 Correct
Correct
Incorrect
Hint
In a routing table, a route with the label O indicates a network that is advertised by another router in the same area. In this case, the exit interface is GigabitEthernet0/1. The designation O IA means the entry was learned from an interarea LSA that was generated from an ABR. Label O*E2 indicates an external network. In this case, the network designation of 0.0.0.0/0 indicates that this external network is the default route for all traffic that goes to external networks. -
Question 69 of 159
69. Question
1 pointsRefer to the exhibit. A network administrator is verifying the bridge ID and the status of this switch in the STP election. Which statement is correct based on the command output?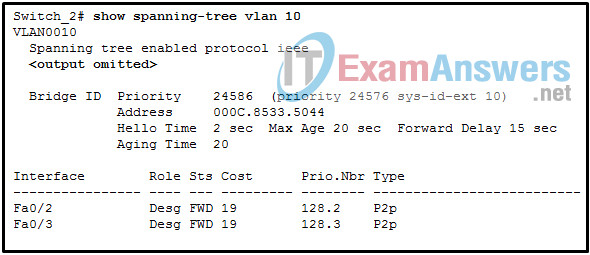 Correct
Correct
Incorrect
Hint
The priority value 24576 is a predefined value that is implemented by the command spanning-tree vlan 10 root primary . This command configures Switch_2 to become the root switch. A root switch will have all forwarding interfaces and no root ports. -
Question 70 of 159
70. Question
1 pointsWhat is the function of a QoS trust boundary?Correct
Incorrect
Hint
Network traffic is classified and marked as close to the source device as possible. The trust boundary is the location where the QoS markings on a packet are trusted as they enter an enterprise network. -
Question 71 of 159
71. Question
1 pointsWhat is a purpose of the OSPFv3 type 8 and type 9 LSAs?Correct
Incorrect
-
Question 72 of 159
72. Question
1 pointsWhich authentication protocol is server-based and preferred for device access control?Correct
Incorrect
-
Question 73 of 159
73. Question
1 pointsWhat is a characteristic of TACACS+?Correct
Incorrect
Hint
The TACACS+ protocol provides flexibility in AAA services. For example, using TACACS+, administrators can select authorization policies to be applied on a per-user or per-group basis. -
Question 74 of 159
74. Question
1 pointsWhich two options best describe an exterior routing protocol (EGP)? (Choose two.)Correct
Incorrect
-
Question 75 of 159
75. Question
1 pointsA company deploys a Cisco wireless network over a large campus. A network administrator is configuring the Layer 3 roaming capability on WLCs. What is the purpose of using Layer 3 roaming?Correct
Incorrect
Hint
If the two VLAN IDs differ, the controllers arrange a Layer 3 roam (also known as a local-to-foreign roam) that will allow the client to keep using its IP address. -
Question 76 of 159
76. Question
1 pointsA high school is deploying a wireless network for the campus. The wireless network consists of 100 lightweight APs and 3 WLCs. These 3 WLCs manage APs in 3 areas: (1) classroom buildings, (2) the library, the dining hall, and an indoor gymnasium, and (3) administration buildings. Which term is used to describe the type of roaming that occurs when a student using a smartphone roams from a classroom to the library?Correct
Incorrect
-
Question 77 of 159
77. Question
1 pointsA network administrator is configuring a prefix list with the ip prefix-list command. Which entry is valid?Correct
Incorrect
-
Question 78 of 159
78. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to a VPN client that provides VPN access and enhanced security to assess the compliance of an endpoint for things like antivirus, antispyware, and firewall software installed on the host?Correct
Incorrect
-
Question 79 of 159
79. Question
1 pointsWhat happens to the signal strength of an RF signal due to wave spreading?Correct
Incorrect
-
Question 80 of 159
80. Question
1 pointsWhich Cisco security solution uses dynamic content analysis to identify inappropriate content in real time for unknown websites?Correct
Incorrect
Hint
Reference: Here (from cisco) -
Question 81 of 159
81. Question
1 pointsWhich Cisco technology is based on the ETSI NFV architectural framework for reducing operational complexity of enterprise branch environments?Correct
Incorrect
Hint
Enterprise NFV reduces operational complexity of branch environments by hosting networking functions as software on standard x86-based platforms. Enterprise Network Functions Virtualization (NFV) – Cisco -
Question 82 of 159
82. Question
1 pointsA network administrator is configuring IPv6 route summarization on a BGP router with the command aggregate-address 2001:db8::/60 summary-only . Which two component networks match the aggregated route? (Choose two.)Correct
Incorrect
-
Question 83 of 159
83. Question
1 pointsWhich special-purpose mode is configured on a lightweight AP that is acting as a dedicated sensor while determining the position of stations using location-based services?Correct
Incorrect
-
Question 84 of 159
84. Question
1 pointsWhat determines the software image release that a lightweight access point will be running?Correct
Incorrect
Hint
Be aware that you cannot control which software image release a lightweight AP runs. Rather, the WLC that the AP joins determines the release, based on its own software version. -
Question 85 of 159
85. Question
1 pointsWhat are three benefits of a hierarchical network model? (Choose three.)Correct
Incorrect
-
Question 86 of 159
86. Question
1 pointsA company has an extensive wireless network of multiple APs and a WLC. Users in one particular area complain of the lack of wireless connectivity. The network engineer verifies that the two APs in that area are communicating with the WLC. The network engineer checks the status of one particular client and the WLC interface shows a black client status dot for DHCP. The network engineer checks the status of another client and it too shows a black status dot of DHCP. What is the most likely problem?Correct
Incorrect
-
Question 87 of 159
87. Question
1 pointsHow do Layer 3 switches differ from traditional routers?Correct
Incorrect
-
Question 88 of 159
88. Question
1 pointsRefer to the exhibit. The network has EIGRP configured on all routers and has converged on the routes advertised. PIM sparse mode has been also configured on all routers. The routers between the source and the rendezvous point (RP) have (S,G) state in the multicast routing table and the routers between the RP and the receivers have (*,G) state in their multicast routing tables. After the first multicast packet is received by the Receivers and the switchover takes place, how will the multicast traffic continue to flow from the source to the receivers?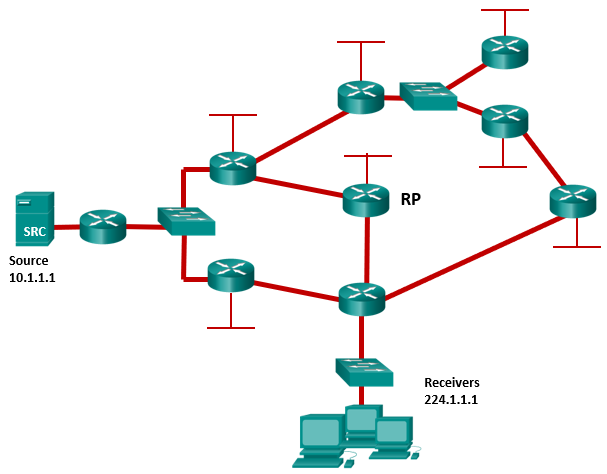 Correct
Correct
Incorrect
-
Question 89 of 159
89. Question
1 pointsWhich situation is a good case for a network technician to troubleshoot a problem using the ERSPAN tool?Correct
Incorrect
Hint
Encapsulated Remote Switched Port Analyzer (ERSPAN): You can capture network traffic on a remote device and send the traffic to the local system through Layer 3 (routing) toward a local port attached to some sort of traffic analyzer. -
Question 90 of 159
90. Question
1 pointsWhich parameter must match for all switches in the same MST region?Correct
Incorrect
Hint
The MST version number must match for all switches in the same MST region. -
Question 91 of 159
91. Question
1 pointsWhich overlay tunnel technology is established by fabric APs to transport wireless client data in an SD-Access wireless deployment?Correct
Incorrect
-
Question 92 of 159
92. Question
1 pointsWhat are two main components of SD-Access? (Choose two.)Correct
Incorrect
-
Question 93 of 159
93. Question
1 pointsWhat are two purposes of LISP? (Choose two.)Correct
Incorrect
-
Question 94 of 159
94. Question
1 pointsWhat are two differences between SNMP and NETCONF? (Choose two.)Correct
Incorrect
-
Question 95 of 159
95. Question
1 pointsRefer to the exhibit. An ACL was configured on R1 with the intention of denying traffic from subnet 172.16.4.0/24 into subnet 172.16.3.0/24. All other traffic into subnet 172.16.3.0/24 should be permitted. This standard ACL was then applied outbound on interface G0/0/0. Which conclusion can be drawn from this configuration?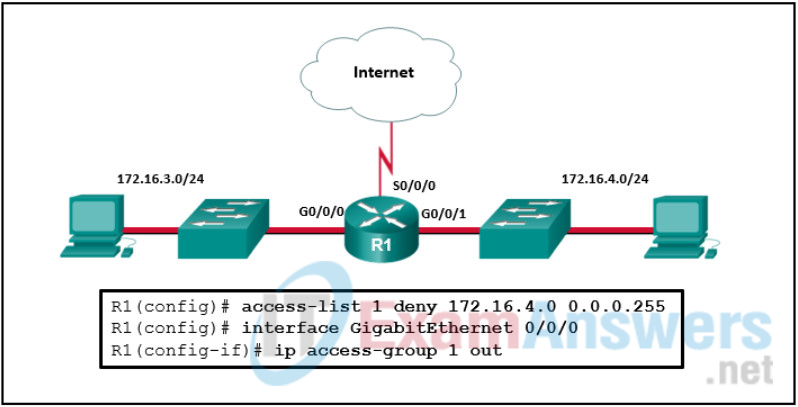 Correct
Correct
Incorrect
Hint
Because of the implicit deny at the end of all ACLs, the access-list 1 permit any command must be included to ensure that only traffic from the 172.16.4.0/24 subnet is blocked and that all other traffic is allowed. -
Question 96 of 159
96. Question
1 pointsWhat is the correct method to configure route summarization on an OSPF router?Correct
Incorrect
-
Question 97 of 159
97. Question
1 pointsThe network administrator configures the router with the ip route 172.16.1.0 255.255.255.0 172.16.2.2 command. How will this route appear in the routing table?Correct
Incorrect
-
Question 98 of 159
98. Question
1 pointsA company has decided to implement VXLANs. What are two types of VTEP interfaces that will be deployed? (Choose two.)Correct
Incorrect
Hint
Each VTEP has two interfaces:- Local LAN interfaces: These interfaces on the local LAN segment provide bridging between local hosts.
- IP interface: This is a core-facing network interface for VXLAN. The IP interface’s IP address helps identify the VTEP in the network. It is also used for VXLAN traffic encapsulation and de-encapsulation.
-
Question 99 of 159
99. Question
1 pointsHow does an antenna add gain to a wireless signal?Correct
Incorrect
Hint
Antennas are passive devices; they do not amplify a transmitter’s signal with any circuitry or external power. Instead, they amplify or add gain to the signal by shaping the RF energy as it is propagated into free space. -
Question 100 of 159
100. Question
1 pointsRefer to the exhibit. A corporate network is using NTP to synchronize the time across devices. What can be determined from the displayed output?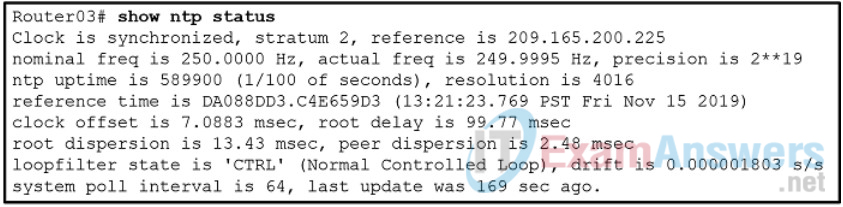 Correct
Correct
Incorrect
-
Question 101 of 159
101. Question
1 pointsRefer to the exhibit. R1 is configured for NAT as displayed. What is wrong with the configuration?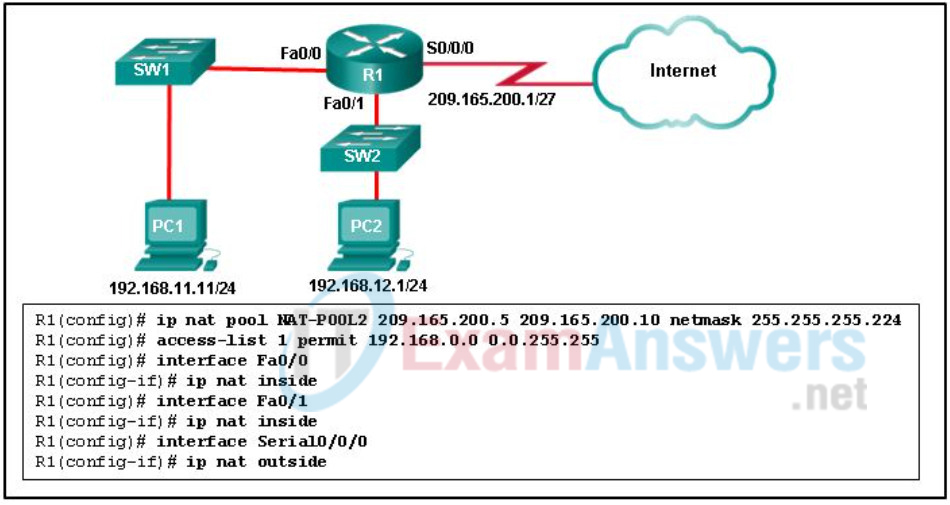 Correct
Correct
Incorrect
Hint
R1 has to have NAT-POOL2 bound to ACL 1. This is accomplished with the command R1(config)#ip nat inside source list 1 pool NAT-POOL2. This would enable the router to check for all interesting traffic and if it matches ACL 1 it would be translated by use of the addresses in NAT-POOL2. -
Question 102 of 159
102. Question
1 pointsWhich type of OSPF link-state advertisement advertises redistributed routes in NSSAs?Correct
Incorrect
Hint
OSPF uses six LSA types for IPv4 routing:- Type 1, router LSA: Advertises the LSAs that originate within an area
- Type 2, network LSA: Advertises a multi-access network segment attached to a DR
- Type 3, summary LSA: Advertises network prefixes that originated from a different area
- Type 4, ASBR summary LSA: Advertises a summary LSA for a specific ASBR
- Type 5, AS external LSA: Advertises LSAs for routes that have been redistributed
- Type 7, NSSA external LSA: Advertises redistributed routes in NSSAs.
-
Question 103 of 159
103. Question
1 pointsWhat command specifies a BGP neighbor that has an IP address of 5.5.5.5/24 and that is in AS 500?Correct
Incorrect
Hint
The neighbor command is used to specify an EBGP neighbor router and peer with it. The command requires that the AS number of the neighbor be included as part of the command. -
Question 104 of 159
104. Question
1 pointsWhich two statements are true about WRED? (Choose two.)Correct
Incorrect
Hint
Weighted random early detection (WRED) is a congestion avoidance mechanism. Different IP precedence and DSCP values each have RED profiles, which determine the probability of packet discard based on the average queue depth of an interface. -
Question 105 of 159
105. Question
1 pointsRefer to the exhibit. Which two networks contain feasible successors? (Choose two.)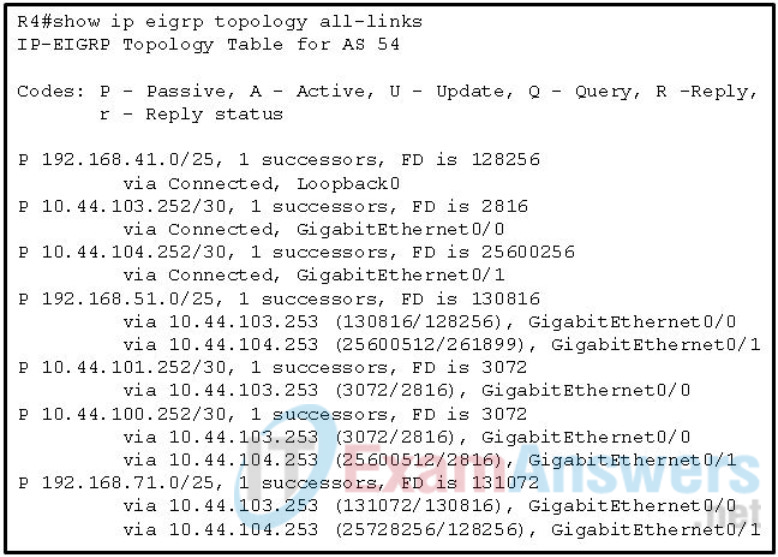 Correct
Correct
Incorrect
Hint
Feasible successors are installed in the EIGRP routing table when the successor becomes unavailable. Feasible successors are backup routes that are have a metric higher than that of successors. -
Question 106 of 159
106. Question
1 pointsRefer to the exhibit. A network administrator issues the show ip protocols command. Based on the exhibited output, what can be concluded?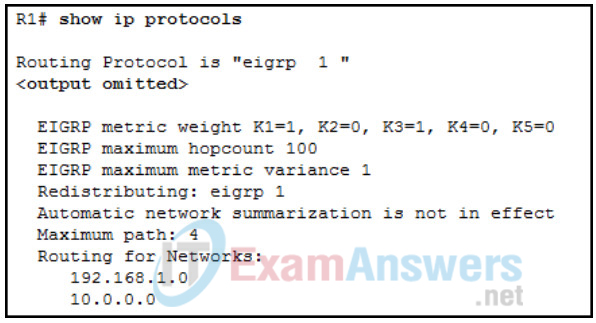 Correct
Correct
Incorrect
Hint
The output indicates that the K values are in default (K1=1, K2=0, K3=1, K4=0, K5=0). The no auto-summary command is used since automatic summarization is not in effect. R1 is advertising the 192.168.1.0 and 10.0.0.0 networks, not receiving advertisements about them. Up to 4 equal metric paths to the same destination network will be included in the routing table since the metric variance parameter is set to 1. -
Question 107 of 159
107. Question
1 pointsWhich three addresses could be used as the destination address for OSPFv3 messages? (Choose three.)Correct
Incorrect
Hint
OSPFv6 messages can be sent to either the OSPF router multicast FF02::5, the OSPF DR/BDR multicast FF02::6, or the link-local address. -
Question 108 of 159
108. Question
1 pointsWhat function is performed by the OSPF designated router?Correct
Incorrect
Hint
OSPF designated routers are elected on multiaccess networks to disseminate LSAs to other OSPF routers. By having a single router disseminate LSAs, the exchanging of LSAs is more efficient. -
Question 109 of 159
109. Question
1 pointsWhat technology will allow containers in different physical servers to communicate?Correct
Incorrect
-
Question 110 of 159
110. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to a collector and aggregator of network telemetry data that uses advanced security analytics to automatically detect threats that infiltrate a network by both inside and outside intruders?Correct
Incorrect
-
Question 111 of 159
111. Question
1 pointsWhich Cisco security architectural framework helps design secure solutions for the various places in the network (PINs)?Correct
Incorrect
Hint
Cisco developed the Cisco SAFE security architecture to help design secure solutions for various places in the network (PINs) such as: the branch, campus, data center, edge, cloud, and WAN. -
Question 112 of 159
112. Question
1 pointsWhich term is used to describe a mapping of one or more VLANs into a single STP tree using MST technology?Correct
Incorrect
-
Question 113 of 159
113. Question
1 pointsHow do WLCs in a mobility group identify each other?Correct
Incorrect
-
Question 114 of 159
114. Question
1 pointsRefer to the exhibit. Considering the route map configuration for BGP, which statement describes the condition for a network prefix to match the route map TEST ?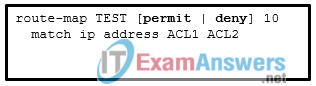 Correct
Correct
Incorrect
Hint
In route map configuration, if there are multiple variables (ACLs, prefix lists, tags, and so on) configured for a specific route map sequence, only one variable must match for the prefix to qualify. The Boolean logic uses an OR operator for this configuration. The processing action is performed only after a match occurs. -
Question 115 of 159
115. Question
1 pointsMultiple paths exist in the BGP table. Assuming the weights are the same, what will the next determining factor be?Correct
Incorrect
-
Question 116 of 159
116. Question
1 pointsWhat are three features of a GRE tunnel? (Choose three.)Correct
Incorrect
-
Question 117 of 159
117. Question
1 pointsRefer to the exhibit. Based on the command output shown, what is the status of the EtherChannel?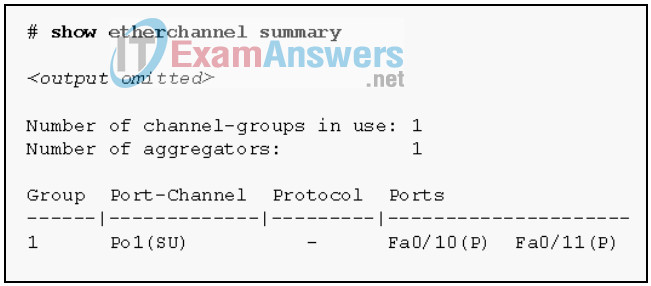 Correct
Correct
Incorrect
Hint
The command output shows the port channel as SU, which means Layer 2 and in use; and the FastEthernet 0/10 and 0/11 interfaces are bundled in port-channel as indicated by the P flag. Configuring the EtherChannel using the channel-group 1 mode on command will cause the Protocol field in the command output to be empty. -
Question 118 of 159
118. Question
1 pointsWhich three options must match in order to establish an EtherChannel between two directly connected switches? (Choose three.)Correct
Incorrect
Hint
Speed and duplex settings must match for all interfaces in an EtherChannel. All interfaces in the EtherChannel must be in the same VLAN if the ports are not configured as trunks. Any ports may be used to establish an EtherChannel. Domain names and port security settings are not relevant to EtherChannel. -
Question 119 of 159
119. Question
1 pointsRefer to the exhibit. On the basis of the information presented, which two IP SLA related statements are true? (Choose two.)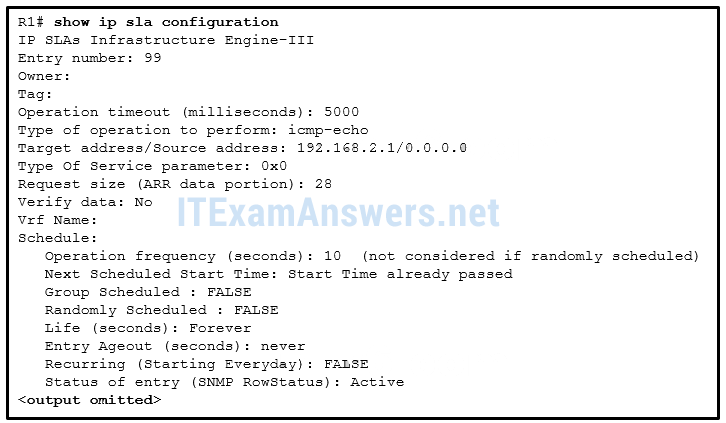 Correct
Correct
Incorrect
Hint
From the output, the IP SLA is configured to perform icmp-echo, the target device is 192.168.2.1, and the icmp-echo requests are sent every 10 seconds. “Start Time already passed” indicates that the operation has started. The “Life” parameter indicates that the setting is “Forever”. -
Question 120 of 159
120. Question
1 pointsMatch the configuration management tool with the component terminology.Correct
Incorrect
-
Question 121 of 159
121. Question
1 pointsWhich three statements describe the characteristics of the Cisco hierarchical network design model? (Choose three.)Correct
Incorrect
-
Question 122 of 159
122. Question
1 pointsA network administrator has configured a Cisco router with the ip flow-export destination 205.168.1.3 2055 command . What are two results of the issued command? (Choose two.)Correct
Incorrect
-
Question 123 of 159
123. Question
1 pointsAn administrator is troubleshooting an 802.11i WLAN which consists of 5 APs and one WLC. The administrator is using a WCS to manage the APs and WLC. The administrator finds that though the WLC has been configured correctly, the Clean Air Zone of impact is not visible for the WLC. Which issue could be causing the problem?Correct
Incorrect
-
Question 124 of 159
124. Question
1 pointsA network administrator is designing the wireless network for a law office. The security policy requires that access to the wireless network must be authenticated with the credentials of employees. The administrator decides to use the WPA2 Enterprise authentication method. Which server is a requirement to deploy WPA2 Enterprise?Correct
Incorrect
-
Question 125 of 159
125. Question
1 pointsRefer to the exhibit. A network administrator is configuring an EtherChannel link between two switches, SW1 and SW2. Which statement describes the effect after the commands are issued on SW1 and SW2?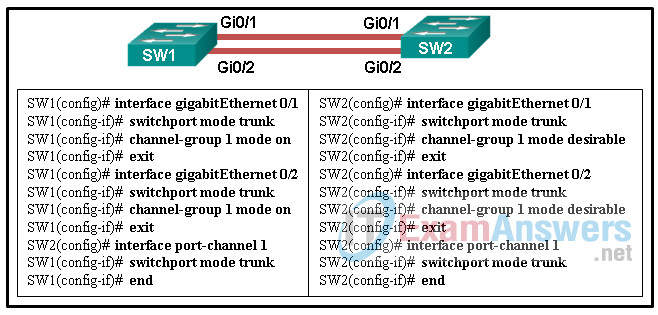 Correct
Correct
Incorrect
Hint
The interfaces GigabitEthernet 0/1 and GigabitEthernet 0/2 are configured “on” for the EtherChannel link. This mode forces the interface to channel without PAgP or LACP. The EtherChannel will be established only if the other side is also set to “on”. However, the mode on SW2 side is set to PAgP desirable. Thus the EtherChannel link will not be established. -
Question 126 of 159
126. Question
1 pointsRefer to the exhibit. A network administrator issues the show bgp ipv4 unicast begin Network command to check the routes in the BGP table. What does the symbol ? at the end of a route indicate?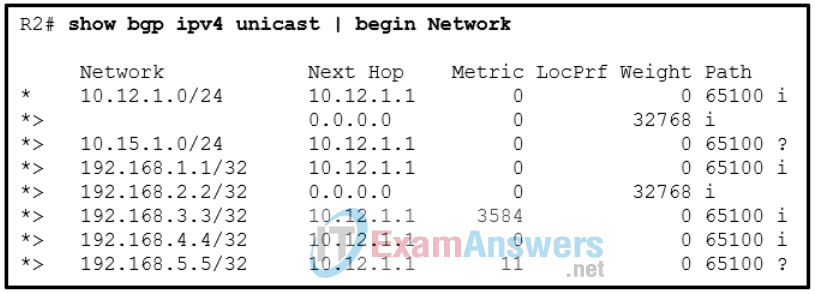 Correct
Correct
Incorrect
Hint
The origin is a well-known mandatory BGP path attribute used in the BGP best-path algorithm. A value of i represents an IGP, e indicates EGP, and ? indicates a route that was redistributed into BGP. -
Question 127 of 159
127. Question
1 pointsWhich component of the Cisco SD-Access Architecture provides policy-based network segmentation and mobility for wired and wireless hosts?Correct
Incorrect
Hint
The SD-Access fabric is the overlay network, and it provides policy-based network segmentation, host mobility for wired and wireless hosts, and enhanced security beyond the normal switching and routing capabilities of a traditional network. -
Question 128 of 159
128. Question
1 pointsRefer to the exhibit. Router R6 has sent a join message to router R4 requesting multicast traffic for users in the multicast group 224.1.1.1. How will the multicast traffic that is sent from the multicast server SRC through the R1-R3-R5 path be handled at router R6?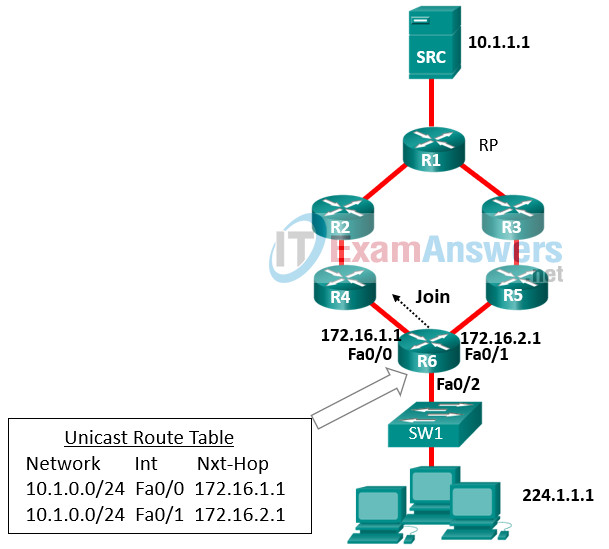 Correct
Correct
Incorrect
-
Question 129 of 159
129. Question
1 pointsAn ABR in a multiarea OSPF network receives LSAs from its neighbor that identify the neighbor as an ASBR with learned external networks from the Internet . Which LSA type would the ABR send to other areas to identify the ASBR , so that internal traffic that is destined for the Internet will be sent through the ASBR?Correct
Incorrect
-
Question 130 of 159
130. Question
1 pointsA network engineer examining the operation of EIGRP on a router notices that one particular route is in an active state. What can the engineer determine about this route?Correct
Incorrect
-
Question 131 of 159
131. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to a cloud delivered DNS service, constantly updated with threat information, that provides the first line of defense before an IP connection is established or a file is downloaded by blocking requests to malicious internet destinations?Correct
Incorrect
-
Question 132 of 159
132. Question
1 pointsA network administrator is setting up the wireless network in a small office. The administrator wants to choose a wireless protocol standard that takes advantage of 5 GHz throughput but is also compatible with a few existing devices that operate at 2.4 GHz. Which wireless standard should the administrator deploy?Correct
Incorrect
Hint
802.11n operates at both 2.4 GHz and 5 GHz and is backward compatible with 802.11b and 802.11g. 802.11b and 802.11g operate at 2.4 GHz only. 802.11a and 802.11ac operate at 5 GHz only. -
Question 133 of 159
133. Question
1 pointsRefer to the exhibit. Which routing protocol would likely be used to distribute routes between these routers?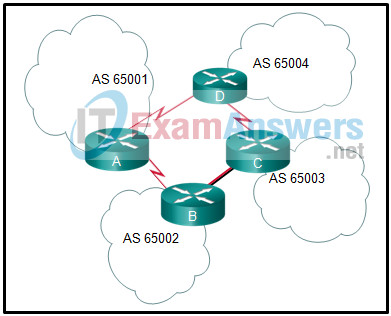 Correct
Correct
Incorrect
-
Question 134 of 159
134. Question
1 pointsMatch the IGMP message type with its value field and description. (Not all options will apply).Correct
Incorrect
-
Question 135 of 159
135. Question
1 pointsWhat are three characteristics of a VLAN access port? (Choose three.)Correct
Incorrect
-
Question 136 of 159
136. Question
1 pointsWhich function is the responsibility of the NFV element manager in the ETSI NFV architectural framework?Correct
Incorrect
Hint
Element managers (EMs), also known as element management systems (EMSs), are responsible for the functional management of VNFs; in other words, they perform fault, configuration, accounting, performance, and security (FCAPS) functions for VNFs. A single EM can manage one or multiple VNFs, and an EM can also be a VNF. -
Question 137 of 159
137. Question
1 pointsRefer to the exhibit. A network administrator is viewing the output from the command show ip nat translations . Which statement correctly describes the NAT translation that is occurring on router RT2?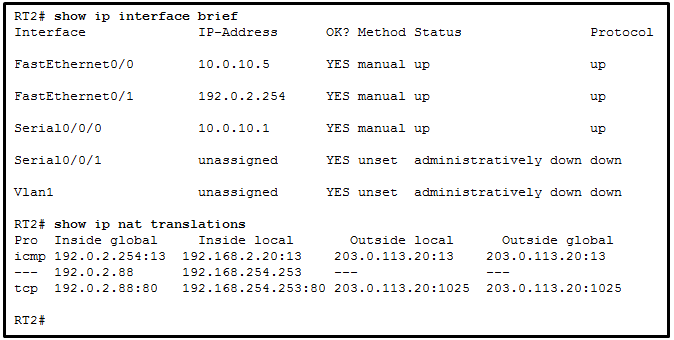 Correct
Correct
Incorrect
Hint
Because no outside local or outside global address is referenced, the traffic from a source IPv4 address of 192.168.254.253 is being translated to 192.0.2.88 by using static NAT. In the output from the command show ip nat translations, the inside local IP address of 192.168.2.20 is being translated into an outside IP address of 192.0.2.254 so that the traffic can cross the public network. A public IPv4 device can connect to the private IPv4 device 192.168.254.253 by targeting the destination IPv4 address of 192.0.2.88. -
Question 138 of 159
138. Question
1 pointsWhich QoS technology provides congestion avoidance by allowing TCP traffic to be throttled before buffers become full and tail drops occur?Correct
Incorrect
Hint
The weighted random early detection (WRED) algorithm provides congestion avoidance on network interfaces by allowing TCP traffic to be throttled before buffers are exhausted. This maximizes network use and TCP-based application performance while minimizing tail drop. -
Question 139 of 159
139. Question
1 pointsWhich type of OSPF link-state advertisement advertises LSAs for routes that have been redistributed?Correct
Incorrect
Hint
Type 5 LSA is External LSA which is generated by Autonomous System Boundary Router ( ASBR ). This LSA contains external route information which is redistributed in OSPF domain. Type 5 LSAs aren’t allowed in stub areas. -
Question 140 of 159
140. Question
1 pointsWhat role does Cisco Umbrella play in the Cisco SAFE framework?Correct
Incorrect
-
Question 141 of 159
141. Question
1 pointsWhen comparing two absolute power values, what can a wireless engineer conclude after calculating a result of 10 dB?Correct
Incorrect
-
Question 142 of 159
142. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to an elite team of security experts who track evolving threats across all parts of networks, cloud environments, and the web to provide a comprehensive understanding and solution for protection against these cyber threats?Correct
Incorrect
-
Question 143 of 159
143. Question
1 pointsA company uses APs to create multiple wireless networks. In one particular area users complain that there is no wireless connectivity. When the network engineer uses the WLC GUI to verify connectivity to the APs, one of the APs does not appear in the list. What should the engineer check first?Correct
Incorrect
-
Question 144 of 159
144. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to a tool that searches for potential network intrusion attacks by monitoring, analysis, and logging of network traffic and also provides advanced threat protection and remediation?Correct
Incorrect
Hint
Next-Generation Intrusion Prevention System (NGIPS): A system that passively monitors and analyzes network traffic for potential network intrusion attacks and logs the intrusion attack data for security analysis is known as an intrusion detection system (IDS). A system that provides IDSfunctions and also automatically blocks intrusion attacks is known as an intrusion prevention system (IPS). -
Question 145 of 159
145. Question
1 pointsRefer to the exhibit. A network administrator is configuring MST tuning on SW1. The objective is to change the priority value of the interface Gi1/0/5 so that the interface is preferred when determining the root ports. Which value could be used in thespanning-tree mst 0 port-prioritycommand to achieve this objective? Correct
Correct
Incorrect
-
Question 146 of 159
146. Question
1 pointsWhich type of OSPF link-state advertisement is an AS external LSA?Correct
Incorrect
-
Question 147 of 159
147. Question
1 pointsA medium-sized company uses APs, WLCs, and laptops for employee workstations. An employee reports the inability to connect to the Internet. A technician verifies that other workstations can successfully connect to the Internet. What are two possible reasons for the problem? (Choose two.)Correct
Incorrect
-
Question 148 of 159
148. Question
1 pointsRefer to the exhibit. Spanning-tree port priorities are 128 for all interfaces. The network administrator enters thespanning-tree vlan 1 root primarycommand on S4. Which two port results are correct? (Choose two.)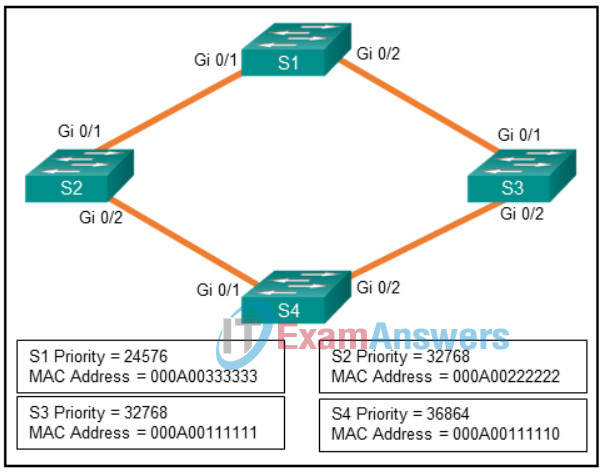 Correct
Correct
Incorrect
-
Question 149 of 159
149. Question
1 pointsWhich service should be disabled on a router to prevent a malicious host from falsely responding to ARP requests with the intent to redirect the Ethernet frames?Correct
Incorrect
Hint
Proxy ARP is a technique used on a device on a network to answer ARP queries for a device on another network. This service should be disabled on a router and the correct default gateway address should be configured (manually or by DHCP) for the normal process of remote network access. CDP and LLDP are device discovery protocols. Reverse ARP is used to resolve IP addresses. -
Question 150 of 159
150. Question
1 pointsMatch the DTP mode with its function. (Not all options are used.)Correct
Incorrect
Hint
The dynamic auto mode makes the interface become a trunk interface if the neighboring interface is set to trunk or desirable mode. The dynamic desirable mode makes the interface actively attempt to convert the link to a trunk link. The trunk mode puts the interface into permanent trunking mode and negotiates to convert the neighboring link into a trunk link. The nonegotiate mode prevents the interface from generating DTP frames. -
Question 151 of 159
151. Question
1 pointsWhich type of OSPF link-state advertisement is an ASBR summary LSA?Correct
Incorrect
-
Question 152 of 159
152. Question
1 pointsWhat are two reasons for creating an OSPF network with multiple areas? (Choose two.)Correct
Incorrect
Hint
If a router is not running OSPF, it is not configurable with an OSPF area. OSPF areas have no direct relationship with the Internet. Routers that run OSPF can connect to the Internet, but multiple OSPF areas are not required for this purpose. OSPF areas help to decrease the demand for router memory and processing power by limiting OSPF protocol traffic, keeping link-state databases small, and requiring fewer SPF recalculations. Multiarea OSPF requires additional steps to configure and therefore does not simplify the configuration process. -
Question 153 of 159
153. Question
1 pointsWhat are three types of IP packets that require process switching and cannot be forwarded by CEF in a Cisco router? (Choose three.)Correct
Incorrect
-
Question 154 of 159
154. Question
1 pointsMatch the RESTful API method to CRUD function.Correct
Incorrect
-
Question 155 of 159
155. Question
1 pointsWhich type of OSPF link-state advertisement advertises a summary LSA for a specific ASBR?Correct
Incorrect
-
Question 156 of 159
156. Question
1 pointsA student is studying in preparation for an interview for a job in programming and network automation. What is a characteristic of Puppet ?Correct
Incorrect
-
Question 157 of 159
157. Question
1 pointsCisco has created a security framework to help protect networks from ever-evolving cybersecurity threats. What is the term given to an all-in-one web gateway that uses real-time intelligence to prevent the latest malware websites from infiltrating the network?Correct
Incorrect
-
Question 158 of 159
158. Question
1 pointsMatch the Chef component to the description.Correct
Incorrect
-
Question 159 of 159
159. Question
1 pointsRefer to the exhibit. Assuming both routers have IPv6 routing enabled and router R1 is configured for OSPFv3 as shown, which set of configuration commands on R2 is required to allow an OSPFv3 adjacency to form between the two routers?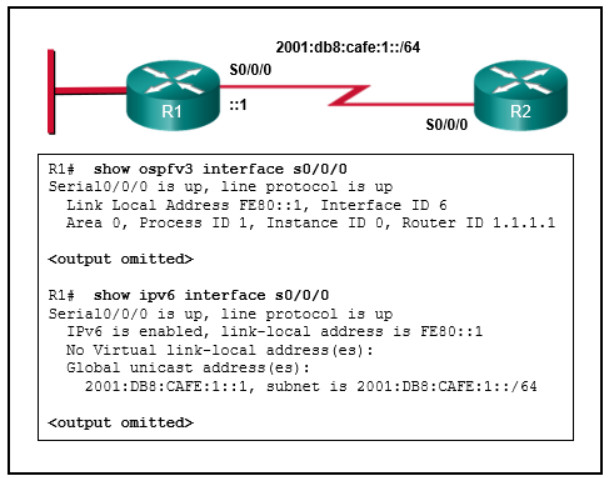 Correct
Correct
Incorrect
