Time limit: 0
Quiz-summary
0 of 188 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
Information
Good Luck For You!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 188 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- Answered
- Review
-
Question 1 of 188
1. Question
1 pointsHow many bits make up the single IPv6 hextet :10CD:?Correct
Incorrect
-
Question 2 of 188
2. Question
1 pointsWhat is the effect of configuring the ipv6 unicast-routing command on a router?Correct
Incorrect
-
Question 3 of 188
3. Question
1 pointsWhich group of IPv6 addresses cannot be allocated as a host source address?Correct
Incorrect
-
Question 4 of 188
4. Question
1 pointsWhat is the purpose of ICMP messages?Correct
Incorrect
-
Question 5 of 188
5. Question
1 pointsRefer to the exhibit. A technician has configured a user workstation with the IP address and default subnet masks that are shown. Although the user can access all local LAN resources, the user cannot access any Internet sites by using either FQDN or IP addresses. Based upon the exhibit, what could account for this failure?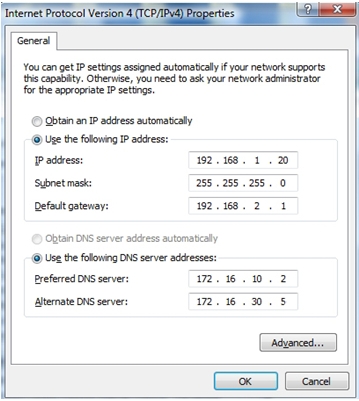 CCNA 1 Final Exam Answer 007 (v5.02, 2015) Correct
CCNA 1 Final Exam Answer 007 (v5.02, 2015) Correct
Incorrect
-
Question 6 of 188
6. Question
1 pointsWhich subnet would include the address 192.168.1.96 as a usable host address?Correct
Incorrect
-
Question 7 of 188
7. Question
1 pointsA network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?Correct
Incorrect
-
Question 8 of 188
8. Question
1 pointsRefer to the exhibit. Which IP addressing scheme should be changed?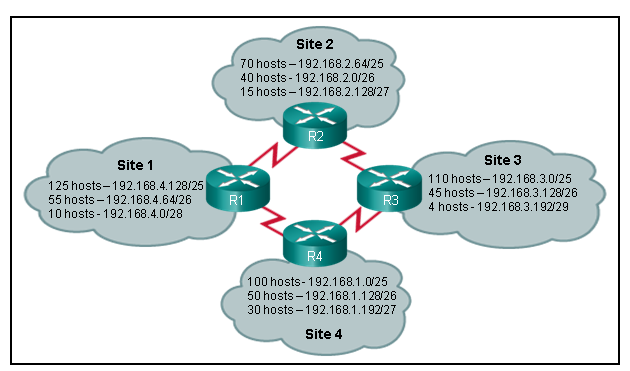 CCNA 1 Final Exam Answer 008 (v5.02, 2015) Correct
CCNA 1 Final Exam Answer 008 (v5.02, 2015) Correct
Incorrect
-
Question 9 of 188
9. Question
1 pointsWhich two notations are useable nibble boundaries when subnetting in IPv6? (Choose two.)Correct
Incorrect
-
Question 10 of 188
10. Question
1 pointsA host PC has just booted and is attempting to lease an address through DHCP. Which two messages will the client typically broadcast on the network? (Choose two.)Correct
Incorrect
-
Question 11 of 188
11. Question
1 pointsWhat is the purpose of the network security accounting function?Correct
Incorrect
-
Question 12 of 188
12. Question
1 pointsWhen applied to a router, which command would help mitigate brute-force password attacks against the router?Correct
Incorrect
-
Question 13 of 188
13. Question
1 pointsA particular website does not appear to be responding on a Windows 7 computer. What command could the technician use to show any cached DNS entries for this web page?Correct
Incorrect
-
Question 14 of 188
14. Question
1 pointsRefer to the exhibit. The network administrator enters these commands into the R1 router: R1# copy running-config tftp Address or name of remote host [ ]? When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?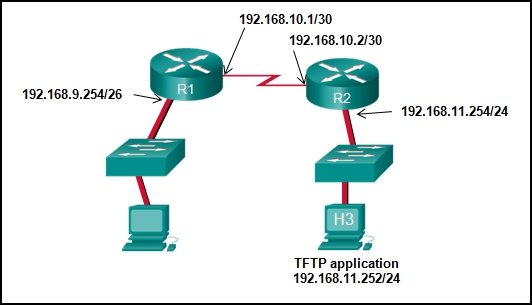 CCNA 1 Final Exam Answer 009 (v5.02, 2015) Correct
CCNA 1 Final Exam Answer 009 (v5.02, 2015) Correct
Incorrect
-
Question 15 of 188
15. Question
1 pointsWhat two preconfigured settings that affect security are found on most new wireless routers? (Choose two.)Correct
Incorrect
-
Question 16 of 188
16. Question
1 pointsWhich type of wireless security generates dynamic encryption keys each time a client associates with an AP?Correct
Incorrect
-
Question 17 of 188
17. Question
1 pointsWhich two components are necessary for a wireless client to be installed on a WLAN? (Choose two.)Correct
Incorrect
-
Question 18 of 188
18. Question
1 pointsA host is accessing an FTP server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.)Correct
Incorrect
-
Question 19 of 188
19. Question
1 pointsWhen is a dial-up connection used to connect to an ISP?Correct
Incorrect
-
Question 20 of 188
20. Question
1 pointsOn a school network, students are surfing the web, searching the library database, and attending an audio conference with their sister school in Japan. If network traffic is prioritized with QoS, how will the traffic be classified from highest priority to lowest priority?Correct
Incorrect
-
Question 21 of 188
21. Question
1 pointsDuring normal operation, from which location do most Cisco routers run the IOS?Correct
Incorrect
-
Question 22 of 188
22. Question
1 pointsWhich connection provides a secure CLI session with encryption to a Cisco switch?Correct
Incorrect
-
Question 23 of 188
23. Question
1 pointsWhich keys act as a hot key combination that is used to interrupt an IOS process?Correct
Incorrect
-
Question 24 of 188
24. Question
1 pointsRefer to the exhibit. An administrator wants to change the name of a brand new switch, using the hostname command as shown. What prompt will display after the command is issued?? Correct
Correct
Incorrect
-
Question 25 of 188
25. Question
1 pointsAfter making configuration changes on a Cisco switch, a network administrator issues a copy running-config startup-config command. What is the result of issuing this command?Correct
Incorrect
-
Question 26 of 188
26. Question
1 pointsOn which switch interface would an administrator configure an IP address so that the switch can be managed remotely?Correct
Incorrect
-
Question 27 of 188
27. Question
1 pointsA technician uses the ping 127.0.0.1 command. What is the technician testing?Correct
Incorrect
-
Question 28 of 188
28. Question
1 pointsWhich device should be used for enabling a host to communicate with another host on a different network?Correct
Incorrect
-
Question 29 of 188
29. Question
1 pointsA network technician is measuring the transfer of bits across the company backbone for a mission critical application. The technician notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)Correct
Incorrect
-
Question 30 of 188
30. Question
1 pointsWhich characteristics describe fiber optic cable? (Choose two.)Correct
Incorrect
-
Question 31 of 188
31. Question
1 pointsWhat are two features of a physical, star network topology? (Choose two.)Correct
Incorrect
-
Question 32 of 188
32. Question
1 pointsA frame is transmitted from one networking device to another. Why does the receiving device check the FCS field in the frame?Correct
Incorrect
-
Question 33 of 188
33. Question
1 pointsWhat will a Layer 2 switch do when the destination MAC address of a received frame is not in the MAC table?Correct
Incorrect
-
Question 34 of 188
34. Question
1 pointsWhich switching method has the lowest level of latency?Correct
Incorrect
-
Question 35 of 188
35. Question
1 pointsWhich parameter does the router use to choose the path to the destination when there are multiple routes available?Correct
Incorrect
-
Question 36 of 188
36. Question
1 pointsWhich two statements describe the functions or characteristics of ROM in a router? (Choose two.)Correct
Incorrect
-
Question 37 of 188
37. Question
1 pointsWhich statement describes a characteristic of the Cisco router management ports?Correct
Incorrect
-
Question 38 of 188
38. Question
1 pointsWhat happens when part of an Internet radio transmission is not delivered to the destination?Correct
Incorrect
-
Question 39 of 188
39. Question
1 pointsWhat is the dotted decimal representation of the IPv4 address 11001011.00000000.01110001.11010011?Correct
Incorrect
-
Question 40 of 188
40. Question
1 pointsWhich three IP addresses are private ? (Choose three.)Correct
Incorrect
-
Question 41 of 188
41. Question
1 pointsWhat types of addresses make up the majority of addresses within the /8 block IPv4 bit space?Correct
Incorrect
-
Question 42 of 188
42. Question
1 pointsRefer to the exhibit. What is the maximum TTL value that is used to reach the destination www.cisco.com??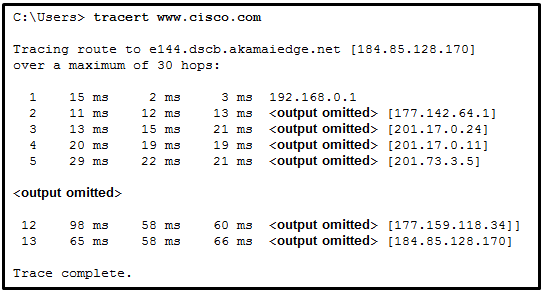 Correct
Correct
Incorrect
-
Question 43 of 188
43. Question
1 pointsA company has a network address of 192.168.1.64 with a subnet mask of 255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks would achieve that? (Choose two.)Correct
Incorrect
-
Question 44 of 188
44. Question
1 pointsIn a network that uses IPv4, what prefix would best fit a subnet containing 100 hosts?Correct
Incorrect
-
Question 45 of 188
45. Question
1 pointsWhich protocol supports rapid delivery of streaming media?Correct
Incorrect
-
Question 46 of 188
46. Question
1 pointsWhy would a network administrator use the tracert utility?Correct
Incorrect
-
Question 47 of 188
47. Question
1 pointsRefer to the exhibit. What is the significance of the asterisk (*) in the exhibited output?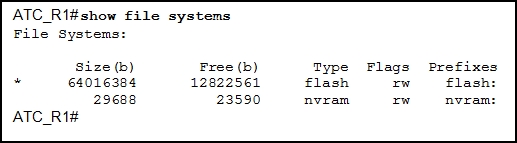 Correct
Correct
Incorrect
-
Question 48 of 188
48. Question
1 pointsWhich WLAN security protocol generates a new dynamic key each time a client establishes a connection with the AP?Correct
Incorrect
-
Question 49 of 188
49. Question
1 pointsA host is accessing a Telnet server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.)Correct
Incorrect
-
Question 50 of 188
50. Question
1 pointsRefer to the exhibit. Which area would most likely be an extranet for the company network that is shown?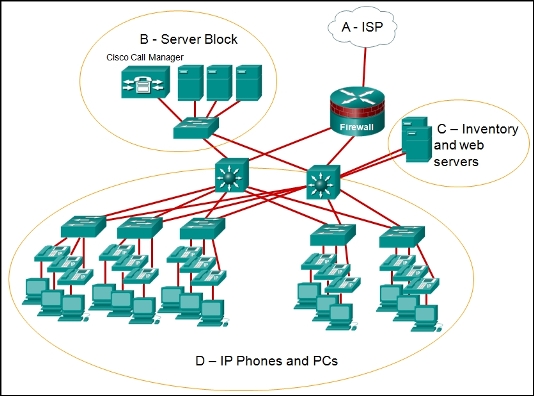 Correct
Correct
Incorrect
-
Question 51 of 188
51. Question
1 pointsWhat is the purpose of having a converged network?Correct
Incorrect
-
Question 52 of 188
52. Question
1 pointsThree office workers are using the corporate network. The first employee uses a web browser to view a company web page in order to read some announcements. The second employee accesses the corporate database to perform some financial transactions. The third employee participates in an important live audio conference with other office workers in branch offices. If QoS is implemented on this network, what will be the priorities from highest to lowest of the different data types?Correct
Incorrect
-
Question 53 of 188
53. Question
1 pointsDuring normal operation, from which location do most Cisco switches and routers run the IOS?Correct
Incorrect
-
Question 54 of 188
54. Question
1 pointsA network administrator is making changes to the configuration of a router. After making the changes and verifying the results, the administrator issues the copy running-config startup-config command. What will happen after this command executes?Correct
Incorrect
-
Question 55 of 188
55. Question
1 pointsWhat information does the loopback test provide?Correct
Incorrect
-
Question 56 of 188
56. Question
1 pointsWhat is a characteristic of the LLC sublayer?Correct
Incorrect
-
Question 57 of 188
57. Question
1 pointsWhat method is used to manage contention-based access on a wireless network?Correct
Incorrect
-
Question 58 of 188
58. Question
1 pointsWhat happens when a switch receives a frame and the calculated CRC value is different than the value that is in the FCS field?Correct
Incorrect
-
Question 59 of 188
59. Question
1 pointsWhich destination address is used in an ARP request frame?Correct
Incorrect
-
Question 60 of 188
60. Question
1 pointsWhat is the auto-MDIX feature on a switch?Correct
Incorrect
-
Question 61 of 188
61. Question
1 pointsWhich frame forwarding method receives the entire frame and performs a CRC check to detect errors before forwarding the frame?Correct
Incorrect
-
Question 62 of 188
62. Question
1 pointsWhat are the two main components of Cisco Express Forwarding (CEF)? (Choose two.)Correct
Incorrect
-
Question 63 of 188
63. Question
1 pointsWhich statement describes the sequence of processes executed by a router when it receives a packet from a host to be delivered to a host on another network?Correct
Incorrect
-
Question 64 of 188
64. Question
1 pointsWhich technology provides a solution to IPv4 address depletion by allowing multiple devices to share one public IP address?Correct
Incorrect
-
Question 65 of 188
65. Question
1 pointsRefer to the exhibit. Router R1 has two interfaces that were configured with correct IP addresses and subnet masks. Why does the show ip route command output not display any information about the directly connected networks??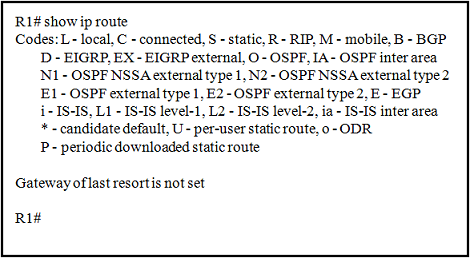 Correct
Correct
Incorrect
-
Question 66 of 188
66. Question
1 pointsWhat happens when part of an Internet television transmission is not delivered to the destination?Correct
Incorrect
-
Question 67 of 188
67. Question
1 pointsWhich three statements characterize the transport layer protocols? (Choose three.)Correct
Incorrect
-
Question 68 of 188
68. Question
1 pointsA user opens three browsers on the same PC to access www.cisco.com to search for certification course information. The Cisco web server sends a datagram as a reply to the request from one of the web browsers. Which information is used by the TCP/IP protocol stack in the PC to identify the destination web browser?Correct
Incorrect
-
Question 69 of 188
69. Question
1 pointsWhich statement is true regarding the UDP client process during a session with a server?Correct
Incorrect
-
Question 70 of 188
70. Question
1 pointsWhich two components are configured via software in order for a PC to participate in a network environment? (Choose two.)Correct
Incorrect
-
Question 71 of 188
71. Question
1 pointsWhat are three characteristics of multicast transmission? (Choose three.)Correct
Incorrect
-
Question 72 of 188
72. Question
1 pointsWhich two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)Correct
Incorrect
-
Question 73 of 188
73. Question
1 pointsWhat is the subnet address for the address 2001:DB8:BC15:A:12AB::1/64?Correct
Incorrect
-
Question 74 of 188
74. Question
1 pointsWhich two tasks are functions of the presentation layer? (Choose two.)Correct
Incorrect
-
Question 75 of 188
75. Question
1 pointsWhat is the purpose of the network security authentication function?Correct
Incorrect
-
Question 76 of 188
76. Question
1 pointsWhich type of wireless security makes use of dynamic encryption keys each time a client associates with an AP?Correct
Incorrect
-
Question 77 of 188
77. Question
1 pointsA PC is configured to obtain an IP address automatically from network 192.168.1.0/24. The network administrator issues the arp –a command and notices an entry of 192.168.1.255 ff-ff-ff-ff-ff-ff. Which statement describes this entry?Correct
Incorrect
-
Question 78 of 188
78. Question
1 pointsWhich field in an IPv4 packet header will typically stay the same during its transmission?Correct
Incorrect
-
Question 79 of 188
79. Question
1 pointsLaunch PT – Hide and Save PT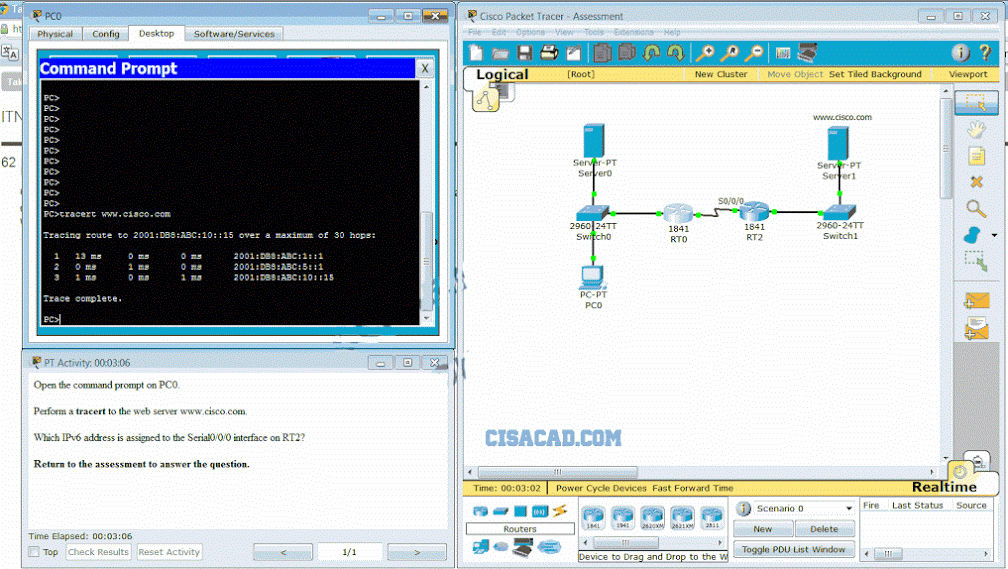 Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which IPv6 address is assigned to the Serial0/0/0 interface on RT2? Correct
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
Which IPv6 address is assigned to the Serial0/0/0 interface on RT2? Correct
Incorrect
-
Question 80 of 188
80. Question
1 pointsThree bank employees are using the corporate network. The first employee uses a web browser to view a company web page in order to read some announcements. The second employee accesses the corporate database to perform some financial transactions. The third employee participates in an important live audio conference with other corporate managers in branch offices. If QoS is implemented on this network, what will be the priorities from highest to lowest of the different data types?Correct
Incorrect
-
Question 81 of 188
81. Question
1 pointsRefer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator has already logged into a Telnet session on the switch, which password is needed to access privileged EXEC mode?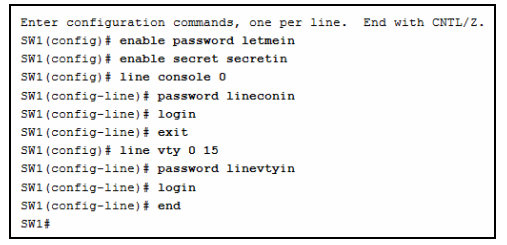 Correct
Correct
Incorrect
-
Question 82 of 188
82. Question
1 pointsWhat are the three primary functions provided by Layer 2 data encapsulation? (Choose three.)Correct
Incorrect
-
Question 83 of 188
83. Question
1 pointsWhat must be configured to enable Cisco Express Forwarding (CEF) on most Cisco devices that perform Layer 3 switching?Correct
Incorrect
-
Question 84 of 188
84. Question
1 pointsWhat is the purpose of adjacency tables as used in Cisco Express Forwarding (CEF)?Correct
Incorrect
-
Question 85 of 188
85. Question
1 pointsWhich statement describes a characteristic of the network layer in the OSI model?Correct
Incorrect
-
Question 86 of 188
86. Question
1 pointsA user gets an IP address of 192.168.0.1 from the company network administrator. A friend of the user at a different company gets the same IP address on another PC. How can two PCs use the same IP address and still reach the Internet, send and receive email, and search the web?Correct
Incorrect
-
Question 87 of 188
87. Question
1 pointsAt a minimum, which address is required on IPv6-enabled interfaces?Correct
Incorrect
-
Question 88 of 188
88. Question
1 pointsWhy does HTTP use TCP as the transport layer protocol?Correct
Incorrect
-
Question 89 of 188
89. Question
1 pointsWhat is the binary representation of 0xCA?Correct
Incorrect
-
Question 90 of 188
90. Question
1 pointsWhat is the valid most compressed format possible of the IPv6 address 2001:0DB8:0000:AB00:0000:0000:0000:1234?Correct
Incorrect
-
Question 91 of 188
91. Question
1 pointsWhat field content is used by ICMPv6 to determine that a packet has expired?Correct
Incorrect
-
Question 92 of 188
92. Question
1 pointsWhich statement is true about variable-length subnet masking?Correct
Incorrect
-
Question 93 of 188
93. Question
1 pointsWhich firewall technique blocks incoming packets unless they are responses to internal requests?Correct
Incorrect
-
Question 94 of 188
94. Question
1 pointsA network technician is investigating network connectivity from a PC to a remote host with the address 10.1.1.5. Which command issued on the PC will return to the technician the complete path to the remote host?Correct
Incorrect
-
Question 95 of 188
95. Question
1 pointsA network engineer is measuring the transfer of bits across the company backbone for a mission critical database application. The engineer notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)Correct
Incorrect
-
Question 96 of 188
96. Question
1 pointsWhat is a possible hazard that can be caused by network cables in a fire?Correct
Incorrect
-
Question 97 of 188
97. Question
1 pointsWhat device is commonly used to verify a UTP cable?Correct
Incorrect
-
Question 98 of 188
98. Question
1 pointsWhat needs to be checked when testing a UTP network cable?Correct
Incorrect
-
Question 99 of 188
99. Question
1 pointsRefer to the exhibit. A ping to PC2 is issued from PC0, PC1, and PC3 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?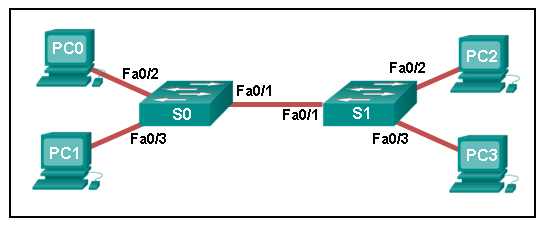 Correct
Correct
Incorrect
-
Question 100 of 188
100. Question
1 pointsWhich function is provided by TCP?Correct
Incorrect
-
Question 101 of 188
101. Question
1 pointsWhat does a router use to determine where to send data it receives from the network?Correct
Incorrect
-
Question 102 of 188
102. Question
1 pointsWhich router interface should be used for direct remote access to the router via a modem?Correct
Incorrect
-
Question 103 of 188
103. Question
1 pointsA technician is configuring a router to allow for all forms of management access. As part of each different type of access, the technician is trying to type the command login. Which configuration mode should be entered to do this task?Correct
Incorrect
-
Question 104 of 188
104. Question
1 pointsWhich communication tool allows real-time collaboration?Correct
Incorrect
-
Question 105 of 188
105. Question
1 pointsA host is accessing a Web server on a remote network. Which three functions are performed by intermediary network devices during this conversation? (Choose three.)Correct
Incorrect
-
Question 106 of 188
106. Question
1 pointsA home user is looking for an ISP connection that provides high speed digital transmission over regular phone lines. What ISP connection type should be used?Correct
Incorrect
-
Question 107 of 188
107. Question
1 pointsRefer to the exhibit. From which location did this router load the IOS?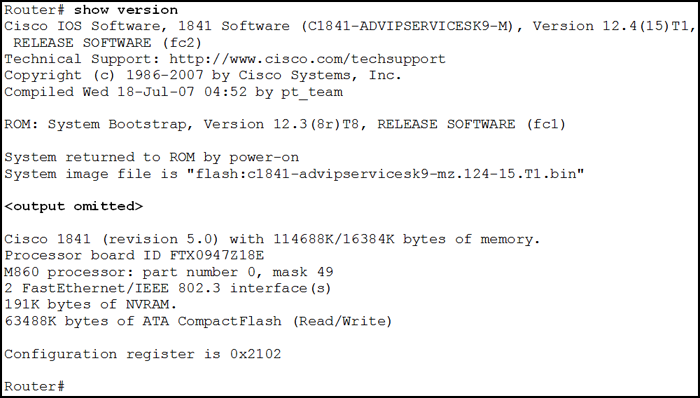 Correct
Correct
Incorrect
-
Question 108 of 188
108. Question
1 pointsWhich connection provides a secure CLI session with encryption to a Cisco network device?Correct
Incorrect
-
Question 109 of 188
109. Question
1 pointsRefer to the exhibit. An administrator is trying to configure the switch but receives the error message that is displayed in the exhibit. What is the problem?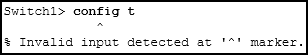 Correct
Correct
Incorrect
-
Question 110 of 188
110. Question
1 pointsAn administrator uses the Ctrl-Shift-6 key combination on a switch after issuing the ping command. What is the purpose of using these keystrokes?Correct
Incorrect
-
Question 111 of 188
111. Question
1 pointsWhat function does pressing the Tab key have when entering a command in IOS?Correct
Incorrect
-
Question 112 of 188
112. Question
1 pointsRefer to the exhibit. An administrator wants to change the name of a brand new switch, using the hostname command as shown. What prompt will display after the command is issued? Correct
Correct
Incorrect
-
Question 113 of 188
113. Question
1 pointsRefer to the exhibit. A network administrator is configuring access control to switch SW1. If the administrator uses Telnet to connect to the switch, which password is needed tss user EXEC mode?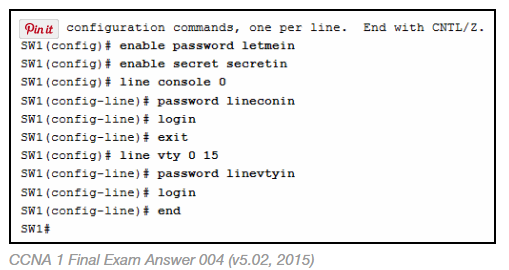 Correct
Correct
Incorrect
-
Question 114 of 188
114. Question
1 pointsAfter making configuration changes, a network administrator issues a copy running-config startup-config command in a Cisco switch. What is the result of issuing this command?Correct
Incorrect
-
Question 115 of 188
115. Question
1 pointsRefer to the exhibit. Which action will be successful?Correct
Incorrect
-
Question 116 of 188
116. Question
1 pointsWhich IPv4 address can be pinged to test the internal TCP/IP operation of a host?Correct
Incorrect
-
Question 117 of 188
117. Question
1 pointsWhat three application layer protocols are part of the TCP/IP protocol suite? (Choose three.)Correct
Incorrect
-
Question 118 of 188
118. Question
1 pointsWhich two protocols function at the internet layer? (Choose two.)Correct
Incorrect
-
Question 119 of 188
119. Question
1 pointsWhich publicly available resources describe protocols, processes, and technologies for the Internet but do not give implementation details?Correct
Incorrect
-
Question 120 of 188
120. Question
1 pointsWhich address on a PC does not change, even if the PC is moved to a different network?Correct
Incorrect
-
Question 121 of 188
121. Question
1 pointsWhat is the protocol that is used to discover a physical address from a known logical address and what message type does it use?Correct
Incorrect
-
Question 122 of 188
122. Question
1 pointsWhat will happen if the default gateway address is incorrectly configured on a host?Correct
Incorrect
-
Question 123 of 188
123. Question
1 pointsWhat is an important function of the physical layer of the OSI model?Correct
Incorrect
-
Question 124 of 188
124. Question
1 pointsWhich procedure is used to reduce the effect of crosstalk in copper cables?Correct
Incorrect
-
Question 125 of 188
125. Question
1 pointsWhich two statements describe the characteristics of fiber-optic cabling? (Choose two.)Correct
Incorrect
-
Question 126 of 188
126. Question
1 pointsWhat is contained in the trailer of a data-link frame?Correct
Incorrect
-
Question 127 of 188
127. Question
1 pointsWhat is the auto-MDIX feature on a switch?Correct
Incorrect
-
Question 128 of 188
128. Question
1 pointsRefer to the exhibit. A ping to PC3 is issued from PC0, PC1, and PC2 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?Correct
Incorrect
-
Question 129 of 188
129. Question
1 pointsHow does a Layer 3 switch differ from a Layer 2 switch?Correct
Incorrect
-
Question 130 of 188
130. Question
1 pointsWhat is the purpose of the routing process?Correct
Incorrect
-
Question 131 of 188
131. Question
1 pointsWhich technology provides a solution to IPv4 address depletion by allowing multiple devices to share one public IP address?Correct
Incorrect
-
Question 132 of 188
132. Question
1 pointsRefer to the exhibit. Consider the IP address configuration shown from PC1. What is a description of the default gateway address?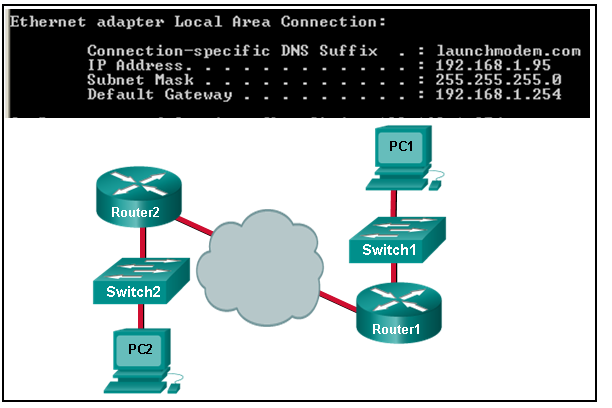 Correct
Correct
Incorrect
-
Question 133 of 188
133. Question
1 pointsWhich of the following are primary functions of a router? (Choose two.)Correct
Incorrect
-
Question 134 of 188
134. Question
1 pointsWhich two statements correctly describe a router memory type and its contents? (Choose two.)Correct
Incorrect
-
Question 135 of 188
135. Question
1 pointsIn which default order will a router search for startup configuration information?Correct
Incorrect
-
Question 136 of 188
136. Question
1 pointsWhat happens when part of an Internet VoIP transmission is not delivered to the destination?Correct
Incorrect
-
Question 137 of 188
137. Question
1 pointsWhich three IP addresses are private ? (Choose three.)Correct
Incorrect
-
Question 138 of 188
138. Question
1 pointsWhich three statements characterize the transport layer protocols? (Choose three.)Correct
Incorrect
-
Question 139 of 188
139. Question
1 pointsRefer to the exhibit. A TCP segment from a server has been captured by Wireshark, which is running on a host. What acknowledgement number will the host return for the TCP segment that has been received?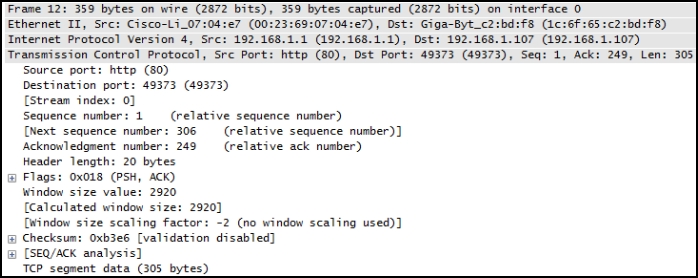 Correct
Correct
Incorrect
-
Question 140 of 188
140. Question
1 pointsWhich statement is true about an interface that is configured with the IPv6 address command?Correct
Incorrect
-
Question 141 of 188
141. Question
1 pointsRefer to the exhibit. The network administrator for a small advertising company has chosen to use the 192.168.5.96/27 network for internal LAN addressing. As shown in the exhibit, a static IP address is assigned to the company web server. However, the web server cannot access the Internet. The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet, and the web server is able to ping local workstations. Which component is incorrectly configured? Correct
Correct
Incorrect
-
Question 142 of 188
142. Question
1 pointsRefer to the exhibit. An administrator must send a message to everyone on the router A network. What is the broadcast address for network 172.16.16.0/22?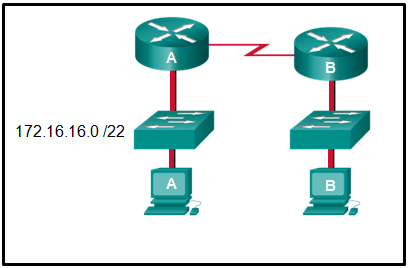 Correct
Correct
Incorrect
-
Question 143 of 188
143. Question
1 pointsA network administrator is variably subnetting a given block of IPv4 addresses. Which combination of network addresses and prefix lengths will make the most efficient use of addresses when the need is for 2 subnets capable of supporting 10 hosts and 1 subnet that can support 6 hosts?Correct
Incorrect
-
Question 144 of 188
144. Question
1 pointsHow many additional bits should be borrowed from a /26 subnet mask in order to create subnets for WAN links that need only 2 useable addresses?Correct
Incorrect
-
Question 145 of 188
145. Question
1 pointsRefer to the exhibit. The administrator configured the access to the console and the vty lines of a router. Which conclusion can be drawn from this configuration?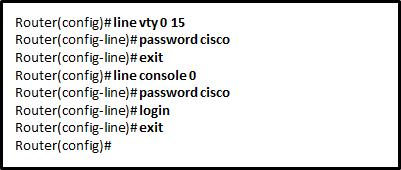 Correct
Correct
Incorrect
-
Question 146 of 188
146. Question
1 pointsAn administrator issued the service password-encryption command to apply encryption to the passwords configured for enable password, vty, and console lines. What will be the consequences if the administrator later issues the no service password-encryption command?Correct
Incorrect
-
Question 147 of 188
147. Question
1 pointsAfter making configuration changes, a network administrator issues a copy running-config startup-config command in a Cisco switch. What is the result of issuing this command?Correct
Incorrect
-
Question 148 of 188
148. Question
1 pointsWhat are two features of ARP? (Choose two.)Correct
Incorrect
-
Question 149 of 188
149. Question
1 pointsWhat are two examples of the cut-through switching method? (Choose two.)Correct
Incorrect
-
Question 150 of 188
150. Question
1 pointsA network administrator is enabling services on a newly installed server. Which two statements describe how services are used on a server? (Choose two.)Correct
Incorrect
-
Question 151 of 188
151. Question
1 pointsWhy does a Layer 3 device perform the ANDing process on a destination IP address and subnet mask?Correct
Incorrect
-
Question 152 of 188
152. Question
1 pointsGiven the binary address of 11101100 00010001 00001100 00001010, which address does this represent in dotted decimal format?Correct
Incorrect
-
Question 153 of 188
153. Question
1 pointsA particular telnet site does not appear to be responding on a Windows 7 computer. What command could the technician use to show any cached DNS entries for this web page?Correct
Incorrect
-
Question 154 of 188
154. Question
1 pointsRefer to the exhibit. What is the maximum TIL value that is used to reach the destination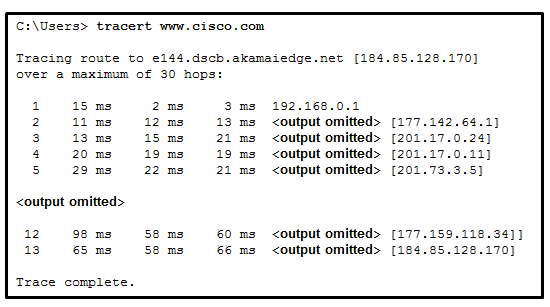 Correct
Correct
Incorrect
-
Question 155 of 188
155. Question
1 pointsWhich statement is true about DHCP operation?Correct
Incorrect
-
Question 156 of 188
156. Question
1 pointsWhich type of wireless security is easily compromised?Correct
Incorrect
-
Question 157 of 188
157. Question
1 pointsA network administrator notices that the throughput on the network appears lower than expected when compared to the end-to-end network bandwidth. Which three factors can explain this difference? (Choose three.)Correct
Incorrect
-
Question 158 of 188
158. Question
1 pointsA host PC is attempting to lease an address through DHCP. What message is sent by the server to the client know it is able to use the provided IP information?Correct
Incorrect
-
Question 159 of 188
159. Question
1 pointsA network administrator is configuring access control to switch SW1. If the administrator uses console line to connect to the switch, which password is needed to access user EXEC mode?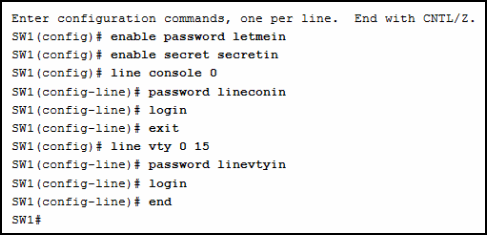 Correct
Correct
Incorrect
-
Question 160 of 188
160. Question
1 pointsWhat is a characteristic of UTP cabling?Correct
Incorrect
-
Question 161 of 188
161. Question
1 pointsHow many bits would need to be borrowed if a network admin were given the IP addressing scheme of 172.16.0.0/16 and needed no more than 16 subnet with equal number of hosts?Correct
Incorrect
-
Question 162 of 188
162. Question
1 pointsWhich statement best describes the operation of the File Transfer Protocol?Correct
Incorrect
-
Question 163 of 188
163. Question
1 pointsA client is establishing a TCP session with a server. How is the acknowledgment number in the response segment to the client determined?Correct
Incorrect
-
Question 164 of 188
164. Question
1 pointsWhy does layer 3 device perform the ANDing process on a destination IP and subnet Mask?Correct
Incorrect
-
Question 165 of 188
165. Question
1 pointsThere was also a question about if you activated service password encryption in the past and you prompt “no service password encryption” what password are modified ?Correct
Incorrect
-
Question 166 of 188
166. Question
1 pointsWhat type of communication rule would best describe CSMA/CD?Correct
Incorrect
-
Question 167 of 188
167. Question
1 pointsWhat is the primary reason to subnet IPv6 prefixes?Correct
Incorrect
-
Question 168 of 188
168. Question
1 pointsWhich statement describes data throughput?Correct
Incorrect
-
Question 169 of 188
169. Question
1 pointsHow could a faulty network device create a source of hazard for a user? (Choose two.)Correct
Incorrect
-
Question 170 of 188
170. Question
1 pointsWhat are three important considerations when planning the structure of an IP addressing scheme? (Choose three.)Correct
Incorrect
-
Question 171 of 188
171. Question
1 pointsWhat is the metric value that is used to reach the 10.1.1.0 network in the following routing table entry? D 10.1.1.0/24 [90/2170112] via 209.165.200.226, 00:00:05, Serial0/0/0Correct
Incorrect
-
Question 172 of 188
172. Question
1 pointsWhich two services or protocols use the preferred UDP protocol for fast transmission and low overhead? (Choose two)Correct
Incorrect
-
Question 173 of 188
173. Question
1 pointsWhat action does a DHCPv4 client take if it receives more than one DHCPOFFER from multiple DHCP servers?Correct
Incorrect
-
Question 174 of 188
174. Question
1 pointsTo what legacy address class does the address 10.0.0.0 belong?Correct
Incorrect
-
Question 175 of 188
175. Question
1 pointsWhat type of communication medium is used with a wireless LAN connection?Correct
Incorrect
-
Question 176 of 188
176. Question
1 pointsWhich method of IPv6 prefix assignment relies on the prefix contained in RA messages?Correct
Incorrect
-
Question 177 of 188
177. Question
1 pointsWhat is a characteristic of DNS?Correct
Incorrect
-
Question 178 of 188
178. Question
1 pointsWhat is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?Correct
Incorrect
-
Question 179 of 188
179. Question
1 pointsWhat are two services provided by the OSI network layer? (Choose two.)Correct
Incorrect
-
Question 180 of 188
180. Question
1 pointsThree bank employees are using the corporate network. The first employee uses a web browser to view a company web page in order to read some announcements. The second employee accesses the corporate database to perform some financial transactions. The third employee participates in an important live audio conference with other corporate managers in branch offices. If QoS is implemented on this network, what will be the priorities from highest to lowest of the different data types?Correct
Incorrect
-
Question 181 of 188
181. Question
1 pointsWhich subnet would include the address 192.168.1.96 as a usable host address?Correct
Incorrect
-
Question 182 of 188
182. Question
1 pointsFill in the blank.- (TFTP) is a best-effort, connectionless application layer protocol that is used to transfer files.
Correct
Incorrect
-
Question 183 of 188
183. Question
1 pointsConsider the following range of addresses:- 2001:0DB8:BC15:00A0:0000:: 2001:0DB8:BC15:00A1:0000:: 2001:0DB8:BC15:00A2:0000:: … 2001:0DB8:BC15:00AF:0000:: The prefix-length for the range of addresses is (/60)
Correct
Incorrect
-
Question 184 of 188
184. Question
1 pointsFill in the blank.- Point-to-point communications where both devices can transmit and receive on the medium at the same time are known as (full-duplex) .
Correct
Incorrect
-
Question 185 of 188
185. Question
1 pointsFill in the blank.- During data communications, a host may need to send a single message to a specific group of destination hosts simultaneously. This message is in the form of a (Multicast) message.
Correct
Incorrect
-
Question 186 of 188
186. Question
1 pointsFill in the blank.- To prevent faulty network devices from carrying dangerous voltage levels, equipment must be (grounded) correctly
Correct
Incorrect
-
Question 187 of 188
187. Question
1 pointsFill in the blank.- Network devices come in two physical configurations. Devices that have expansion slots that provide the flexibility to add new modules have a (Modular) configuration.
Correct
Incorrect
-
Question 188 of 188
188. Question
1 pointsFill in the blank. Use a number.- IPv4 multicast addresses are directly mapped to IEEE 802 (Ethernet) MAC addresses using the last (4) of the 28 available bits in the IPv4 multicast group address.
Correct
Incorrect
