This posts consists of a list of important CCNA commands that you may need to use both in CCNA exams and in real world. When you start preparing for CCNA exam, you start developing concepts on various networking topics, but in the real world when you will work as a network engineer or in any other relevant position, you will need to know when and how to apply your CCNA knowledge. This posts aims to equip you with all the necessary commands with in-depth illustrations to make your familiarize with network configuration environment so that you know exactly which command to use in a particular situation.
This posts has included all the CCNA commands that an exam. candidate may need to solve CCNA simulation lab, and to solve switching and routing problems in real networks.
Router Modes:
- Router>: User mode = Limited to basic monitoring commands
- Router#: Privileged mode (exec-level mode) = Provides access to all other router commands
- Router(config)#: global configuration mode = Commands that affect the entire system
- Router(config-if)#: interface mode = Commands that affect interfaces
- Router(config-subif)#: subinterface mode = Commands that affect subinterfaces
- Router(config-line)#: line mode = Commands that affect in lines modes (console, vty, aux…)
- Router(config-router)#: router configuration mode
| Changing switch hostname | |
|---|---|
| Switch(config)#hostname SW1 | |
| Configuring passwords | |
| SW1(config)#enable secret cisco | MD5 hash. |
| SW1(config)#enable password notcisco | Clear text. |
| Securing console port | |
|
SW1(config)#line con 0 SW1(config-line)#password cisco SW1(config-line)#login |
|
| Securing terminal lines | |
|
SW1(config)#line vty 0 4 SW1(config-line)#password cisco SW1(config-line)#login |
|
| Encrypting passwords | |
| SW1(config)#service password-encryption | |
| Configuring banners | |
| SW1(config)#banner motd $ ================================= UNAUTHORIZED ACCESS IS PROHIBITED ================================= $ |
|
| Giving the switch an IP address | |
| SW1(config)#interface vlan 1 SW1(config-if)#ip address 172.16.1.1 255.255.255.0 (or dhcp) SW1(config-if)#no shutdown |
|
| Setting the default gateway | |
| SW1(config)#ip default-gateway 172.16.1.1 | |
| Saving configuration | |
| SW1#copy running-config startup-config Destination filename [startup-config]? Building configuration… [OK] |
Press enter to confirm file name. |
| SW1#wr Building configuration… [OK] |
Short for write memory. |
| Working environment (name lookup, history, exec-timeout and logging behavior) |
|
| SW1(config)#no ip domain-lookup SW1(config)#line vty 0 4 SW1(config-line)#history size 15 SW1(config-line)# exec-timeout 10 30 SW1(config-line)#logging synchronous |
Also valid for line con 0 |
| Configuring switch to use SSH | |
SW1(config)#ip domain-name example.com SW1(config)#username admin password cisco SW1(config)#crypto key generate rsa SW1(config)#ip ssh version 2 SW1(config)#line vty 0 4 |
The size of the key modulus in the range of 360 to 2048. You can set vty lines to use only telnet or only ssh or both as in the example. |
| Aliases | |
| SW1(config)#alias exec c configure terminal SW1(config)#alias exec s show ip interface brief SW1(config)#alias exec sr show running-config |
Used to create shortcuts for long commands. |
| Description, speed and duplex | |
| SW1(config)#interface fastEthernet 0/1 SW1(config-if)#description LINK TO INTERNET ROUTER SW1(config-if)#speed 100 (options: 10, 100, auto) SW1(config)#interface range fastEthernet 0/5 – 10 SW1(config-if-range)#duplex full (options: half, full, auto) |
The range keyword used to set a group of interfaces at once. |
| Verify Basic Configuration | |
| SW1#show version | Shows information about the switch and its interfaces, RAM, NVRAM, flash, IOS, etc. |
| SW1#show running-config | Shows the current configuration file stored in DRAM. |
| SW1#show startup-config | Shows the configuration file stored in NVRAM which is used at first boot process |
| SW1#show history | Lists the commands currently held in the history buffer. |
| SW1#show ip interface brief | Shows an overview of all interfaces, their physical status, protocol status and ip address if assigned. |
| SW1#show interface vlan 1 | Shows detailed information about the specified interface, its status, protocol, duplex, speed, encapsulation, last 5 min traffic. |
| SW1#show interfaces description | Shows the description of all interfaces |
| SW1#show interfaces status | Shows the status of all interfaces like connected or not, speed, duplex, trunk or access vlan. |
| SW1#show crypto key mypubkey rsa | Shows the public encryption key used for SSH. |
| SW1#show dhcp lease | Shows information about the leased IP address (when an interface is configured to get IP address via a dhcp server) |
| Configuring port security | |
SW1(config-if)#switchport mode access SW1(config-if)#switchport port-security SW1(config-if)#switchport port-security maximum 1 SW1(config-if)#switchport port-security violation shutdown (options: shutdown, protect, restrict) SW1(config-if)#switchport port-security mac-address 68b5.9965.1195 (options: H.H.H, sticky) |
The sticky keyword is used to let the interface dynamically learns and configures the MAC addresses of the currently connected hosts. |
| Verify and troubleshoot port security | |
| SW1#show mac-address-table | Shows the entries of the mac address table |
| SW1#show port-security | overview of port security of all interfaces |
| SW1#show port-security interface fa0/5 | Shows detailed information about port security on the specified interface |
| Configuring VLANs | |
SW1(config)#vlan 10 SW1(config-vlan)#name SALES SW1(config)#interface fastEthernet 0/5 |
|
| Configuring an auxiliary VLAN for cisco IP phones | |
| SW1(config)#interface fastEthernet 0/5 SW1(config-if)#switchport access vlan 10 SW1(config-if)#switchport voice vlan 12 |
accessing vlan 10 (data) and 12 (VoIP) |
| Configuring Trunks | |
| SW1(config)#interface fastEthernet 0/1 SW1(config-if)#switchport mode trunk (options: access, trunk, dynamic auto, dynamic desirable) SW1(config-if)#switchport trunk allowed vlan add 10 (options: add, remove, all, except) |
|
| Securing VLANS and Trunking | |
SW1(config-if)#shutdown SW1(config-if)#nonegotiate (or hardcode the port as an access port) SW1(config-if)#switchport access vlan 222 |
|
| Configuring VTP | |
SW1(config)#vtp mode server (options: server, client, transparent) SW1(config)#vtp domain EXAMPLE (case-sensitive) SW1(config)#vtp password cisco (case-sensitive) SW1(config)#vtp pruning (only works on VTP servers) SW1(config)#vtp version 2 |
The transparent VTP mode is used when an engineer wants to deactivate VTP on a particular switch |
| Verify and troubleshoot VLANS and VTP | |
| SW1#show interfaces if switchport | Lists information about administrative setting and operation status of interface |
| SW1#show interfaces trunk | Lists all the trunk ports on a switch including the trunk allowed VLANS |
| SW1#show vlan {brief id| name summary} | Lists information about the VLANs |
| SW1#show vtp status | Lists VTP configuration (mode, domain name, version, etc) and revision number |
| SW1#show vtp password | Shows the VTP password |
| STP optimization | |
SW1(config)#spanning-tree vlan 1 root primary SW1(config)#spanning-tree mode rapid-pvst (options: mst, pvst, rapid-pvst) SW1(config-if)#spanning-tree portfast SW1(config-if)#spanning-tree [vlan 1] cost 25 SW1(config-if)#channel-group 1 mode on (options: auto, desirable, on) |
Priority must be a multiply of 4096 Portfast and BPDU guard are enabled only on interfaces connected to end user hosts |
| STP verification and troubleshooting | |
| SW1#show spanning-tree | Shows detailed info about STP state |
| SW1#show spanning-tree interface fa0/2 | Shows STP info only on a specific port |
| SW1#show spanning-tree vlan 1 | Shows STP info only for a specific VLAN |
| SW1#show spanning-tree [vlanl] root | Shows info about the root switch |
| SW1#show spanning-tree [vlanl] bridge | Shows info about the local switch |
| SW1#show etherchannel 1 | Show the state of the etherchannels |
| SW1#debug spanning-tree events | Provides informational messages about the changes in the STP topology |
| Enabling or disabling CDP | |
SW1(config)#cdp run SW1(config-if)#no cdp enable |
|
| Using CDP for network verification and troubleshooting | |
| SW1#show cdp | Shows global information about CDP itself |
| SW1#show cdp interface fa0/2 | Shows information about CDP on a specific interface |
| SW1#show cdp neighbors | Shows information about the directly connected cisco devices including interfaces names capabilities |
| SW1#show cdp neighbors detail | Shows detailed information about the neighboring cisco devices including device address and version of IOS they run |
| SW1#show cdp entry * | Same as show cdp neighbor detail |
| SW1#show cdp entry SW2 | Shows detailed information about the specified entry only |
| Router Basic configuration | |
|
Router(config)#hostname R1 Rl(config)#enable secret cisco Rl(config)#line con 0 Rl(config-line)#password cisco Rl(config-line)#login Rl(config-line)»logging synchronous Rl(config-line)#exec-timeout 30 0 Rl(config-line)#exit Rl(config)#line vty 0 4 Rl(config-line)#password cisco Rl(config-line)#login Rl(config-line)»logging synchronous Rl(config-line)#exec-timeout 30 0 Rl(config-line)#exit Rl(config)#line aux 0 Rl(config-line)#password cisco Rl(config-line)#login Rl(config-line)Slogging synchronous Rl(config-line)#exec-timeout 30 0 Rl(config-line)#exit Rl(config)#banner motd $ -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- UNAUTHORIZED ACCESS IS PROHIBITED -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- $ Rl(config)#alias exec c configure terminal Rl(config)#alias exec s show ip interface brief Rl(config)#alias exec sr show running-config Rl(config)#no ip domain-lookup Rl(config)#service password-encryption Rl(config)#ip domain-name example.com Rl(config)#username admin password cisco Rl(config)#crypto key generate rsa How many bits in the modulus [512]: 1024 Rl(config)#ip ssh version 2 Rl(config)#line vty 0 4 Rl(config-line)#login local Rl(config-line)#transport input telnet ssh |
This section includes IOS commands that are absolutely identical on both routers and switches, except the part of line aux 0 which is configured only on router because switches do not have an auxiliary port. |
| Configuring router interfaces | |
| Rl(config)#interface fastEthernet 0/0
R1(config-if)#description LINK_T0_L0CAL_LAN_THR0UGH_SW1 Rl(config-if)#ip address 172.16.1.1 255.255.255.0 Rl(config-if)#no shutdown Rl(config-if)#exit Rl(config)#interface serial 0/1/0 R1(config-if)#description WAN_C0NNECTI0N_T0_R2 Rl(config-if)#ip address 10.1.1.1 255.255.255.252 Rl(config-if)#clock rate 128000 Rl(config-if)#no shutdown |
Clock rate is set only on the DCE side, typically the ISP side. On your router which is DTE you don’t need to set clocking. |
| Configuring Router-On-Stick for vlan routing | |
| Rl(config)#interface fastEthernet 0/0
Rl(config-if)#no shutdown Rl(config)# interface fastEthernet 0/0.10 Rl(config-subif)# encapsulation dotlq 10 Rl(config-subif)#ip address 192.168.10.1 255.255.255.0 Rl(config-subif)# interface fastEthernet 0/0.20 Rl(config-subif)# encapsulation dotlq 20 Rl(config-subif)#ip address 192.168.20.1 255.255.255.0 |
|
| Static routes | |
| Rl(config)#ip route 10.1.2.0 255.255.255.0 10.1.128.1 | Using next hop |
| Rl(config)#ip route 10.1.2.0 255.255.255.0 Serial 0/0 *Note: Exit interface can be used in point-to-point serial links. |
Using exit interface |
| Default Route | |
| Rl(config)#ip route 0.0.0.0 0.0.0.0 199.1.1.1 | |
| RIPv2 Configuration | |
| Rl(config)#router rip Rl(config-router)#version 2 Rl(config-router)#network 10.0.0.0 (written as an original class A) |
|
| Rl(config-router)#no autosummary | |
| Rl(config-router)#passive-interface serial 0/0 | |
| RIPv2 Verification | |
| Rl#show ip protocols | Shows information about the running routing protocol process |
| Rl#show ip route | Shows the entire routing table |
| Rl#show ip route rip</td> | Shows routes learned via RIP only |
| Rl#show ip route 10.1.1.1 | Shows detailed information about the route to the specified destination network |
| OSPF Configuration | |
Rl(config)#router ospf 10 (process ID) Rl(config-router)#network 10.0.0.0 0.255.255.255 area 0 |
|
Using router-id ospf subcommand: |
|
Rl(config-if)#ip ospf hello-interval 2 |
|
– Changing interface cost: |
|
Rl(config-router)#passive-interface serial 0/0 |
|
Type 0 authentication (none): |
|
Rl(config-router)#maximum paths 6 |
|
| OSPF verification | |
| Rl#show ip protocols | Shows information about the running routing protocol process |
| Rl#show ip route | Shows the entire routing table |
| Rl#show ip route ospf | Shows routes learned via OSPF only |
| Rl#show ip ospf neighbors | Shows all neighboring routers along with their respective adjacency state |
| Rl#show ip ospf database | Shows all the information contained in the LSDB |
| Rl#show ip ospf interfaces serial 0/0 | Shows detailed information about OSPF running on a specific interface |
| EIGRP Configuration | |
Rl(config)#router eigrp 121 (AS number) Rl(config-router)#network 10.0.0.0 |
|
Rl(config-router)#no autosummary |
|
Rl(config-router)#passive-interface serial 0/0 |
|
Rl(config-router)#maximum-paths 6 |
|
Rl(config-if)#ip hello-interval eigrp 121 3 |
|
Rl(config-if)#bandwidth 265 (kbps) |
|
| EIGRP Authentication | |
Create a key chain and give it a name: Rl(config-if)#ip authentication mode eigrp 121 md5 Rl(config-if)#ip authentication key-chain eigrp 121 MY_KEYS |
The key-string value and the mode must be the same on both routers. Lifetime options of the keys requires the clock of the routers to be set correctly, better use NTP, or it can cause problems |
| EIGRP Verification | |
| Rl#show ip route eigrp | Shows routes learned via EIGRP only |
| Rl#show ip eigrp neighbors | Shows EIGRP neighbors and status |
| Rl#show ip eigrp topology | Shows EIGRP topology table, including successor and feasible successor |
| Rl#show ip eigrp interfaces | Shows interfaces that run EIGRP |
| Rl#show ip eigrp traffic | Lists statistics on numbers of EIGRP messages sent and received by the router |
| Access Control Lists (ACLs) | |
| Standard ACL | |
– Standard ACL should be placed as close as possible to the destination of the packet. Rl(config)#access-list 1 remark ACL TO DENY ACCESS FROM SALES VLAN – ACL uses first-match logic. Rl(config-if)#ip access-group 2 out |
Standard ACL number ranges: 1-99 and 1300 – 1999. |
Create the ACL that defines the permitted telnet clients: | |
| Extended ACL | |
– Extended ACL should be placed as close as possible to the source of the packet. |
Extended ACL number ranges: 100 – 199 and 2000 – 2699. |
| Named ACL | |
– Named ACLs use names to identify ACLs rather than numbers, and commands that permit or deny traffic are written in a sub mode called named ACL mode (nacl). Rl(config)#ip access-list standard MY_STANDARD_ACL |
|
Rl(config)#ip access-list extended MY_EXTENDED_ACL Rl(config)#ip access-list extended MY_EXTENDED_ACL |
You can edit numbered ACLs using the configuration style of the named ACLs in as shown in the last example. |
| Verifying ACLs | |
| Rl#show access-lists | Shows all ACLs configured on a router with counters at the end of each statement |
| Rl#show ip access-list | Same as the previous command |
| Rl#show ip access-list 101 | Shows only the specified ACL |
| Rl#show ip interface f0/0 | Includes a reference to the on that interface either in ACLs enabled or out. |
| DHCP Server | |
Rl(config)#ip dhcp pool MY_POOL R1(dhcp-config)»network 192.168.1.0 255.255.255.0 R1(dhcp-config)»default-router 192.168.1.1 R1(dhcp-config)»dns-server 213.131.65.20 8.8.8.8 Rl(dhcp-config)lease 2 (days) Rl(config)#ip dhcp excluded-address 192.168.1.1 192.168.1.100 |
|
| DHCP Verification and Troubleshooting | |
| Rl»show ip dhcp pool POOL_1 | shows the status of the specified pool and the leased addresses from that pool |
| Rl»show ip dhcp binding | Shows all the leased ip addresses from all configured DHCP pools |
| Rl»show ip dhcp conflict | Shows any conflicts that occurred |
| PPP Configuration | |
| Rl(config)#interface serial 0/0 Rl(config-if)#encapsulation ppp |
|
| PPP Authentication | |
| CHAP | |
Rl(config)#hostname ALPHA ALPHA(config)#username BETA password XYZ ALPHA(config)#interface serial 0/0 ALPHA(config-if)#ppp authentication chap |
The password used is shared password, that means it must be the same on both routers |
| PAP | |
Rl(config)#hostname ALPHA ALPHA(config)#username BETA password XYZ ALPHA(config)#interface serial 0/0 |
|
| PPP Verification and troubleshoot | |
| R1#show interface s0/0 | Shows the encapsulation type and the control protocols of PPP |
| R1#show run | Useful for viewing the configuration of usernames and passwords used to authenticate ppp |
| R1#debug ppp authentication | Displays the authentication process of ppp in real time |
| Frame Relay | |
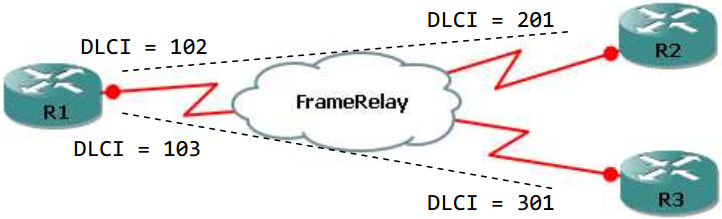
|
|
| Multipoint (one subnet) | |
Rl(config)#interface serial 0/0 Rl(config-if)#frame-relay lmi-type ansi Rl(config-if)#frame-relay map ip 1.1.1.2 102 broadcast (ietf) |
|
| R2(config)#interface serial 0/0 R2(config-if)#ip address 1.1.1.2 255.255.255.0 R2(config-if)#encapsulation frame-relay R2(config-if )#frame-relay map ip 1.1.1.1 201 broadcast R2(config-if)#frame-relay map ip 1.1.1.3 201 broadcast |
|
| R3(config)#interface serial 0/0 R3(config-if)#ip address 1.1.1.3 255.255.255.0 R3(config-if)#encapsulation frame-relay R3(config-if)#frame-relay map ip 1.1.1.1 301 broadcast R3(config-if)#frame-relay map ip 1.1.1.2 301 broadcast |
|
| Point-to-point (different subnets; one subnet per subinterface) | |
Rl(config)#interface serial 0/0 Rl(config-if)#encapsulation frame-relay Rl(config)#interface serial 0/0.102 point-to-point |
|
| R2(config)#interface serial 0/0 R2(config-if)#encapsulation frame-relay R2(config)#interface serial 0/0.201 point-to-point R2(config-subif)#ip address 1.1.1.2 255.255.255.0 R2(config-subif)#frame-relay interface-dlci 201 |
|
| R3(config)#interface serial 0/0 R3(config-if)#encapsulation frame-relay R3(config)#interface serial 0/0.301 point-to-point R3(config-subif)#ip address 2.2.2.2 255.255.255.0 R3(config-subif)#frame-relay interface-dlci 301 |
|
| Frame Relay Verification and troubleshoot | |
| Rl#show interfaces serial 0/0 | Shows the encapsulation type |
| Rl#show frame-relay PVC | Lists PVC status information |
| Rl#show frame-relay map | Lists DLCI to IP mapping |
| Rl#show frame-relay lmi | Lists LMI status information |
| Rl#debug frame-relay lmi | Displays the content of LMI messages |
| Rl#debug frame-relay events | Lists messages about certain Frame Relay events, including Inverse ARP messaeges |
| Network Address Translation (NAT) | |
| Static NAT | |
Rl(config)#interface serial 0/0 Rl(config-if)#ip nat outside Rl(config)#interface FastEthernet 1/1 Rl(config-if)#ip nat inside Rl(config)#ip nat inside source static 192.168.1.10 200.1.1.1 |
|
| Dynamic NAT | |
Rl(config)#access-list 3 permit 192.168.1.0 0.0.0.255 Rl(config)#ip nat pool PUB 200.1.1.1 200.1.1.6 netmask 255.255.255.248 Rl(config)#ip nat inside source list 3 pool PUB |
|
| NAT Overload (PAT) | |
Rl(config)#ip nat inside source list 3 pool PUB overload |
|
| NAT verification and troubleshoot | |
| Rl#show run | Useful in viewing the configuration of NAT pool and the inside and outside interfaces |
| Rl#show access-lists | Displays access lists, including the one used for NAT |
| Rl#show ip nat stasitics | Shows counters for packets and NAT table entries, as well as basic configuration information |
| Rl#show ip nat translations | Displays the NAT table |
| Rl#clear ip nat translations * | Clears all the dynamic entries in the NAT table |
| Rl#debug ip nat | Issues a log message describing each packet whose ip address is translated with NAT |

Excellent work – very useful
BSDK content to acha dala wa hai to pdf download link bhi khol daita
missing PDF Download funktion :(
This is great, you have contributed to people’s up coming success in the field of networking, thank you so much.
Great material!!
With this…
Giving the switch an IP address
SW1(config)#interface vlan 1
SW1(config-if)#ip address 172.16.1.1 1 255.255.255.0 (or dhcp)
SW1(config-if)#shutdown
… the last commend should be “no shutdown”
also, the “ip address” command has an extra “1” between the address and the mask, which shouldn’t be there.
Fixed, thanks rob!
very nice
Very Good material you attached.
Not only for students even for engineers who are working in that field.
thAnkx dude
WHERE IS THE OPTION TO DOWNLOAD THIS IN A PDF?
KINDLY INCLUDE BGP COMMONDS ALSO