16. Refer to the exhibit. When considering the route map configuration for BGP, what is the result when inbound traffic is received with a source IP that matches ACL1?
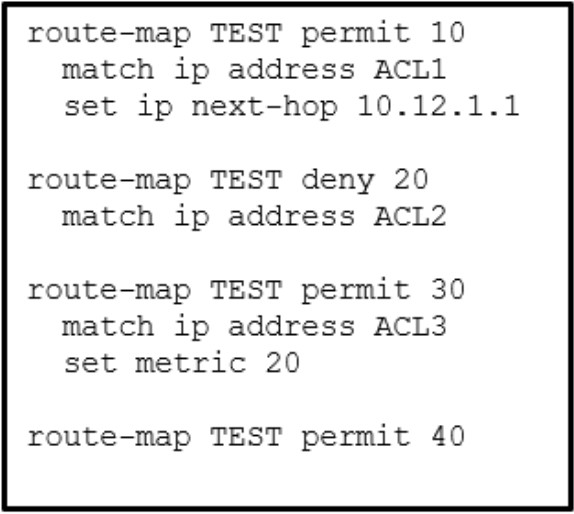
- The incoming network traffic will go through the whole route map.
- The optional action is processed, and the route map completes.
- If the incoming network traffic does not match ACL2 and ACL3, it will be dropped.
- The optional action is processed, and route map continues to test with ACL2.
Explanation: A route map uses the command syntax route-map route-map-name [permit | deny][*sequence-number*]. The rules that apply to route map statements are as follows:
- If a processing action is not provided, the default value permit is used.
- If a sequence number is not provided, the sequence number is incremented by 10 automatically.
- If a matching statement is not included, an implied all prefixes is associated with the statement.
- Processing within a route map stops after all optional actions have processed and after matching a conditional matching criterion.
17. A company is deploying BGP multihoming to provide network connection redundancy for several branch sites. Which method can be used to avoid the branch transit routing situation?
- ensuring that no IGP session is running on branch site BGP routers
- designating a data center or a specific location to handle the transit traffic
- applying inbound BGP route policies so that only data packets from other branch sites can enter local networks
- applying outbound BGP route policies so that branch sites do not advertise routes learned from the WAN connection
Explanation: Multihomed environments should be configured so that branch routers cannot act as transit routers. In most designs, transit routing of traffic from another branch is undesirable, because WAN bandwidth may not be sized accordingly. Transit routing can be avoided by configuring outbound route filtering at each branch site so that the branch sites do not advertise what they learn from the WAN but advertise only networks that face the LAN.
18. A BGP routing policy has been created using route maps. The command route-map TEST permit 10 is part of the configuration. What does the argument 10 indicate?
- It identifies the access list number to be used by the route map statement.
- It identifies the position of the route map in relation to other instances.
- It indicates the local preference to be set for routes that match the route map.
- It indicates the metric to be set for routes that match the route map.
- It specifies the route map to be used on autonomous system 10.
Explanation: A route map uses the command syntax route-map route-map-name [permit | deny][*sequence-number*]. It has four components:
- Sequence number – dictates the processing order of the route map
- Conditional matching criteria – identifies prefix characteristics (network, BGP path attribute, next hop, and so on) for a specific sequence
- Processing action – permits or denies the prefix
- Optional action – allows for manipulations, depending on how the route map is referenced on the router
19. A network administrator is configuring an ACL to match networks for BGP route filtering. The administrator creates an ACE permit ip 10.0.128.0 0.0.63.0 255.255.255.0 0.0.0.0. Which network matches the ACE?
- 10.0.63.0/24
- 10.0.130.0/24
- 10.0.192.0/24
- 10.0.128.0/25
Explanation: One method for conditional matching of routes in BGP is through extended ACLs. When using extended ACLs for this purpose, the source fields match against the network portion of the route, and the destination fields match against the network mask. The matching networks are 10.0.128.0/24 through 10.0.191.0/24.
20. A network administrator is configuring a prefix list to match networks for BGP route filtering. Which network matches the prefix match specification 10.160.0.0/14 ge 22?
- 10.158.0.0/22
- 10.162.0.0/14
- 10.163.0.0/24
- 10.128.0.0/28
Explanation: Prefix lists provide another method of identifying networks in a routing protocol. A prefix list identifies a specific IP address, network, or network range and allows for the selection of multiple networks with a variety of prefix lengths by using a prefix match specification. A prefix match specification contains two parts: a high-order bit pattern and a high-order bit count, which determines the high-order bits in the bit pattern that are to be matched. The high-order bit pattern is also known as the network address and the high-order bit count as the mask length. The network portion of the matching networks is 10.160.0.0 and higher. The mask length of the matching networks must be greater than or equal to /22.
21. Refer to the exhibit. A network administrator is troubleshooting BGP configuration and wants to verify routes that carry the 100 AS in the AS_Path value. Which regular expression should the administrator use in the command show bgp ipv4 unicast regex regex-pattern?
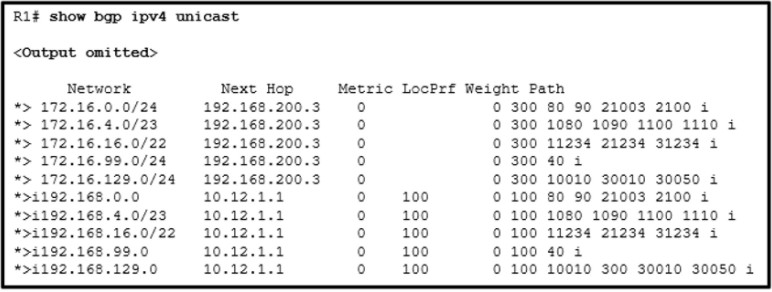
- show bgp ipv4 unicast regex .100.
- show bgp ipv4 unicast regex $100
- show bgp ipv4 unicast regex 100_
- show bgp ipv4 unicast regex ^100^
Explanation: In troubleshooting BGP, regular expressions (regex) can be used to parse through the large number of available ASNs. Regular expressions are based on query modifiers used to select the appropriate content. The regex pattern 100_ indicates to only include the lines that contain the exact phrase of 100. Some regex query modifiers are as follows:
- (underscore) – Matches a space
- ^ (caret) – Indicates the start of a string
- $ (dollar sign) – Indicates the end of a string
- . (period) – Matches a single character, including a space
22. What is the first attribute to be used in determining the best path when a BGP router has multiple paths for the same network prefix length?
- weight
- lowest MED
- local originated
- local preference
Explanation: The BGP best-path algorithm uses the attributes, in the following order, for the best-path selection:
- Weight.
- Local preference.
- Local originated (network statement, redistribution, or aggregation).
- AIGP.
- Shortest AS_Path.
- Origin type.
- Lowest MED.
- EBGP over IBGP.
- Lowest IGP next hop.
- If both paths are external (EBGP), prefer the first (oldest).
- Prefer the route that comes from the BGP peer with the lower RID.
- Prefer the route with the minimum cluster list length.
- Prefer the path that comes from the lowest neighbor address.
23. Refer to the exhibit. A network administrator is configuring BGP route filtering on R1. The router ID for R1 is configured with lookback address 192.168.1.1. Which three routes are allowed from the BGP neighbor router 10.12.1.2 to inject into the BGP table of R1? (Choose three.)
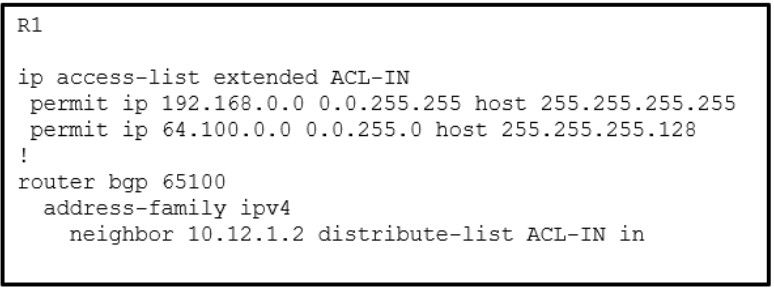
- 192.168.1.1/32
- 192.168.2.2/32
- 192.168.3.3/32
- 10.12.1.0/24
- 64.100.3.0/25
- 64.100.2.192/26
Explanation: Per the distribute list filtering ACL-IN, two loopback networks (192.168.2.2/32 and 192.168.3.3/32) are allowed because they match the first ACE in the ACL-IN. The network 64.100.3.0/25 is allowed because it matches the second ACE in the ACL-IN. The networks 192.168.1.1/32 and 10.12.1.0/24 are local routes. The network 64.100.2.192/26 would not be allowed because it does not match entries in the ACL-IN.
24. A network administrator is configuring a prefix list with the ip prefix-list command. How does the IOS process the prefix list if the administrator does not specify a sequence number?
- It will present a prompt to ask the administrator to enter one.
- It will present an error message that indicates the entry fails.
- It automatically increments by 5 based on the highest sequence number.
- It automatically increments by 10 based on the highest sequence number.
Explanation: Prefix lists are configured with the global configuration command ip prefix-list prefix-listname [seq sequence-number] {permit | deny} high-order-bit-pattern/high-order-bit-count [ge ge-value][**le** *le-value*]. If a sequence is not provided, the sequence number automatically increments by 5 based on the highest sequence number.
1. IGMP snooping examines traffic at which OSI layer(s)?
- Layer 2
- Layer 3
- Layer 2 and Layer 3
- Layer 2, Layer 3, and Layer 4
Explanation: IGMP snooping examines traffic at layer two for unicast traffic and layer three for multicast traffic.
2. An IPv6 enabled device sends a data packet with the destination address of FF02::1. What is the target of this packet?
- all IPv6 DHCP servers
- all IPv6 enabled nodes on the local link
- all IPv6 configured routers on the local link
- all IPv6 configured routers across the network
Explanation: FF02::1 is the all-nodes multicast group within the scope of the local link. A packet with this destination address is received and processed by all IPv6-enabled interfaces.
3. What is the hexadecimal representation of the first 24 bits of any multicast MAC address?
- 01:00:5E
- 00:E1:12
- 01:5E:01
- 00:1E:12
Explanation: The first 24 bits of a multicast MAC address are always 01:00:5E.
4. What is the IP address for the Cisco-RP-discovery multicast group?
- 224.0.0.1
- 224.0.1.39
- 224.0.1.40
- 224.1.1.1
Explanation: The multicast address 224.0.1.40 is the address used by RP MAs to advertise the RP mappings to another well-known multicast group.
5. Which IP address does the BSR mechanism use to send all BSR messages?
- 224.0.0.10
- 224.0.0.14
- 224.0.0.15
- 224.0.0.13
Explanation: BSR messages are sent by the bootstrap router mechanism using the IP address 224.0.0.13 with a TTL factor of one.
6. What is the default maximum response time for a general membership query message sent to the all-host group address 224.0.0.1 in an attached subnet?
- 5 seconds
- 8 seconds
- 10 seconds
- 12 seconds
Explanation: The general query message has a default max response time field that is set to 10 seconds. However, this can be set using a nondefault value.
7. Which version of IGMP supports Source Specific Multicast (SSM)?
Explanation: The PIM extension Source Specific Multicast (SSM) is supported only by IGMPv3.
8. What message type would a receiver in a multicast environment send in order to receive a specific multicast feed?
- IGMP include
- IGMP exclude
- IGMP join
- IGMP Version 2 specific query
Explanation: The Internet Group Management Protocol (IGMP) is a protocol used by receivers to join multicast groups. This is done by using the IGMP join membership report.
9. What is a benefit of shared trees over source trees when comparing multicast distribution trees?
- Shared trees receive traffic from all sources that send traffic to the multicast group.
- They require fewer multicast entries.
- They can allow multiple sources in an IP multicast group.
- They can be pruned.
Explanation: Shared trees receive traffic from all sources sending traffic to the same multicast group. This generates a lot of unnecessary traffic. However, because they use Rendezvous Points, shared trees require fewer multicast entries.
10. Which two statements describe IGMP? (Choose two.)
- IGMPv2 supports multicast source filtering.
- IGMPv3 provides support for SSM.
- Multicast flooding on a LAN segment can be mitigated by using IGMP snooping.
- An IGMPv2 router will only allow IGMPv2 hosts to execute a join request.
- IGMPv1 only supports queries sent to a predefined group.
Explanation: IGMPv3 is used to provide source filtering for Source Specific Multicast (SSM). IGMP snooping can be used to mitigate multicast flooding and optimize the forwarding of multicast traffic to interested receivers.
11. Which two statements about Protocol Independent Multicast (PIM) are true? (Choose two.)
- PIM does not require an IGP protocol to be configured in the network.
- PIM should be configured only on the first and the last hop routers in the multicast tree.
- PIM should be configured on the device that hosts the source of the muticast traffic.
- PIM sparse mode is most useful when there are few senders, many receivers, and the volume of multicast traffic is high.
- PIM is a multicast routing protocol that makes packet-forwarding decisions independent of the unicast IP routing protocol that is running in the network.
- Three of the forwarding modes for PIM are PIM dense mode (PIM-DM), PIM sparse mode (PIMSM), and PIM sparse-dense mode.
Explanation: PIM is a multicast routing protocol that routes multicast traffic between network segments by creating distribution trees. It makes packet-forwarding decisions independent of the unicast IP routing protocol that is running in the network. There are five operating PIM modes: PIM dense mode (PIM-DM) PIM sparse mode (PIM-SM) PIM sparse dense Mode PIM source specific multicast (PIM-SSM) PIM bidirectional mode (Bidir-PIM)
12. For configuring IP multicast routing, what is the purpose of the global configuration mode command ip pim send-rp-announce 10.1.1.1?
- enables IP multicast routing with router ID 10.1.1.1
- assigns the role of rendezvous point mapping agent to the router with IP address 10.1.1.1
- announces the candidacy of the router with IP address 10.1.1.1 as the rendezvous point for all multicast groups
- enables protocol independent multicast (PIM) with router ID 10.1.1.1
Explanation: The command ip pim send-rp-announce 10.1.1.1 is used in Auto-RP to announce the candidacy of the router with IP address 10.1.1.1 as the rendezvous point for all multicast groups. This command is used in the global configuration mode.
“Do I Know This Already?” Quiz Answers:
1. Which of the following transmission methods is multicast known for?
- One-to-one
- One-to-all
- One-for-all
- All-for-one
- One-to-many
Explanation: Multicast uses the one-to-many transmission method, where one server sends multicast traffic to a group of receivers.
2. Which protocols are essential to multicast operation? (Choose two.)
- Open Shortest Path First (OSPF)
- Protocol Independent Multicast (PIM)
- Internet Group Management Protocol (IGMP)
- Auto-RP and BSR
Explanation: Multicast relies on Internet Group Management Protocol (IGMP) for its operation in Layer 2 networks and Protocol Independent Multicast (PIM) for its operation in Layer 3 networks. It is routing protocol independent and can work with static RPs.
3. Which of the following multicast address ranges match the administratively scoped block? (Choose two.)
- 239.0.0.0 to 239.255.255.255
- 232.0.0.0 to 232.255.255.255
- 224.0.0.0 to 224.0.0.255
- 239.0.0.0/8
- 224.0.1.0/24
Explanation: 239.0.0.0/8 (239.0.0.0 to 239.255.255.255) is the IANA IP multicast address range assigned to the administratively scoped block.
4. The first 24 bits of a multicast MAC address always start with ______.
- 01:5E:00
- 01:00:53
- 01:00:5E
- 01:05:E0
- none of the above
Explanation: The first 24 bits of a multicast MAC address always start with 01:00:5E. The low-order bit of the first byte is the individual/group bit (I/G) bit, also known as the unicast/multicast bit, and when it is set to 1, it indicates that the frame is a multicast frame and the 25th bit is always 0.
5. What does a host need to do to start receiving multicast traffic?
- Send an IGMP join
- Send an unsolicited membership report
- Send an unsolicited membership query
- Send an unsolicited group specific query
Explanation: An IGMP membership report is a message type that receivers use to join a multicast group or to respond to a local router’s membership query message.
6. What is the main difference between IGMPv2 and IGMPv3?
- IGMPv3’s max response time is 10 seconds by default.
- IGMPv3 sends periodic IGMP membership queries.
- IGMPv3 introduced a new IGMP membership report with source filtering support.
- IGMPv3 can only work with SSM, while IGMPv2 can only work with PIM-SM/DM.
Explanation: IGMPv3 supports all IGMPv2’s IGMP message types and is backward compatible with it. The differences between the two are that IGMPv3 added new fields to the IGMP membership query and introduced a new IGMP message type called a Version 3 membership report to support source filtering.
7. True or false: IGMPv3 was designed to work exclusively with SSM and is not backward compatible with PIM-SM.
Explanation: IGMPv3 is backward compatible with IGMPv2. To receive traffic from all sources, which is the behavior of IGMPv2, a receiver uses exclude mode membership with an empty exclude list.
8. How can you avoid flooding of multicast frames in a Layer 2 network?
- Disable unknown multicast flooding
- Enable multicast storm control
- Enable IGMP snooping
- Enable control plane policing
Explanation: IGMP snooping, defined in RFC 4541, examines IGMP joins sent by receivers and maintains a table of interfaces to IGMP joins. When a switch receives a multicast frame destined for a multicast group, it forwards the packet only out the ports where IGMP joins were received for that specific multicast group. This prevents multicast traffic from flooding in a Layer 2 network.
9. Which of the following best describe SPT and RPT? (Choose two.)
- RPT is a source tree where the rendezvous point is the root of the tree.
- SPT is a source tree where the source is the root of the tree.
- RPT is a shared tree where the rendezvous point is the root of the tree.
- SPT is a shared tree where the source is the root of the tree.
Explanation: A source tree is a multicast distribution tree where the source is the root of the tree, and branches form a distribution tree through the network all the way down to the receivers. When this tree is built, it uses the shortest path through the network from the source to the leaves of the tree; for this reason, it is also referred to as a shortest path tree. A shared tree is a multicast distribution tree where the root of the shared tree is not the source but a router designated as the rendezvous point (RP). For this reason, shared trees are also referred to as RP trees (RPTs).
10. What does an LHR do after it receives an IGMP join from a receiver?
- It sends a PIM register message toward the RP.
- It sends a PIM join toward the RP.
- It sends a PIM register message toward the source.
- It sends a PIM join message toward the source.
Explanation: The last-hop router (LHR) is a router that is directly attached to the receivers. It is responsible for sending PIM joins upstream toward the RP or to the source after an SPT switchover.
11. What does an FHR do when an attached source becomes active and there are no interested receivers?
- It unicasts register messages to the RP and stops after a register stop from the RP.
- It unicasts encapsulated register messages to the RP and stops after a register stop from the RP.
- It waits for the RP to send register message indicating that there are interested receivers.
- It multicasts encapsulated register messages to the RP and stops after a register stop from the RP.
- It unicasts encapsulated register messages to the RP until there are interested receivers.
Explanation: When there is an active source attached to the FHR, the FHR encapsulates the multicast data from the source in a special PIM-SM message called the register message and unicasts that data to the RP by using a unidirectional PIM tunnel. When the RP receives the register message, it decapsulates the multicast data packet inside the register message, and if there is no active shared tree because there are no interested receivers, the RP sends a register stop message to the FHR, instructing it to stop sending the register messages.
12. Which of the following is a group-to-RP mapping mechanism developed by Cisco?
- BSR
- Static RP
- Auto-RP
- Phantom RP
- Anycast-RP
Explanation: Auto-RP is a Cisco proprietary mechanism that automates the distribution of group-to-RP mappings in a PIM network.
13. True or false: When PIM is configured in dense mode, it is mandatory to choose one or more routers to operate as rendezvous points (RPs)
Explanation: PIM-DM does not use RPs. When PIM is configured in sparse mode, it is mandatory to choose one or more routers to operate as rendezvous points (RPs).



