How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
Networking Basics – My Knowledge Check (Answers)
1. Which two application layer protocols manage the exchange of messages between a client with a web browser and a remote web server? (Choose two.)
Explanation: Hypertext Transfer Protocol (HTTP) and HTTP Secure (HTTPS) are two application layer protocols that manage the content requests from clients and the responses from the web server. HTML (Hypertext Mark-up Language) is the encoding language that describes the content and display features of a web page. DNS is for domain name to IP address resolution. DHCP manages and provides dynamic IP configurations to clients.
2. What is the default SSID Broadcast setting on a wireless router?
- Enabled
- Disabled
- Auto
- Off
Explanation: When a wireless router is being set up, the default setting for the SSID Broadcast is enabled. This means the wireless router will broadcast the SSID to all devices. This can be a security concern and best practice is to disable the broadcast setting.
3. A user is unable to access the company server from a computer. On issuing the ipconfig command, the user finds that the IP address of the computer is displayed as 169.254.0.2. What type of address is this?
- private
- link-local
- loopback
- experimental
Explanation: IPv4 addresses in the address block 169.254.0.0 to 169.254.255.255 are link-local addresses. The operating system of a host can automatically assign an address from this block to the host in case no IP configuration is available. An example is when a host is configured to obtain a dynamic IP address but cannot reach any DHCP server during the boot process. In such a case, the operating system can assign a link-local address.
4. Which items are collectively referred to as network media?
- routers and switches
- wires and radio waves
- firewalls and servers
- PCs and laptops
Explanation: Network media is a term used to describe the actual physical layer transport along the path over which an electrical signal travels as it moves from one component to another.
5. Match the protocol function to the description while taking into consideration that a network client is visiting a web site.
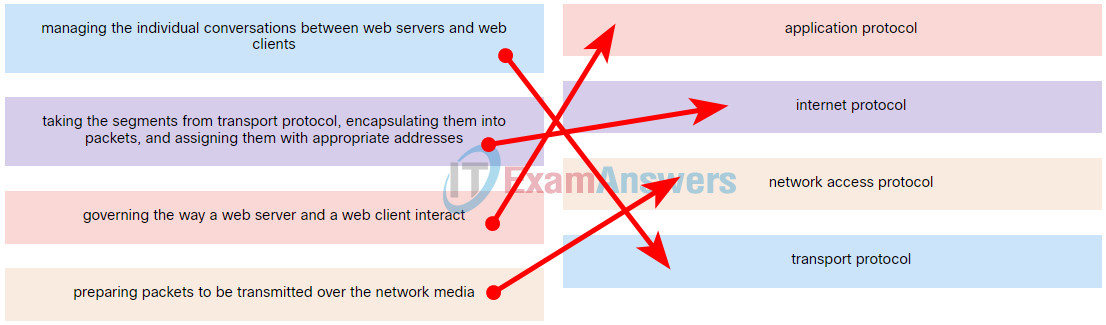
Explanation: When a web client visits a web server, several network communication protocols are involved. These different protocols work together to ensure that the messages are received and understood by both parties. These protocols include the following:
Application Protocol – governing the way a web server and a web client interact
Transport Protocol – managing the individual conversations between web servers and web clients
Internet Protocol – taking the formatted segments from the transport protocol, encapsulating them into packets, assigning them the appropriate addresses, and delivering them across the best path to the destination host
Network Access Protocol – preparing packets to be transmitted over the network media
Network Time Protocol is used to synchronize clocks between computer systems. It is not involved in this case.
6. Which wireless technology uses a device-pairing process to communicate and operates over short distances of 100 meters?
- wireless wide-area network
- Wi-Fi
- Bluetooth
- GPS
Explanation: Wireless networks can be broadly classified as follows:
- Wireless wide-area network (WWAN) – It operates in the range of miles.
- Wi-Fi – It operates up to distances of 0.18 miles and provides network access to home and corporate users and can include data, voice and video traffic.
- Bluetooth – It uses a device-pairing process to communicate over distances of up to 0.05 miles.
- GPS – It uses satellites to transmit signals that cover the globe.
7. Which two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)
- It eliminates most address configuration errors.
- It ensures that addresses are only applied to devices that require a permanent address.
- It guarantees that every device that needs an address will get one.
- It provides an address only to devices that are authorized to be connected to the network.
- It reduces the burden on network support staff.
Explanation: DHCP is generally the preferred method of assigning IP addresses to hosts on large networks because it reduces the burden on network support staff and virtually eliminates entry errors. However, DHCP itself does not discriminate between authorized and unauthorized devices and will assign configuration parameters to all requesting devices. DHCP servers are usually configured to assign addresses from a subnet range, so there is no guarantee that every device that needs an address will get one.
8. A computer has to send a packet to a destination host in the same LAN. How will the packet be sent?
- The packet will be sent to the default gateway first, and then, depending on the response from the gateway, it may be sent to the destination host.
- The packet will be sent directly to the destination host.
- The packet will first be sent to the default gateway, and then from the default gateway it will be sent directly to the destination host.
- The packet will be sent only to the default gateway.
Explanation: If the destination host is in the same LAN as the source host, there is no need for a default gateway. A default gateway is needed if a packet needs to be sent outside the LAN.
9. Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?

- The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
Explanation: The MAC address of PC3 is not present in the MAC table of the switch. Because the switch does not know where to send the frame that is addressed to PC3, it will forward the frame to all the switch ports, except for port 4, which is the incoming port.
10. What action does the ARP process take when a host needs to build a frame, but the ARP cache does not contain an address mapping?
- The ARP process sends out an ARP request to the IPv4 broadcast address to discover the MAC address of the destination device.
- The ARP process sends out an ARP request to the IPv4 broadcast address to discover the IPv4 address of the destination device.
- The ARP process sends out an ARP request to the Ethernet broadcast address to discover the IPv4 address of the destination device.
- The ARP process sends out an ARP request to the Ethernet broadcast address to discover the MAC address of the destination device.
Explanation: The address resolution protocol (ARP) maintains a cache of MAC to IPv4 address mappings on the local computer. If there is no mapping in the cache for a specific IPv4 address, then the ARP process sends an Ethernet broadcast on the local link in an attempt to resolve the destination IPv4 address to a MAC address.
11. When analog voice signals are converted for use on a computer network, in what format are they encapsulated?
- IP packets
- segments
- frames
- bits
Explanation: When Voice over iP (VoIP) is being used, analog voice signals are translated into digital data in the form of IP packets. This translation allows the phone call to be carried through a computer network.
12. What is a characteristic of a peer-to-peer application?
- Each device using the application provides a user interface and runs a background service.
- Each device can act both as a client and a server, but not simultaneously.
- The resources required for the application are centralized.
- One device is designated a server and one device is designated a client for all communications and services.
Explanation: Peer-to-peer networks exist directly between client devices, with no centralized resources or authentication. Hybrid peer-to-peer systems also exist that decentralize resource sharing but can use centralized indexes to point to the resource locations.
13. What are two features of IPv4 addresses? (Choose two.)
- An IPv4 address contains 8 octets.
- IPv4 is a logical addressing scheme.
- An IPv4 addressing scheme is hierarchical.
- IPv4 addresses are only used for communications on the internet.
- An IPv4 address is bound to a network interface card to make it unique.
Explanation: IPv4 addresses are 32-bit (4 octets) long. IPv4 addresses are logical addresses and are assigned to host network interfaces as needed. IPv4 addressing is hierarchical and each IPv4 address is made up of two parts, the network number (or network address) and the host number. IPv4 addresses are used both on local networks and on the internet.
14. Refer to the exhibit. Workstation A sends an IP packet to workstation B. Which two statements describe the encapsulation of the packet as it passes through the network? (Choose two.)
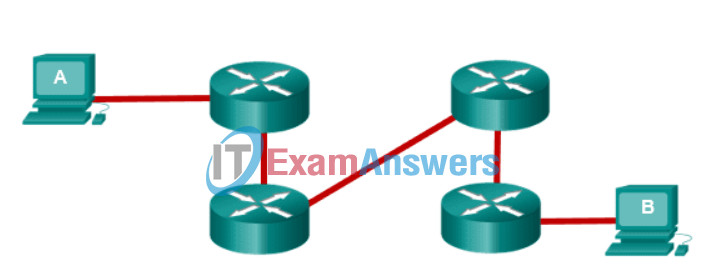
- The destination Layer 2 address of the frame does not change as it is forwarded.
- The Layer 3 header is stripped from the packet when it is received at each router.
- The Layer 2 header of the frame is reassembled when it is forwarded by each router.
- The Layer 2 header is stripped from the frame when it is received by each router.
- The source Layer 3 address is changed when it is received at each router.
Explanation: When a router receives a frame on an interface, it strips the Layer 2 frame header information from the frame. It checks the routing table to determine which interface to use to send the packet to its destination. Once the interface is known, the packet is encapsulated with a new frame header containing different source and destination MAC addresses.
15. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question or complete the task.
PT Activity: https://itexamanswers.net/download/pc-a-requesting-from-the-web-server
Capture traffic in simulation mode. What application layer service is PC-A requesting from the web server?
Explanation: When a client is initiating a request to open an FTP session, it does so by sending a packet to the FTP server with the destination port 21.
16. Which network design has the fewest broadcast domains?
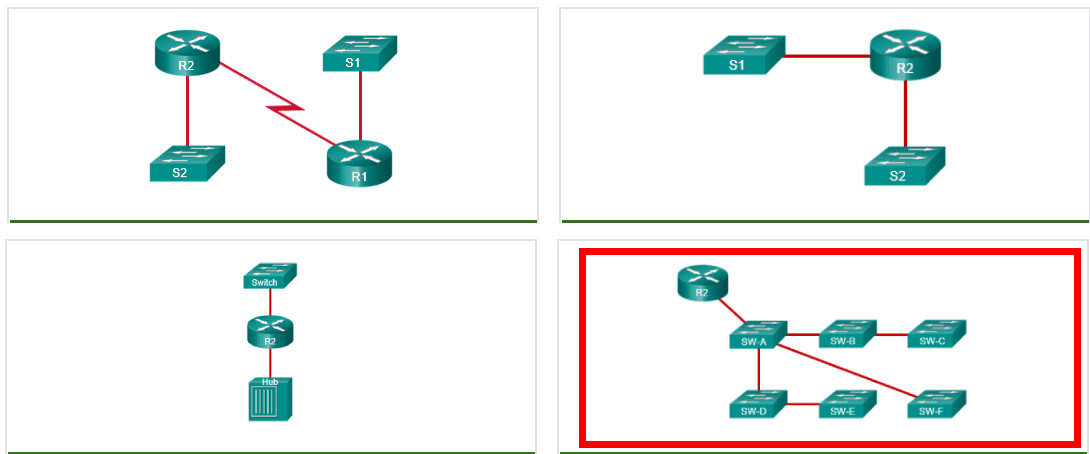
Explanation: Routers break networks into separate broadcast domains. Each LAN is a broadcast domain. The correct answer has only one broadcast domain. All other answers have two broadcast domains.
17. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
When PC0 pings the web server, which MAC address is the source MAC address in the frame from R2 to the web server?
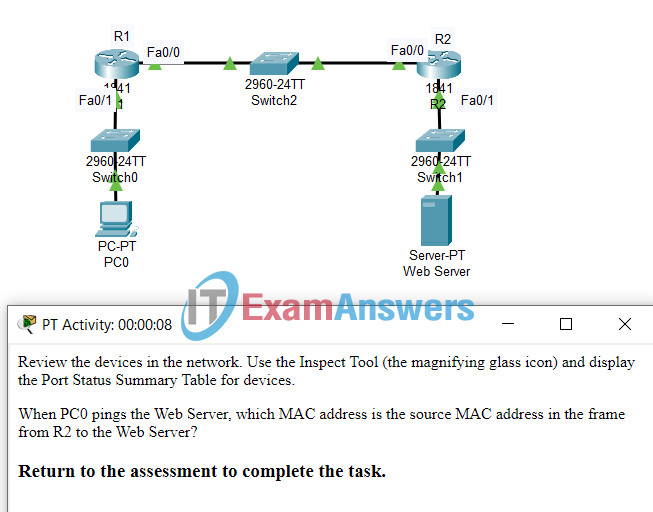
- 0001.43EA.3E03
- 0001.9756.6278
- 0001.C972.4201
- 0001.C972.4202
- 0002.16D6.A601
Explanation: In the segment between R2 and the web server, when R2 encapsulates a frame to be sent to the web server, R2 uses the MAC address of its interface that is directly connected to the segment, Fa0/1, as the source MAC.
18. What are two reasons to install routers to segment a network? (Choose two.)
- to limit the number of devices that can connect to the network
- to expand the network to a different geographic location
- to create smaller broadcast domains within the network
- to reduce the number of switches needed to connect devices
Explanation: There are a number of reasons to use routers to divide a network into smaller segments. Expanding the network into a different geographic location may require the use of routers at both locations. Another reason is to limit broadcasts that must be processed by all devices on the network segment. Routers do not forward broadcast traffic off the local network segment.
19. How are port numbers used in the TCP/IP encapsulation process?
- Source port numbers and destination port numbers are not necessary when UDP is the transport layer protocol being used for the communication.
- Source port and destination port numbers are randomly generated.
- If multiple conversations occur that are using the same service, the source port number is used to track the separate conversations.
- Destination port numbers are assigned automatically and cannot be changed.
Explanation: Both UDP and TCP use port numbers to provide a unique identifier for each conversation. Source port numbers are randomly generated and are used to track different conversations. Destination port numbers identify specific services by using either a default port number for the service or a port number that is assigned manually by a system administrator.
20. Which message does an IPv4 host use to reply when it receives a DHCPOFFER message from a DHCP server?
- DHCPOFFER
- DHCPDISCOVER
- DHCPREQUEST
- DHCPACK
Explanation: When the client receives the DHCPOFFER from the server, it sends back a DHCPREQUEST broadcast message. On receiving the DHCPREQUEST message, the server replies with a unicast DHCPACK message.
21. Which term refers to the set of rules that define how a network operates?
- standard
- protocol
- model
- domain
Explanation: Standards ensure that different devices connecting to the network are able to communicate with each other. In networking there are many standards that define how the network should operate and that all components implement the same protocols.
22. Which feature is characteristic of MAC filtering in wireless networks?
- It allows only authorized users to detect the network.
- It restricts computer access to a wireless network.
- It is configured on the computer rather than on the router.
- It encrypts data that is transmitted on a wireless network.
Explanation: MAC address filtering uses the MAC address to identify which devices are allowed to connect to the wireless network.
23. Which three elements do all communication methods have in common? (Choose three.)
- message priority
- message source
- message type
- message destination
- message data
- transmission medium
Explanation: All communication methods include a message source, destination, and a transmission medium.
24. Which shortened address is an accurate representation of the IPv6 address 2001:0db8:0000:0000:ab00:0000:0000:0000?
- 2001:db8:0:0:ab::
- 2001:db8:0:0:ab00::
- 2001:db8:0:ab00:0
- 2001:db8::ab00::
Explanation: There are two rules to help reduce the notation of IPv6 addresses. The first one is to omit any leading 0s (zeros) in any hextet. The second one is that a double colon (::) can replace any single, contiguous string of one or more 16-bit hextets consisting of all zeros, but the double colon (::) can only be used once within an address. If an address has more than one contiguous string of all-0 hextets, the best practice is to use the double colon (::) on the longest string. So, applying the first rule in the IPv6 address we have 2001:db8:0:0:ab00:0:0:0, and applying the second rule results in 2001:db8:0:0:ab00::
25. What type of network must a home user access in order to do online shopping?
- an intranet
- the Internet
- an extranet
- a local area network
Explanation: Home users will go online shopping over the Internet because online vendors are accessed through the Internet. An intranet is basically a local area network for internal use only. An extranet is a network for external partners to access certain resources inside an organization. A home user does not necessarily need a LAN to access the Internet. For example, a PC connects directly to the ISP through a modem.
26. What is the IP address of this server?
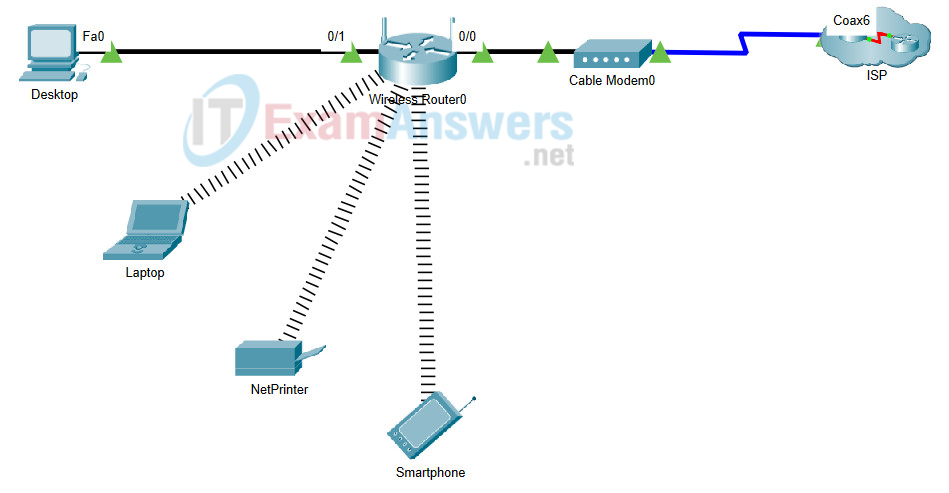
- 209.165.201.4
- 192.168.10.1
- 209.165.201.3
- 192.168.10.100
Explanation: The DNS server resolves Internet names to associated IP addresses.
27. Which protocol is used to transfer web pages from a server to a client device?
Explanation: The Hypertext Transfer Protocol (HTTP) provides services between a web browser requesting web pages and a web server responding to the requests. HTML (Hypertext Markup Language) is a markup language to instruct a web browser how to interpret and display a web page.
28. What is an advantage of the peer-to-peer network model?
- scalability
- high level of security
- ease of setup
- centralized administration
Explanation: The simplest peer-to-peer network consists of two computers that are directly connected to each other through the use of a wired or wireless connection. The advantages of peer-to-peer networking include ease of setup, lower cost, and less complexity.
29. A message is sent to all hosts on a remote network. Which type of message is it?
- limited broadcast
- multicast
- directed broadcast
- unicast
Explanation: A directed broadcast is a message sent to all hosts on a specific network. It is useful for sending a broadcast to all hosts on a nonlocal network. A multicast message is a message sent to a selected group of hosts that are part of a subscribing multicast group. A limited broadcast is used for a communication that is limited to the hosts on the local network. A unicast message is a message sent from one host to another.
30. Match the port number to the email protocol.

31. Which statement is true about the TCP/IP and OSI models?
- The TCP/IP transport layer and OSI Layer 4 provide similar services and functions.
- The TCP/IP network access layer has similar functions to the OSI network layer.
- The OSI Layer 7 and the TCP/IP application layer provide identical functions.
- The first three OSI layers describe general services that are also provided by the TCP/IP internet layer.
Explanation: The TCP/IP internet layer provides the same function as the OSI network layer. The transport layer of both the TCP/IP and OSI models provides the same function. The TCP/IP application layer includes the same functions as OSI Layers 5, 6, and 7.
32. What action will a router take when it receives a frame with a broadcast MAC address?
- It will not forward the frame to another network.
- It forwards the frame back to the sending host.
- It forwards the frame out of all connected interfaces.
- It forwards the frame back out the receiving interface.
Explanation: Routers do not forward broadcasts to other networks. Routers examine broadcasts to determine if they need to act on the broadcast, such as an ARP request or a DHCP DISCOVER message. If the router does not need to respond to the broadcast, it is dropped.
33. A host PC is attempting to lease an address through DHCP. What message is sent by the server to let the client know it is able to use the provided IP information?
- DHCPDISCOVER
- DHCPOFFER
- DHCPREQUEST
- DHCPACK
Explanation: When a host uses DHCP to automatically configure an IP address, the typically sends two messages: the DHCPDISCOVER message and the DHCPREQUEST message. These two messages are usually sent as broadcasts to ensure that all DHCP servers receive them. The servers respond to these messages using DHCPOFFER, DHCPACK, and DHCPNACK messages, depending on the circumstance.
34. What term is used to describe connecting a mobile device to another mobile device or computer to share a network connection?
- joining
- syncing
- pairing
- tethering
Explanation: Pairing describes connecting two devices using Bluetooth. Syncing Is the term used to describe synchronizing emails and calendars across a number of devices.
35. What is the primary advantage of using NAT?
- allows a large group of users to share one or more public IP addresses
- allows a large group of users to share the same private IP address within a LAN
- allows static mapping of public inside addresses to private outside addresses
- allows dynamic mapping of registered inside addresses to private outside addresses
Explanation: Network Address Translation (NAT) can allow a large group of privately addressed hosts to share one or more registered public IP addresses in order to route packets over the internet.
36. A technician is setting up equipment on a network. Which three devices will need IP addresses? (Choose three.)
- a printer with an integrated NIC
- a web camera that is attached directly to a host
- a server with two NICs
- an IP phone
- a wireless mouse
- a PDA that is attached to a networked workstation
Explanation: A device needs an IP address in order to connect to a network. A device that is attached to a networked device can use the established connection to access the network.
37. A college has five campuses. Each campus has IP phones installed. Each campus has an assigned IP address range. For example, one campus has IP addresses that start with 10.1.x.x. On another campus the address range is 10.2.x.x. The college has standardized that IP phones are assigned IP addresses that have the number 4X in the third octet. For example, at one campus the address ranges used with phones include 10.1.40.x, 10.1.41.x, 10.1.42.x, etc. Which two groupings were used to create this IP addressing scheme? (Choose two.)
- personnel type
- device type
- geographic location
- department
- support model
Explanation: The IP address design being used is by geographic location (for example, one campus is 10.1, another campus 10.2, another campus 10.3). The other design criterion is that the next octet number designates IP phones, or a specific device type, with numbers starting with 4, but which can include other numbers. Other devices that might get a designation inside this octet could be printers, PCs, and access points.
38. Which IPv6 address notation is valid?
- 2001:0DB8::ABCD::1234
- ABCD:160D::4GAB:FFAB
- 2001:DB8:0:1111::200
- 2001::ABCD::
Explanation: IPv6 addresses are represented by 32 hexadecimal digits (0-9, A-F). The size of the notation can be reduced by eliminating leading zeroes in any hextet and by replacing a single, contiguous string of hextets containing all zeroes with a double colon, which can only be used one time.
39. What makes fiber preferable to copper cabling for interconnecting buildings? (Choose three.)
- greater distances per cable run
- lower installation cost
- limited susceptibility to EMI/RFI
- durable connections
- greater bandwidth potential
- easily terminated
Explanation: Optical fiber cable transmits data over longer distances and at higher bandwidths than any other networking media. Unlike copper wires, fiber-optic cable can transmit signals with less attenuation and is completely immune to EMI and RFI.
40. What type of applications are best suited for using UDP?
- applications that are sensitive to delay
- applications that need reliable delivery
- applications that require retransmission of lost segments
- applications that are sensitive to packet loss
Explanation: UDP is not a connection-oriented protocol and does not provide retransmission, sequencing, or flow control mechanisms. It provides basic transport layer functions with a much lower overhead than TCP. Lower overhead makes UDP suitable for applications which are sensitive to delay.
41. What will a Layer 2 switch do when the destination MAC address of a received frame is not in the MAC table?
- It initiates an ARP request.
- It broadcasts the frame out of all ports on the switch.
- It notifies the sending host that the frame cannot be delivered.
- It forwards the frame out of all ports except for the port at which the frame was received.
Explanation: A Layer 2 switch determines how to handle incoming frames by using its MAC address table. When an incoming frame contains a destination MAC address that is not in the table, the switch forwards the frame out all ports, except for the port on which it was received.
42. What type of device is able to create physical movement?
- actuator
- sensor
- RFID tag
- console
Explanation: Actuators are a type of device that is used to produce physical movement.
43. Which device is an intermediary device?
- firewall
- PC
- server
- smart device
Explanation: An intermediary device sends network messages toward a final destination. Examples of intermediary devices include a firewall, router, switch, multilayer switch, and wireless router.
44. At which layer of the OSI model would a logical address be added during encapsulation?
- physical layer
- data link layer
- network layer
- transport layer
Explanation: Logical addresses, also known as IP addresses, are added at the network layer. Physical addresses are edded at the data link layer. Port addresses are added at the transport layer. No addresses are added at the physical layer.
45. Which wireless RF band do IEEE 802.11b/g devices use?
- 900 MHz
- 2.4 GHz
- 5 GHz
- 60 GHz
Explanation: 900 MHz is an FCC wireless technology that was used before development of the 802.11 standards. 900 MHz devices have a larger coverage range than the higher frequencies have and do not require line of sight between devices. 802.11b/g/n/ad devices all operate at 2.4 GHz. 802.11a/n/ac/ad devices operate at 5 GHz, and 802.11ad devices operate at 60 GHz.
46. Consider the group of five IPv4 addresses each with the subnet mask of 255.255.255.0. Which two IPv4 addresses belong to the same local network? (Choose two.)
- 192.168.10.2
- 193.168.10.16
- 192.168.10.56
- 192.167.10.74
- 192.168.100.62
Explanation: The subnet mask determines which part of the IP address is the network number. Because the subnet mask is 255.255.255.0, the first three sets of numbers in each IPv4 address indicate the network number. IPv4 addresses with the same network number are considered in the same local network.
47. Which three IPv4 network addresses are private IP addresses? (Choose three.)
- 10.0.0.0
- 172.32.0.0
- 192.157.0.0
- 172.16.0.0
- 192.168.0.0
- 224.6.0.0
Explanation: The reserved private IPv4 network addresses include 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255.
48. Which destination IPv4 address does a DHCPv4 client use to send the initial DHCP Discover packet when the client is looking for a DHCP server?
- 127.0.0.1
- 224.0.0.1
- 255.255.255.255
- the IP address of the default gateway
Explanation: Broadcast communications on a network may be directed or limited. A directed broadcast is sent to all hosts on a specific network. A limited broadcast is sent to 255.255.255.255. When a DHCP client needs to send a DHCP Discover packet in order to seek DHCP servers, the client will use this IP address of 255.255.255.255 as the destination in the IP header because it has no knowledge of the IP addresses of DHCP servers.
49. When a router receives a packet, what information must be examined in order for the packet to be forwarded to a remote destination?
- destination MAC address
- source IP address
- destination IP address
- source MAC address
Explanation: When a router receives a packet, it examines the destination address of the packet and uses the routing table to search for the best path to that network.
50. Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF
- 127.0.0.1
- 01-00-5E-00-AA-23
Explanation: The purpose of an ARP request is to find the MAC address of the destination host on an Ethernet LAN. The ARP process sends a Layer 2 broadcast to all devices on the Ethernet LAN. The frame contains the IP address of the destination and the broadcast MAC address, FFFF.FFFF.FFFF. The host with the IP address that matches the IP address in the ARP request will reply with a unicast frame that includes the MAC address of the host. Thus the original sending host will obtain the destination IP and MAC address pair to continue the encapsulation process for data transmission.
51. What process is used to place one message inside another message for transfer from the source to the destination?
- access control
- decoding
- encapsulation
- flow control
- the source MAC address and the incoming port
Explanation: Encapsulation is the process of placing one message format into another message format. An example is how a packet is placed in its entirety into the data field as it is encapsulated into a frame.
52. Which wireless technology can be used to connect wireless headphones to a computer?
Explanation: Bluetooth is a low-power, short range wireless technology that provides connectivity for accessories such as speakers, headphones, and microphones.
53. A user is setting up a home wireless network. Which type of device must the user have in order to establish the wireless network and provide access to the internet for multiple home devices?
- hub
- wireless router
- switch
- patch panel
Explanation: A wireless router connects multiple wireless devices to the network. It will then aggregate the internet access requests from home devices to the internet.
54. Which protocol is used by web servers to serve up a web page?
Explanation: Hypertext Transfer Protocol (HTTP) is a protocol that is used by web servers to serve up a web page.
55. What is the order of bandwidth measurement from smallest to largest?
- Kbps, Mbps, Gbps, Tbps
- Gbps, Tbps, Mbps, Kbps
- Tbps, Mbps, Kbps, Gbps
- Kbps, Tbps, Mbps, Gbps
Explanation: Command bandwidth measurements are as follows from smallest to largest:
- Thousands of bits per second (Kbps) or Kilobits per second
- Millions of bits per second (Mbps) or Megabits per second
- Billions of bits per second (Gbps) or Gigabits per second
- Trillions of bits per second (Tbps) or Terabits per second
56. A network technician is extending the network from the main office building over several hundred meters to a new security station. The security station needs a high speed connection to support video surveillance of the main building. What type of cable is best suited to connect the security station to the rest of the main office network?
- coax
- fiber optic
- shielded twisted pair
- unshielded twisted pair
Explanation: Fiber optic cable can deliver signals over distances of several miles. Because it uses light, fiber is impervious to RFI and EMI and is superior to signals sent over copper or aluminum wiring.
57. What data representation is used when a computer or network device is processing data?
- inferred
- text
- binary
- readable
58. True or False? Every device on a network needs an IP address to identify itself and communicate on the network.
Explanation: All network devices must have an IP address to communicate on the network. The IP address is used to uniquely identify each device on the network.
59. What type of network is defined by two computers that can both send and receive requests for resources?
- client/server
- peer-to-peer
- enterprise
- campus
Explanation: The simplest form of peer-to-peer networking consists of two computers that are directly connected to each other through the use of a wired or wireless connection.
60. What is the network number for an IPv4 address 172.16.34.10 with the subnet mask of 255.255.255.0?
- 10
- 34.10
- 172.16.0.0
- 172.16.34.0
Explanation: The subnet mask is used to determine which part of the IPv4 address is the network number. Because the subnet mask is 255.255.255.0, the first three sets of numbers in an IPv4 address indicate the network number.
61. A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a local routing table
- a network connection and usage report
- a list of all established active TCP connections
- a historical list of successful pings that have been sent
Explanation: When used by itself (without any options), the netstat command will display all the active TCP connections that are available.
62. What are the three ranges of IP addresses that are reserved for internal private use? (Choose three.)
- 10.0.0.0/8
- 64.100.0.0/14
- 127.16.0.0/12
- 172.16.0.0/12
- 192.31.7.0/24
- 192.168.0.0/16
Explanation: The private IP address blocks that are used inside companies are as follows:10.0.0.0 /8 (any address that starts with 10 in the first octet)
172.16.0.0 /12 (any address that starts with 172.16 in the first two octets through 172.31.255.255)
192.168.0.0 /16 (any address that starts with 192.168 in the first two octets)
63. Which three layers of the OSI model map to the application layer of the TCP/IP model? (Choose three.)
- application
- presentation
- session
- data link
- transport
- network
Explanation: The TCP/IP model consists of four layers: application, transport, internet, and network access. The OSI model consists of seven layers: application, presentation, session, transport, network, data link, and physical. The top three layers of the OSI model: application, presentation, and session map to the application layer of the TCP/IP model.
64. What measurement is used to indicate thousands of bits per second?
Explanation:Command bandwidth measurements are as follows:
- Thousands of bits per second (Kbps) or Kilobits per second
- Millions of bits per second (Mbps) or Megabits per second
- Billions of bits per second (Gbps) or Gigabits per second
- Trillions of bits per second (Tbps) or Terabits per second
65. Which type of network technology is used for low-speed communication between peripheral devices?
- Bluetooth
- Ethernet
- 802.11
- channels
Explanation: Bluetooth is a wireless technology that uses the 2.4 GHz frequency to connect peripheral devices over a short-range, low-speed connection.
66. Which letter represents the hexadecimal value of the decimal number 15?
Explanation: The hexadecimal numbers are 0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f. The hexadecimal number 0 represents 0 in decimal and is represented as 0000 in binary. The hexadecimal number f represents 15 in decimal.
67. Which type of server dynamically assigns an IP address to a host?
Explanation: DHCP servers can be computers or networking devices that are configured to assign IPv4 addresses to network connected devices.
68. A salesperson is using a smartphone map application to locate a business. What wireless technology enables the smartphone to receive satellite geolocation information for the map application?
Explanation: GPS, or Global Positioning System, provides the geolocation services used by smartphones to calculate the position of the phone.
69. Which type of connected device is placed on objects to track and monitor them?
- RFID tags
- sensors
- actuators
- consoles
Explanation: Radio-frequency identification (RFID) tags use electromagnetic fields to identify and track objects.
70. What is an advantage of using IPv6 ?
- more addresses for networks and hosts
- faster connectivity
- higher bandwidth
- more frequencies
Explanation: An IPv6 address is comprised of 128 bits as opposed to 32 bits in an IPv4 address. Thus it offers far more addresses for networks and hosts than an IPv4 address does.
71. Refer to the exhibit. Which router port connects to the modem provided by the service provider?
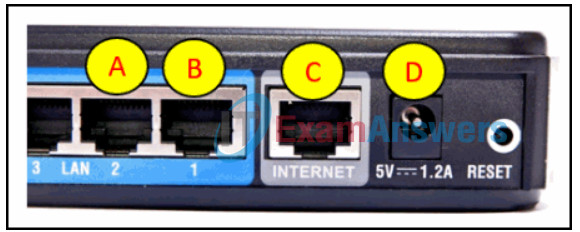
Explanation: The ports shown in the diagram are used as follows: The LAN ports, A and B, are used to connect wired devices on the home network. The Internet port, C, is connected to the modem. The port, labeled D, is the 5V DC power port that supplies power to the router.
72. What are three options for signal transmission on a network? (Choose three.)
- radio waves
- vibration pulses
- sound waves
- electrical pulses
- light pulses
Explanation: There are three common methods of signal transmission used in networks:
- Electrical signals – Transmission is achieved by representing data as electrical pulses on copper wire.
- Optical signals – Transmission is achieved by converting the electrical signals into light pulses.
- Wireless signals – Transmission is achieved by using infrared, microwave, or radio waves through the air.
73. Which three devices are considered intermediate devices in a network? (Choose three.)
- router
- server
- switch
- workstation
- network printer
- wireless access point
Explanation: Intermediate devices in a network provide network connectivity to end devices and transfer user data packets during data communications.
74. Which three pieces of information are identified by a URL? (Choose three.)
- the MAC address of the web server
- the protocol that is being used
- the domain name that is being accessed
- the IP address of the gateway
- the version of the browser
- the location of the resource
Explanation: URLs are used to access specific content on a web server through a web browser. The URL identifies the protocol that is being used such as HTTP or FTP, the domain of the server, and the location of the resource on the server.
75. What is the purpose of protocols in data communications?
- specifying the bandwidth of the channel or medium for each type of communication
- specifying the device operating systems that will support the communication
- providing the rules required for a specific type of communication to occur
- dictating the content of the message sent during communication
Explanation: Protocols provide rules that define how a message is transmitted across a network. Implementation requirements such as electronic and bandwidth details for data communication are specified by standards. Operating systems are not specified by protocols, but will implement protocols. Protocols determine how and when to send a message but they do not control the contents of a message.
76. Which network device can serve as a boundary to divide a Layer 2 broadcast domain?
- router
- Ethernet bridge
- Ethernet hub
- access point
Explanation: Layer 1 and 2 devices (LAN switch and Ethernet hub) and access point devices do not filter MAC broadcast frames. Only a Layer 3 device, such as a router, can divide a Layer 2 broadcast domain.
77. What is the destination IP address when an IPv4 host sends a DHCPDISCOVER message?
- 255.255.255.255
- 224.0.0.1
- 0.0.0.0
- 192.168.1.1
Explanation: Because a DHCP client does not have a valid IPv4 address, it must use a broadcast IP address of 255.255.255.255 as the destination address to communicate with the DHCP server. The DHCPDISCOVER message sent by the client is the first message sent in order to make initial contact with a DHCP server.
78. In the context of mobile devices, what does the term tethering involve?
- connecting a mobile device to another mobile device or computer to share a network connection
- connecting a mobile device to a hands-free headset
- connecting a mobile device to a 4G cellular network
- connecting a mobile device to a USB port on a computer in order to charge the mobile device
Explanation: Tethering allows a laptop or PC to use the Internet connection of a mobile device such as a cell phone, usually through a cellular data connection. This allows devices to connect to the Internet in locations where there is no Wi-Fi or cabled connection, but where there is still a cellular data connection.
79. What are two common media used in networks? (Choose two.)
- copper
- water
- nylon
- fiber
- wood
Explanation: Common media used in networks include copper, glass or plastic optical fiber, and wireless.
80. Which type of wireless communication is based on 802.11 standards?
- Wi-Fi
- Cellular WAN
- Bluetooth
- Infrared
Explanation: The IEEE 802.11 standards define Wi-Fi wireless LAN specifications.
81. What does a double colon (::) represent in an IPv6 address notation?
- a continuous string of one or more hextets that contain only zeros
- at least eight occurrences of the same non-zero value
- the boundary between the network portion and the host portion of the address
- the beginning of the MAC address assigned to the IPv6 device
Explanation: To help reduce the notation of IPv6 addresses a double colon (::) can replace any single, contiguous string of one or more hextets consisting of all zeros. Only one instance of the double colon can be used in any IPv6 notation.
82. A network technician attempts to ping www.example.net from a customer computer, but the ping fails. Access to mapped network drives and a shared printer are working correctly. What are two potential causes for this problem? (Choose two.)
- The Windows domain or workgroup name that is configured on the computer is incorrect.
- The target web server is down.
- The computer has been assigned a static IP address.
- DNS service is unavailable on the customer network.
- The HTTP protocol is not working properly on the target server.
Explanation: A ping would fail if the destination device was not operational. It would also fail if the DNS server was unavailable to convert the URL to an IP address. The fact that a computer had a static IP address is not a factor. Even if the target protocol (HTTP) is not functioning, the server would still respond to a ping.









Which type of packet is sent by a DHCP server after receiving a DHCP Discover message?
DHCP ACK
DHCP Discover
DHCP Offer
DHCP Request
How many unique values are possible using a single binary digit?
1
2
4
8
9
16
Which statement describes one purpose of the subnet mask setting for a host?
It is used to describe the type of the subnet.
It is used to identify the default gateway.
It is used to determine to which network the host is connected.
It is used to determine the maximum number of bits within one packet that can be placed on a particular network.
What feature of a communication protocol adds a header, to the transmitted message, containing addressing information for the sender and receiver?
encoding
encapsulation
signal_cellular_4_bar
message format
message pattern
A technician is troubleshooting a network connectivity problem. Pings to the local wireless router are successful but pings to a server on the Internet are unsuccessful. Which CLI command could assist the technician to find the location of the networking problem?
tracert
ipconfig
msconfig
ipconfig/renew
Which two types of network media carries data encoded into electrical impulses? (Choose two.)
coaxial cable
wireless media
twisted-pair cable
glass fiber-optic cable
plastic fiber-optic cable
What two radio frequency bands are used in home Wireless LANs? (Choose two.)
9 MHz
2.4 GHz
5 GHz
5 MHz
900 GHz
What statement describes a characteristic of MAC addresses?
They are the physical address of the NIC or interface.
They are only routable within the private network.
They are added as part of a Layer 3 PDU.
They have a 32-bit binary value.