1. A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Task Manager
- Event Viewer
- System Restore
- Add or Remove Programs
2. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com
- net cisco.com
- nbtstat cisco.com
- ipconfig /flushdns
- ping cisco.com
3. A technician has installed a third party utility that is used to manage a Windows 7 computer. However, the utility does not automatically start whenever the computer is started. What can the technician do to resolve this problem?
- Uninstall the program and then choose Add New Programs in the Add or Remove Programs utility to install the application.
- Set the application registry key value to one.
- Change the startup type for the utility to Automatic in Services.
- Use the Add or Remove Programs utility to set program access and defaults.
4. A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a historical list of successful pings that have been sent
- a local routing table
- a list of all established active TCP connections
- a network connection and usage report
5. What would be a reason for a computer user to use the Task Manager Performance tab?
- to increase the performance of the CPU
- to check the CPU usage of the PC
- to view the processes that are running and end a process if needed
- to view the services that are currently running on the PC
6. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS provides more security features.
- NTFS allows faster formatting of drives.
- NTFS supports larger files.
- NTFS allows the automatic detection of bad sectors.
- NTFS is easier to configure.
- NTFS allows faster access to external peripherals such as a USB drive.
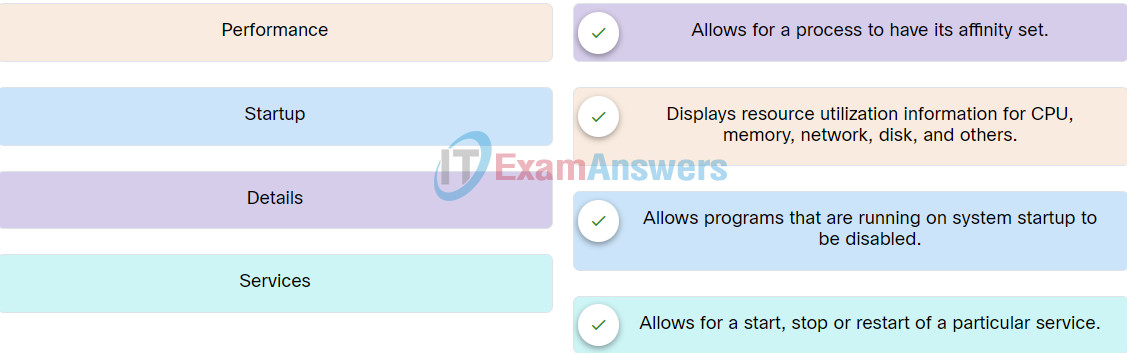
7. Match the tabs of the Windows 10 Task Manager to their functions.
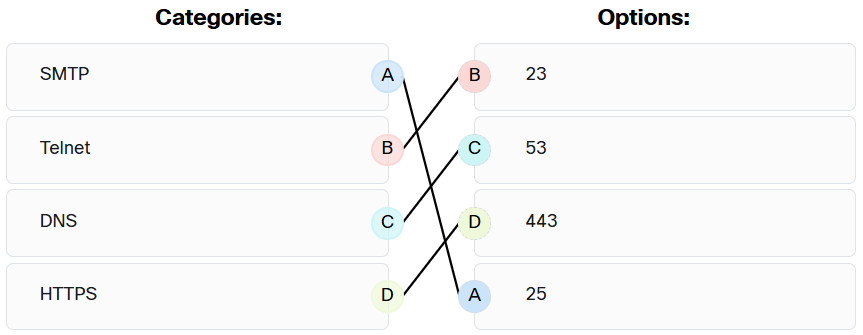
8. Match the commonly used ports on a Linux server with the corresponding service.
Operating Systems Basics Final Exam Q8
9. Which two options are window managers for Linux? (Choose two.)
- Gnome
- Kali
- File Explorer
- KDE
- PenTesting
10. Which method can be used to harden a device?
- allow USB auto-detection
- use SSH and disable the root account access over SSH
- maintain use of the same passwords
- allow default services to remain enabled
11. What term describes a set of software tools designed to increase the privileges of a user or to grant access to the user to portions of the operating system that should not normally be allowed?
- package manager
- rootkit
- compiler
- penetration testing
12. Why would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?
- More network applications are created for this environment.
- It is more secure than other server operating systems.
- The administrator has more control over the operating system.
- It is easier to use than other operating systems.
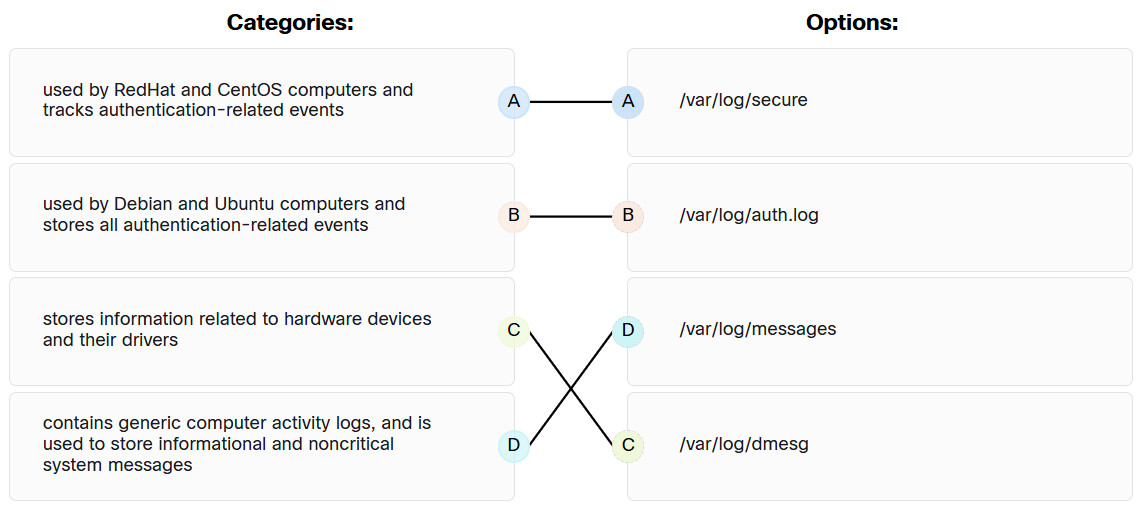
13. Match typical Linux log files to the function.
Operating Systems Basics Final Exam Q13
14. A client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?
- 443
- 404
- 110
- 80
15. Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls –l analyst.txt -rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- write only
- read, write
- read only
- read, write, execute
16. A salesperson wants to embed the location on a digital photograph to record where it was taken. What technology, product, or setting allows this task to be accomplished?
- geotagging
- GPS
- RFID
- MIME
17. A user wants to synchronize some apps, movies, music, and ebooks between mobile devices. What are the two types of connections used to synchronize this type of data? (Choose two.)
- Bluetooth
- USB
- Wi-Fi
- cellular
- NFC
18. Which cellular technology supports speeds up to 20 Gbps?
- 5G
- 4G
- Zigbee
- Z-Wave
19. What are three reasons that users of iOS devices might use iCloud? (Choose three.)
- to store documents and photos on remote servers
- to provide access to the Apple App Store and the iTunes Store
- to enable automatic software updates and patches
- to create an email account
- to make a backup copy of all of the data on their mobile device
- to increase the security settings on their mobile device
20. A traveling sales representative uses a cell phone to interact with the home office and customers, track samples, make sales calls, log mileage, and upload/download data while at a hotel. Which internet connectivity method would be a preferred method to use on the mobile device due to the low cost?
- DSL
- cable
- Wi-Fi
- cellular
21. Which protocol enables mail to be downloaded from an email server to a client and then deletes the email from the server?
- POP3
- IMAP
- HTTP
- SMTP
22. What are two features of the Android operating system? (Choose two.)
- Each implementation of Android requires a royalty to be paid to Google.
- All available Android applications have been tested and approved by Google to run on the open source operating system.
- Android has been implemented on devices such as cameras, smart TVs, and e-book readers.
- Android is open source and allows anyone to contribute to its development and evolution.
- Android applications can only be downloaded from Google Play.
23. What are two potential risks that could result from rooting or jailbreaking a mobile device? (Choose two.)
- enabling features that are disabled by a cellular carrier
- allowing the user interface to be extensively customized
- not properly creating or maintaining sandboxing features
- improving device performance
- enabling app access to the root directory
24. What is required as an additional verification mechanism on iOS mobile devices when setting up biometric screen locks, such as Touch ID or Face ID?
- a linked email account
- a swipe code
- a passcode
- a pattern lock
25. Which statement describes the Touch ID in iOS devices?
- It is used to set the touch screen sensitivity.
- It is the hash value of the user fingerprint.
- It is the encryption key set by the user.
- It is used as the passcode.
26. Which two tasks can be done with the iOS device Home button? (Choose two.)
- place apps into folders
- return to the home screen
- display the navigation icons
- respond to an alert
- wake the device
27. Android apps run primarily based on privileges enabled by the user. Sometimes an Android app requires extra privileges to access system components. How do Android apps run to accomplish both situations?
- Android apps run in a guest mode.
- Android apps run in a walled garden.
- Android apps run in a sandbox.
- Android apps run through a proxy service.
28. Which two location-specific services can the GPS feature on a mobile device offer? (Choose two.)
- planning a route between two locations
- displaying a map of a destination city while driving
- delivering local advertising
- playing local songs
- displaying local weather information
29. An employee wants to keep a local backup of iPhone data on a Windows laptop. What type of software does the employee need on the laptop to create this backup?
- iTunes
- Finder
- Google sync
- Time Machine
30. Which navigation icon on the system bar of an Android device is used to return to the previous screen?
- Recent Apps
- Menu
- Back
- Home
31. What is the outcome when a Linux administrator enters the man man command?
- The man man command configures the network interface with a manual address
- The man man command provides a list of commands available at the current prompt
- The man man command provides documentation about the man command
- The man man command opens the most recent log file
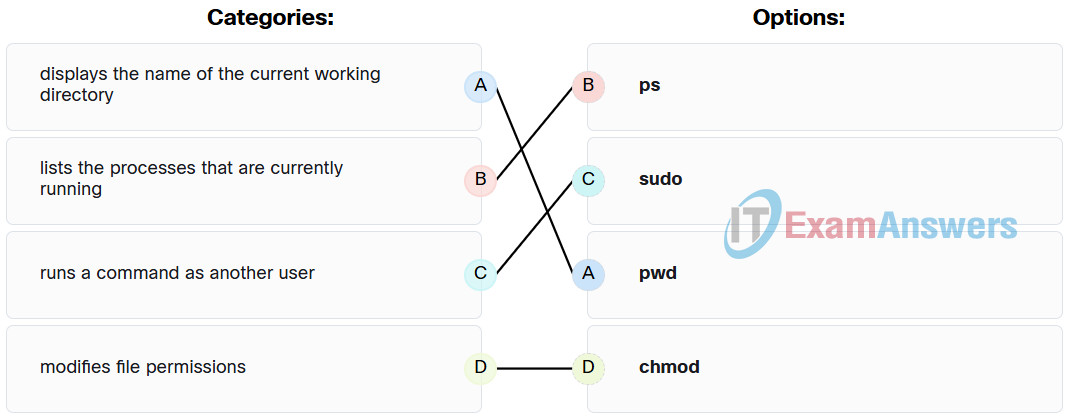
32. Match the Linux command to the function.
33. What is the purpose of running mobile device apps in a sandbox?
- to prevent malicious programs from infecting the device
- to enable the phone to run multiple operating systems
- to bypass phone carrier restrictions that prevent access to unauthorized apps
- to enable separate app icons to be displayed on the home screen
34. In the Linux shell, which character is used between two commands to instruct the shell to combine and execute these two commands in sequence?
- %
- $
- #
- |
