2.4.1.2 Packet Tracer – Skills Integration Challenge (Instructor Version)
2.4.1.2 Packet Tracer – Skills Integration Challenge
Packet Tracer – Skills Integration Challenge
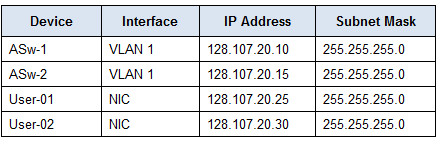
Addressing Table
Objectives
· Configure hostnames and IP addresses on two Cisco Internetwork Operating System (IOS) switches using the command-line interface (CLI).
· Use Cisco IOS commands to specify or limit access to the device configurations.
· Use IOS commands to save the running configuration.
· Configure two host devices with IP addresses.
· Verify connectivity between the two PC end devices.
Scenario
As a recently hired LAN technician, your network manager has asked you to demonstrate your ability to configure a small LAN. Your tasks include configuring initial settings on two switches using the Cisco IOS and configuring IP address parameters on host devices to provide end-to-end connectivity. You are to use two switches and two hosts/PCs on a cabled and powered network.
Requirements
· Use a console connection to access each switch.
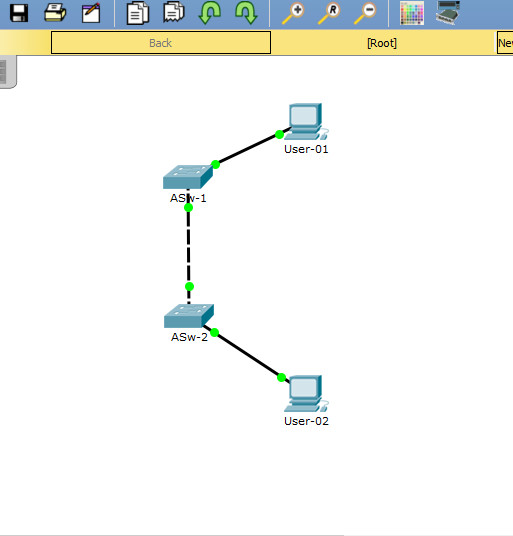
· Name ASw-1 and ASw-2 switches.
· Use the R4Xe3 password for all lines.
· Use the C4aJa secret password.
· Encrypt all clear text passwords.
· Include the word warning in the message-of-the-day (MOTD) Banner.
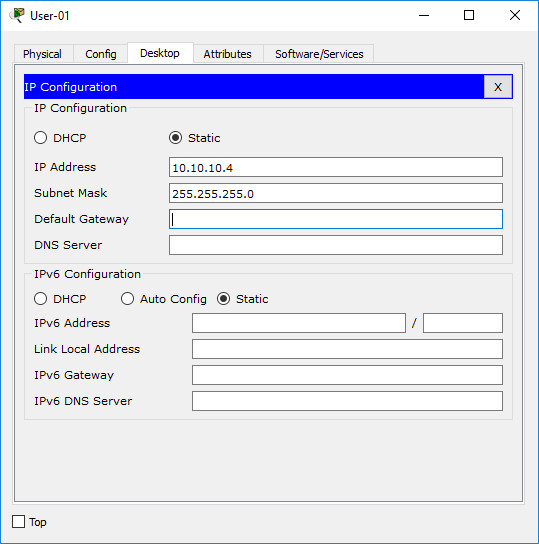
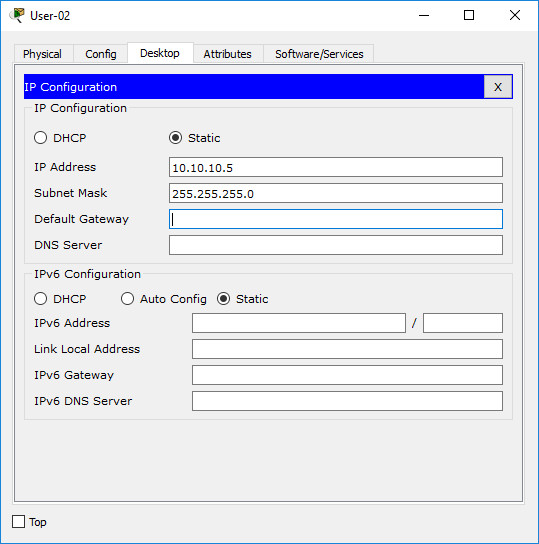
· Configure addressing for all devices according to the Addressing Table.
· Save your configurations.
· Verify connectivity between all devices.
Note: Click Check Results to see your progress. Click Reset Activity to generate a new set of requirements. If you click on this before you complete the activity, all configurations will be lost.
Instructions:
The following information is for the Instructor version only.
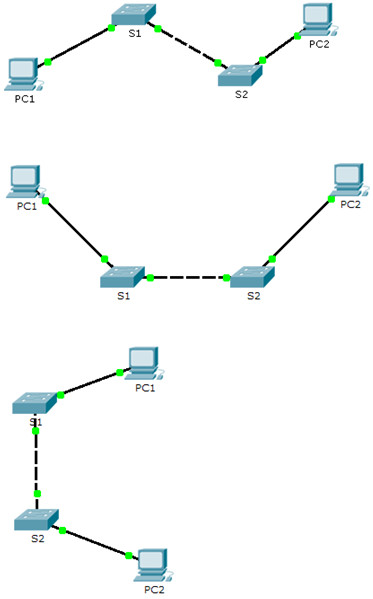
This activity uses variables that are randomly generated each time the activity is open or the “Reset Activity” button is clicked. Although the tables below show device names mapping to specific address schemes, the names and addresses are not bound together. For example, a student could get the device names shown in Scenario 1 with the addressing shown in Scenario 2. In addition, one of three versions of the topology will be presented to the student.
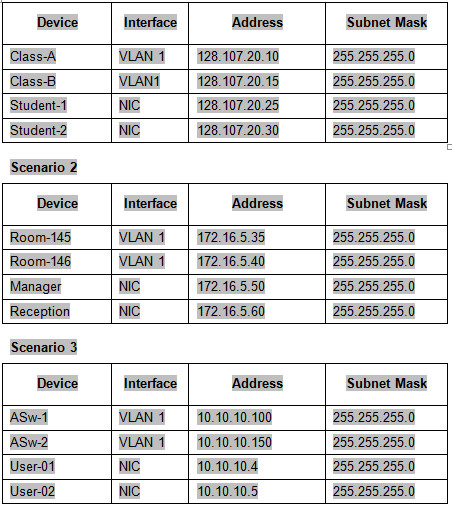
Topology Isomorphs