Command
Access-list (standard)
Use
This command is used to create a list that matches packets on a given criteria. While access-lists are most commonly associated with security, there are numerous uses.
Standard lists match on source addresses only.
Syntax
R1(config)#access-list <1-99 or 1300-1999> <permit or deny> <source address or source network or any>
Options
| <1-99> or <1300-1999> | Defines a standard access-list |
| <permit> | Permits all matches specified in the list. |
| <deny> | Denies all matches specified in the list. |
| <source address> | Host ip address that sources packets matched by the list. |
| <source network> | IP network that sourced packets matched by the list. Uses Wildcard masks for matching. |
| <any> | Match anything. |
Wildcard Masks
Wildcard masks are how access-lists know what networks apply to the list. They are the inverse of the subnet mask.
For example, network 123.123.123.0 0.0.0.255 would match any ip address in the 123.123.123.0/24 network.
Because a /24 mask is 255.255.255.0, the inverse would be 0.0.0.255. For the network 34.77.108.0/28, the subnet mask would be 255.255.255.248 and the inverse would be 0.0.0.7
Notice how the subnet mask and the inverse add to 255.
Example
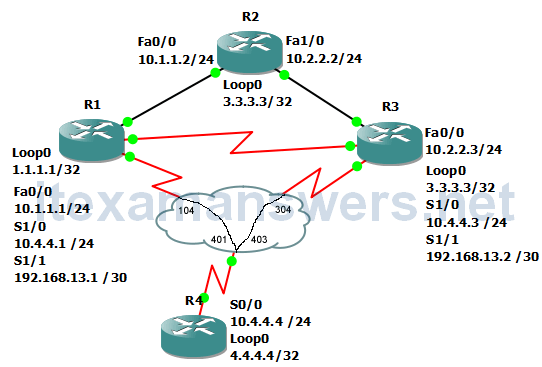
In this example, we will make an access-list that will only allow packets sourced by the host 1.1.1.1 and apply the list to R2’s Fa0/0.
R2(config)#access-list 1 permit 1.1.1.1 R2(config)#int fa0/0 R2(config-if)#ip access-group 1 in
Pinging 10.1.1.2 from R1, we see that the ping fails unless it is sourced from R1’s loopback0 interface.
R1(config)#do ping 10.1.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: U.U.U Success rate is 0 percent (0/5) R1(config)#do ping 10.1.1.2 source 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/22/44 ms R1(config)#
We can also have an access-list that will allow the entire 10.1.1.0/24 network to be permited on R2’s Fa0/0
R2(config)#access-list 55 permit 10.1.1.0 0.0.0.255 R2(config)#int fa0/0 R2(config-if)#ip access-group 55 in R2(config-if)#
Heres a quick ping test
R1(config-if)#do ping 10.1.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/19/36 ms R1(config-if)#do ping 10.1.1.2 source 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 U.U.U Success rate is 0 percent (0/5) R1(config-if)
In this example, we deny any traffic sourced from 1.1.1.1 but permit any other traffic on R2’s Fa0/0
R2(config-if)#access-list 95 deny 1.1.1.1 R2(config)#access-list 95 permit any R2(config)#int fa0/0 R2(config-if)#ip access-group 95 in R2(config-if)#do sh run int fa0/0
Notice that only 1.1.1.1 is denied.
R1(config)#do ping 10.1.1.2 source 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 U.U.U Success rate is 0 percent (0/5) R1(config)#do ping 10.1.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/13/32 ms R1(config)#do ping 10.1.1.2 source lo1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds: Packet sent with a source address of 11.11.11.11 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/20/44 ms
