Author: ITExamAnswers
6.3.2.7 Lab – Blockchain Demo 2.0 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Complete the Blockchain Demo 2.0 Complete Reflection Questions Background / Scenario Blockchain is the technology behind the cryptocurrency, bitcoin. It uses a …
6.2.3.6 Lab – Assess Risk with DREAD (Instructor Version) Objectives In this lab, you will use the DREAD risk assessment model to assess risk. Part 1: Using the DREAD Scoring System to Assess Risk Part 2: Using the DREAD System to Assess the Risk of a Described Vulnerability …
6.2.1.9 Lab – Using the CVSS (Instructor Version) Objectives In this lab, you will explain the concepts behind a strong password. Part 1: Researching the Details of the CVSS Metrics Used to Compute the CVSS Score Part 2: Using the CVSS Calculator to Determine the Severity Level of …
5.1.3.9 Lab – UPnP Vulnerabilities (Instructor Version) Lab Topology Addressing The Pi will acquire an address from the external network, while providing addresses to the internal network. Objectives Part 1: Configuring the Raspberry Pi as a wired router using a BASH script Part 2: Connecting a Client to …
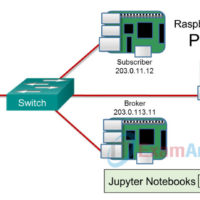
5.1.3.7 Lab – Hacking MQTT (Instructor Version) Topology Required Resources 3 Raspberry Pi 3 devices, Model B or later 8GB Micro SD card (minimum required) PC with IoTSec Kali VM Network connectivity between PC and Raspberry Pi Devices A Network Switch Objectives Part 1: Setting up a Publishing/Subscriber …
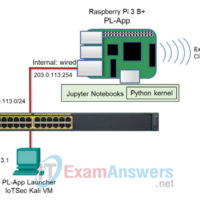
5.1.2.9 Lab – Web Application Vulnerability (Instructor Version) Topology Required Resources Raspberry Pi 3 Model B or later (with PL-App) 8GB Micro SD card (minimum required) PC with IoTSec Kali VM Network connectivity between PC and Raspberry Pi Objectives In this lab, you will discover vulnerabilities in a …
5.1.2.8 Lab – Challenge Passwords with Kali Tools (Instructor Version) Objectives In this lab, you will explore tools that are available in the Kali VM to challenge passwords. Part 1: Using Hashcat to Challenge Passwords Part 2: Investigating Other Password Challenging Tools on Kali Linux Background / Scenario …
5.1.2.7 Lab – Use OpenVAS for Vulnerability Assessment (Instructor Version) Addressing Table Device IP Address Subnet Mask Kali 203.0.113.1 255.255.255.0 Metasploitable 203.0.113.5 255.255.255.0 Objectives Part 1: Exploring OpenVAS Part 2: Configuring a Vulnerability Scan Part 3: Reviewing the Results Background / Scenario Open Vulnerability Assessment System (OpenVAS) is …
4.2.2.6 Lab – Packet Crafting to Exploit Unsecured Ports (Instructor Version) Topology Objectives Part 1: Using hping3 for Port Scanning Part 2: Crafting Different Types of ICMP Messages Part 3: Launching DoS Attacks Background / Scenario hping3 is a tool used to send custom-crafted TCP/IP packets to a …
4.2.2.5 Lab – Port Scanning an IoT Device (Instructor Version) Topology Objectives Part 1: Perform a Nmap network discovery scan Part 2: Compare a Nmap TCP default port scan and full scan Part 3: Perform a Nmap UDP Scan Part 4: Perform Nmap OS and Service Foot Printing …