4.3.1.1 It’s Network Access Time (Instructor Version – Optional Lab)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or to provide additional practice.
Objectives
Describe features available for switches to support requirements of a small- to medium-sized business network.
Students will design two networks using Packet Tracer to suffice requirements shown in a LAN and WAN scenarios.
Scenario
Use Packet Tracer for this activity. Work with a classmate to create two network designs to accommodate the following scenarios:
Scenario 1 – Classroom Design (LAN)
- 15 student end devices represented by 1 or 2 PCs.
- 1 instructor end device; a server is preferred.
- Device capability to stream video presentations over LAN connection. Internet connectivity is not required in this design.
Scenario 2 – Administrative Design (WAN)
- All requirements as listed in Scenario 1.
- Add access to and from a remote administrative server for video presentations and pushed updates for network application software.
Both the LAN and WAN designs should fit on to one Packet Tracer file screen. All intermediary devices should be labeled with the switch model (or name) and the router model (or name).
Save your work and be ready to justify your device decisions and layout to your instructor and the class.
Reflection
1. What are some problems that may be encountered if you receive streaming video from your instructor’s server through a low-end switch?
____________________________________________________
Answers will vary – bandwidth might be too low for the video stream to many recipients causing lag time – distortion may result in picture, audio, etc. Some stations could be “kicked out” as a result of traffic overload depending on the application program being used to stream the video, etc. There is also the possibility of “sniffing or snooping” depending on how the switch is configured.
2. How would the traffic flow be determined: multicast or broadcast – in transmission?
____________________________________________________
When users have to “log in” to the application to receive the video transmission, this would be considered a multicast. If students are set up collectively into a group by the server to push the stream, it would be considered a broadcast on the LAN side.
3. What would influence your decision on the type of switch to use for voice, streaming video and regular data these types of transmissions?
____________________________________________________
Answers will vary – if the switch will be also used for WAN streams and other intensive download traffic, a higher level switch would be used.
4. As you learned in the first course of the Academy, video and voice use a special TCP/IP model, transport layer protocol. What protocol is used in this layer and why is it important to voice and video streaming?
_____________________________________________________
(UDP is the protocol used for voice and video – it allows for a continuous stream of data to flow without interruption to report delays back to the sender. There is no guaranteed delivery of data from source to destination hosts)
Packet Tracer Example (answers will vary)
Instructor Note: This is a representative model that might be “built” as a result of this activity:
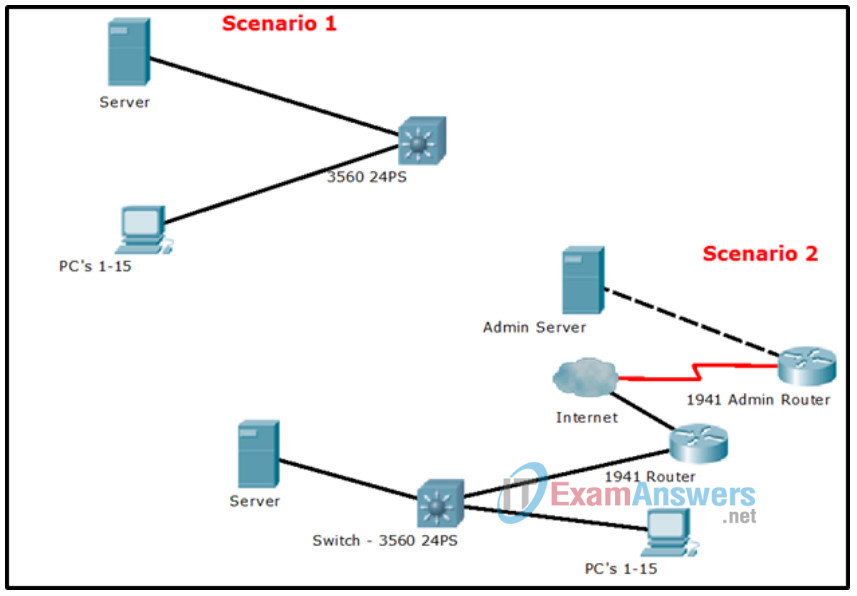
Identify elements of the model that map to IT-related content:
- Voice, video and regular data can traverse networks using different devices, such as routers and switches.
- The type of switch that is used as an intermediary device provides different functional capacities.
- The type of network traffic will impact the switch’s performance in sending and delivering data.
- Sufficient bandwidth is necessary to handle different types of traffic; therefore, network switch types/models and their capabilities are important to the switch model and type.
- Security impacts the switch selection. If the switch will be accessible physically, remotely or over the network locally, it will need to have security configured to include ACLs and/or port security.
