8.1.2.5 Lab – Configuring Basic DHCPv4 on a Switch (Instructor Version – Optional Lab)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or to provide additional practice.
Topology
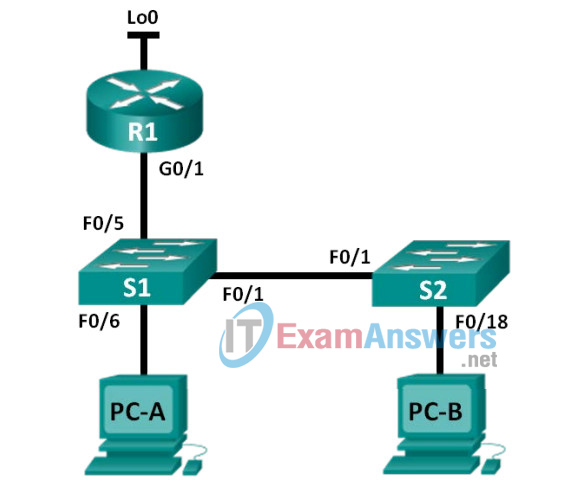
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| R1 | G0/1 | 192.168.1.10 | 255.255.255.0 |
| Lo0 | 209.165.200.225 | 255.255.255.224 | |
| S1 | VLAN 1 | 192.168.1.1 | 255.255.255.0 |
| VLAN 2 | 192.168.2.1 | 255.255.255.0 |
Objectives
Part 1: Build the Network and Configure Basic Device Settings
Part 2: Change the SDM Preference
- Set the SDM preference to lanbase-routing on S1.
Part 3: Configure DHCPv4
- Configure DHCPv4 for VLAN 1.
- Verify DHCPv4 and connectivity.
Part 4: Configure DHCP for Multiple VLANs
- Assign ports to VLAN 2.
- Configure DHCPv4 for VLAN 2.
- Verify DHCPv4 and connectivity.
Part 5: Enable IP Routing
- Enable IP routing on the switch.
- Create static routes.
Background / Scenario
A Cisco 2960 switch can function as a DHCPv4 server. The Cisco DHCPv4 server assigns and manages IPv4 addresses from identified address pools that are associated with specific VLANs and switch virtual interfaces (SVIs). The Cisco 2960 switch can also function as a Layer 3 device and route between VLANs and a limited number of static routes. In this lab, you will configure DHCPv4 for both single and multiple VLANs on a Cisco 2960 switch, enable routing on the switch to allow for communication between VLANs, and add static routes to allow for communication between all hosts.
Note: This lab provides minimal assistance with the actual commands necessary to configure DHCP. However, the required commands are provided in Appendix A. Test your knowledge by trying to configure the devices without referring to the appendix.
Note: The routers used with CCNA hands-on labs are Cisco 1941 Integrated Services Routers (ISRs) with Cisco IOS Release 15.2(4)M3 (universalk9 image). The switches used are Cisco Catalyst 2960s with Cisco IOS Release 15.0(2) (lanbasek9 image). Other routers, switches and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of this lab for the correct interface identifiers.
Note: Make sure that the router and switches have been erased and have no startup configurations. If you are unsure, contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 1 Router (Cisco 1941 with Cisco IOS Release 15.2(4)M3 universal image or comparable)
- 2 Switches (Cisco 2960 with Cisco IOS Release 15.0(2) lanbasek9 image or comparable)
- 2 PCs (Windows 7, Vista, or XP with terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Part 1: Build the Network and Configure Basic Device Settings
Step 1: Cable the network as shown in the topology.
Step 2: Initialize and reload the router and switches.
Step 3: Configure basic setting on devices.
a. Console into the router and enter global configuration mode.
b. Copy the following basic configuration and paste it to the running-configuration on the router.
no ip domain-lookup service password-encryption enable secret class banner motd # Unauthorized access is strictly prohibited. # line con 0 password cisco login logging synchronous line vty 0 4 password cisco login
c. Console into the switches and enter global configuration mode.
d. Copy the following basic configuration and paste it to the running-configuration on the switches.
no ip domain-lookup service password-encryption enable secret class banner motd # Unauthorized access is strictly prohibited. # line con 0 password cisco login logging synchronous line vty 0 15 password cisco login exit
e. Assign device names as shown in the topology.
f. Configure the IP addresses on R1 G0/1 and Lo0 interfaces, according to the Addressing Table.
g. Configure the IP addresses on S1 VLAN 1 and VLAN 2 interfaces, according to the Addressing Table.
h. Save the running configuration to the startup configuration file.
Part 2: Change the SDM Preference
The Cisco Switch Database Manager (SDM) provides multiple templates for the Cisco 2960 switch. The templates can be enabled to support specific roles depending on how the switch is used in the network. In this lab, the sdm lanbase-routing template is enabled to allow the switch to route between VLANs and to support static routing.
Step 1: Display the SDM preference on S1.
On S1, issue the show sdm prefer command in privileged EXEC mode. If the template has not been changed from the factory default, it should still be the default template. The default template does not support static routing. If IPv6 addressing has been enabled, the template will be dual-ipv4-and-ipv6 default.
S1# show sdm prefer The current template is "default" template. The selected template optimizes the resources in the switch to support this level of features for 0 routed interfaces and 255 VLANs. number of unicast mac addresses: 8K number of IPv4 IGMP groups: 0.25K number of IPv4/MAC qos aces: 0.125k number of IPv4/MAC security aces: 0.375k S1# show sdm prefer The current template is "dual-ipv4-and-ipv6 default" template. The selected template optimizes the resources in the switch to support this level of features for 0 routed interfaces and 255 VLANs. number of unicast mac addresses: 4K number of IPv4 IGMP groups + multicast routes: 0.25K number of IPv4 unicast routes: 0 number of IPv6 multicast groups: 0.375k number of directly-connected IPv6 addresses: 0 number of indirect IPv6 unicast routes: 0 number of IPv4 policy based routing aces: 0 number of IPv4/MAC qos aces: 0.125k number of IPv4/MAC security aces: 0.375k number of IPv6 policy based routing aces: 0 number of IPv6 qos aces: 0.625k number of IPv6 security aces: 125 S1# show sdm prefer The current template is "lanbase-routing" template. The selected template optimizes the resources in the switch to support this level of features for 0 routed interfaces and 255 VLANs. number of unicast mac addresses: 4K number of IPv4 IGMP groups + multicast routes: 0.25K number of IPv4 unicast routes: 0.75K number of directly-connected IPv4 hosts: 0.75K number of indirect IPv4 routes: 16 number of IPv6 multicast groups: 0.375k number of directly-connected IPv6 addresses: 0.75K number of indirect IPv6 unicast routes: 16 number of IPv4 policy based routing aces: 0 number of IPv4/MAC qos aces: 0.125k number of IPv4/MAC security aces: 0.375k number of IPv6 policy based routing aces: 0 number of IPv6 qos aces: 0.375k number of IPv6 security aces: 127
What is the current template?
___________________________________________________
Answers will vary. “default” or “dual-ipv4-and-ipv6 default” or “lanbase-routing”.
Step 2: Change the SDM Preference on S1.
a. Set the SDM preference to lanbase-routing. (If lanbase-routing is the current template, please proceed to Part 3.) From global configuration mode, issue the sdm prefer lanbase-routing command.
S1(config)# sdm prefer lanbase-routing Changes to the running SDM preferences have been stored, but cannot take effect until the next reload. Use 'show sdm prefer' to see what SDM preference is currently active. S1# show sdm prefer The current template is "default" template. The selected template optimizes the resources in the switch to support this level of features for 0 routed interfaces and 255 VLANs. number of unicast mac addresses: 8K number of IPv4 IGMP groups: 0.25K number of IPv4/MAC qos aces: 0.125k number of IPv4/MAC security aces: 0.375k On next reload, template will be "lanbase-routing" template.
Which template will be available after reload? _______________________________lanbase-routing
b. The switch must be reloaded for the template to be enabled.
S1# reload System configuration has been modified. Save? [yes/no]: no Proceed with reload? [confirm]
Note: The new template will be used after reboot even if the running configuration has not been saved. To save the running configuration, answer yes to save the modified system configuration.
Step 3: Verify the lanbase-routing template is loaded.
Issue the show sdm prefer command to verify that the lanbase-routing template has been loaded on S1.
S1# show sdm prefer
The current template is "lanbase-routing" template.
The selected template optimizes the resources in
the switch to support this level of features for
0 routed interfaces and 255 VLANs.
number of unicast mac addresses: 4K
number of IPv4 IGMP groups + multicast routes: 0.25K
number of IPv4 unicast routes: 0.75K
number of directly-connected IPv4 hosts: 0.75K
number of indirect IPv4 routes: 16
number of IPv6 multicast groups: 0.375k
number of directly-connected IPv6 addresses: 0.75K
number of indirect IPv6 unicast routes: 16
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.125k
number of IPv4/MAC security aces: 0.375k
number of IPv6 policy based routing aces: 0
number of IPv6 qos aces: 0.375k
number of IPv6 security aces: 127
Part 3: Configure DHCPv4
In Part 3, you will configure DHCPv4 for VLAN 1, check IP settings on host computers to validate DHCP functionality, and verify connectivity for all devices in VLAN 1.
Step 1: Configure DHCP for VLAN 1.
a. Exclude the first 10 valid host addresses from network 192.168.1.0/24. Write the command you used in the space provided.
____________________________________________________
S1(config)# ip dhcp excluded-address 192.168.1.1 192.168.1.10
b. Create a DHCP pool named DHCP1. Write the command you used in the space provided.
____________________________________________________
S1(config)# ip dhcp pool DHCP1
c. Assign the network 192.168.1.0/24 for available addresses. Write the command you used in the space provided.
____________________________________________________
S1(dhcp-config)# network 192.168.1.0 255.255.255.0
d. Assign the default gateway as 192.168.1.1. Write the command you used in the space provided.
____________________________________________________
S1(dhcp-config)# default-router 192.168.1.1
e. Assign the DNS server as 192.168.1.9. Write the command you used in the space provided.
____________________________________________________
S1(dhcp-config)# dns-server 192.168.1.9
f. Assign a lease time of 3 days. Write the command you used in the space provided.
____________________________________________________
S1(dhcp-config)# lease 3
g. Save the running configuration to the startup configuration file.
Step 2: Verify DHCP and connectivity.
a. On PC-A and PC-B, open the command prompt and issue the ipconfig command. If IP information is not present, or if it is incomplete, issue the ipconfig /release command, followed by the ipconfig /renew command.
For PC-A, list the following:
IP Address: ________________________________192.168.1.11
Subnet Mask: ______________________________255.255.255.0
Default Gateway: ____________________________192.168.1.1
For PC-B, list the following:
IP Address: ________________________________192.168.1.12
Subnet Mask: ______________________________255.255.255.0
Default Gateway: ____________________________192.168.1.1
b. Test connectivity by pinging from PC-A to the default gateway, PC-B, and R1.
From PC-A, is it possible to ping the VLAN 1 default gateway? __________Yes
From PC-A, is it possible to ping PC-B? __________Yes
From PC-A, is it possible to ping R1 G0/1? __________Yes
If the answer is no to any of these questions, troubleshoot the configurations and correct the error.
Part 4: Configure DHCPv4 for Multiple VLANs
In Part 4, you will assign PC-A to a port accessing VLAN 2, configure DHCPv4 for VLAN 2, renew the IP configuration of PC-A to validate DHCPv4, and verify connectivity within the VLAN.
Step 1: Assign a port to VLAN 2.
Place port F0/6 into VLAN 2. Write the command you used in the space provided.
__________________________________________________
S1(config)# interface f0/6
S1(config-if)# switchport access vlan 2
Step 2: Configure DHCPv4 for VLAN 2
a. Exclude the first 10 valid host addresses from network 192.168.2.0. Write the command you used in the space provided.
__________________________________________________
S1(config)# ip dhcp excluded-address 192.168.2.1 192.168.2.10
b. Create a DHCP pool named DHCP2. Write the command you used in the space provided.
__________________________________________________
S1(config)# ip dhcp pool DHCP2
c. Assign the network 192.168.2.0/24 for available addresses. Write the command you used in the space provided.
__________________________________________________
S1(dhcp-config)# network 192.168.2.0 255.255.255.0
d. Assign the default gateway as 192.168.2.1. Write the command you used in the space provided.
___________________________________________________
S1(dhcp-config)# default-router 192.168.2.1
e. Assign the DNS server as 192.168.2.9. Write the command you used in the space provided.
___________________________________________________
S1(dhcp-config)# dns-server 192.168.2.9
f. Assign a lease time of 3 days. Write the command you used in the space provided.
____________________________________________________
S1(dhcp-config)# lease 3
g. Save the running configuration to the startup configuration file.
Step 3: Verify DHCPv4 and connectivity.
a. On PC-A, open the command prompt and issue the ipconfig /release command, followed by ipconfig /renew command.
For PC-A, list the following:
IP Address: ___________________________________192.168.2.11
Subnet Mask: __________________________________255.255.255.0
Default Gateway: _______________________________192.168.2.1
b. Test connectivity by pinging from PC-A to the VLAN 2 default gateway and PC-B.
From PC-A, is it possible to ping the default gateway? ________Yes
From PC-A, is it possible to ping PC-B? ________No
Were these pings successful? Why?
_________________________________________________
Because the default gateway is in the same network as PC-A, PC-A can ping the default gateway. PC-B is in a different network; therefore, the ping from PC-A is not successful.
c. Issue the show ip route command on S1.
S1# show ip route Default gateway is not set Host Gateway Last Use Total Uses Interface ICMP redirect cache is empty
What was the result of this command?
________________________________________________
No default gateway has been set and no routing table is present on the switch.
Part 5: Enable IP Routing
In Part 5, you will enable IP routing on the switch, which will allow for inter-VLAN communication. For all networks to communicate, static routes on S1 and R1 must be implemented.
Step 1: Enable IP routing on S1.
a. From global configuration mode, use the ip routing command to enable routing on S1.
S1(config)# ip routing
b. Verify inter-VLAN connectivity.
From PC-A, is it possible to ping PC-B? ________Yes
What function is the switch performing?
____________________________________________________
The switch is routing between VLANs.
c. View the routing table information for S1.
S1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is not set 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.1.0/24 is directly connected, Vlan1 L 192.168.1.1/32 is directly connected, Vlan1 192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.2.0/24 is directly connected, Vlan2 L 192.168.2.1/32 is directly connected, Vlan2
What route information is contained in the output of this command?
__________________________________________________
The switch exhibits a routing table showing VLANs as directly connected networks 192.168.1.0/24 and 192.168.2.0/24.
d. View the routing table information for R1.
R1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is not set 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.1.0/24 is directly connected, GigabitEthernet0/1 L 192.168.1.10/32 is directly connected, GigabitEthernet0/1 209.165.200.0/27 is variably subnetted, 2 subnets, 2 masks C 209.165.200.0/27 is directly connected, Loopback0 L 209.165.200.225/32 is directly connected, Loopback0
What route information is contained in the output of this command?
__________________________________________________
The router output shows directly connected networks of 192.168.1.0 and to 209.165.200.224 but has no entry for the 192.168.2.0 network.
e. From PC-A, is it possible to ping R1? _________No
From PC-A, is it possible to ping Lo0? _________No
Consider the routing table of the two devices, what must be added to communicate between all networks?
__________________________________________________
In order for communication to occur between all networks, routes must be added to the routing tables.
Step 2: Assign static routes.
Enabling IP routing allows the switch to route between VLANs assigned on the switch. For all VLANs to communicate with the router, static routes must be added to the routing table of both the switch and the router.
a. On S1, create a default static route to R1. Write the command you used in the space provided.
__________________________________________________
S1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.10
b. On R1, create a static route to VLAN 2. Write the command you used in the space provided.
__________________________________________________
R1(config)# ip route 192.168.2.0 255.255.255.0 g0/1
c. View the routing table information for S1.
S1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is 192.168.1.10 to network 0.0.0.0 S* 0.0.0.0/0 [1/0] via 192.168.1.10 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.1.0/24 is directly connected, Vlan1 L 192.168.1.1/32 is directly connected, Vlan1 192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.2.0/24 is directly connected, Vlan2 L 192.168.2.1/32 is directly connected, Vlan2
How is the default static route represented?
__________________________________________________
Gateway of last resort is 192.168.1.10 to network 0.0.0.0
d. View the routing table information for R1.
R1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is not set 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.1.0/24 is directly connected, GigabitEthernet0/1 L 192.168.1.10/32 is directly connected, GigabitEthernet0/1 S 192.168.2.0/24 is directly connected, GigabitEthernet0/1 209.165.200.0/24 is variably subnetted, 2 subnets, 2 masks C 209.165.200.0/27 is directly connected, Loopback0 L 209.165.200.225/32 is directly connected, Loopback0
How is the static route represented?
____________________________________________________
S 192.168.2.0/24 is directly connected, GigabitEthernet0/1
e. From PC-A, is it possible to ping R1? _________Yes
From PC-A, is it possible to ping Lo0? _________Yes
Reflection
1. In configuring DHCPv4, why would you exclude the static addresses prior to setting up the DHCPv4 pool?
_______________________________________________________
If the static addresses were excluded after the DHCPv4 pool was created, a window of time exists where the excluded addresses could be given out dynamically to hosts.
2. If multiple DHCPv4 pools are present, how does the switch assign the IP information to hosts?
_______________________________________________________
The switch will assign IP configurations based on the VLAN assignment of the port to which the host is connected.
3. Besides switching, what functions can the Cisco 2960 switch perform?
_______________________________________________________
The switch can function as a DHCP server and can perform static and inter-VLAN routing.
Router Interface Summary Table
| Router Interface Summary | ||||
|---|---|---|---|---|
| Router Model | Ethernet Interface #1 | Ethernet Interface #2 | Serial Interface #1 | Serial Interface #2 |
| 1800 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 1900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2801 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 2811 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface. | ||||
Appendix A: Configuration Commands
Configure DHCPv4
S1(config)# ip dhcp excluded-address 192.168.1.1 192.168.1.10 S1(config)# ip dhcp pool DHCP1 S1(dhcp-config)# network 192.168.1.0 255.255.255.0 S1(dhcp-config)# default-router 192.168.1.1 S1(dhcp-config)# dns-server 192.168.1.9 S1(dhcp-config)# lease 3
Configure DHCPv4 for Multiple VLANs
S1(config)# interface f0/6 S1(config-if)# switchport access vlan 2 S1(config)# ip dhcp excluded-address 192.168.2.1 192.168.2.10 S1(config)# ip dhcp pool DHCP2 S1(dhcp-config)# network 192.168.2.0 255.255.255.0 S1(dhcp-config)# default-router 192.168.2.1 S1(dhcp-config)# dns-server 192.168.2.9 S1(dhcp-config)# lease 3
Enable IP RoutingS1(config)# ip routing
S1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.10 R1(config)# ip route 192.168.2.0 255.255.255.0 g0/1
Device Configs
Router R1
R1#show run Building configuration... Current configuration : 1489 bytes ! version 15.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R1 ! boot-start-marker boot-end-marker ! ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model memory-size iomem 15 ! ! ! ! ! ! ! no ip domain lookup ip cef no ipv6 cef multilink bundle-name authenticated ! ! interface Loopback0 ip address 209.165.200.225 255.255.255.0 ! interface Embedded-Service-Engine0/0 no ip address shutdown ! interface GigabitEthernet0/0 no ip address shutdown duplex auto speed auto ! interface GigabitEthernet0/1 ip address 192.168.1.10 255.255.255.0 duplex auto speed auto ! interface Serial0/0/0 no ip address shutdown clock rate 2000000 ! interface Serial0/0/1 no ip address shutdown ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ip route 192.168.2.0 255.255.255.0 GigabitEthernet0/1 ! ! ! ! control-plane ! ! ! line con 0 password cisco login line aux 0 line 2 no activation-character no exec transport preferred none transport input all transport output pad telnet rlogin lapb-ta mop udptn v120 ssh stopbits 1 line vty 0 4 password cisco login transport input all ! scheduler allocate 20000 1000 ! end
Switch S1
S1#show run Building configuration... Current configuration : 3636 bytes ! version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model system mtu routing 1500 ip routing ip dhcp excluded-address 192.168.1.1 192.168.1.10 ip dhcp excluded-address 192.168.2.1 192.168.2.10 ! ip dhcp pool DHCP1 network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 dns-server 192.168.1.9 lease 3 ! ip dhcp pool DHCP2 network 192.168.2.0 255.255.255.0 default-router 192.168.2.1 dns-server 192.168.2.9 lease 3 ! ! no ip domain-lookup ! ! crypto pki trustpoint TP-self-signed-2531409152 enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-2531409152 revocation-check none rsakeypair TP-self-signed-2531409152 ! ! crypto pki certificate chain TP-self-signed-2531409152 certificate self-signed 01 3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030 31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274 69666963 6174652D 32353331 34303931 3532301E 170D3933 30333031 30303030 35365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649 4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 35333134 30393135 3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 8100CA1B 27DE634E CF9FE284 C86127EF 41E7A52F 0A82FA2B 7C5448B7 184EA1AB C22510E1 38A742BC D9F416FD 93A52DC6 BA77A928 B317DA75 1B3E2C66 C2D9061B 806132D9 E3189012 467C7A2C DCAC3EF4 4C419338 790AA98B C7A81D73 8621536C 4A90659E 267BA2E3 36F801A4 F06BEC65 386A40DA 255D9790 F9412706 9E73A660 45230203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603 551D2304 18301680 14A7356A D364AE65 E1E9D42F 9B059B27 B69BB9C6 FD301D06 03551D0E 04160414 A7356AD3 64AE65E1 E9D42F9B 059B27B6 9BB9C6FD 300D0609 2A864886 F70D0101 05050003 8181002A D78919E7 0D75567C EF60036C 6C4B051A 2ABC5B9C DA1C1E48 AF33C405 5C64E074 B954C5B5 D825BE61 7340C695 03049797 D869E516 3936D0EC C871F140 66A1DEB2 BA57AB0D D2AB2706 17674B3A 7423C276 B96CFB88 DE98A86E 7B539B68 7DEE53BB ED16BFA0 A89A5CA4 79F15F49 59DDF6E5 E716514A 5CFC7522 8E76778E 029E8F quit ! ! ! ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! ! ! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 switchport access vlan 2 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 ip address 192.168.1.1 255.255.255.0 ! interface Vlan2 ip address 192.168.2.1 255.255.255.0 ! ip http server ip http secure-server ip route 0.0.0.0 0.0.0.0 192.168.1.10 ! ! ! line con 0 password cisco login line vty 0 4 password cisco login line vty 5 15 password cisco login ! end
