Version 6.0:
1. Which statement best describes a WAN?
- A WAN interconnects LANs over long distances.
- A WAN is a public utility that enables access to the Internet.
- WAN is another name for the Internet.
- A WAN is a LAN that is extended to provide secure remote network access.
2. Connecting offices at different locations using the Internet can be economical for a business. What are two important business policy issues that should be addressed when using the Internet for this purpose? (Choose two.)
- addressing
- bandwidth
- privacy
- security
- WAN technology
3. What is a disadvafntage of a packet-switched network compared to a circuit-switched network?
- higher cost
- fixed capacity
- less flexibility
- higher latency
4. A company is considering updating the campus WAN connection. Which two WAN options are examples of the private WAN architecture? (Choose two.)
- cable
- leased line
- Ethernet WAN
- municipal Wi-Fi
- digital subscriber line
5. Which statement describes a characteristic of dense wavelength division multiplexing (DWDM)?
- It supports the SONET standard, but not the SDH standard.
- It enables bidirectional communications over one pair of copper cables.
- It can be used in long-range communications, like connections between ISPs.
- It assigns incoming electrical signals to specific frequencies.
6. Which WAN technology can serve as the underlying network to carry multiple types of network traffic such as IP, ATM, Ethernet, and DSL?
- ISDN
- MPLS
- Frame Relay
- Ethernet WAN
7. Which two WAN technologies are more likely to be used by a business than by teleworkers or home users? (Choose two.)
- cable
- DSL
- Frame Relay
- MetroE
- VPN
8. The security policy in a company specifies that the staff in the sales department must use a VPN to connect to the corporate network to access the sales data when they travel to meet customers. What component is needed by the sales staff to establish a remote VPN connection?
- VPN gateway
- VPN appliance
- VPN concentrator
- VPN client software
9. How many DS0 channels are bundled to produce a 1.544 Mbps T1 line?
- 2
- 12
- 24
- 28
10. What function is provided by Multilink PPP?
- spreading traffic across multiple physical WAN links
- dividing the bandwidth of a single link into separate time slots
- enabling traffic from multiple VLANs to travel over a single Layer 2 link
- creating one logical link between two LAN switches via the use of multiple physical links
11. Refer to the exhibit. A network administrator is configuring the PPP link between the routers R1 and R2. However, the link cannot be established. Based on the partial output of the show running-config command, what is the cause of the problem?
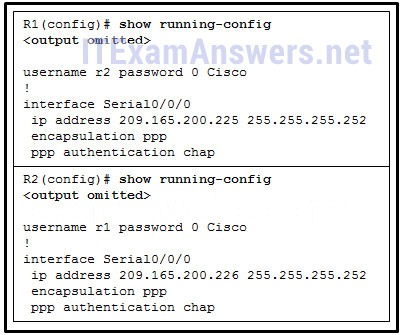
- The usernames do not match each other.
- The usernames do not match the host names.
- The passwords for CHAP should be in lowercase.
- The username r1 should be configured on the router R1 and the username r2 should be configured on the router R2.
12. Refer to the exhibit. A network administrator has configured routers RTA and RTB, but cannot ping from serial interface to serial interface. Which layer of the OSI model is the most likely cause of the problem?
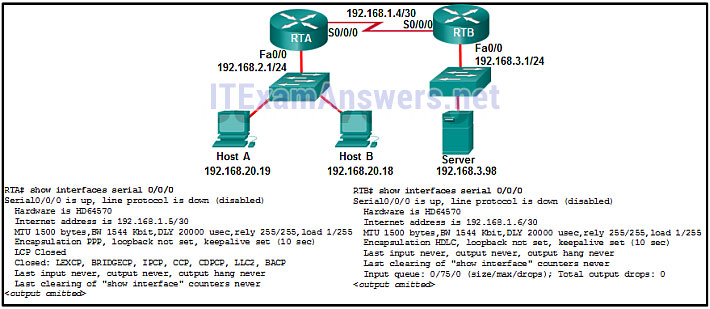
- application
- transport
- network
- data link
- physical
13. What advantage does DSL have compared to cable technology?
- DSL upload and download speeds are always the same.
- DSL is faster.
- DSL has no distance limitations.
- DSL is not a shared medium.
14. Which broadband technology would be best for a user that needs remote access when traveling in mountains and at sea?
- Wi-Fi Mesh
- mobile broadband
- WiMax
- satellite
15. Which technology requires the use of PPPoE to provide PPP connections to customers?
- dialup analog modem
- dialup ISDN modem
- DSL
- T1
16. Refer to the exhibit. What is the network administrator verifying when issuing the show ip interface brief command on R1 in respect to the PPPoE connection to R2?
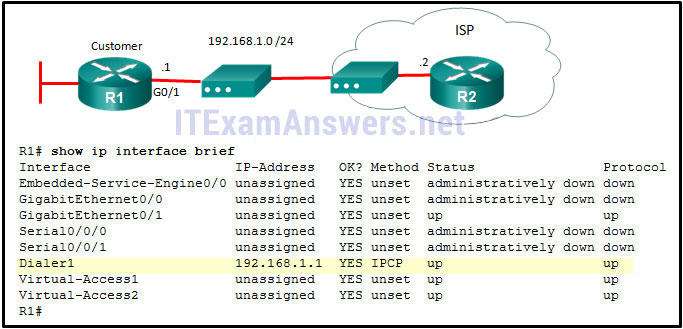
- that the Dialer1 interface has been manually assigned an IP address
- that the Dialer1 interface is up and up
- that the Dialer1 interface has been assigned an IP address by the ISP router
- that the IP address on R1 G0/1 is in the same network range as the DSL modem
17. Which technology creates a mapping of public IP addresses for remote tunnel spokes in a DMVPN configuration?
- ARP
- NHRP
- NAT
- IPsec
18. What is the purpose of the generic routing encapsulation tunneling protocol?
- to provide packet level encryption of IP traffic between remote sites
- to manage the transportation of IP multicast and multiprotocol traffic between remote sites
- to support basic unencrypted IP tunneling using multivendor routers between remote sites
- to provide fixed flow-control mechanisms with IP tunneling between remote sites
19. Refer to the exhibit. What is used to exchange routing information between routers within each AS?
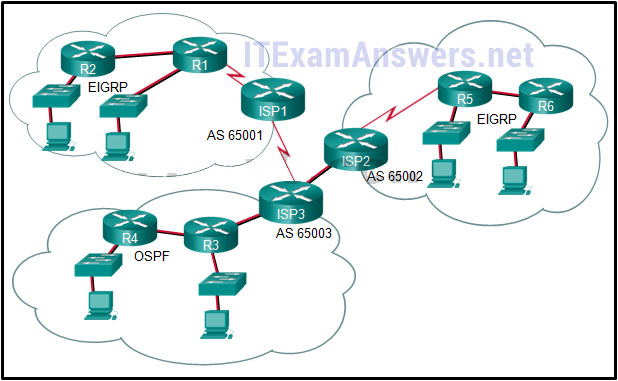
- static routing
- IGP routing protocols
- EGP routing protocols
- default routing
20. Which IPv4 address range covers all IP addresses that match the ACL filter specified by 172.16.2.0 with wildcard mask 0.0.1.255?
- 172.16.2.0 to 172.16.2.255
- 172.16.2.1 to 172.16.3.254
- 172.16.2.0 to 172.16.3.255
- 172.16.2.1 to 172.16.255.255
21. Refer to the exhibit. A named access list called chemistry_block has been written to prevent users on the Chemistry Network and public Internet from access to Records Server. All other users within the school should have access to this server. The list contains the following statements:
deny 172.16.102.0 0.0.0.255 172.16.104.252 0.0.0.0
permit 172.16.0.0 0.0.255.255 172.16.104.252 0.0.0.0
Which command sequence will place this list to meet these requirements?
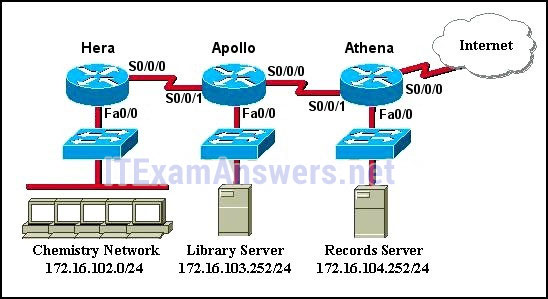
- Hera(config)# interface fa0/0
Hera(config-if)# ip access-group chemistry_block in - Hera(config)# interface s0/0/0
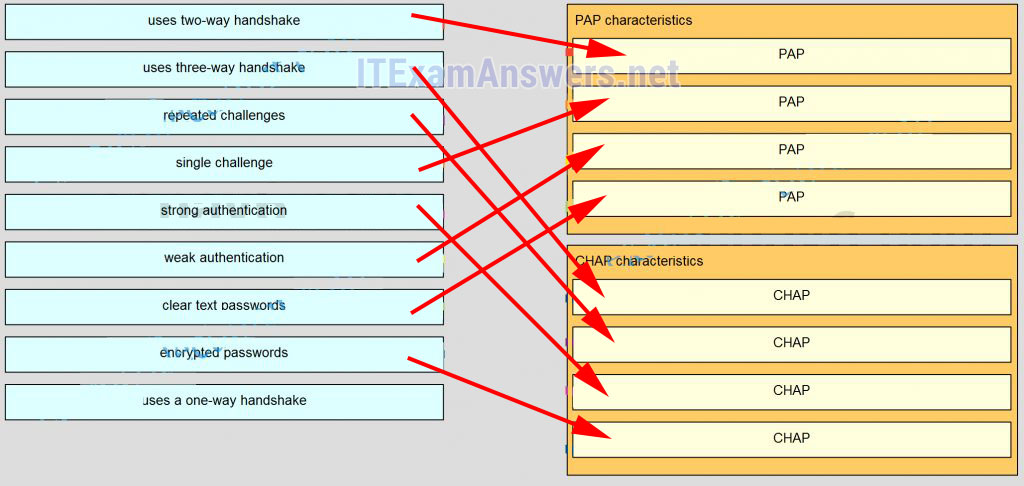
Hera(config-if)# ip access-group chemistry_block out - Apollo(config)# interface s0/0/0
Apollo(config-if)# ip access-group chemistry_block out - Apollo(config)# interface s0/0/1
Apollo(config-if)# ip access-group chemistry_block in - Athena(config)# interface fa0/0
Athena(config-if)# ip access-group chemistry_block out
22. What guideline is generally followed about the placement of extended access control lists?
- They should be placed as close as possible to the source of the traffic to be denied.
- They should be placed as close as possible to the destination of the traffic to be denied.
- They should be placed on the fastest interface available.
- They should be placed on the destination WAN link.
23. In the creation of an IPv6 ACL, what is the purpose of the implicit final command entries, permit icmp any any nd-na and permit icmp any any nd-ns?
- to allow IPv6 to MAC address resolution
- to allow forwarding of IPv6 multicast packets
- to allow automatic address configuration
- to allow forwarding of ICMPv6 packets
24. A network administrator is testing IPv6 connectivity to a web server. The network administrator does not want any other host to connect to the web server except for the one test computer. Which type of IPv6 ACL could be used for this situation?
- only a standard ACL
- a standard or extended ACL
- only an extended ACL
- an extended, named, or numbered ACL
- only a named ACL
25. Refer to the exhibit. The IPv6 access list LIMITED_ACCESS is applied on the S0/0/0 interface of R1 in the inbound direction. Which IPv6 packets from the ISP will be dropped by the ACL on R1?
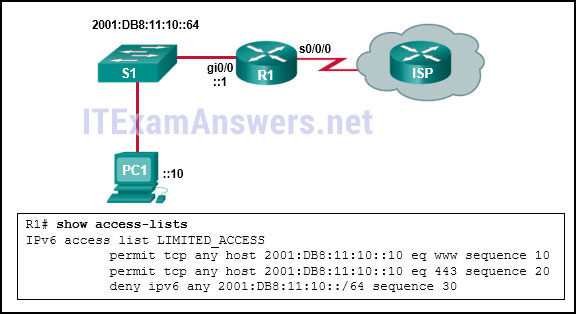
- HTTPS packets to PC1
- ICMPv6 packets that are destined to PC1
- packets that are destined to PC1 on port 80
- neighbor advertisements that are received from the ISP router
26. What is a secure configuration option for remote access to a network device?
- Configure SSH.
- Configure Telnet.
- Configure 802.1x.
- Configure an ACL and apply it to the VTY lines.
27. What protocol should be disabled to help mitigate VLAN attacks?
- DTP
- STP
- CDP
- ARP
28. Which term describes the role of a Cisco switch in the 802.1X port-based access control?
- agent
- supplicant
- authenticator
- authentication server
29. What two protocols are supported on Cisco devices for AAA communications? (Choose two.)
- VTP
- LLDP
- HSRP
- RADIUS
- TACACS+
30. In configuring SNMPv3, what is the purpose of creating an ACL?
- to define the source traffic that is allowed to create a VPN tunnel
- to define the type of traffic that is allowed on the management network
- to specify the source addresses allowed to access the SNMP agent
- to define the protocols allowed to be used for authentication and encryption
31. Refer to the exhibit. What feature does an SNMP manager need in order to be able to set a parameter on switch ACSw1?
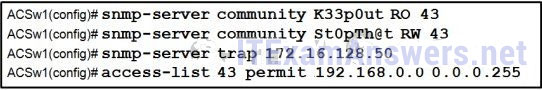
- a manager who is using an SNMP string of K44p0ut
- a manager who is using an Inform Request MIB
- a manager who is using host 192.168.0.5
- a manager who is using authPriv
32. Which Cisco feature sends copies of frames entering one port to a different port on the same switch in order to perform traffic analysis?
- CSA
- HIPS
- SPAN
- VLAN
33. What are two characteristics of video traffic? (Choose two.)
- Video traffic is more resilient to loss than voice traffic is.
- Video traffic is unpredictable and inconsistent.
- Video traffic latency should not exceed 400 ms.
- Video traffic requires a minimum of 30 kbs of bandwidth.
- Video traffic consumes less network resources than voice traffic consumes.
34. Which QoS mechanism allows delay-sensitive data, such as voice, to be sent first before packets in other queues are sent?
- CBWFQ
- FIFO
- LLQ
- FCFS
35. Refer to the exhibit. As traffic is forwarded out an egress interface with QoS treatment, which congestion avoidance technique is used?
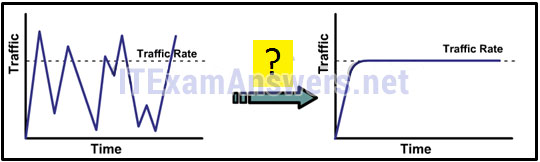
- traffic shaping
- weighted random early detection
- classification and marking
- traffic policing
36. Which type of QoS marking is applied to Ethernet frames?
- CoS
- ToS
- DSCP
- IP precedence
37. What is the function of a QoS trust boundary?
- A trust boundary identifies the location where traffic cannot be remarked.
- A trust boundary identifies which devices trust the marking on packets that enter a network.
- A trust boundary only allows traffic to enter if it has previously been marked.
- A trust boundary only allows traffic from trusted endpoints to enter the network.
38. A vibration sensor on an automated production line detects an unusual condition. The sensor communicates with a controller that automatically shuts down the line and activates an alarm. What type of communication does this scenario represent?
- machine-to-people
- machine-to-machine
- people-to-people
- people-to-machine
39. Which pillar of the Cisco IoT System allows data to be analyzed and managed at the location where it is generated?
- data analytics
- fog computing
- network connectivity
- application enhancement platform
40. Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?
- PaaS
- SaaS
- ITaaS
- IaaS
41. A data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?
- BYOD
- virtualization
- maintaining communication integrity
- online collaboration
42. What is used to pre-populate the adjacency table on Cisco devices that use CEF to process packets?
- the ARP table
- the routing table
- the FIB
- the DSP
43. What is the wildcard mask that is associated with the network 128.165.216.0/23?
- 0.0.0.255
- 0.0.1.254
- 0.0.1.255
- 0.0.1.0
- 0.0.0.254
44. What two features are added in SNMPv3 to address the weaknesses of previous versions of SNMP? (Choose two.)
- encryption
- authentication
- authorization with community string priority
- ACL management filtering
- bulk MIB objects retrieval
45. Which component of the ACI architecture translates application policies into network programming?
- the Nexus 9000 switch
- the Application Network Profile endpoints
- the Application Policy Infrastructure Controller
- the hypervisor
46. Which two pieces of information should be included in a logical topology diagram of a network? (Choose two.)
- device type
- OS/IOS version
- connection type
- interface identifier
- cable specification
- cable type and identifier
47. Which network performance statistics should be measured in order to verify SLA compliance?
- NAT translation statistics
- device CPU and memory utilization
- latency, jitter, and packet loss
- the number of error messages that are logged on the syslog server
48. Which feature sends simulated data across the network and measures performance between multiple network locations?
- LLDP
- IP SLA
- syslog
- SPAN
49. Which troubleshooting tool would a network administrator use to check the Layer 2 header of frames that are leaving a particular host?
- protocol analyzer
- baselining tool
- knowledge base
- CiscoView
50. Refer to the exhibit. A network administrator is troubleshooting the OSPF network. The 10.10.0.0/16 network is not showing up in the routing table of Router1. What is the probable cause of this problem?
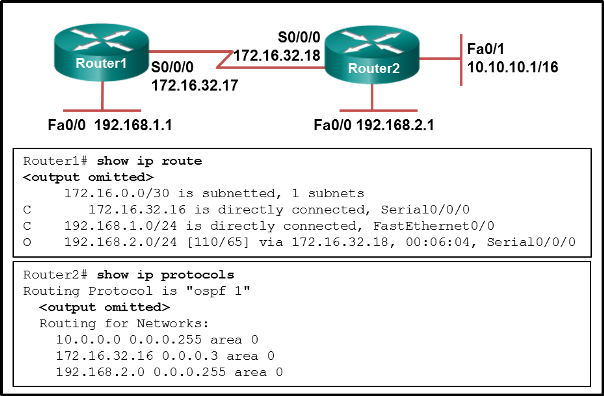
- The serial interface on Router2 is down.
- The OSPF process is not running on Router2.
- The OSPF process is configured incorrectly on Router1.
- There is an incorrect wildcard mask statement for network 10.10.0.0/16 on Router2.
51. Refer to the exhibit. A user turns on a PC after it is serviced and calls the help desk to report that the PC seems unable to reach the Internet. The technician asks the user to issue the arp –a and ipconfig commands. Based on the output, what are two possible causes of the problem? (Choose two.)
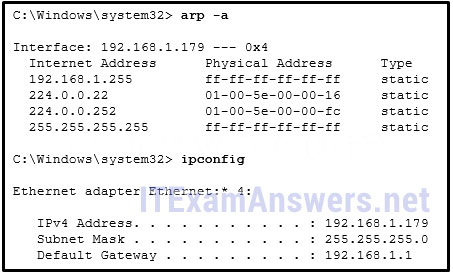
- The IP configuration is incorrect.
- The network cable is unplugged.
- The DNS server address is not configured.
- The subnet mask is configured incorrectly.
- The default gateway device cannot be contacted.
52. Which circumstance would result in an enterprise deciding to implement a corporate WAN?
- when its employees become distributed across many branch locations
- when the network will span multiple buildings
- when the number of employees exceeds the capacity of the LAN
- when the enterprise decides to secure its corporate LAN
52. Match QoS techniques with the description. (Not all options are used.)
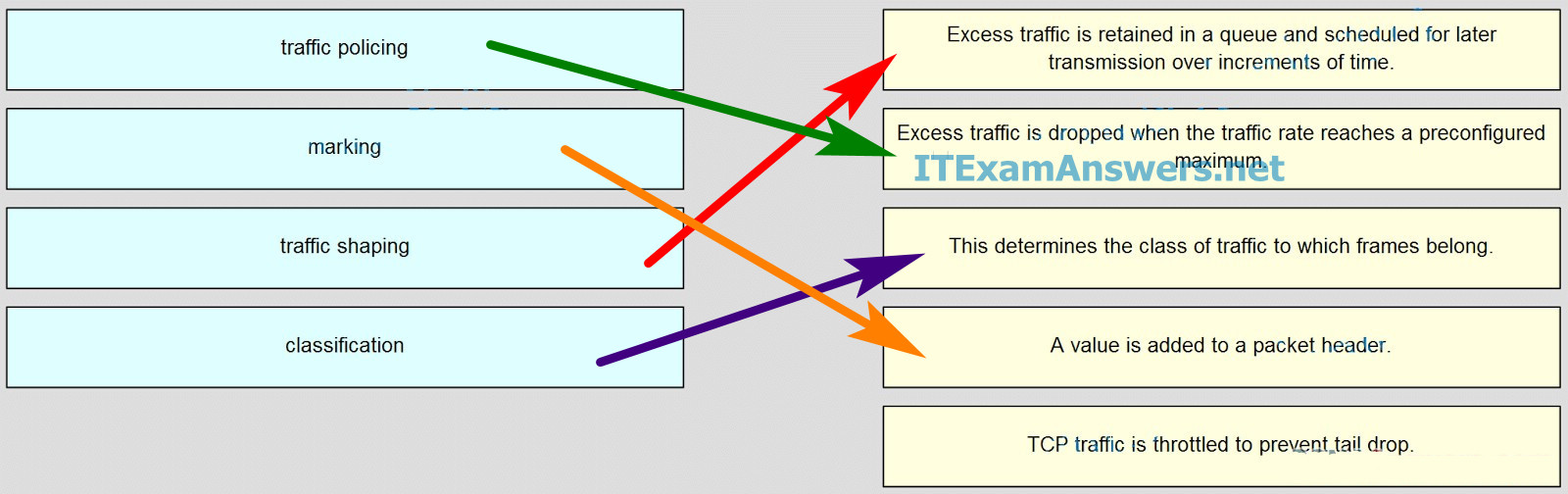
- Excess traffic is retained in a queue and scheduled for later transmission over increments of time –> traffic shaping
- Excess traffic is dropped when the traffic rate reaches a preconfigured maximum –> traffic policing
- This determines the class of traffic to which frames belong –> classification
- A value is added to a packer header –> marking
53. What are two types of WAN providers? (Choose two.)
- DNS servers
- satellite service
- web hosting service
- telephone company
- Internet search engine service
54. Which two types of devices are specific to WAN environments and are not found on a LAN? (Choose two.)
- access layer switch
- broadband modem
- core switch
- CSU/DSU
- distribution layer router
55. What is a feature of dense wavelength-division multiplexing (DWDM) technology?
- It replaces SONET and SDH technologies.
- It enables bidirectional communications over one strand of fiber.
- It provides Layer 3 support for long distance data communications.
- It provides a 10 Gb/s multiplexed signal over analog copper telephone lines.
56. What is a disadvantage of ATM compared to Frame Relay?
- less efficient
- lacks SVC support
- does not scale well to provide high speed WAN connections
- requires multiple interfaces on the edge router to support multiple VCs
57. Which WAN solution uses labels to identify the path in sending packets through a provider network?
- cable
- DSL
- Frame Relay
- MPLS
- VSAT
58. An intercity bus company wants to offer constant Internet connectivity to the users traveling on the buses. Which two types of WAN infrastructure would meet the requirements? (Choose two.)
- private infrastructure
- public infrastructure
- dedicated
- circuit-switched
- cellular
59. What device is needed at a central office to aggregate many digital subscriber lines from customers?
- CMTS
- DSLAM
- CSU/DSU
- access server
60. A corporation is searching for an easy and low cost solution to provide teleworkers with a secure connection to headquarters. Which solution should be selected?
- dial-up connection
- leased line connection
- site-to-site VPN over the Internet
- remote access VPN over the Internet
61. What is the maximum number of DS0 channels in a 1.544 Mbps T1 line?
- 2
- 12
- 24
- 28
62. Refer to the exhibit. What type of Layer 2 encapsulation will be used for RtrA connection D if it is left to the default and the router is a Cisco router?
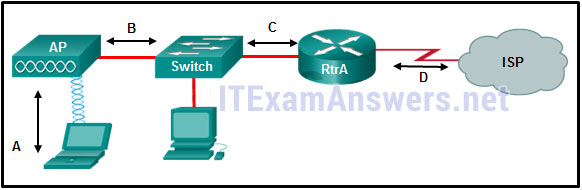
- Ethernet
- Frame Relay
- HDLC
- PPP
63. Which two functions are provided by the NCP during a PPP connection? (Choose two.)
- identifying fault conditions for the PPP link
- providing multilink capabilities over the PPP link
- bringing the network layer protocol or protocols up and down
- enhancing security by providing callback over PPP
- negotiating options for the IP protocol
- managing authentication of the peer routers of the PPP link
64. What PPP information will be displayed if a network engineer issues the show ppp multilink command on Cisco router?
- the link LCP and NCP status
- the queuing type on the link
- the IP addresses of the link interfaces
- the serial interfaces participating in the multilink
65. Refer to the exhibit. Which statement describes the status of the PPP connection?
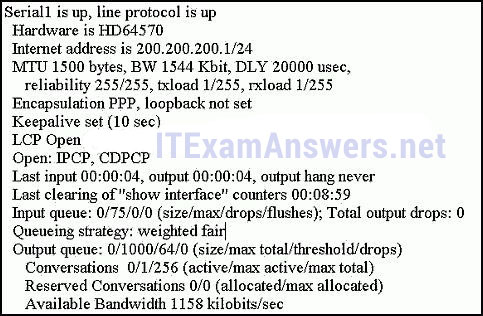
- Only the link-establishment phase completed successfully.
- Only the network-layer phase completed successfully.
- Neither the link-establishment phase nor the network-layer phase completed successfully.
- Both the link-establishment and network-layer phase completed successfully.
66. A network administrator is configuring a PPP link with the commands:
R1(config-if)# encapsulation ppp
R1(config-if)# ppp quality 70
What is the effect of these commands?
- The PPP link will be closed down if the link quality drops below 70 percent.
- The NCP will send a message to the sending device if the link usage reaches 70 percent.
- The LCP establishment phase will not start until the bandwidth reaches 70 percent or more.
- The PPP link will not be established if more than 30 percent of options cannot be accepted.
67. How does virtualization help with disaster recovery within a data center?
- Power is always provided.
- Less energy is consumed.
- Server provisioning is faster.
- Hardware does not have to be identical.
68. Which broadband solution is appropriate for a home user who needs a wired connection not limited by distance?
- cable
- DSL
- WiMax
- ADSL
69. What is the protocol that provides ISPs the ability to send PPP frames over DSL networks?
- PPPoE
- CHAP
- ADSL
- LTE
70. In software defined network architecture, what function is removed from network devices and performed by an SDN controller?
- control plane
- data plane
- security
- application policies
71. What would a network administrator expect the routing table of stub router R1 to look like if connectivity to the ISP was established via a PPPoE configuration?
- 192.168.1.0/32 is subnetted, 2 subnetted
C 192.168.1.1 is directly connected, Dialer1
C 192.168.1.2 is directly connected, Dialer2 - S* 0.0.0.0/0 is directly connected, Dialer1
- 192.168.1.0/32 is subnetted, 2 subnetted
C 192.168.1.1 is directly connected, Dialer - S* 0.0.0.0/0 is directly connected, Dialer1
192.168.1.0/32 is subnetted, 2 subnetted
C 192.168.1.1 is directly connected, Dialer1
C 192.168.1.2 is directly connected, Dialer1
72. What is a benefit of implementing a Dynamic Multipoint VPN network design?
- A DMVPN will use an encrypted session and does not require IPsec.
- A DMVPN uses a Layer 3 protocol, NHRP, to dynamically establish tunnels.
- A DMVPN will support remote peers by providing a mapping database of public IP addresses to each one.
- A DMVPN uses mGRE to create multiple GRE interfaces that each support a single VPN tunnel.
73. Which remote access implementation scenario will support the use of generic routing encapsulation tunneling?
- a mobile user who connects to a router ata central site
- a branch office that connects securely to a central site
- a mobile user who connects to a SOHO site
- a central site that connects to a SOHO site without encryption
74. Refer to the exhibit. All routers are successfully running the BGP routing protocol. How many routers must use EBGP in order to share routing information across the autonomous systems?
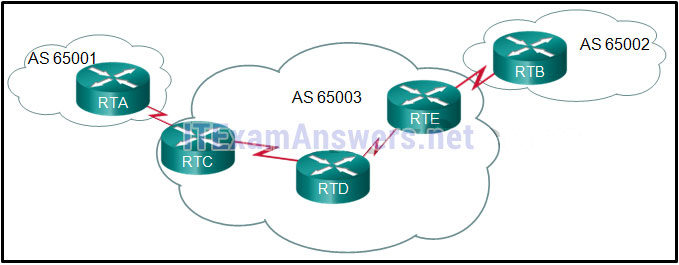
- 2
- 3
- 4
- 5
75. Which statement describes a characteristic of standard IPv4 ACLs?
- They are configured in the interface configuration mode.
- They filter traffic based on source IP addresses only.
- They can be created with a number but not with a name.
- They can be configured to filter traffic based on both source IP addresses and source ports.
76. Which three values or sets of values are included when creating an extended access control list entry? (Choose three.)
- access list number between 1 and 99
- access list number between 100 and 199
- default gateway address and wildcard mask
- destination address and wildcard mask
- source address and wildcard mask
- source subnet mask and wildcard mask
- destination subnet mask and wildcard mask
77. Refer to the exhibit. A router has an existing ACL that permits all traffic from the 172.16.0.0 network. The administrator attempts to add a new ACE to the ACL that denies packets from host 172.16.0.1 and receives the error message that is shown in the exhibit. What action can the administrator take to block packets from host 172.16.0.1 while still permitting all other traffic from the 172.16.0.0 network?
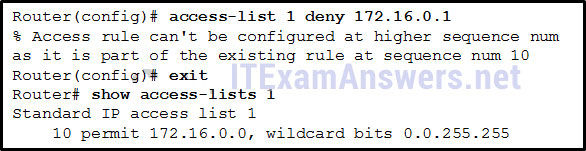
- Manually add the new deny ACE with a sequence number of 5.
- Manually add the new deny ACE with a sequence number of 15.
- Create a second access list denying the host and apply it to the same interface.
- Add a deny any any ACE to access-list 1.
78. Which three implicit access control entries are automatically added to the end of an IPv6 ACL? (Choose three.)
- deny ip any any
- deny ipv6 any any
- permit ipv6 any any
- deny icmp any any
- permit icmp any any nd-ns
- permit icmp any any nd-na
79. The computers used by the network administrators for a school are on the 10.7.0.0/27 network. Which two commands are needed at a minimum to apply an ACL that will ensure that only devices that are used by the network administrators will be allowed Telnet access to the routers? (Choose two.)
- access-class 5 in
- access-list 5 deny any
- access-list standard VTY
- permit 10.7.0.0 0.0.0.127
- access-list 5 permit 10.7.0.0 0.0.0.31
- ip access-group 5 out
- ip access-group 5 in
80. A network administrator is adding ACLs to a new IPv6 multirouter environment. Which IPv6 ACE is automatically added implicitly at the end of an ACL so that two adjacent routers can discover each other?
- permit ip any any
- permit ip any host ip_address
- permit icmp any any nd-na
- deny ip any any
81. What would be the primary reason an attacker would launch a MAC address overflow attack?
- so that the switch stops forwarding traffic
- so that legitimate hosts cannot obtain a MAC address
- so that the attacker can see frames that are destined for other hosts
- so that the attacker can execute arbitrary code on the switch
82. What are three of the six core components in the Cisco IoT system? (Choose three.)
- fog computing
- wearable technologies
- data analytics
- robot guides
- cyber and physical security
- smart bandages
83. What security countermeasure is effective for preventing CAM table overflow attacks?
- port security
- DHCP snooping
- IP source guard
- Dynamic ARP Inspection
84. Which SNMP feature provides a solution to the main disadvantage of SNMP polling?
- SNMP set messages
- SNMP trap messages
- SNMP get messages
- SNMP community strings
85. When SNMPv1 or SNMPv2 is being used, which feature provides secure access to MIB objects?
- packet encryption
- message integrity
- community strings
- source validationfeatures
86. What two are added in SNMPv3 to address the weaknesses of previous versions of SNMP? (Choose two.)
- bulk MIB objects retrieval
- encryption
- authorization with community string priority
- authentication
- ACL management filtering
87. Which queuing mechanism supports user-defined traffic classes?
- FIFO
- CBWFQ
- WFQ
- FCFS
88. Which field is used to mark Layer 2 Ethernet frames for QoS treatment?
- Type of Service field
- Traffic Class field
- Priority field
- Version field
89. What is an example of cloud computing?
- a continuous interaction between people, processes, data, and things
- a service that offers on-demand access to shared resources
- a network infrastructure that spans a large geographic area
- an architectural style of the World Wide Web
90. Which type of resources are required for a Type 1 hypervisor?
- a host operating system
- a server running VMware Fusion
- a management console
- a dedicated VLAN
91. A network technician made a configuration change on the core router in order to solve a problem. However, the problem is not solved. Which step should the technician take next?
- Gather symptoms.
- Isolate the problem.
- Restore the previous configuration.
- Implement the next possible corrective action.
92. A user reports that when the corporate web page URL is entered on a web browser, an error message indicates that the page cannot be displayed. The help-desk technician asks the user to enter the IP address of the web server to see if the page can be displayed. Which troubleshooting method is being used by the technician?
- top-down
- bottom-up
- substitution
- divide-and-conquer
93. What is a primary function of the Cisco IOS IP Service Level Agreements feature?
- to detect potential network attacks
- to provide network connectivity for customers
- to adjust network device configurations to avoid congestion
- to measure network performance and discover a network failure as early as possible
94. Which IOS log message level indicates the highest severity level?
- level 0
- level 1
- level 4
- level 7
95. Which symptom is an example of network issues at the network layer?
- A misconfigured firewall blocks traffic to a file server.
- There are too many invalid frames transmitted in the network.
- Neighbor adjacency is formed with some routers, but not all routers.
- A web server cannot be reached by its domain name, but can be reached via its IP address.
96. Refer to the exhibit. H1 can only ping H2, H3, and the Fa0/0 interface of router R1. H2 and H3 can ping H4 and H5. Why might H1 not be able to successfully ping H4 and H5?
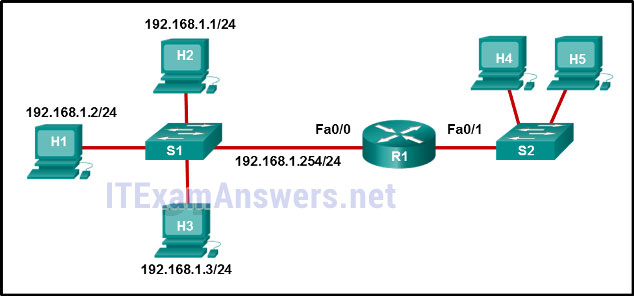
- Router R1 does not have a route to the destination network.
- Switch S1 does not have an IP address configured.
- The link between router R1 and switch S2 has failed.
- Host H1 does not have a default gateway configured.
- Hosts H4 and H5 are members of a different VLAN than host H1.
97. Refer to the exhibit. On the basis of the output, which two statements about network connectivity are correct? (Choose two.)
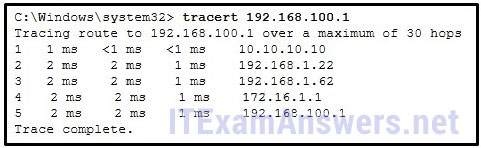
- There is connectivity between this device and the device at 192.168.100.1.
- The connectivity between these two hosts allows for videoconferencing calls.
- There are 4 hops between this device and the device at 192.168.100.1.
- The average transmission time between the two hosts is 2 milliseconds.
- This host does not have a default gateway configured.
98. Fill in the blanks. Use dotted decimal format.
The wildcard mask that is associated with 128.165.216.0/23 is 0.0.1.255
99. Match the characteristic to the appropriate authentication protocol. (Not all options are used.)
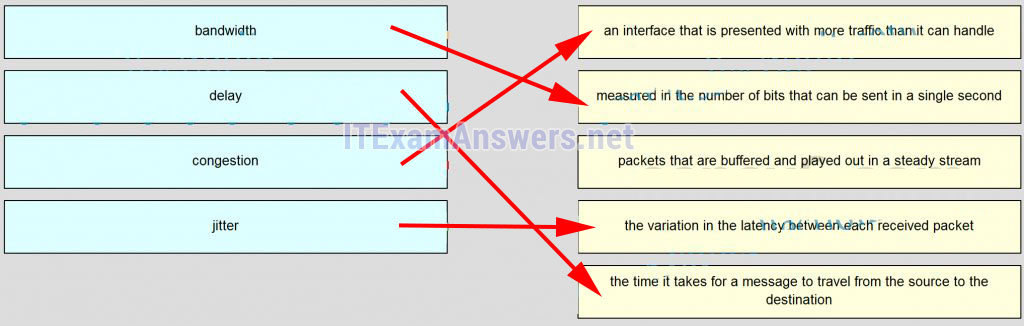
100. Match the term to the description. (Not all options are used.)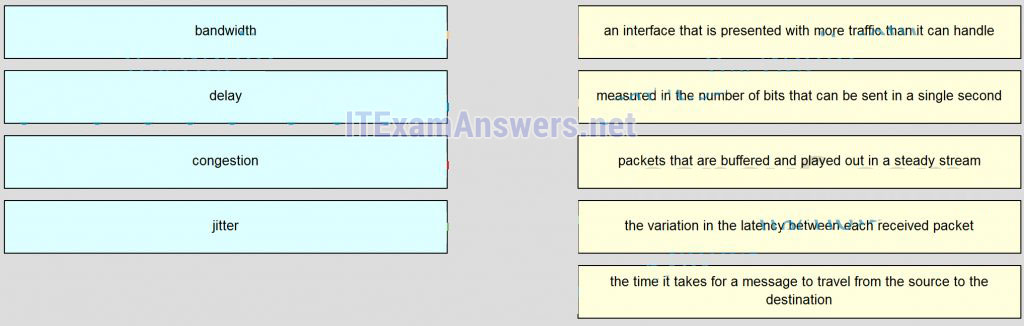
101. What is a primary difference between a company LAN and the WAN services that it uses?
- The company must subscribe to an external WAN service provider.
- The company has direct control over its WAN links but not over its LAN.
- Each LAN has a specified demarcation point to clearly separate access layer and distribution layer equipment.
- The LAN may use a number of different network access layer standards whereas the WAN will use only one standard.
102. To which two layers of the OSI model do WAN technologies provide services? (Choose two.)
- network layer
- session layer
- physical layer
- transport layer
- data link layer
- presentation layer
103. Which two technologies are private WAN technologies? (Choose two.)
- cable
- Frame Relay
- DSL
- ATM
- cellular
104. Which WAN technology can switch any type of payload based on labels?
- PSTN
- DSL
- MPLS
- T1/E1
105. What technology can be used to create a private WAN via satellite communications?
- VPN
- 3G/4G cellular
- dialup
- VSAT
- WiMAX
106. Which public WAN access technology utilizes copper telephone lines to provide access to subscribers that are multiplexed into a single T3 link connection?
- ISDN
- DSL
- dialup
- cable
107. How many DS0 channels are bounded to produce a 1.544 Mb/s DS1 line?
- 2
- 12
- 24
- 28
108. Refer to the exhibit. Communication between two peers has failed. Based on the output that is shown, what is the most likely cause?
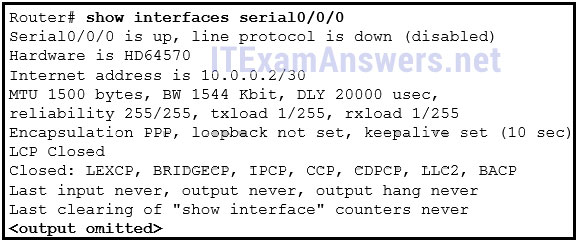
- interface reset
- unplugged cable
- improper cable type
- PPP issue
109. Refer to the exhibit. Which type of Layer 2 encapsulation used for connection D requires Cisco routers?
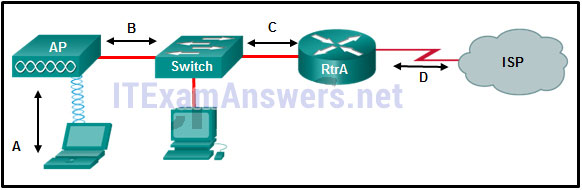
- Ethernet
- PPPoE
- HDLC
- PP
110. Which three statements are true about PPP? (Choose three.)
- PPP can use synchronous and asynchronous circuits.
- PPP can only be used between two Cisco devices.
- PPP carries packets from several network layer protocols in LCPs.
- PPP uses LCPs to establish, configure, and test the data-link connection.
- PPP uses LCPs to agree on format options such as authentication, compression, and error detection.
111. A network administrator is evaluating authentication protocols for a PPP link. Which three factors might lead to the selection of CHAP over PAP as the authentication protocol? (Choose three.)
- establishes identities with a two-way handshake
- uses a three-way authentication periodically during the session to reconfirm identities
- control by the remote host of the frequency and timing of login events
- transmits login information in encrypted format
- uses an unpredictable variable challenge value to prevent playback attacks
- makes authorized network administrator intervention a requirement to establish each session
112. Which cellular or mobile wireless standard is considered a fourth generation technology?
- LTE
- GSM
- CDMA
- UMTS
113. A company is looking for the least expensive broadband solution that provides at least 10 Mb/s download speed. The company is located 5 miles from the nearest provider. Which broadband solution would be appropriate?
- satellite
- DSL
- WiMax
- cable
114. Which technology can ISPs use to periodically challenge broadband customers over DSL networks with PPPoE?
- PAP
- CHAP
- HDLC
- Frame
- Relay
115. What are the three core components of the Cisco ACI architecture? (Choose three.)
- Application Network Profile
- Application Policy Infrastructure Controller
- Cisco Nexus Switches
- Microsoft hypervisor
- Cisco Information Server
- Virtual Security Gateway
116. Which statement describes a feature of site-to-site VPNs?
- The VPN connection is not statically defined.
- VPN client software is installed on each host.
- Internal hosts send normal, unencapsulated packets.
- Individual hosts can enable and disable the VPN connection.
117. What are three features of a GRE tunnel? (Choose three.)
- creates nonsecure tunnels between remote sites
- transports multiple Layer 3 protocols
- creates additional packet overhead
- uses RSA signatures to authenticate peeers
- provides encryption to keep VPN traffic confidential
- supports hosts as GRE tunnel endpoints by installing Cisco VPN client software
118. Refer to the exhibit. What two commands are needed to complete the GRE tunnel configuration on router R1? (Choose two.)
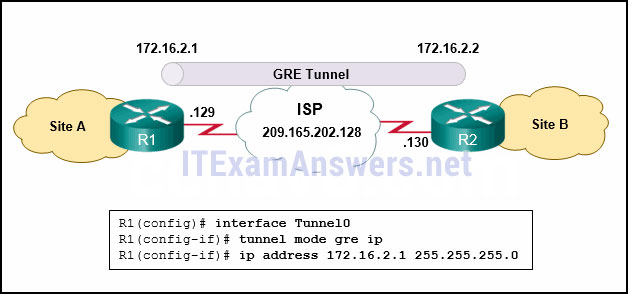
- R1(config-if)# tunnel source 209.165.202.129
- R1(config-if)# tunnel source 172.16.2.1
- R1(config-if)# tunnel destination 206.165.202.130
- R1(config-if)# tunnel destination 172.16.2.2
- R1(config-if)# tunnel source 209.165.202.130
- R1(config-if)# tunnel destination 206.165.202.129
119. What does BGP use to exchange routing updates with neighbors?
- TCP connections
- area numbers
- group identification numbers
- hellos
120. Refer to the exhibit. The network administrator that has the IP address of 10.0.70.23/25 needs to have access to the corporate FTP server (10.0.54.5/28). The FTP server is also a web server that is accessible to all internal employees on networks within the 10.x.x.x address. No other traffic should be allowed to this server. Which extended ACL would be used to filter this traffic, and how would this ACL be applied? (Choose two.)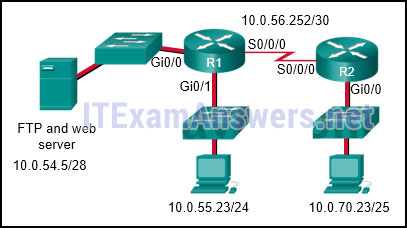
- access-list 105 permit ip host 10.0.70.23 host 10.0.54.5
access-list 105 permit tcp any host 10.0.54.5 eq www
access-list 105 permit ip any anyaccess-list 105 permit tcp host 10.0.54.5 any eq www
access-list 105 permit tcp host 10.0.70.23 host 10.0.54.5 eq 20
access-list 105 permit tcp host 10.0.70.23 host 10.0.54.5 eq 21 - access-list 105 permit tcp host 10.0.70.23 host 10.0.54.5 eq 20
access-list 105 permit tcp host 10.0.70.23 host 10.0.54.5 eq 21
access-list 105 permit tcp 10.0.0.0 0.255.255.255 host 10.0.54.5 eq www
access-list 105 deny ip any host 10.0.54.5
access-list 105 permit ip any any - R2(config)# interface gi0/0
R2(config-if)# ip access-group 105 in - R1(config)# interface gi0/0
R1(config-if)# ip access-group 105 out - R1(config)# interface s0/0/0
R1(config-if)# ip access-group 105 out
121. Refer to the exhibit. What can be determined from this output?
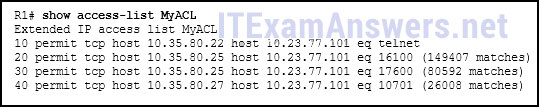
- The ACL is missing the deny ip any any ACE.
- Because there are no matches for line 10, the ACL is not working.
- The ACL is only monitoring traffic destined for 10.23.77.101 from three specific hosts.
- The router has not had any Telnet packets from 10.35.80.22 that are destined for 10.23.77.101.
122. What is the only type of ACL available for IPv6?
- named standard
- named extended
- numbered standard
- numbered extended
123. Which IPv6 ACL command entry will permit traffic from any host to an SMTP server on network 2001:DB8:10:10::/64?
- permit tcp any host 2001:DB8:10:10::100 eq 25
- permit tcp host 2001:DB8:10:10::100 any eq 25
- permit tcp any host 2001:DB8:10:10::100 eq 23
- permit tcp host 2001:DB8:10:10::100 any eq 23
124. Refer to the exhibit. Considering how packets are processed on a router that is configured with ACLs, what is the correct order of the statements?
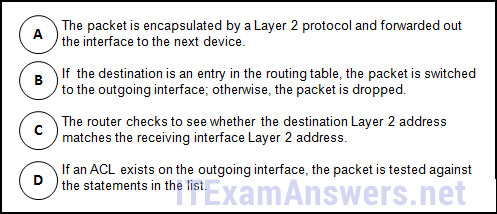
- C-B-A-D
- A-B-C-D
- C-B-D-A
- B-A-D-C
- D-A-C-B
125. Which two hypervisors are suitable to support virtual machines in a data center? (Choose two.)
- Virtual PC
- VMware Fusion
- VMware ESX/ESXi
- Oracle VM VirtualBox
- Microsoft Hyper-V 2012
126. How can DHCP spoofing attacks be mitigated?
- by disabling DTP negotiations on nontrunking ports
- by implementing DHCP snooping on trusted ports
- by implementing port security
- by the application of the ip verify source command to untrusted ports
127. What action can a network administrator take to help mitigate the threat of VLAN attacks?
- Disable VTP.
- Configure all switch ports to be members of VLAN 1.
- Disable automatic trunking negotiation.
- Enable PortFast on all switch ports.
128. Which SNMP message type informs the network management system (NMS) immediately of certain specified events?
- GET request
- SET request
- GET response
- Trap
129. Refer to the exhibit. A SNMP manager is using the community string of snmpenable and is configured with the IP address 172.16.10.1. The SNMP manager is unable to read configuration variables on the R1 SNMP agent. What could be the problem?
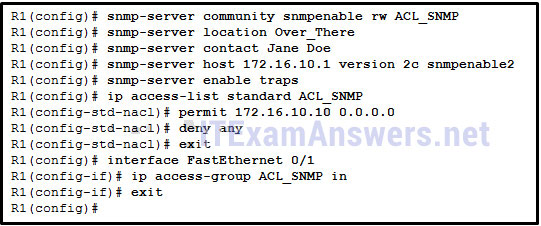
- The SNMP agent is not configured for read-only access.
- The community of snmpenable2 is incorrectly configured on the SNMP agent.
- The ACL is not permitting access by the SNMP manager.
- The incorrect community string is configured on the SNMP manager.
130. Refer to the exhibit. Which SNMP authentication password must be used by the member of the ADMIN group that is configured on router R1?
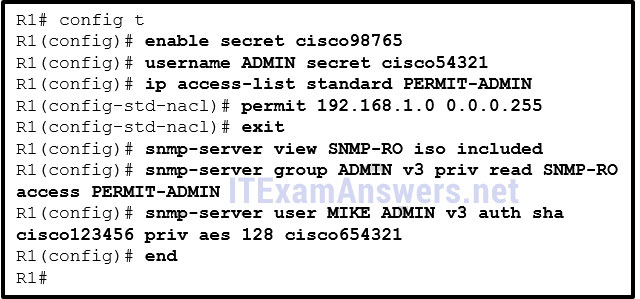
- cisco54321
- cisco98765
- cisco123456
- cisco654321
131. A network administrator has noticed an unusual amount of traffic being received on a switch port that is connected to a college classroom computer. Which tool would the administrator use to make the suspicious traffic available for analysis at the college data center?
- RSPAN
- TACACS+
- 802.1X
- DHCP snooping
- SNMP
132. What network monitoring tool copies traffic moving through one switch port, and sends the copied traffic to another switch port for analysis?
- 802.1
- XSNMP
- SPAN
- syslog
133. Voice packets are being received in a continuous stream by an IP phone, but because of network congestion the delay between each packet varies and is causing broken conversations. What term describes the cause of this condition?
- buffering
- latency
- queuing
- jitter
134. What mechanism compensates for jitter in an audio stream by buffering packets and then replaying them outbound in a steady stream?
- digital
- signal
- processor
- playout delay buffer
- voice codecWFQ
135. Which type of network traffic cannot be managed using congestion avoidance tools?
- TCP
- UDP
- IP
- ICMP
136. A network administrator has moved the company intranet web server from a switch port to a dedicated router interface. How can the administrator determine how this change has affected performance and availability on the company intranet?
- Conduct a performance test and compare with the baseline that was established previously.
- Determine performance on the intranet by monitoring load times of company web pages from remote sites.
- Interview departmental administrative assistants to determine if web pages are loading more quickly.
- Compare the hit counts on the company web server for the current week to the values that were recorded in previous weeks.
137. In which stage of the troubleshooting process would ownership be researched and documented?
- Gather symptoms.
- Implement corrective action.
- Isolate the problem.
- Update the user and document the problem.
138. Which troubleshooting approach is more appropriate for a seasoned network administrator rather than a less-experienced network administrator?
- a less-structured approach based on an educated guess
- an approach comparing working and nonworking components to spot significant differences
- a structured approach starting with the physical layer and moving up through the layers of the OSI model until the cause of the problem is identified
- an approach that starts with the end-user applications and moves down through the layers of the OSI model until the cause of the problem has been identified
139. A router has been configured to use simulated network traffic in order to monitor the network performance between the router and a distant network device. Which command would display the results of this analysis?
- show ip route
- showip protocols
- show ip sla statistics
- show monitor
140. Which type of tool would an administrator use to capture packets that are going to and from a particular device?
- NMS tool
- knowledge base
- baselining tool
- protocol analyzer
141. Refer to the exhibit. Which two statements describe the results of entering these commands? (Choose two.)
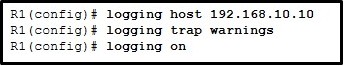
- R1 will send system messages of levels 0 (emergencies) to level 4 (warnings) to a server.
- R1 will not send critical system messages to the server until the command debug all is entered.
- R1 will reset all the warnings to clear the log.R1 will output the system messages to the local RAM.
- The syslog server has the IPv4 address 192.168.10.10.
142. Refer to the exhibit. A network administrator discovers that host A is having trouble with Internet connectivity, but the server farm has full connectivity. In addition, host A has full connectivity to the server farm. What is a possible cause of this problem?
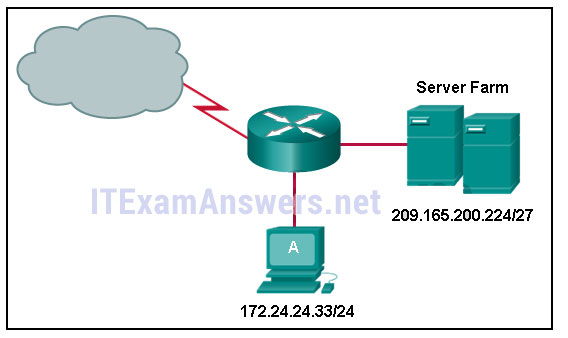
- The router has an incorrect gateway.
- Host A has an overlapping network address.
- Host A has an incorrect default gateway configured.
- Host A has an incorrect subnet mask.
- NAT is required for the host A network.
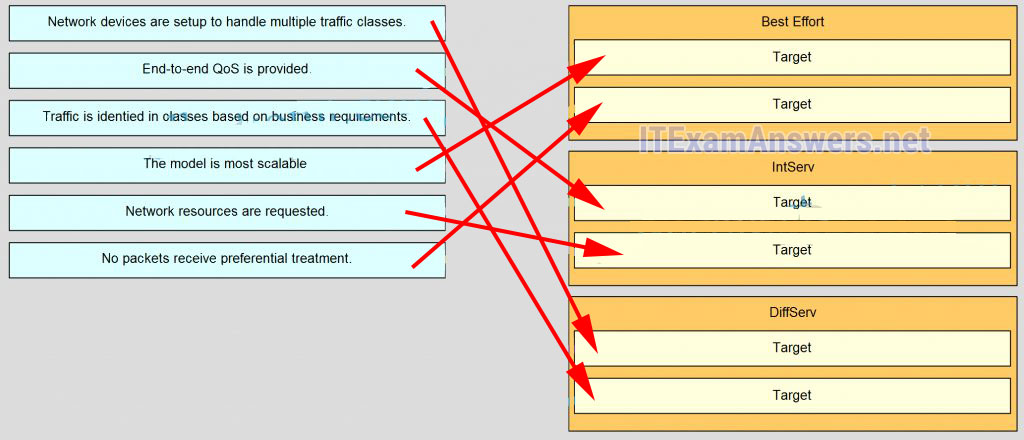
143. Match the operation to the appropriate QoS model.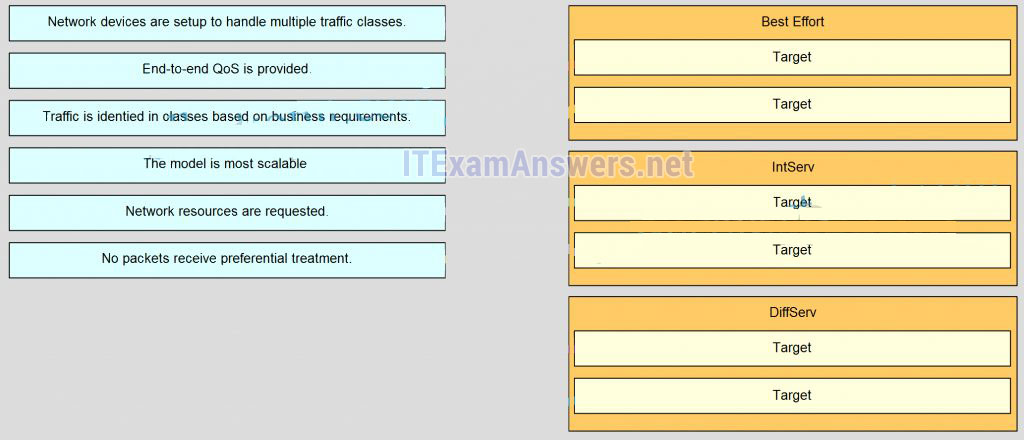
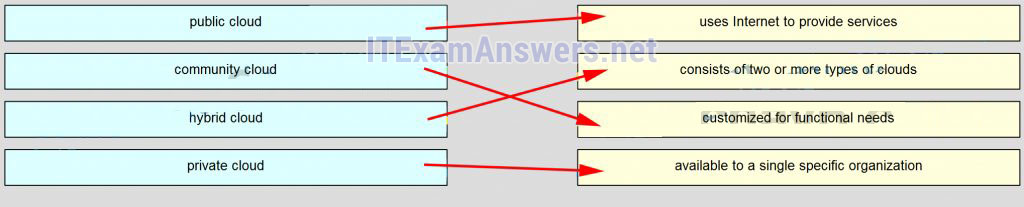
144. Match the cloud model with the description.
145. Match QoS techniques with the description. (Not all options are used.)
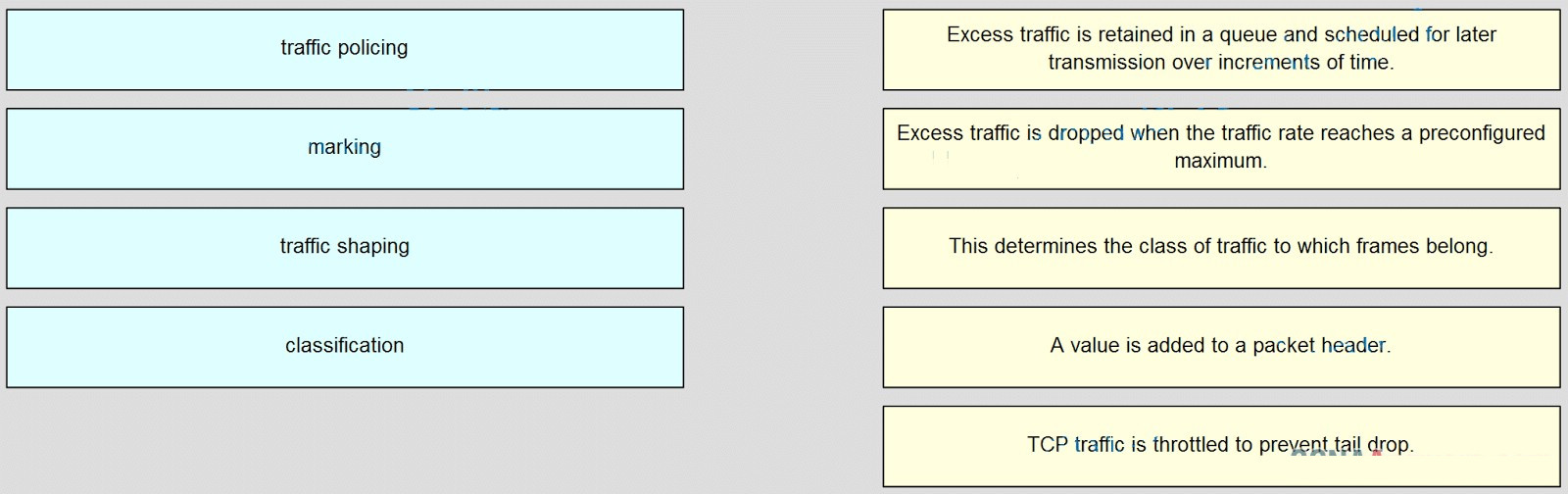
- traffic policing –> Excess traffic is dropped when the traffic rate reaches a preconfigured maximum.
- marking –> A value is added to a packet header.
- traffic shaping –> Excess traffic is retained in a queue and scheduled for later transmission over increments of time.
- classification –> This determines the class of traffic to which frames belong.
- empty –> TCP traffic is throttled to prevent tail drop.
Version 5:
146. Which two factors allow businesses to safely communicate and perform transactions using the Internet? (Choose two.)
- security
- addressing
- privacy
- WAN technology
- bandwidth
147. Which two statements about DSL are true? (Choose two.)
- users are on a shared medium
- uses RF signal transmission
- local loop can be up to 3.5 miles (5.5km)
- physical and data link layers are defined by DOCSIS
- user connections are aggregated at a DSLAM located at the CO
148. Which two statements are true regarding a PPP connection between two Cisco routers? (Choose two.)
- LCP tests the quality of the link.
- LCP manages compression on the link.
- Only a single NCP is allowed between the two routers.
- NCP terminates the link when data exchange is complete.
- With CHAP authentication, the routers exchange plain text passwords.
149. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP can only supply five public IP addresses for this network. What technology can the administrator use to accomplish this task?
- classful subnetting
- variable length subnet masks
- classless interdomain routing
- port-based Network Address Translation
150. Refer to the exhibit. An administrator is configuring NAT to provide Internet access to the inside network. After the configuration is completed, users are unable to access the Internet. What is the cause of the problem?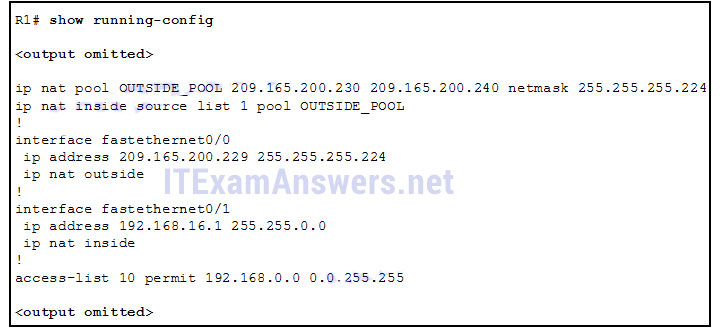
- The NAT pool is using an invalid address range.
- The inside and outside interfaces are backwards.
- The ACL is referencing the wrong network address.
- The NAT inside source command is referring to the wrong ACL.
151. What is the expected behavior of an ADSL service?
- The download rate is faster than the upload rate.
- The upload rate is faster than the download rate.
- The download and upload rates are the same.
- The user can select the upload and download rates based on need.
152. A network administrator is troubleshooting the dynamic NAT that is configured on router R2. Which command can the administrator use to see the total number of active NAT translations and the number of addresses that are allocated from the NAT pool?
- R2# show ip nat statistics
- R2# show ip nat translations
- R2# show running-config
- R2# clear ip nat translation
153. Which type of traffic would most likely have problems when passing through a NAT device?
- Telnet
- IPsec
- HTTP
- ICMP
- DNS
154. Refer to the exhibit. The inside local IP address of PC-A is 192.168.0.200. What will be the inside global address of packets from PC-A after they are translated by R1?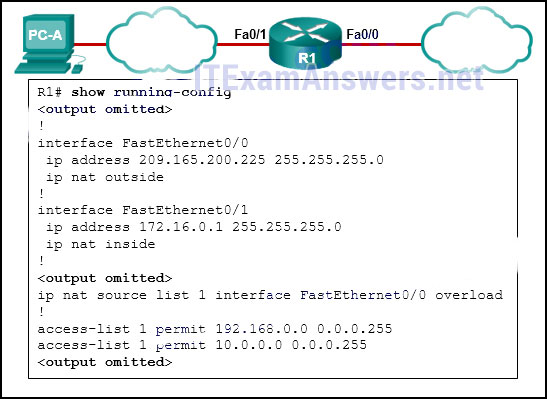
- 10.0.0.1
- 172.16.0.1
- 192.168.0.1
- 192.168.0.200
- 209.165.200.225
155. Refer to the exhibit. What kind of NAT is being configured on R1?![]()
- PAT
- dynamic NAT
- NAT overload
- port forwarding
156. What benefit does NAT64 provide?
- It allows sites to use private IPv6 addresses and translates them to global IPv6 addresses.
- It allows sites to connect multiple IPv4 hosts to the Internet via the use of a single public IPv4 address.
- It allows sites to connect IPv6 hosts to an IPv4 network by translating the IPv6 addresses to IPv4 addresses.
- It allows sites to use private IPv4 addresses, and thus hides the internal addressing structure from hosts on public IPv4 networks.
157. What are three benefits of using Frame Relay for WAN connectivity? (Choose three.)
- QoS support using the IP precedence field
- one physical interface that can be used for several circuits
- integrated encryption
- mature technology
- reasonable cost
- seamless direct connectivity to an Ethernet LAN
158. The DLCI number assigned to a Frame Relay circuit is to be manually added on a point-to-point link. Which three subinterface commands could be used to complete the configuration? (Choose three.)
- bandwidth kilobits
- encapsulation frame-relay
- frame-relay interface-dlci dlci
- frame-relay map ip ip-address dlci
- frame-relay map ip ip-address dlci broadcast
- ip address ip-address mask
- no shutdown
159. Which command can be used to check the information about congestion on a Frame Relay link?
- show frame-relay pvc
- show frame-relay lmi
- show interfaces
- show frame-relay map
160. Refer to the exhibit. A network administrator has implemented the configuration in the displayed output. What is missing from the configuration that would be preventing OSPF routing updates from passing to the Frame Relay service provider?
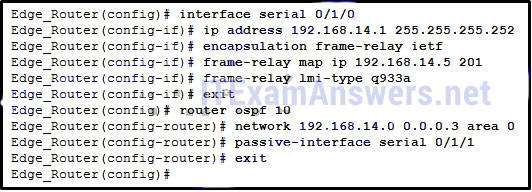
- The passive-interface command has not been issued on interface serial 0/1/0.
- The broadcast keyword has not been issued.
- The directly connected neighbor should have been identified by using static mapping.
- The command to disable split horizon has not been issued.
161. What is a characteristic of Frame Relay that allows customer data transmissions to dynamically “burst” over their CIR for short periods of time?
- The combination of LMI status messages and Inverse ARP messages enables the CIR to be exceeded.
- The physical circuits of the Frame Relay network are shared between subscribers and there may be times when unused bandwidth is available.
- Bursting is enabled by the configuration of multiple subinterfaces on one physical interface.
- BECN and FECN messages notify the router that the CIR can be exceeded.
162. Which broadband technology would be best for a small office that requires fast upstream connections?
- DSL
- fiber-to-the-home
- cable
- WiMax
163. Which technology requires the use of PPPoE to provide PPP connections to customers?
- dialup analog modem
- dialup ISDN modem
- DSL
- T1
164. Why is it useful to categorize networks by size when discussing network design?
- Knowing the number of connected devices will define how many multilayer switches will be necessary at the core layer.
- Knowing the number of connected devices will define how many additional layers will be added to the three-tier hierarchical network design.
- A high-level redundancy at the access layer may be better implemented if the number of connected devices is known.
- The complexity of networking infrastructure will vary according to the number of connected devices.
165. A company connects to one ISP via multiple connections. What is the name given to this type of connection?
- single-homed
- multihomed
- dual-multihomed
- dual-homed
166. What is one advantage to designing networks in building block fashion for large companies?
- failure isolation
- increased network access time
- coarse security control
- fewer required physical resources
167. Which network module maintains the resources that employees, partners, and customers rely on to effectively create, collaborate, and interact with information?
- access-distribution
- services
- data center
- enterprise edge
168. A group of Windows PCs in a new subnet has been added to an Ethernet network. When testing the connectivity, a technician finds that these PCs can access local network resources but not the Internet resources. To troubleshoot the problem, the technician wants to initially confirm the IP address and DNS configurations on the PCs, and also verify connectivity to the local router. Which three Windows CLI commands and utilities will provide the necessary information? (Choose three.)
- arp -a
- ipconfig
- nslookup
- ping
- telnet
- tracert
- netsh interface ipv6 show neighbor
169. A team of engineers has identified a solution to a significant network problem. The proposed solution is likely to affect critical network infrastructure components. What should the team follow while implementing the solution to avoid interfering with other processes and infrastructure?
- change-control procedures
- one of the layered troubleshooting approaches
- knowledge base guidelines
- syslog messages and reports
170. Which two specialized troubleshooting tools can monitor the amount of traffic that passes through a switch? (Choose two.)
- TDR
- digital multimeter
- NAM
- portable network analyzer
- DTX cable analyzer
171. Which statement is a characteristic of SNMP MIBs?
- The MIB organizes variables in a flat manner.
- The SNMP agent uses the SNMP manager to access information within the MIB.
- The NMS must have access to the MIB in order for SNMP to operate properly.
- The MIB structure for a given device includes only variables that are specific to that device or vendor.
172. Refer to the exhibit. Router R1 was configured by a network administrator to use SNMP version 2. The following commands were issued:
R1(config)# snmp-server community batonaug ro SNMP_ACL
R1(config)# snmp-server contact Wayne World
R1(config)# snmp-server host 192.168.1.3 version 2c batonaug
R1(config)# ip access-list standard SNMP_ACL
R1(config-std-nacl)# permit 192.168.10.3
Why is the administrator not able to get any information from R1?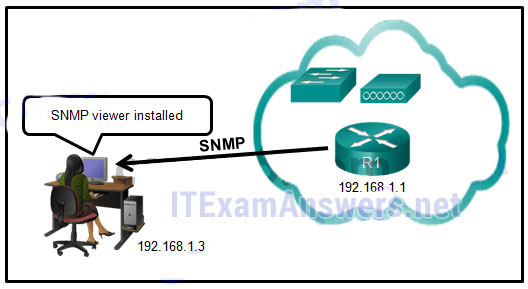
- The snmp-server enable traps command is missing.
- The snmp-server community command needs to include the rw keyword.
- There is a problem with the ACL configuration.
- The snmp-server location command is missing.
173. What is used as the default event logging destination for Cisco routers and switches?
- terminal line
- syslog server
- console line
- workstation
174. In the data gathering process, which type of device will listen for traffic, but only gather traffic statistics?
- NMS
- syslog server
- NetFlow collector
- SNMP agent
175. Which three flows associated with consumer applications are supported by NetFlow collectors? (Choose three.)
- bandwidth regulation
- accounting
- billing
- quality of service
- error correction
- network monitoring
176. Which algorithm is considered insecure for use in IPsec encryption?
- 3DES
- AES
- RSA
- SHA-1
177. Two corporations have just completed a merger. The network engineer has been asked to connect the two corporate networks without the expense of leased lines. Which solution would be the most cost effective method of providing a proper and secure connection between the two corporate networks?
- Cisco AnyConnect Secure Mobility Client with SSL
- Cisco Secure Mobility Clientless SSL VPN
- Frame Relay
- remote access VPN using IPsec
- site-to-site VPN
178. Refer to the exhibit. Which IP address is configured on the physical interface of the CORP router?
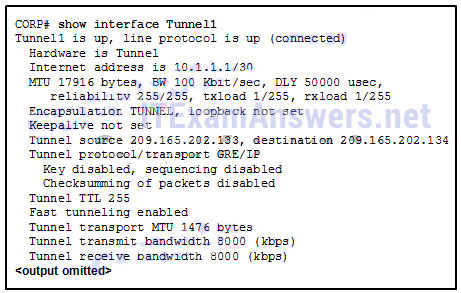
- 10.1.1.1
- 10.1.1.2
- 209.165.202.133
- 209.165.202.134
179. What are three characteristics of the generic routing encapsulation (GRE) protocol? (Choose three.)
- GRE tunnels support multicast traffic.
- By default, GRE does not include any flow control mechanisms.
- Developed by the IETF, GRE is a secure tunneling protocol that was designed for Cisco routers.
- GRE uses AES for encryption unless otherwise specified.
- GRE creates additional overhead for packets that are traveling through the VPN.
- GRE provides encapsulation for a single protocol type that is traveling through the VPN.
180. Which two statements describe remote access VPNs? (Choose two.)
- Remote access VPNs are used to connect entire networks, such as a branch office to headquarters.
- End users are not aware that VPNs exists.
- A leased line is required to implement remote access VPNs.
- Client software is usually required to be able to access the network.
- Remote access VPNs support the needs of telecommuters and mobile users.
181. Under which two categories of WAN connections does Frame Relay fit? (Choose two.)
- public infrastructure
- private infrastructure
- dedicated
- Internet
- packet-switched
182. What term is used to identify the point where the customer network ends and the service provider network begins?
- CSU/DSU
- the central office
- the local loop
- the demarcation point
183. Which two characteristics describe time-division multiplexing? (Choose two.)
- Traffic is allocated bandwidth across a single wire based on preassigned time slots.
- Bandwidth is allocated to channels based on whether a station has data to transmit.
- Encoding technology provides high data throughput in a minimum RF spectrum by supporting parallel data transmission.
- Depending on the configured Layer 2 protocol, data is transmitted across two or more channels via the use of time slots.
- Data capacity across a single link increases as bits from multiple sources are transmitted using interleaved slices of time.
184. A branch office uses a leased line to connect to the corporate network. The lead network engineer confirms connectivity between users in the branch office, but none of the users can access corporate headquarters. System logs indicate that nothing has changed in the branch office network. What should the engineer consider next to resolve this network outage?
- The network technician for the branch office should troubleshoot the switched infrastructure.
- The system administrator in the branch office should reconfigure the default gateway on the user PCs.
- The server administrator in the branch office should reconfigure the DHCP server.
- The service provider for the branch office should troubleshoot the issue starting from the point of demarcation.
185. Refer to the exhibit. Which three steps are required to configure Multilink PPP on the HQ router? (Choose three.)
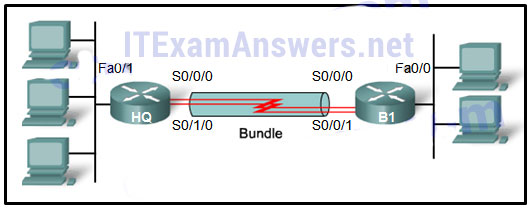
- Assign the serial interfaces to the multilink bundle.
- Assign the Fast Ethernet interface to the multilink bundle.
- Enable PPP encapsulation on the multilink interface.
- Enable PPP encapsulation on the serial interfaces.
- Bind the multilink bundle to the Fast Ethernet interface.
- Create and configure the multilink interface.
186. What is required for a host to use an SSL VPN to connect to a remote network device?
- VPN client software must be installed.
- A site-to-site VPN must be preconfigured.
- A web browser must be installed on the host.
- The host must be connected to a wired network.
187. What type of information is collected by Cisco NetFlow?
- interface errors
- CPU usage
- memory usage
- traffic statistics
188. What is a disadvantage of a packet-switched network compared to a circuit-switched network?
- fixed capacity
- higher latency
- less flexibility
- higher cost
189. Which three parts of a Frame Relay Layer 2 PDU are used for congestion control? (Choose three.)
- the FECN bit
- the BECN bit
- the C/R bit
- the 10-bit DLCI
- the Extended Address field
- the DE bit
190. Which two statements correctly describe asymmetric encryption used with an IPsec VPN? (Choose two.)
- The same encryption keys must be manually configured on each device.
- Public key encryption is a type of asymmetric encryption.
- Encryption and decryption use a different key.
- A shared secret key is used to perform encryption and descryption.
- AES is an example of an asymmetric encryption protocol.
191. What are two examples of network problems that are found at the data link layer? (Choose two.)
- incorrect interface clock rates
- late collisions and jabber
- framing errors
- electromagnetic interface
- encapsulation errors
192. Which IEEE standard defines the WiMax technology?
- 802.5
- 802.11
- 802.16
- 802.3
193. Place the options in the following order:
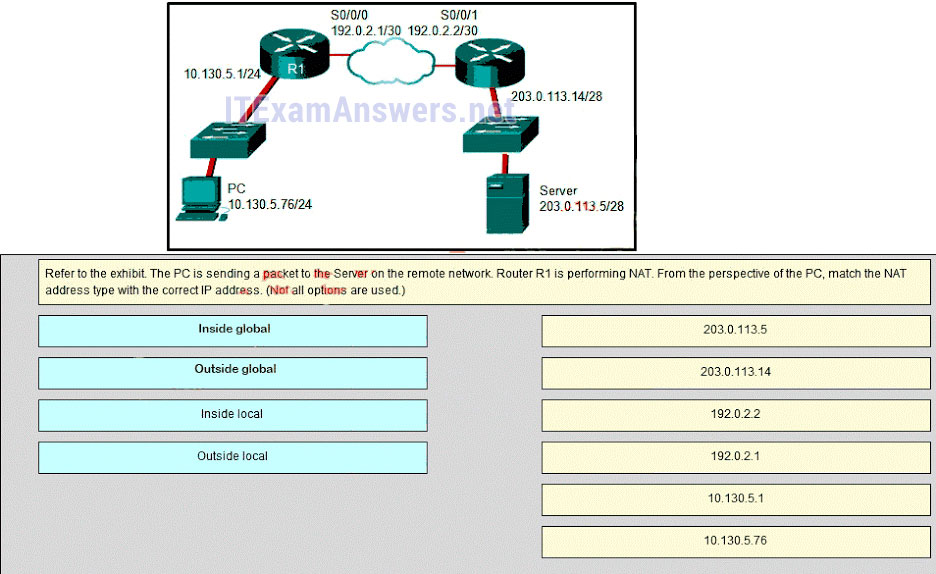
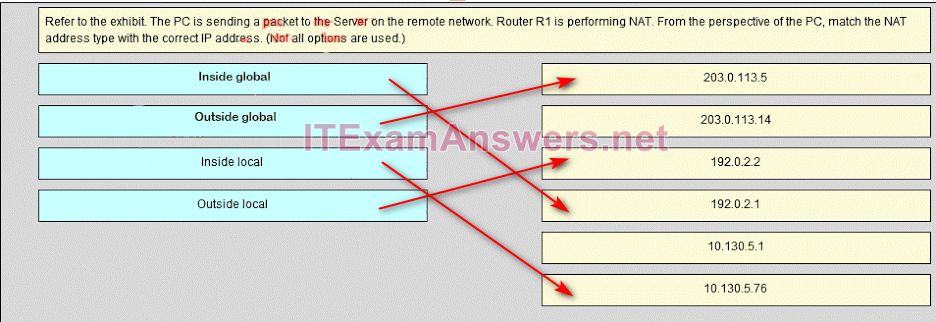
Outside global
– not scored –
Outside local
Inside global
– not scored –
Inside local
194. What is the default location for Cisco routers and switches to send critical logging events?
- syslog server
- virtual terminal
- console port
- auxiliary port
195. What is a type of VPN that is generally transparent to the end user?
- remote access
- public
- site-to-site
- private
196. Refer to the exhibit. Which three events will occur as a result of the configuration shown on R1? (Choose three.)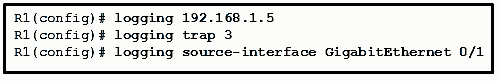
- Only traffic that originates from the GigabitEthernet 0/1 interface will be monitored.
- Messages that are sent to the syslog server will be limited to levels 3 or lower.
- Messages that are sent to the syslog server will use 192.168.1.5 as the destination IP address.
- The syslog messages will contain the IP address the GigabitEthernet 0/1 interface.
- Messages that are sent to the syslog server will be limited to levels 3 and higher.
- For multiple occurrences of the same error, only the first three messages will be sent to the server.
197. Which two technologies are implemented by organizations to support teleworker remote connections? (Choose two.)
- CMTS
- VPN
- CDMA
- IPsec
- DOCSIS
198. How many 64 kb/s voice channels are combined to produce a T1 line?
- 8
- 32
- 24
- 16
199. What is the purpose of a message hash in a VPN connection?
- It ensures that the data is coming from the correct source.
- It ensures that the data cannot be duplicated and replayed to the destination.
- It ensures that the data has not changed while in transit.
- It ensures that the data cannot be read in plain text.
200. Users are reporting longer delays in authentication and in accessing network resources during certain time periods of the week. What kind of information should network engineers check to find out if this situation is part of a normal network behavior?
- network configuration files
- syslog records and messages
- debug output and packet captures
- the network performance baseline
201. Which structured engineering desing principle ensures that the network reamins available even under abnormal conditions?
- resiliency
- hierarchy
- flexibility
- modularity
202. A team of engineers has identified a solution to a significant network problem. The proposed solution is likely to affect critical network infrastruture components. What should the team follow while implementing the solution to avoid interfering with other processes and infrastructure?
- suslog messages and reports
- one of the layered troubleshooting approaches
- change-control procedures
- knowledge base guidelines
203. What is a Frame Relay feauture that supports the IP address-to-DLCI dynamic mapping?
- FECN
- Inverse ARP
- ARP
- BECN
204. A small remote office needs to connect to headquarters through a secure IPsec VPN connection. The company is implementing the Cisco Easy VPN solution. Which Cisco Easy VPN component needs to be added on the Cisco router at the remote office?
- Cisco AnyConnect
- Cisco Easy VPN Server
- Cisco Easy VPN Remote
- Cisco VPN Client
205. Which scenario would require the use of static NAT?
- when an internal corporate web server needs to be accessed from a home network
- when there are more internal private IP addresses than available public IP addresses
- when all public IP addresses have been exhausted
- when an IPv4 site connects to an IPv6 site
206. An organization has purchased a Frame Relay service from a provider. The service agreement specifies that the access rate is 512 kbps, the CIR is 384 kbps, and the Bc is 32 kbps. What will happen when the customer sends a short burst of frames above 450 kbps?
- The frames are marked with the DE bit set to 1 and are most likely forwarded.
- The frames are marked with the DE bit set to 0 and are most likely forwarded.
- The frames are marked with the DE bit set to 0 and are allowed to pass.
- The frames are marked with the DE bit set to 1 and are most likely dropped.
207. What is a Frame Relay feature that supports the IP address-to-DLCI dynamic mapping?
- Inverse ARP
- ARP
- BECN
- FECN
208. An administrator wants to configure a router so that users on the outside network can only establish HTTP connections to the internal web site by navigating to http://www.netacad.com:8888. Which feature would the administrator configure to accomplish this?
- port forwarding
- dynamic NAT
- NAT overload
- static NAT
- PAT
209. Which two components are needed to provide a DSL connection to a SOHO? (Choose two.)
- PPPoE enabled switch
- CMTS
- transceiver
- CM
- DSLAM
210. A network engineer is troubleshooting an unsuccessful PPP multilink connection between two routers. That multilink interface has been created and assigned a number, the interface has been enabled for multilink PPP, and the interface has been assigned a multilink group number that matches the group assigned to the member physical serial interfaces. The physical serial interfaces have also been enabled for PPP multilink. Which additional command should to be issued on the multilink interface?
- clock rate 4000000
- encapsulation ppp
- ip address 192.168.10.1 255.255.255.252
- no ip address
211. What is the international standard defining cable-related technologies?
- WiMax
- DOCSIS
- ADSL
- PPPoE
212. Which three statements describe characteristics of converging corporate network architecture?
- Server applications are housed within the phisical corporate
- network.
- Users connect their own devices to the corporate network.
- Data types include data, and video.
- Users have to use company-owned computers.
- Networks are borderless.
213. Which inefficient feature of time-division multiplexing does statistical TDM overcome?
- the unused high speed time slots
- the buffering of data during peak periods
- the use of channel identifiers
- the use of a multiplexer at the transmitter and receiver
214. What are three characteristics of SSL VPNs?
- authentication can be one way
- authentication uses shared secret or digital cerificates
- an ssl vpn supports web enable applications, e-mail and file sharing
- connecting may challeenge nontechnical users
- encryption requires key lengths from 40 bits to 256 bits
- an ssl vpn requires specific configuration of PCs to connect
215. A network engineer is designing an IPsec VPN between Cisco routers for a national bank. Which algorithm assures the highest level of confidentiality for data crossing the VPN?
- 256bit AES
- 512 bit RSA
- SHA-1
- 3DES
216. By the use of sequence numbers, which function of the IPsec security services prevents spoofing by verifying that each packet is non-duplicated and unique?
- anti-replay protection
- confidentiality
- data integrity
- authentication
217. A small law firm wants to connect to the Internet at relatively high speed but with low cost. In addition, the firm prefers that the connection be through a dedicated link to the service provider. Which connection type should be selected?
- leased line
- ISDN
- cable
- DSL
218. How can an administrator configure a Cisco Easy VPN Server to enable the company to manage many remote VPN connections efficiently?
- by updating the client software in regular intervals
- by preconfiguring IPsec parameters when deploying the client solution
- by provisioning dedicated bandwidth for VPN connections
- by pushing the IPsec security policies to the clients when establishing the tunnel
219. How does QoS improve the effectiveness of teleworking?
- It provides wireless data transmission over large urban areas.
- It provides high speed connections over copper wires.
- It provides better service for VoIP and video conferencing applications.
- It provides authentication, accounting, and link management features for ISPs.
220. Which two networking technologies enable businesses to use the Internet, instead of an enterprise WAN, to securely interconnect their distributed networks? (Choose two.)
- DSL
- remote LANs
- remote access VPNs
- site-to-site VPNs
- Frame Relay
221. What are two benefits of using SNMP traps? (Choose two.)
- They eliminate the need for some periodic polling requests.
- They reduce the load on network and agent resources.
- They can provide statistics on TCP/IP packets that flow through Cisco devices.
- They can passively listen for exported NetFlow datagrams.
- They limit access for management systems only.
New Questions (v6.0):
222. A network engineer has issued the show interfaces serial 0/0/0 command on a router to examine the open NCPs on a PPP link to another router. The command output displays that the encapsulation is PPP and that the LCP is open. However, the IPV6CP NCP is not shown as open. What does the engineer need to configure to open the IPV6CP NCP on the link?
- Configure an IPv6 address on each interface on the link.
- Configure PPP multilink interfaces on each router.
- Issue the compress predictor command on each interface on the link.
- Configure CHAP authentication on each router.
223. What address translation is performed by static NAT?
- An inside local address is translated to a specified inside global address
- An inside local address is translated to a specified outside local address
- An inside local address is translated to a specified outside global address
- An outside local address is translated to a specified outside global address
224. What are two advantages of using IPv4 NAT? (Choose two.)
- provides consistent traceability when it is necessary to troubleshoot internal corporate network problems
- conserves public IP addresses
- provides consistency when an internal corporate IP addressing scheme is being designed
- allows maintaining end-to-end addressing
- increases network performance
225. Which network design module would not commonly connect to the service provider edge?
- Remote Access and VPN *
- E-Commerce
- Enterprise Branch
- WAN Site-to-site VPN
226. Whichtwo types of devices are specific to WAN environments and are not found ona LAN?(Choose two.)
- Distribution layer router
- Broadband modem
- Core switch
- Access layer switch
- CSU/DSU
227. What is a plausible reason that an employee would become a teleworker for a company?
- to become employed without having to share files or resourcesto
- become employed in a traditional workplace
- to keep employment during a time of rehabilitation
- to keep employment without having to adhere to company regulations
228. Connecting offices at different locations using the Internet can be economical for a business. What are two important business policy issues that should be addressed when using the Internet for this purpose? (Choose two.)
- WAN technology
- bandwidth
- security
- privacy
- addressing
229. A technician at a remote location is troubleshooting a router and has emailed partial debug command output to a network engineer at the central office. The message that is received by the engineer only contains a number of LCP messages that relate to a serial interface. Which WAN protocol is being used on the link?
- HDLC
- VPN
- Frame Relay
- PPP
230. What is a feature of physical point-to-point WAN links?
- Point-to-point links are generally the least expensive type of WAN access.
- The MAC address is not used in the address field of the point-to-point frame.
- WAN operations focus primarily on the network layer (OSI Layer 3).
- Point-to-point WAN services are circuit switched.
231. Which PPP protocol allows a device to specify an IP address for routing over the PPP link?
- CHAP
- LCP
- PAP
- IPCP
232. Which two statements describe benefits of NAT? (Choose two.)
- NAT simplifies troubleshooting by removing the need for end-to-end traceability.
- NAT can provide application port-level multiplexing in order to conserve public IP addresses.
- NAT allows for easy readdressing when changing ISPs.
- NAT makes tunneling protocols like IPsec more efficient by modifying the addresses in the headers.
- NAT provides stateful packet filtering features similar to a firewall.
- NAT increases router performance by reducing the number of routes needed in the routing table.
233. What is one drawback to using the top-down method of troubleshooting?
- trying to decide which device to check first
- the amount of paperwork that is generated
- the need to check every device and interface on the network and document them
- the need to check every possible application problem and document it
234. What are three functions provided by syslog service? (Choose three.)
- to specify the destination of captured messages
- to provide traffic analysis
- to gather logging information for monitoring and troubleshooting
- to select the type of logging information that is captured
- to periodically poll agents for data
- to provide statistics on packets that are flowing through a Cisco device
235. Which two types of equipment are needed to send digital modem signals upstream and downstream on a cable system? (Choose two.)
- DSLAM
- CMTS
- transceiver
- microfilter
- cable modem
236. What two advantages are associated with Frame Relay WAN technology when compared with leased lines? (Choose two.)
- Dedicated data path between sites
- Fixed and dedicated capacity
- Flexibility
- Globally unique DLCI for each site
- Cost effectieness
237. Which statement describes an advantage of deploying the Cisco SSL VPN solution rather than the Cisco Easy VPN solution?
- It provides a stronger authentication mechanism.
- It provides more network service access.
- It provides a stronger encryption algorithm.
- It supports clientless remote access.

Is it updated dump ? I have exam in next week. if not please kindly comment new answer page Please
2 years ago
Can anyone tell me which one is the “practice final exam with PT”?.
Not the one with questions, i mean the one with packet tracer.
https://itexamanswers.net/connecting-networks-v6-0-cn-practice-skills-assessment-pt.html
How updated is this? I am taking my ccna 200-301 exam next month.
Hello Admin, Your Contents are great for preparing CCNA, but I have a doubt that in CCNA exam there will be simulator question right do have any sample practice questions for simulator type question and do you know how many questions will be there in simulator type??
As far as I know, this exam don’t have simulator question.
what about SIMLET questions?
https://learningnetwork.cisco.com/docs/DOC-34312
see this website there is simulation type questions in CCNA R&S
Help me find revision question for CCNA final exam
Is question 118 correct for the second answer? How come it’s 206 and not 209?
Can anyone tell me which one is the “practice final exam with PT”?.
Not the one with questions, i mean the one with packet tracer.
Question 103 needs the second answer colored red. Thanks for this btw.
ok, thanks you!
Are both versions actual test possibilities?
You just need to learn the questions in the sessions “Version 6.0” & “New Question (v6.0)”
Thanks
Questions which are repeats:
2 and 228
9 and 61 and 107
44 and 86
52 and 145
54 and 226
62 and 109
We have removed some duplicate questions, thank you so much!
Duplicates 44 – 86 and 54 – 226 are still there.
ok, thanks you!
Questions 2 and 228 are the same exam question, but the answers are different. Which one is the correct one?
Answers is: “privacy” and “security”
We are updating the duplicate issues, thanks for feedback!
Is this 3 or 4? I am panicking now because someone said 3 lol. I’ve been studying this for weeks and my exam is on the 10th of next month. I have to take it in front of people so I have completely know this. Also, are all 237 questions necessary for this test? Which ones will be on the test?
CCNA 4, the questions are still valid
This is CCNA3 not 4 !! :O
Are you sure? Can you send me your screenshot?
There are 8 chapters in CCNA3 not 10, all CCN3 chapters are in your CCN4 and this questions are about all thems in CCNA3, WAN concpets, troubelshooting, SNMP, QoS…
I think you have confused. Please press the PrintScreen key (PrtScr), go to https://paste.pics/ and press Ctrl+V to upload your course screenshot and share url for me. Thanksyou!
Hello, here :
https://paste.pics/19e20ed6ee6e00d36509cac437858b51
https://paste.pics/cb85e8f251d98f79aa2d3bd7a734ca70
Instructor you have mistakenly assigned courses or your CCNA 3 course (Scaling Networks) was skipped.
CCNA 3: Scaling Networks
CCNA 4: Connecting Networks
Match QoS techniques with the description. (Not all options are used.)
traffic policing
marking
traffic shaping
classification
Excess traffic is retained in a queue and scheduled for later transmission over increments of time.
traffic policing
Excess traffic is dropped when the traffic rate reaches a preconfigured maximum.
classification
This determines the class of traffic to which frames belong.
traffic shaping
A value is added to a packet header.
marking
TCP traffic is throttled to prevent tail drop.
Updated answers, thanks !
What is the likelihood of passing when you use this exams?
99% pass
is CCNA V6 and CCNA V7 the same
Which two factors allow businesses to safely communicate and perform transactions using the Internet?
security
addressing
privacy
WAN technology
bandwidth
security
privacy
In the NEW VERSION, the questions from 113 to the end (of the new version), ARE NOT PRESENT IN THE ONLINE test. Thank you a lot!!!
How do you know for certain bro??
Bout to sit 4 this soon
how i can download this question
In which stage of the troubleshooting process would ownership be researched and documented??
Implement corrective action.
OR
Gather symptoms.
???
gather symptoms
A company is considering updating the campus WAN connection. Which two WAN options are examples of the private WAN architecture? (Choose two.)
A company is considering updating the campus WAN connection. Which two WAN options are examples of the private WAN architecture? (Choose two.)
cable
leased line*
Ethernet WAN*
municipal Wi-Fi
digital subscriber line
Ethernet WAN
leased line
What is used to pre-populate the adjacency table on Cisco devices that use CEF to process packets?
the ARP table*