Time limit: 0
Quiz-summary
0 of 20 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
Information
CCNP SWITCH Chapter 10 Test Online (Version 7) – Score 100%
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 20 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- Answered
- Review
-
Question 1 of 20
1. Question
1 pointsWhich statement describes the purpose of the configuration that is shown? Switch(config)# ip dhcp snooping Switch(config)# ip dhcp snooping vlan 3 Switch(configif)#ip dhcp snooping trust Switch(configif)#ip dhcp snooping limit rate 30Correct
Incorrect
-
Question 2 of 20
2. Question
1 pointsWhat IOS feature is executed with the traceroute mac command?Correct
Incorrect
-
Question 3 of 20
3. Question
1 pointsWhich countermeasure can be implemented to determine the validity of an ARP packet, based on the valid MACaddresstoIP address bindings stored in a DHCP snooping database?Correct
Incorrect
-
Question 4 of 20
4. Question
1 pointsA network administrator is tasked with protecting a server farm by implementing private VLANs. Each server should only be allowed to communicate with the default gateway. Which type of pVLAN should be configured on the switch port that connects to a server?Correct
Incorrect
-
Question 5 of 20
5. Question
1 pointsWhat can be used to mitigate MAC table flooding attacks?Correct
Incorrect
-
Question 6 of 20
6. Question
1 pointsHow does MAC address flooding cause a vulnerability in the network?Correct
Incorrect
-
Question 7 of 20
7. Question
1 pointsWhich type of output would be produced on a switch after entering the command, Switch# show ip dhcp snooping binding?Correct
Incorrect
-
Question 8 of 20
8. Question
1 pointsWhat are two purposes for an attacker launching a MAC table flood? (Choose two.)Correct
Incorrect
-
Question 9 of 20
9. Question
1 pointsHow does VLAN hopping cause a vulnerability in the network?Correct
Incorrect
-
Question 10 of 20
10. Question
1 pointsWhat switchport portsecurity keyword causes MAC addresses to be added to the running configuration?Correct
Incorrect
-
Question 11 of 20
11. Question
1 pointsIn which location or situation is a private VLAN appropriate?Correct
Incorrect
-
Question 12 of 20
12. Question
1 pointsA network administrator is tasked with protecting a server farm by implementing private VLANs (PVLANs). A server is only allowed to communicate with its default gateway and other related servers. Which type of PVLAN should be configured on the switch ports that connect to the servers?Correct
Incorrect
-
Question 13 of 20
13. Question
1 pointsWhich statement best describes how traffic is handled between different port types within a primary pVLAN?Correct
Incorrect
-
Question 14 of 20
14. Question
1 pointsWhat is one way to mitigate spanningtree compromises?Correct
Incorrect
-
Question 15 of 20
15. Question
1 pointsHow should unused ports on a switch be configured in order to prevent VLAN hopping attacks?Correct
Incorrect
-
Question 16 of 20
16. Question
1 pointsWhat technology can be used to help mitigate MAC address flooding attacks?Correct
Incorrect
-
Question 17 of 20
17. Question
1 pointsWhich configuration guideline applies to using the capture option in VACL?Correct
Incorrect
-
Question 18 of 20
18. Question
1 pointsAll access ports on a switch are configured with the administrative mode of dynamic auto. An attacker, connected to one of the ports, sends a malicious DTP frame. What is the intent of the attacker?Correct
Incorrect
-
Question 19 of 20
19. Question
1 pointsRefer to the exhibit. After the configuration has been applied to ACSw22, frames that are bound for the node on port FastEthernet 0/1 are periodically being dropped. What should be done to correct the issue?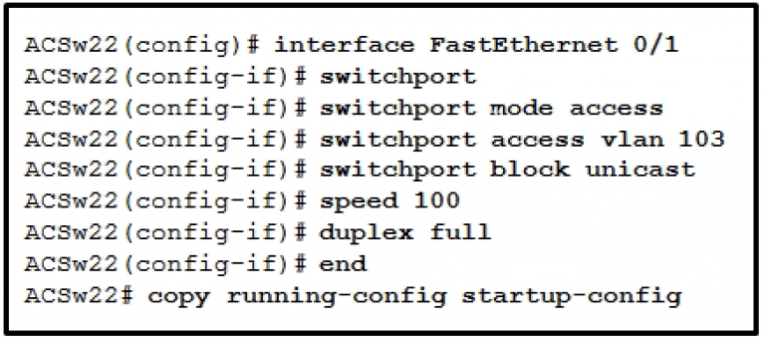 Correct
Correct
Incorrect
-
Question 20 of 20
20. Question
1 pointsWhat is one way to mitigate ARP spoofing?Correct
Incorrect
