Cyber Threat Management (CyberTM) Course Final Exam Answers
1. What are three disclosure exemptions that pertain to the FOIA? (Choose three.)
- law enforcement records that implicate one of a set of enumerated concerns
- information specifically non-exempt by statue
- confidential business information
- non-geological information regarding wells
- national security and foreign policy information
- public information from financial institutions
Explanation: The nine Freedom of Information Act (FOIA) exemptions include the following:
1. National security and foreign policy information
2. Internal personnel rules and practices of an agency
3. Information specifically exempted by statute
4. Confidential business information
5. Inter- or intra-agency communication subject to deliberative process, litigation, and other privileges
6. Information that, if disclosed, would constitute a clearly unwarranted invasion of personal privacy
7. Law enforcement records that implicate one of a set of enumerated concerns
8. Agency information from financial institutions
9. Geological and geophysical information concerning wells
2. A company is developing security policies. Which security policy would address the rules that determine access to and use of network resources and define the consequences of policy violations?
- data policy
- remote access policy
- acceptable use policy
- password policy
Explanation: An organization needs to establish clear and detailed security policies. Some of these policies are:
Password policy- Defines minimum password requirements, such as the number and type of characters used and how often they need to be changed.
Acceptable use policy- Highlights a set of rules that determine access to and use of network resources. It may also define the consequences of policy violations.
Remote access policy- Sets out how to remotely connect to the internal network of an organization and explains what information is remotely accessible.
Data policy- Sets out measurable rules for processing data within an organization, such as specifying where data is stored, how data is classified, and how data is handled and disposed of.
3. Which framework should be recommended for establishing a comprehensive information security management system in an organization?
- ISO/IEC 27000
- ISO OSI model
- CIA Triad
- NIST/NICE framework
Explanation: A cybersecurity specialist needs to be familiar with the different frameworks and models for managing information security.
4. If a person knowingly accesses a government computer without permission, what federal act laws would the person be subject to?
Explanation: The Computer Fraud and Abuse Act (CFAA) provides the foundation for US laws criminalizing unauthorized access to computer systems.
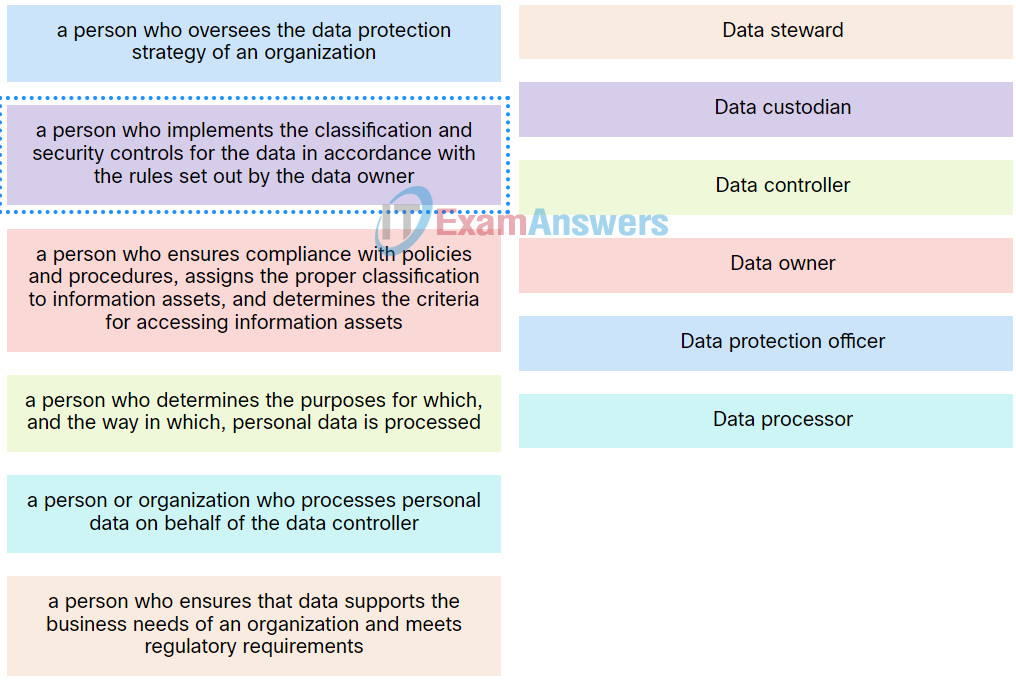
5. Match the roles in the data governance program to the description.
Cyber Threat Management (CyberTM) Course Final Exam 5
Explanation: Place the options in the following order:
| a person who oversees the data protection strategy of an organization |
Data protection officer |
| a person or organization who processes personal data on behalf of the data controller |
Data processor |
| a person who determines the purposes for which, and the way in which, personal data is processed |
Data controller |
| a person who ensures that data supports the business needs of an organization and meets regulatory requirements |
Data steward |
| a person who ensures compliance with policies and procedures, assigns the proper classification to information assets, and determines the criteria for accessing information assets |
Data owner |
| a person who implements the classification and security controls for the data in accordance with the rules set out by the data owner. |
Data custodian |
6. What type of security test uses simulated attacks to determine possible consequences of a real threat?
- penetration testing
- integrity checking
- network scanning
- vulnerability scanning
Explanation: There are many security tests that can be used to assess a network. Penetration testing is used to determine the possible consequences of successful attacks on the network. Integrity checking is used to detect and report changes made to systems. Vulnerability scanning is used to find weaknesses and misconfigurations on network systems. Network scanning is used to discover available resources on the network.
7. What are two tasks that can be accomplished with the Nmap and Zenmap network tools? (Choose two.)
- Identification of Layer 3 protocol support on hosts
- Password recovery
- TCP and UDP port scanning
- Validation of IT system configuratio
- Password auditing
Explanation: Nmap is a low-level network scanner that is available to the public and which has the ability to perform port scanning, to identify open TCP and UDP ports, and perform system identification. It can also be used to identify Layer 3 protocols that are running on a system.
8. Which network security tool can detect open TCP and UDP ports on most versions of Microsoft Windows?
- L0phtcrack
- Zenmap
- SuperScan
- Nmap
Explanation: There are various network security tools available for network security testing and evaluation. L0phtcrack can be used to perform password auditing and recovery. SuperScan is a Microsoft port scanning software that detects open TCP and UDP ports on systems. Nmap and Zenmap are low-level network scanners available to the public.
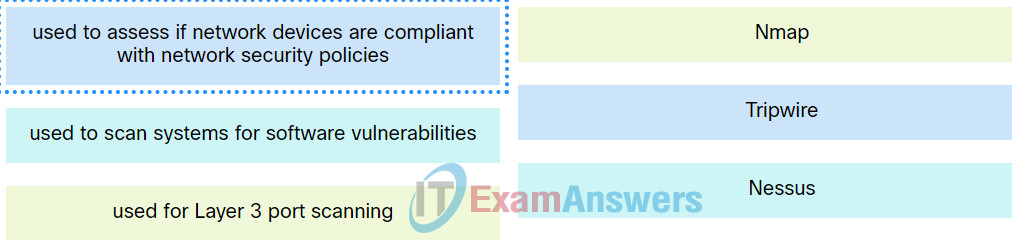
9. Match the network security testing tool with the correct function. (Not all options are used.)
Cyber Threat Management (CyberTM) Course Final Exam 9
Explanation: Place the options in the following order:
| used to assess if network devices are compliant with network security policies |
Tripwire |
| used to scan systems for software vulnerabilities |
Nessus |
| used for Layer 3 port scanning |
Nmap |
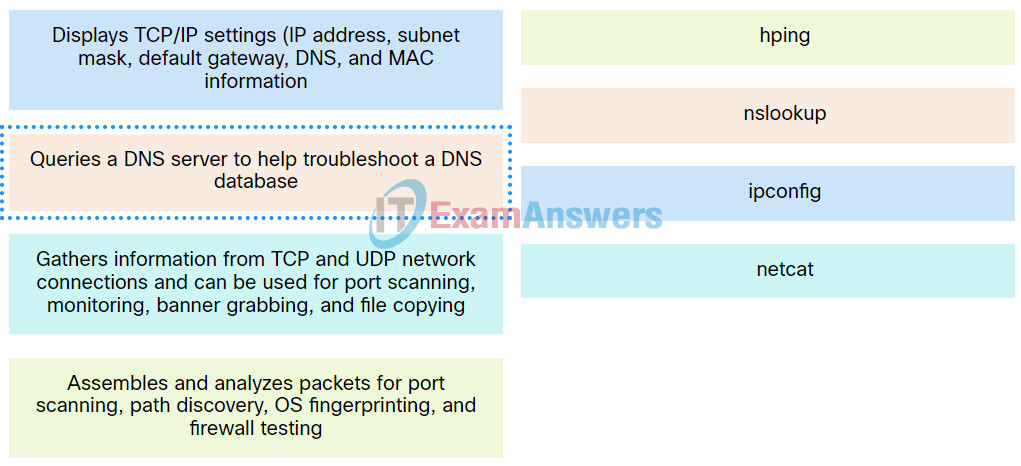
10. Match the command line tool with its description.
Cyber Threat Management (CyberTM) Course Final Exam 10
Explanation: Place the options in the following order:
| Displays TCP/IP settings (IP address, subnet mask, default gateway, DNS, and MAC information. |
ipconfig |
| Gathers information from TCP and UDP network connections and can be used for port scanning, monitoring, banner grabbing, and file copying. |
netcat |
| Assembles and analyzes packets for port scanning, path discovery, OS fingerprinting, and firewall testing. |
hping |
| Queries a DNS server to help troubleshoot a DNS database. |
nslookup |
11. What three services are offered by FireEye? (Choose three.)
- deploys incident detection rule sets to network security tools
- creates firewall rules dynamically
- identifies and stops email threat vectors
- identifies and stops latent malware on files
- subjects all traffic to deep packet inspection analysis
- blocks attacks across the web
Explanation: FireEye is a security company that uses a three-pronged approach combining security intelligence, security expertise, and technology. FireEye offers SIEM and SOAR with the Helix Security Platform, which use behavioral analysis and advanced threat detection.
12. What is a characteristic of CybOX?
- It is the specification for an application layer protocol that allows the communication of CTI over HTTPS.
- It enables the real-time exchange of cyberthreat indicators between the U.S. Federal Government and the private sector.
- It is a set of standardized schemata for specifying, capturing, characterizing, and communicating events and properties of network operations.
- It is a set of specifications for exchanging cyberthreat information between organizations.
Explanation: CybOX is an open standards set of standardized schemata for specifying, capturing, characterizing, and communicating events and properties of network operations that support many cybersecurity functions.
13. What three security tools does Cisco Talos maintain security incident detection rule sets for? (Choose three.)
- ClamAV
- Snort
- Socat
- NetStumbler
- SpamCop
Explanation: Talos maintains the security incident detection rule sets for the Snort.org, ClamAV, and SpamCop network security tools.
14. Which security organization maintains a list of common vulnerabilities and exposures (CVE) and is used by prominent security organizations?
- CIS
- SecurityNewsWire
- MITRE
- SANDS
Explanation: The MITRE Corporation maintains a list of common vulnerabilities and exposures (CVE) used by prominent security organizations.
15. As a Cybersecurity Analyst, it is very important to keep current. It was suggested by some colleagues that NewsBites contains many good current articles to read. What network security organization maintains this weekly digest?
Explanation: The SysAdmin, Audit, Network, Security (SANS) Institute has many resources. One of them is called NewsBites, the weekly digest of news articles about computer security.
16. A network administrator is creating a network profile to generate a network baseline. What is included in the critical asset address space element?
- the IP addresses or the logical location of essential systems or data
- the time between the establishment of a data flow and its termination
- the TCP and UDP daemons and ports that are allowed to be open on the server
- the list of TCP or UDP processes that are available to accept data
Explanation: A network profile should include some important elements, such as the following:
Total throughput – the amount of data passing from a given source to a given destination in a given period of time
Session duratio n – the time between the establishment of a data flow and its termination
Ports used – a list of TCP or UDP processes that are available to accept data
Critical asset address space – the IP addresses or the logical location of essential systems or data
17. When a server profile for an organization is being established, which element describes the TCP and UDP daemons and ports that are allowed to be open on the server?
- service accounts
- listening ports
- software environment
- critical asset address space
Explanation: A server profile will often contain the following:
* Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server
* User accounts – the parameters defining user access and behavior
* Service accounts – the definitions of the type of service that an application is allowed to run on a server
* Software environment – the tasks, processes, and applications that are permitted to run on the server
18. The IT security personnel of an organization notice that the web server deployed in the DMZ is frequently targeted by threat actors. The decision is made to implement a patch management system to manage the server. Which risk management strategy method is being used to respond to the identified risk?
- risk retention
- risk sharing
- risk reduction
- risk avoidance
Explanation: There are four potential strategies for responding to risks that have been identified:
* Risk avoidance – Stop performing the activities that create risk.
* Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
* Risk sharing – Shift some of the risk to other parties.
* Risk retention – Accept the risk and its consequences.
19. Which class of metric in the CVSS Base Metric Group defines the features of the exploit such as the vector, complexity, and user interaction required by the exploit?
- Exploitability
- Exploit Code Maturity
- Impact
- Modified Base
Explanation: The Base Metric Group of CVSS represents the characteristics of a vulnerability that are constant over time and across contexts. It contains two classes of metrics:
* Exploitability metrics – features of the exploit such as the vector, complexity, and user interaction required by the exploit
* Impact metrics – the impacts of the exploit rooted in the CIA triad of confidentiality, integrity, and availability
20. In what order are the steps in the vulnerability management life cycle conducted?
- discover, prioritize assets, assess, remediate, report, verify
- discover, prioritize assets, assess, remediate, verify, report
- discover, assess, prioritize assets, report, remediate, verify
- discover, prioritize assets, assess, report, remediate, verify
Explanation: There are six steps in the vulnerability management life cycle:
– Discover
– Prioritize assets
– Assess
– Report
– Remediate
– Verify
21. An organization has implemented antivirus software. What type of security control did the company implement?
- detective control
- compensative control
- deterrent control
- recovery control
Explanation: A cybersecurity specialist must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities.
22. What is the first step taken in risk assessment?
- Identify threats and vulnerabilities and the matching of threats with vulnerabilities.
- Compare to any ongoing risk assessment as a means of evaluating risk management effectiveness.
- Establish a baseline to indicate risk before security controls are implemented.
- Perform audits to verify threats are eliminated.
Explanation: The three steps of risk assessment in order are as follows:
– Identify threats and vulnerabilities and the matching of threats with vulnerabilities.
– Establish a baseline to indicate risk before security controls are implemented.
– Compare to an ongoing risk assessment as a means of evaluating risk management effectiveness.
23. Match the stages in the risk management process to the description.
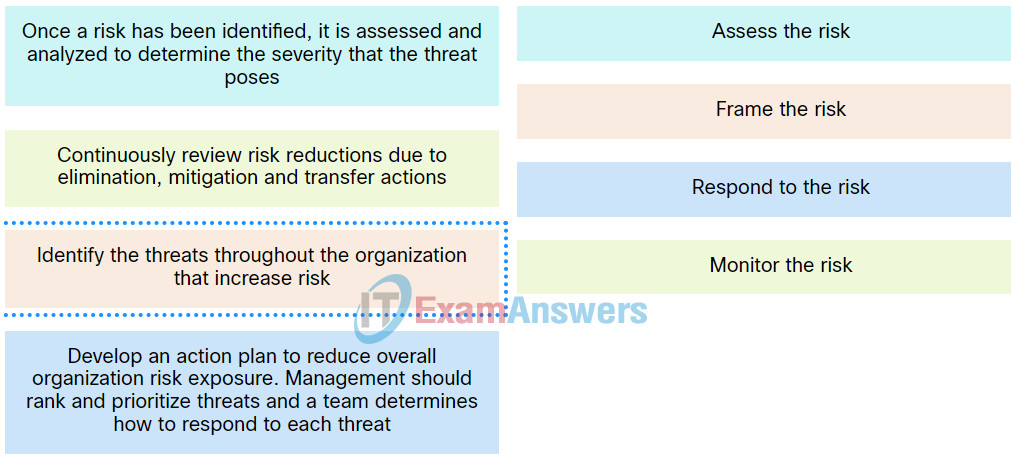
Explanation: Place the options in the following order:
| Develop an action plan to reduce overall organization risk exposure. Management should rank and prioritize threats and a team determines how to respond to each threat. |
Respond to the risk. |
| Once a risk has been identified, it is assessed and analyzed to determine the severity that the threat poses. |
Assess the risk. |
| Continuously review risk reductions due to elimination, mitigation and transfer actions. |
Monitor the risk. |
| Identify the threats throughout the organization that increase risk. |
Frame the risk. |
24. Your risk manager just distributed a chart that uses three colors to identify the level of threat to key assets in the information security systems. Red represents high level of risk, yellow represents average level of threat and green represents low level of threat. What type of risk analysis does this chart represent?
- qualitative analysis
- quantitative analysis
- loss analysis
- exposure factor analysis
Explanation: A qualitative or quantitative risk analysis is used to identify and prioritize threats to the organization.
25. A company manages sensitive customer data for multiple clients. The current authentication mechanism to access the database is username and passphrase. The company is reviewing the risk of employee credential compromise that may lead to a data breach and decides to take action to mitigate the risk before further actions can be taken to eliminate the risk. Which action should the company take for now?
- Install fingerprint or retinal scanners.
- Implement multi-factor authentication.
- Purchase an insurance policy.
- Enhance data encryption with an advanced algorithm.
Explanation: Risk management is the identification, evaluation, and prioritization of risks. Organizations manage risk in one of four ways, avoidance, mitigation, transfer, or accept. In this scenario, implementing multi-factor authentication can reduce the risk of employee credential compromise, which is a mitigation action. Installing fingerprint or retinal scanners eliminates the risk, which is avoidance. Purchasing an insurance policy is transferring the financial risk to the insurance company.
26. Match the security incident stakeholder with the role.
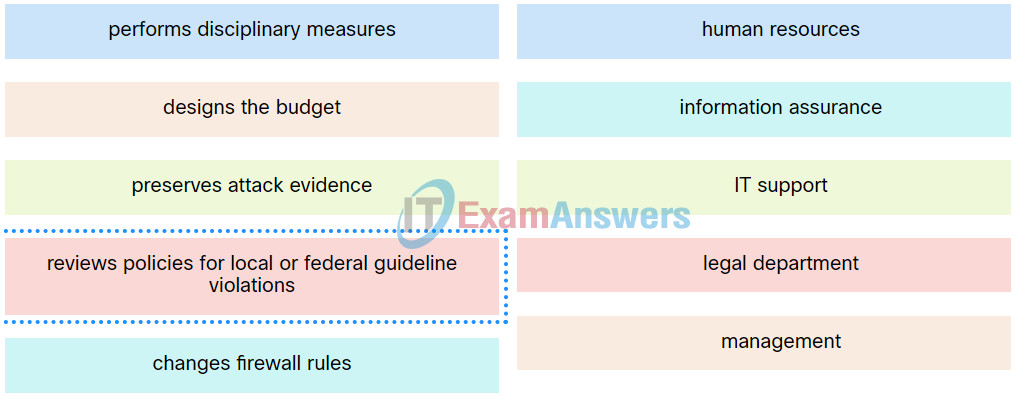
Cyber Threat Management (CyberTM) Course Final Exam 26
Explanation: Place the options in the following order:
| performs disciplinary measures |
human resources |
| changes firewall rules |
information assurance |
| preserves attack evidence |
IT support |
| designs the budget |
management |
| reviews policies for local or federal guideline violations |
legal department |
27. Why would threat actors prefer to use a zero-day attack in the Cyber Kill Chain weaponization phase?
- to launch a DoS attack toward the target
- to get a free malware package
- to avoid detection by the target
- to gain faster delivery of the attack on the target
Explanation: When a threat actor prepares a weapon for an attack, the threat actor chooses an automated tool (weaponizer) that can be deployed through discovered vulnerabilities. Malware that will carry desired attacks is then built into the tool as the payload. The weapon (tool plus malware payload) will be delivered to the target system. By using a zero-day weaponizer, the threat actor hopes that the weapon will not be detected because it is unknown to security professionals and detection methods are not yet developed.
28. A threat actor has identified the potential vulnerability of the web server of an organization and is building an attack. What will the threat actor possibly do to build an attack weapon?
- Create a point of persistence by adding services.
- Install a webshell on the web server for persistent access.
- Obtain an automated tool in order to deliver the malware payload through the vulnerability.
- Collect credentials of the web server developers and administrators.
Explanation: One tactic of weaponization used by a threat actor after the vulnerability is identified is to obtain an automated tool to deliver the malware payload through the vulnerability.
29. According to NIST standards, which incident response stakeholder is responsible for coordinating an incident response with other stakeholders to minimize the damage of an incident?
- IT support
- human resources
- legal department
- management
Explanation: The management team creates the policies, designs the budget, and is in charge of staffing all departments. Management is also responsible for coordinating the incident response with other stakeholders and minimizing the damage of an incident.
30. Which meta-feature element in the Diamond Model describes information gained by the adversary?
- resources
- results
- direction
- methodology
Explanation: The meta-feature element results are used to delineate what the adversary gained from the intrusion event.
31. The manager of a new data center requisitions magnetic door locks. The locks will require employees to swipe an ID card to open. Which type of security control is being implemented?
- corrective
- compensative
- preventive
- recovery
Explanation: Preventive security controls prevent unwanted or unauthorized activities from occurring and/or apply restrictions to authorized users.
32. What is a statement of applicability (SOA)?
- It stipulates total compliance with NIST.
- It sets out a broad framework of network protocols used and their implementations.
- It allows for the tailoring of available control objectives and controls to best meet its priorities around confidentiality, integrity, and availability
- It is used as an audit point for network device implementation.
33. An organization is developing a data governance program that follows regulations and policies. Which role in the program is responsible for ensuring compliance with policies and procedures, assigning the proper classification to information assets, and determining the criteria for accessing information assets?
- data controller
- data custodian
- data owner
- data protection officer
34. A company is preparing for an ISMS audit. Match the right control for each control objective.
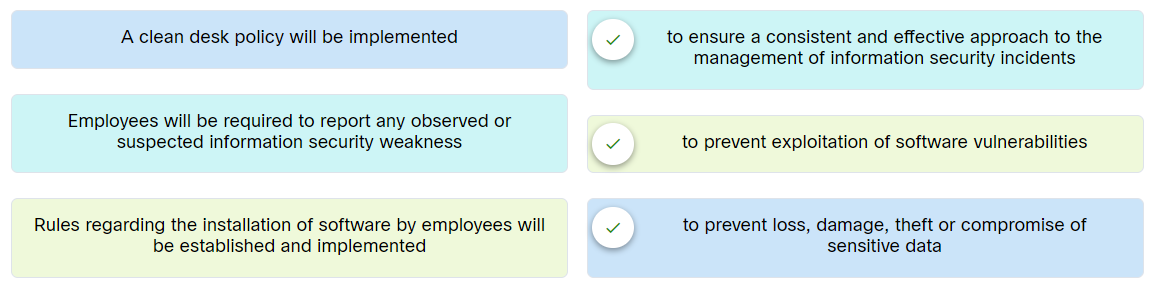
35. Which step in the Vulnerability Management Life Cycle performs inventory of all assets across the network and identifies host details, including operating system and open services?
- Assess
- Discover
- Remediate
- Prioritize assets
Explanation: The steps in the Vulnerability Management Life Cycle include these:
- Discover – inventory all assets across the network and identify host details, including operating systems and open services to identify vulnerabilities
- Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations
- Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification
- Report – measure the level of business risk associated with your assets according to your security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities
- Remediate – prioritize according to business risk and fix vulnerabilities in order of risk
- Verify – verify that threats have been eliminated through follow-up audits
36. Which two classes of metrics are included in the CVSS Base Metric Group? (Choose two.)
- Confidentiality Requirement
- Modified Base
- Exploit Code Maturity
- Exploitability
- Impact metrics
Explanation: The Base Metric Group of CVSS represents the characteristics of a vulnerability that are constant over time and across contexts. It contains two classes of metrics, Exploitability and Impact.
37. Which type of evidence cannot prove an IT security fact on its own?
- best
- corroborative
- indirect
- hearsay
Explanation: Indirect evidence cannot prove a fact on its own, but direct evidence can. Corroborative evidence is supporting information. Best evidence is most reliable because it is something concrete such as a signed contract.
38. What three tasks are accomplished by a comprehensive security policy? (Choose three.)
- useful for management
- defines legal consequences of violations
- is not legally binding
- gives security staff the backing of management
- vagueness
- sets rules for expected behavior
Explanation: The security policy of an organization accomplishes several tasks:
- It demonstrates the commitment to security by an organization.
- It sets the rules for expected behavior.
- It ensures consistency in system operations, and software and hardware acquisition use and maintenance.
- It defines the legal consequences of violations.
- It gives security staff the backing of management.
39. To ensure that the chain of custody is maintained, what three items should be logged about evidence that is collected and analyzed after a security incident has occurred? (Choose three.)
- measures used to prevent an incident
- time and date the evidence was collected
- extent of the damage to resources and assets
- vulnerabilities that were exploited in an attack
- serial numbers and hostnames of devices used as evidence
- location of all evidence
Explanation: A chain of custody refers to the proper accounting of evidence collected about an incident that is used as part of an investigation. The chain of custody should include the location of all evidence, the identifying information of all evidence such as serial numbers and hostnames, identifying information about all persons handing the evidence, and the time and date that the evidence was collected.
40. Which meta-feature element in the Diamond Model classifies the general type of intrusion event?
- phase
- results
- methodology
- direction
Explanation: Methodology – This is used to classify the general type of event, such as port scan, phishing, content delivery attack, syn flood, etc.
41. What key considerations does a business impact analysis (BIA) examine? (Choose four.)
- Recovery time objectives (RTOs)
- Recovery point objectives (RPOs)
- Recovery point times (RPTs)
- Mean time between objectives (RBOs)
- Mean time between failures (MTBF)
- Mean time to repair (MTTR)
Explanation: Business continuity controls are more than just backing up data and providing redundant hardware. Creating a business continuity plan starts with carrying out a business impact analysis (BIA) to identify critical business processes, resources, and relationships between systems. The BIA focuses on the consequences of the interruption to critical business functions and examines the key considerations listed here: RTOs, RPOs, MTTR, and MTBF. The National Institute of Standards and Technology (NIST) developed best practices in relation to business continuity.
42. Which type of controls help uncover new potential threats?
- Preventive controls
- Detective controls
- Corrective controls
Explanation: Detective measures include controls that discover unwanted events. These measures uncover new potential threats.







A risk analyst conducts quantitative risk analysis and determines that the SLE factor is $10,000 and the ARO factor is 10%. What would be the ALE factor given these values?
$150
$100
$1,000
$1,500
Why are honeypots positioned in the cloud?
to isolate the honeypots from production networks
to have easier access to the honeypots
to create DMZ zones within the cloud
to have a faster solution to gather information
A cybersecurity analyst is testing a new vulnerability scanner on a system. The analyst chooses to run an intrusive credentialed scan. A few moments later, the system that was running the scan crashed. What is the most probable cause of the crash?
a hardware failure
the intrusive scan
a false positive
a false negative
The intrusive scan
An organization has experienced several data breaches over the last five years. These data breaches have cost the organization financially and damaged its reputation. The organization has hired a cybersecurity penetration team to perform a full security audit on the entire organization. This independent contractor conducted the audit and found the following vulnerabilities:
• Several user accounts allowed unauthorized and escalated privileges.
• Systems and information without formal authorization.
What two steps can the organization take to mitigate these risks? (Choose two.)
terminate access and reset all passwords
adopt a no reuse of passwords on different applications policy
log when elevated privileges are used
assign the least privilege to perform the given task
Ethicsl hacker review please,?
The manager of a new data center requisitions magnetic door locks. The locks will require employees to swipe an ID card to open. Which type of security control is being implemented?
I added all your questions. Thank you for sharing.
Which type of evidence cannot prove an IT security fact on its own?
What three tasks are accomplished by a comprehensive security policy? (Choose three.)
To ensure that the chain of custody is maintained, what three items should be logged about evidence that is collected and analyzed after a security incident has occurred? (Choose three.)
Which meta-feature element in the Diamond Model classifies the general type of intrusion event?
Which meta-feature element in the Diamond Model classifies the general type of intrusion event?
What key considerations does a business impact analysis (BIA) examine?
Choose four correct answers
Which type of controls help uncover new potential threats?
What is a statement of applicability (SOA)?
An organization is developing a data governance program that follows regulations and policies. Which role in the program is responsible for ensuring compliance with policies and procedures, assigning the proper classification to information assets, and determining the criteria for accessing information assets?
Which two classes of metrics are included in the CVSS Base Metric Group? (Choose two.)
Which step in the Vulnerability Management Life Cycle performs inventory of all assets across the network and identifies host details, including operating system and open services?
What key considerations does a business impact analysis (BIA) examine?
* the mean/average time between failures
* the mean/average time to repair an asset
* the average lifespan of an asset
* the maximum time the system/network/application can be down
A company is preparing for an ISMS audit. Match the right control for each control objective.
Place the options in the following order:
A clean desk policy will be implemented.
To prevent loss, damage, theft or compromise of sensitive data
Employees will be required to report any observed or suspected information security weakness.
To ensure a consistent and effective approach to the management of information security incidents
Rules regarding the installation of softwareby employess will be established and implemented.
To prevent exploitation of software vulnerabilities
What is a statement of applicability (SOA)?