1.4.2 Governance and Compliance Quiz Answers
1.4.2 Governance and Compliance Quiz. Cyber Threat Management Module 1 Quiz Answers
1. Which of the following principles is used by the U.S. government in its access control models?
- Job rotation
- Separation of duties
- Need to know
- Mandatory vacations
Explanation: Employees in an organization are typically granted access to the data and information that they need to do their job. The U.S. government uses the “need to know” principle in its access control models.
2. An organization has experienced several incidents involving employees downloading unauthorized software and using unauthorized websites and personal USB devices. What measures could the organization implement to manage these threats? (Choose three correct answers)
- Implement disciplinary action
- Monitor all employee activity
- Disable USB access
- Provide security awareness training
- Use content filtering
- Run computers from a central server rather than localized hard drives
Explanation: An organization should implement measures to manage user threats, including:
- Conduct security awareness training to prevent employees from falling victim to phishing scams.
- Enabling content filtering to permit or deny specific domains in accordance with acceptable use policies.
- Disabling internal CD drives and USB ports.
- Enabling automatic antimalware scans for inserted media drives, files, and email attachments.
- Allocating write and delete permissions to the data owner only.
3. The ability to carry out highly specialized review and evaluation of incoming cybersecurity information to determine if it is useful for intelligence is covered in what category of the National Cybersecurity Workforce Framework?
- Protect and defend
- Oversight and development
- Security provision
- Analyze
Explanation: The National Institute of Standards and Technologies (NIST) created the National Cybersecurity Workforce Framework to support organizations seeking cybersecurity professionals. The framework organizes cybersecurity work into seven categories:
- Operate and maintain – Provides the support, administration and maintenance required to ensure effective and efficient IT system performance and security.
- Protect and defend – Identifies, analyzes, and mitigates threats to internal systems and networks.
- Investigate – Investigates cybersecurity events and/or cyber-attacks involving IT resources.
- Collect and operate – Provides specialized denial and deception operations and collection of cybersecurity information.
- Analyze – Performs highly specialized review and evaluation of incoming cybersecurity information to determine its usefulness for intelligence.
- Oversee and govern – Provides leadership, management, direction or development and advocacy so an organization may effectively conduct cybersecurity work.
- Securely provision – Conceptualizes, designs, procures or builds secure IT systems.
4. What act protects the personal information of students in schools?
Explanation: Family Education Records and Privacy Act (FERPA) is an US federal law that governs the access to education records. Under the law, parents must approve the disclosure of a student’s educational information to public entities prior to the actual disclosure. When a student turns 18 years old, or enters a postsecondary institution at any age, their rights under FERPA transfer from the parents to the student.
5. Match the data governance role to the correct function.
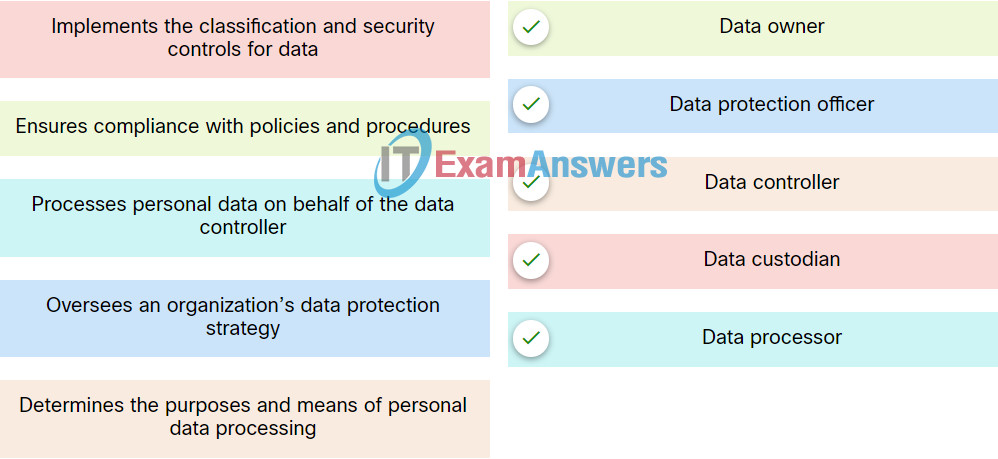
Explanation: IT security governance determines who is authorized to make decisions about cybersecurity risks within an organization. There are several key roles in good data governance programs:
- Data owner -A person who ensures compliance with policies and procedures, assigns the proper classification to information assets, and determines the criteria for accessing information assets.
- Data controller – A person who determines the purposes for which, and the way in which, personal data is processed.
- Data custodian – A person who implements the classification and security controls for the data in accordance with the rules set out by the data owner.
- Data steward – A person who ensures that data supports an organization’s business needs and meets regulatory requirements.
- Data protection officer – A person who oversees an organization’s data protection strategy.
6. Cybersecurity professionals may have access to sensitive data. What one factor should they understand to help them make informed ethical decisions in relation to this data?
- Partnerships with third parties
- Laws governing the data
- A potential bonus
- Cloud provider agreements
Explanation: Professional ethics are principles that govern the behavior of a person or group in a business environment. A cybersecurity specialist needs to understand both the law and the interest of the organization to be able to make right decisions.
7. Which of the following frameworks identifies controls based on the latest information about common cyber attacks and provides benchmarks for various platforms?
- CIS
- CSA
- The National Cybersecurity Workforce
- ISO
Explanation: The Center for Internet Security (CIS) developed a set of critical security controls to help organizations with different levels of resources and expertise at their disposal to improve their cyber defenses.
8. What law protects the privacy of an employee’s personal information from being shared with third parties?
Explanation: The Gramm-Leach-Bliley Act (GLBA) is a piece of legislation provides opt-out provisions for individuals, putting them in control of how the information they share with an organization during a business transaction is used. The GLBA restricts information sharing with third party organizations.
9. What federal act law would an individual be subject to if they knowingly accessed a government computer without permission?
Explanation: The Computer Fraud and Abuse Act (CFAA) is a US law enacted in 1986. CFAA prohibits unauthorized access to computer systems. Knowingly accessing a government computer without permission or accessing any computer used in or affecting interstate or foreign commerce is a criminal offense.
10. What do penetration tests and red team exercises achieve?
- They simulate attacks to gauge the security capabilities of an organization.
- They provide audit controls for all NetBIOS connections made.
- They provide a list of malware that has successfully penetrated the firewall.
- They provide audit trails for all TCP connections in place at any given time.
Explanation: Organizations with significant resources and cybersecurity expertise run penetration tests and red team exercises (simulated attack exercises) to gauge the security capabilities of an organization.
11. What is the function of the Cloud Security Alliance (CSA)?
- It provides security guidance to any organization that uses cloud computing.
- It audits the CIA Triad objectives.
- It produces a statement of applicability (SOA) which stipulates control objectives and audit controls to be implemented.
- It ensures total compliance with the ISO 27000 standards.
Explanation: The Cloud Security Alliance (CSA) provides security guidance to any organization that uses cloud computing or wants to assess the overall security risk of a cloud provider.
12. What is the primary goal of IT security governance?
- To provide oversight to ensure that risks are adequately mitigated
- To define a set of controls that an organization should implement
- To make decisions to mitigate risk
- To provide a set of policies and procedures to manage sensitive data
Explanation: IT security governance demonstrates accountability and provides oversight to ensure that any risks are adequately mitigated and that security strategies are aligned with the organization’s business objectives and are compliant with regulations.

