How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
Cyber Threat Management: My Knowledge Check Answers
1. Match the network security testing tool with the correct function. (Not all options are used.)
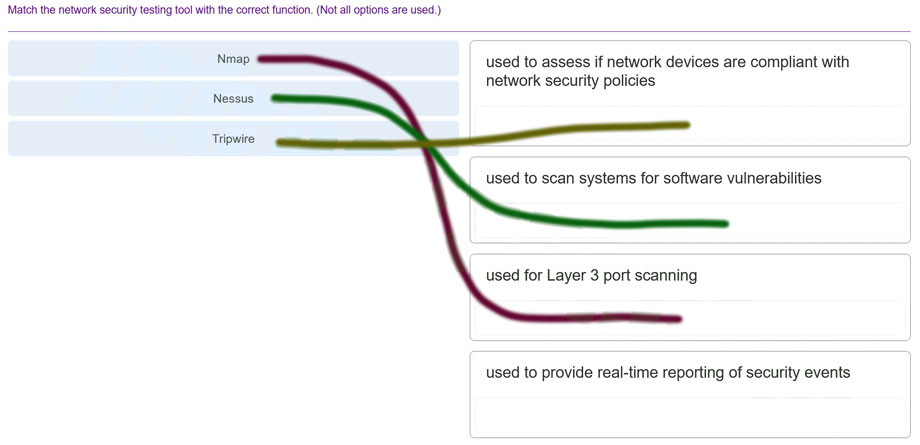
Explanation: Place the options in the following order:
| used to assess if network devices are compliant with network security policies |
Tripwire |
| used to scan systems for software vulnerabilities |
Nessus |
| used for Layer 3 port scanning |
Nmap |
2. In which step of the NIST incident response process does the CSIRT perform an analysis to determine which networks, systems, or applications are affected; who or what originated the incident; and how the incident is occurring?
- scoping
- detection
- incident notification
- attacker identification
Explanation: In the detection and analysis phase of the NIST incident response process life cycle, the CSIRT should immediately perform an initial analysis to determine the scope of the incident, such as which networks, systems, or applications are affected; who or what originated the incident; and how the incident is occurring.
3. What act protects the personal information of students in schools?
Explanation: Family Education Records and Privacy Act (FERPA) is an US federal law that governs the access to education records. Under the law, parents must approve the disclosure of a student’s educational information to public entities prior to the actual disclosure. When a student turns 18 years old, or enters a postsecondary institution at any age, their rights under FERPA transfer from the parents to the student.
4. The manager of a new data center requisitions magnetic door locks. The locks will require employees to swipe an ID card to open. Which type of security control is being implemented?
- preventive
- recovery
- corrective
- compensative
Explanation: Preventive security controls prevent unwanted or unauthorized activities from occurring and/or apply restrictions to authorized users.
5. When establishing a network profile for an organization, which element describes the time between the establishment of a data flow and its termination?
- total throughput
- session duration
- routing protocol convergence
- bandwidth of the Internet connection
Explanation: A network profile should include some important elements, such as the following:
- Total throughput – the amount of data passing from a given source to a given destination in a given period of time
- Session duration – the time between the establishment of a data flow and its termination
- Ports used – a list of TCP or UDP processes that are available to accept data
- Critical asset address space – the IP addresses or the logical location of essential systems or data
6. What do penetration tests and red team exercises achieve?
- They provide a list of malware that has successfully penetrated the firewall.
- They provide audit controls for all NetBIOS connections made.
- They provide audit trails for all TCP connections in place at any given time.
- They simulate attacks to gauge the security capabilities of an organization.
Explanation: Organizations with significant resources and cybersecurity expertise run penetration tests and red team exercises (simulated attack exercises) to gauge the security capabilities of an organization.
7. Which approach provides automated tools allowing an organization to collect data about security threats from various sources?
- NETCAT
- SOAR
- Nmap
- SuperScan
Explanation: Orchestration Automation and Response (SOAR) tools allow an organization to collect data about security threats from various sources, and respond to low-level events without human intervention.
8. How does network scanning help assess operations security?
- It can log abnormal activity.
- It can detect weak or blank passwords.
- It can detect open TCP ports on network systems.
- It can simulate attacks from malicious sources.
Explanation: Network scanning can help a network administrator strengthen the security of the network and systems by identifying open TCP and UDP ports that could be targets of an attack.
9. What type of exercise interrupts services to verify that all aspects of a business continuity plan are able to respond to a certain type of incident?
- Tabletop exercise
- Functional test
- Operational exercise
Explanation: Operational exercises: At the most extreme are full operational exercises, or simulations. These are designed to interrupt services to verify that all aspects of a plan are in place and sufficient to respond to the type of incident that is being simulated.
10. An organization is developing a data governance program that follows regulations and policies. Which role in the program is responsible for ensuring compliance with policies and procedures, assigning the proper classification to information assets, and determining the criteria for accessing information assets?
- data owner
- data controller
- data custodian
- data protection officer
11. What will a threat actor do to create a back door on a compromised target according to the Cyber Kill Chain model?
- Collect and exfiltrate data.
- Add services and autorun keys.
- Obtain an automated tool to deliver the malware payload.
- Open a two-way communications channel to the CnC infrastructure.
Explanation: Once a target system is compromised, the threat actor will establish a back door into the system to allow for continued access to the target. Adding services and autorun keys is a way to create a point of persistent access.
12. What is the purpose of the policy element in a computer security incident response capability of an organization, as recommended by NIST?
- It details how incidents should be handled based on the organizational mission and functions.
- It defines how the incident response teams will communicate with the rest of the organization and with other organizations.
- It provides metrics for measuring the incident response capability and effectiveness.
- It provides a roadmap for maturing the incident response capability.
Explanation: NIST recommends creating policies, plans, and procedures for establishing and maintaining a CSIRC. A purpose of the policy element is to detail how incidents should be handled based on the mission and functions of an organization.
13. Which network security tool can detect open TCP and UDP ports on most versions of Microsoft Windows?
- SuperScan
- Nmap
- Zenmap
- L0phtcrack
Explanation: There are various network security tools available for network security testing and evaluation. L0phtcrack can be used to perform password auditing and recovery. SuperScan is a Microsoft port scanning software that detects open TCP and UDP ports on systems. Nmap and Zenmap are low-level network scanners available to the public.
14. A cybersecurity analyst is performing a CVSS assessment on an attack where a web link was sent to several employees. Once clicked, an internal attack was launched. Which CVSS Base Metric Group Exploitability metric is used to document that the user had to click on the link in order for the attack to occur?
- availability requirement
- integrity requirement
- scope
- user interaction
Explanation: The CVSS Base Metric Group has the following metrics: attack vector, attack complexity, privileges required, user interaction, and scope. The user interaction metric expresses the presence or absence of the requirement for user interaction in order for an exploit to be successful.
15. A breach occurs in a company that processes credit card information. Which industry specific law governs credit card data protection?
Explanation: The Payment Card Industry Data Security Standard (PCI DSS) governs how to protect credit card data as merchants and banks exchange transactions.
16. Which type of security control includes backup and restore operations, as well as fault-tolerant data storage?
- deterrent
- recovery
- detection
- compensative
Explanation: Recovery security controls restore resources, functions and capabilities back to a normal state after a violation of a security policy.
17. An organization has hired a former hacker to test how well the organization would tolerate a real attack by using malicious techniques. What type of testing is the hacker performing for the organization?
- reconnaissance
- penetration
- vulnerability
- sniffing
Explanation: A penetration test is a safe way for an organization to test systems for weakness by using the same malicious techniques that are used by real hackers.
18. According to NIST, which step in the digital forensics process involves identifying potential sources of forensic data, its acquisition, handling, and storage?
- collection
- examination
- analysis
- reporting
Explanation: NIST describes the digital forensics process as involving the following four steps:
- Collection – the identification of potential sources of forensic data and acquisition, handling, and storage of that data.
- Examination – assessing and extracting relevant information from the collected data. This may involve decompression or decryption of the data.
- Analysis – drawing conclusions from the data. Salient features, such as people, places, times, events, and so on should be documented.
- Reporting – preparing and presenting information that resulted from the analysis. Reporting should be impartial and alternative explanations should be offered if appropriate.
19. The laptop of an attacker is attached to a corporate network. The attacker is examining all of the network traffic that is passing through the network interface card. Which network reconnaissance method does this scenario describe?
- bug bounty
- penetration exercise
- red team blue team
- sniffing
Explanation: Sniffing is effectively electronic eavesdropping on a network. It occurs when someone is examining all network traffic as it passes through their NIC, independent of whether the traffic is addressed to them or not. Criminals accomplish network sniffing using software, hardware, or a combination of the two.
20. Which two classes of metrics are included in the CVSS Base Metric Group? (Choose two.)
- Impact metrics
- Exploitability
- Modified Base
- Exploit Code Maturity
- Confidentiality Requirement
Explanation: The Base Metric Group of CVSS represents the characteristics of a vulnerability that are constant over time and across contexts. It contains two classes of metrics, Exploitability and Impact.
21. What network scanning tool has advanced features that allows it to use decoy hosts to mask the source of the scan?
- Nmap
- Tripwire
- Nessus
- Metasploit
Explanation: There are various network security tools available for network security testing and evaluation. Nessus can scan systems for software vulnerabilities. Metasploit is used for penetration testing and IDS signature development. Tripwire is used to assess if network devices are compliant with network security policies. Nmap is a low-level network scanner available to the public that an administrator can use to identify network layer protocol support on hosts. Nnmap can use decoy hosts to mask the source of the scan.
22. Your risk manager just distributed a chart that uses three colors to identify the level of threat to key assets in the information security systems. Red represents high level of risk, yellow represents average level of threat and green represents low level of threat. What type of risk analysis does this chart represent?
- qualitative analysis
- exposure factor analysis
- loss analysis
- quantitative analysis
Explanation: A qualitative or quantitative risk analysis is used to identify and prioritize threats to the organization.
23. In addressing an identified risk, which strategy aims to decrease the risk by taking measures to reduce vulnerability?
- risk sharing
- risk retention
- risk reduction
- risk avoidance
Explanation: There are four potential strategies for responding to risks that have been identified:
- Risk avoidance – Stop performing the activities that create risk.
- Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
- Risk sharing – Shift some of the risk to other parties.
- Risk retention – Accept the risk and its consequences.
24. Which service is provided by the Cisco Talos Group?
- preventing online malware from affecting end user devices
- preventing viruses from affecting end user devices
- scanning updates for malware code
- collecting information about active, existing, and emerging threats
Explanation: The Cisco Talos group collects information about active, existing, and emerging threats which can be used by Cisco Security products in real time to provide fast and effective security solutions.
25. Cybersecurity professionals may have access to sensitive data. What one factor should they understand to help them make informed ethical decisions in relation to this data?
- A potential bonus
- Laws governing the data
- Partnerships with third parties
- Cloud provider agreements
Explanation: Professional ethics are principles that govern the behavior of a person or group in a business environment. A cybersecurity specialist needs to understand both the law and the interest of the organization to be able to make right decisions.
26. What is the first step in the risk management process that helps to reduce the impact of threats and vulnerabilities?
- Frame the risk.
- Assess the risk.
- Monitor the risk.
- Respond to the risk.
Explanation: Risk management is a formal process that reduces the impact of threats and vulnerabilities. The process involves four general steps:
- Frame the risk – Identify the threats throughout the organization that increase risk.
- Assess the risk – Once a risk has been identified, it is assessed and analyzed to determine the severity that the threat poses.
- Respond to the risk – Develop an action plan to reduce overall organization risk exposure. Management should rank and prioritize threats and a team determines how to respond to each threat.
- Monitor the risk – Continuously review risk reductions due to elimination, mitigation and transfer actions.
27. Which NIST-defined incident response stakeholder is responsible for coordinating incident response with other stakeholders and minimizing the damage of an incident?
- IT support
- the legal department
- management
- human resources
Explanation: The management team creates the policies, designs the budget, and is in charge of staffing all departments. Management is also responsible for coordinating the incident response with other stakeholders and minimizing the damage of an incident.
28. Which penetration test phase is concerned with conducting reconnaissance to gain information about the target network or device?
- planning
- discovery
- attack
- reporting
Explanation: There are four phases in performing network penetration tests: planning, discovery, attack, and reporting.
Phase 2, discovery, is concerned with using passive and active reconnaissance techniques to gather information.
29. According to the Cyber Kill Chain model, after a weapon is delivered to a targeted system, what is the next step that a threat actor would take?
- installation
- exploitation
- weaponization
- action on objectives
Explanation: The Cyber Kill Chain specifies seven steps (or phases) and sequences that a threat actor must complete to accomplish an attack:
- Reconnaissance – The threat actor performs research, gathers intelligence, and selects targets.
- Weaponization – The threat actor uses the information from the reconnaissance phase to develop a weapon against specific targeted systems.
- Delivery – The weapon is transmitted to the target using a delivery vector.
- Exploitation – The threat actor uses the weapon delivered to break the vulnerability and gain control of the target.
- Installation – The threat actor establishes a back door into the system to allow for continued access to the target.
- Command and Control (CnC) – The threat actor establishes command and control (CnC) with the target system.
- Action on Objectives – The threat actor is able to take action on the target system, thus achieving the original objective.
30. The CEO of a company is concerned that if a data breach should occur and customer data is exposed, the company could be sued. The CEO makes the decision to buy insurance for the company. What type of risk mitigation is the CEO implementing?
- avoidance
- transference
- reduction
- mitigation
Explanation: Buying insurance transfers the risk to a third party.
31. Which meta-feature element in the Diamond Model describes tools and information (such as software, black hat knowledge base, username and password) that the adversary uses for the intrusion event?
- results
- direction
- resources
- methodology
Explanation: The resources element in the Diamond Model is used to describe one or more external resources used by the adversary for the intrusion event. The resources include software, knowledge gained by the adversary, information (e.g., username/passwords), and assets to carry out the attack.
32. What network security testing tool has the ability to provide details on the source of suspicious network activity?
- SIEM
- SuperScan
- Tripwire
- Zenmap
Explanation: There are various network security tools available for network security testing and evaluation. SuperScan is a Microsoft port scanning software that detects open TCP and UDP ports on systems. Nmap and Zenmap are low-level network scanners available to the public. Tripwire is used to assess if network devices are compliant with network security policies. SIEM is used to provide real-time reporting of security events on the network.
33. What is a MITRE ATT&CK framework?
- a collection of malware exploits and prevention solutions
- guidelines for the collection of digital evidence
- a knowledge base of threat actor behavior
- documented processes and procedures for digital forensic analysis
Explanation: The MITRE framework is a global knowledge base of threat actor behavior. It is based on observation and analysis of real-world exploits with the purpose of describing the behavior of the attacker, not the attack itself. It is designed to enable automated information sharing by defining data structures for the exchange of information between its community of users and MITRE.
34. The IT security personnel of an organization notice that the web server deployed in the DMZ is frequently targeted by threat actors. The decision is made to implement a patch management system to manage the server. Which risk management strategy method is being used to respond to the identified risk?
- risk sharing
- risk retention
- risk reduction
- risk avoidance
Explanation: There are four potential strategies for responding to risks that have been identified:
Risk avoidance – Stop performing the activities that create risk.
Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
Risk sharing – Shift some of the risk to other parties.
Risk retention – Accept the risk and its consequences.
35. A user is asked to evaluate the security posture of a company. The user looks at past attempts to break into the company and evaluates the threats and exposures to create a report. Which type of risk analysis could the user perform?
- qualitative
- objective
- subjective
- opinion
Explanation: Two approaches to risk analysis are quantitative and qualitative. Qualitative analysis is based on opinions and scenarios.
36. In which situation would a detective control be warranted?
- after the organization has experienced a breach in order to restore everything back to a normal state
- when the organization cannot use a guard dog, so it is necessary to consider an alternative
- when the organization needs to look for prohibited activity
- when the organization needs to repair damage
Explanation: Access control prevents an unauthorized user from gaining access to sensitive data and networked systems. There are several technologies used to implement effective access control strategies.
37. How does FireEye detect and prevent zero-day attacks?
- by keeping a detailed analysis of all viruses and malware
- by establishing an authentication parameter prior to any data exchange
- by only accepting encrypted data packets that validate against their configured hash values
- by addressing all stages of an attack lifecycle with a signature-less engine utilizing stateful attack analysis
Explanation: FireEye uses a three-pronged approach combining security intelligence, security expertise, and technology. It addresses all stages of an attack lifecycle with a signature-less engine utilizing stateful attack analysis to detect zero-day threats.
38. What is a statement of applicability (SOA)?
- It stipulates total compliance with NIST.
- It sets out a broad framework of network protocols used and their implementations.
- It is used as an audit point for network device implementation.
- It allows for the tailoring of available control objectives and controls to best meet its priorities around confidentiality, integrity, and availability
39. When a network baseline is being established for an organization, which network profile element indicates the time between the establishment of a data flow and its termination?
- ports used
- total throughput
- session duration
- critical asset address space
Explanation: Important elements of a network profile include:
- Total throughput – the amount of data passing from a given source to a given destination in a given period of time
- Session duration – the time between the establishment of a data flow and its termination
- Ports used – a list of TCP or UDP processes that are available to accept data
- Critical asset address space – the IP addresses or the logical location of essential systems or data
40. Match the stages in the risk management process to the description.
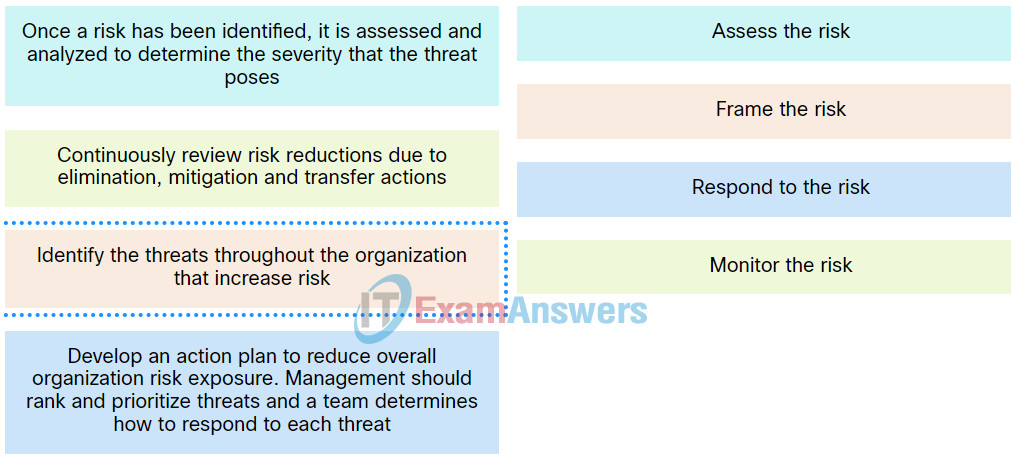
Explanation: Place the options in the following order:
| Develop an action plan to reduce overall organization risk exposure. Management should rank and prioritize threats and a team determines how to respond to each threat. |
Respond to the risk. |
| Once a risk has been identified, it is assessed and analyzed to determine the severity that the threat poses. |
Assess the risk. |
| Continuously review risk reductions due to elimination, mitigation and transfer actions. |
Monitor the risk. |
| Identify the threats throughout the organization that increase risk. |
Frame the risk. |
41. Which term is used in the Diamond Model of intrusion to describe a tool that a threat actor uses toward a target system?
- adversary
- capability
- infrastructure
- weaponization
Explanation: The Diamond Model of intrusion contains four parts:
- Adversary – the parties responsible for the intrusion
- Capability – a tool or technique that the adversary uses to attack the victim
- Infrastructure – the network path or paths that the adversaries use to establish and maintain command and control over their capabilities
- Victim – the target of the attack
42. What federal act law would an individual be subject to if they knowingly accessed a government computer without permission?
Explanation: Enacted in 1986 as an amendment to the Comprehensive Crime Control Act of 1984, CFAA prohibits unauthorized access to computer systems. Knowingly accessing a government computer without permission or accessing any computer used in or affecting interstate or foreign commerce is a criminal offense. The Act also criminalizes the trafficking of passwords or similar access information, as well as knowingly transmitting a program, code or a command that results in damage.
43. Which threat intelligence sharing open standard specifies, captures, characterizes, and communicates events and properties of network operations?
Explanation: Structured Threat Information Expression (STIX) is a set of specifications for exchanging cyberthreat information between organizations. Cyber Observable Expression (CybOX) is a set of standardized schema that specifies, captures, characterizes, and communicates events and properties of network operations and that supports many cybersecurity functions. Trusted Automated Exchange of Indicator Information (TAXII) is a specification for an application layer protocol that allows the communication of CTI over HTTPS and is designed to support STIX.
44. Why would threat actors prefer to use a zero-day attack in the Cyber Kill Chain weaponization phase?
- to get a free malware package
- to launch a DoS attack toward the target
- to avoid detection by the target
- to gain faster delivery of the attack on the target
Explanation: When a threat actor prepares a weapon for an attack, the threat actor chooses an automated tool (weaponizer) that can be deployed through discovered vulnerabilities. Malware that will carry desired attacks is then built into the tool as the payload. The weapon (tool plus malware payload) will be delivered to the target system. By using a zero-day weaponizer, the threat actor hopes that the weapon will not be detected because it is unknown to security professionals and detection methods are not yet developed.
45. Which meta-feature element in the Diamond Model classifies the general type of intrusion event?
- phase
- results
- direction
- methodology
Explanation: Methodology – This is used to classify the general type of event, such as port scan, phishing, content delivery attack, syn flood, etc.
46. In what order are the steps in the vulnerability management life cycle conducted?
- discover, prioritize assets, assess, report, remediate, verify
- discover, assess, prioritize assets, report, remediate, verify
- discover, prioritize assets, assess, remediate, report, verify
- discover, prioritize assets, assess, remediate, verify, report
Explanation: There are six steps in the vulnerability management life cycle:
Discover
Prioritize assets
Assess
Report
Remediate
Verify
47. What are two tasks that can be accomplished with the Nmap and Zenmap network tools? (Choose two.)
- TCP and UDP port scanning
- Identification of Layer 3 protocol support on hosts
- Password auditing
- Password recovery
- Validation of IT system configuration
Explanation: Nmap is a low-level network scanner that is available to the public and which has the ability to perform port scanning, to identify open TCP and UDP ports, and perform system identification. It can also be used to identify Layer 3 protocols that are running on a system.
48. What is the workforce framework category that includes highly specialized review and evaluation of incoming cybersecurity information to determine if it is useful for intelligence?
- Protect and Defend
- Oversight and Development
- Securely Provision
- Analyze
Explanation: The “Analyze” category of the workforce framework includes specialty areas responsible for highly specialized review and evaluation of incoming cybersecurity information to determine its usefulness.
49. After containing an incident that infected user workstations with malware, what are three effective remediation procedures that an organization can take for eradication? (Choose three.)
- Use clean and recent backups to recover hosts.
- Change assigned names and passwords for all devices.
- Rebuild DHCP servers using clean installation media.
- Rebuild hosts with installation media if no backups are available.
- Update and patch the operating system and installed software of all hosts.
- Disconnect or disable all wired and wireless network adapters until the remediation is complete.
Explanation: To recover infected user workstations, use clean and recent backups or rebuild the PCs with installation media if no backups are available or they have been compromised. Also, fully update and patch the operating system and installed software of all hosts. All users are encouraged to change their passwords for the workstation or workstations they use. Rebuilding DHCP servers is needed only if they are affected by the incident.Also not all devices need to change the name and password configuration setting unless they are affected by the incident.
50. What is the primary function of (ISC2)?
- to maintain a list of common vulnerabilities and exposures (CVE) used by prominent security organizations
- to provide vendor neutral education products and career services
- to provide a weekly digest of news articles about computer security
- to maintain a detailed list of all zero-day attacks
Explanation: International Information Systems Security Certification Consortium (ISC2) is a network security organization that provides vendor neutral education products and career services.
51. If a person knowingly accesses a government computer without permission, what federal act laws would the person be subject to?
Explanation: The Computer Fraud and Abuse Act (CFAA) provides the foundation for US laws criminalizing unauthorized access to computer systems.
52. Which of the following principles is used by the U.S. government in its access control models?
- Separation of duties
- Need to know
- Job rotation
- Mandatory vacations
Explanation: Employees in an organization are typically granted access to the data and information that they need to do their job. The U.S. government uses the “need to know” principle in its access control models.
53. What is the primary function of SANS?
- to maintain the Internet Storm Center
- to maintain the list of common vulnerabilities and exposures (CVE)
- to foster cooperation and coordination in information sharing, incident prevention, and rapid reaction
- to provide vendor neutral education products and career services
Explanation: One of the primary functions of the SysAdmin, Audit, Network, Security (SANS) Institute is the maintenance of the Internet Storm Center early warning system.
54. Which security management plan specifies a component that involves tracking the location and configuration of networked devices and software across an enterprise?
- asset management
- risk management
- vulnerability management
- patch management
Explanation: Asset management involves tracking the location and configuration of networked devices and software across an enterprise.
55. Place the seven steps defined in the Cyber Kill Chain in the correct order.
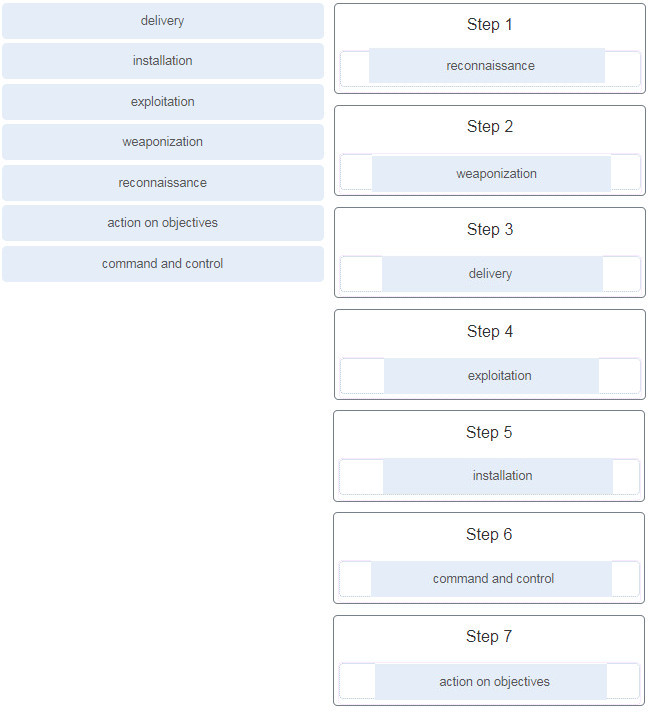
Explanation: Place the options in the following order:
| step 1 |
reconnaissance |
| step 2 |
weaponization |
| step 3 |
delivery |
| step 4 |
exploitation |
| step 5 |
installation |
| step 6 |
command and control |
| step 7 |
action on objectives |
56. Which risk mitigation strategies include outsourcing services and purchasing insurance?
- acceptance
- transfer
- avoidance
- reduction
Explanation: Risk mitigation lessens the exposure of an organization to threats and vulnerabilities by transferring, accepting, avoiding, or taking an action to reduce risk.
57. When a server profile for an organization is being established, which element describes the TCP and UDP daemons and ports that are allowed to be open on the server?
- listening ports
- service accounts
- software environment
- critical asset address space
Explanation: A server profile will often contain the following:
Listening ports – the TCP and UDP daemons and ports that are allowed to be open on the server
User accounts – the parameters defining user access and behavior
Service accounts – the definitions of the type of service that an application is allowed to run on a server
Software environment – the tasks, processes, and applications that are permitted to run on the server
58. Which framework should be recommended for establishing a comprehensive information security management system in an organization?
- ISO/IEC 27000
- ISO OSI model
- NIST/NICE framework
- CIA Triad
Explanation: A cybersecurity specialist needs to be familiar with the different frameworks and models for managing information security.
59. Match the data governance role to the correct function.
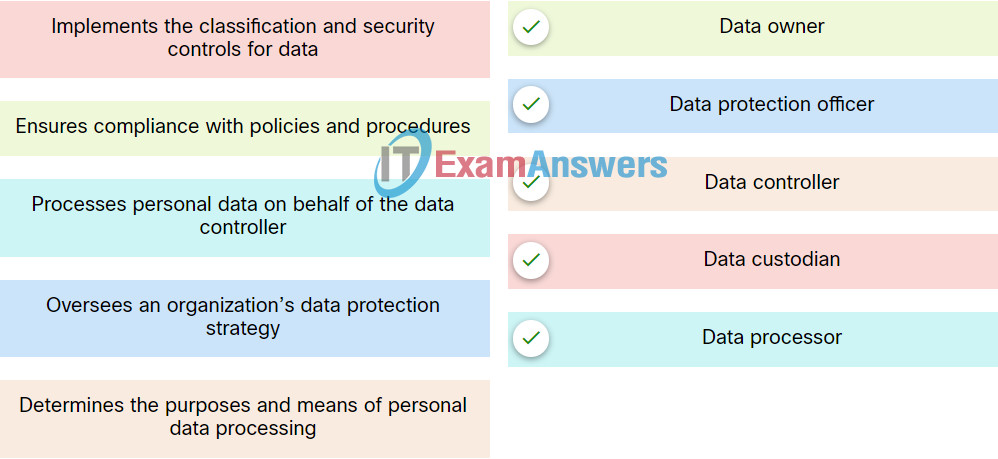
Explanation: IT security governance determines who is authorized to make decisions about cybersecurity risks within an organization. There are several key roles in good data governance programs:
- Data owner -A person who ensures compliance with policies and procedures, assigns the proper classification to information assets, and determines the criteria for accessing information assets.
- Data controller – A person who determines the purposes for which, and the way in which, personal data is processed.
- Data custodian – A person who implements the classification and security controls for the data in accordance with the rules set out by the data owner.
- Data steward – A person who ensures that data supports an organization’s business needs and meets regulatory requirements.
- Data protection officer – A person who oversees an organization’s data protection strategy.
60. What is a chain of custody?
- the documentation surrounding the preservation of evidence related to an incident
- a list of all of the stakeholders that were exploited by an attacker
- the disciplinary measures an organization may perform if an incident is caused by an employee
- a plan ensuring that each party involved in an incident response understands how to collect evidence
Explanation: A chain of custody refers to the documentation of evidence collected about an incident that is used by authorities during an investigation.
61. Which statement describes the threat-vulnerability (T-V) pairing?
- It is the advisory notice from a vulnerability research center.
- It is the comparison between known malware and system risks.
- It is the detection of malware against a central vulnerability research center.
- It is the identification of threats and vulnerabilities and the matching of threats with vulnerabilities.
Explanation: A mandatory activity in risk assessment is the identification of threats and vulnerabilities and the matching of threats with vulnerabilities, also called threat-vulnerability (T-V) pairing.
62. Which metric in the CVSS Base Metric Group is used with an attack vector?
- the proximity of the threat actor to the vulnerability
- the determination whether the initial authority changes to a second authority during the exploit
- the presence or absence of the requirement for user interaction in order for an exploit to be successful
- the number of components, software, hardware, or networks, that are beyond the control of the attacker and that must be present in order for a vulnerability to be successfully exploited
Explanation: The attack vector is one of several metrics defined in the Common Vulnerability Scoring System (CVSS) Base Metric Group Exploitability metrics. The attack vector is how close the threat actor is to the vulnerable component. The farther away the threat actor is to the component, the higher the severity because threat actors close to the network are easier to detect and mitigate.
63. What is the primary objective of a threat intelligence platform (TIP)?
- to aggregate the data in one place and present it in a comprehensible and usable format
- to provide a security operations platform that integrates and enhances diverse security tools and threat intelligence
- to provide a specification for an application layer protocol that allows the communication of CTI over HTTPS
- to provide a standardized schema for specifying, capturing, characterizing, and communicating events and properties of network operations
Explanation: A threat intelligence platform (TIP) centralizes the collection of threat data from numerous data sources and formats. TIP is designed to aggregate the data in one place and present it in a comprehensible and usable format. This is especially important as the volume of threat intelligence data can be overwhelming.
64. To ensure that the chain of custody is maintained, what three items should be logged about evidence that is collected and analyzed after a security incident has occurred? (Choose three.)
- measures used to prevent an incident
- location of all evidence
- time and date the evidence was collected
- serial numbers and hostnames of devices used as evidence
- extent of the damage to resources and assets
- vulnerabilities that were exploited in an attack
Explanation: A chain of custody refers to the proper accounting of evidence collected about an incident that is used as part of an investigation. The chain of custody should include the location of all evidence, the identifying information of all evidence such as serial numbers and hostnames, identifying information about all persons handing the evidence, and the time and date that the evidence was collected.
65. Match the network profile element to the description.
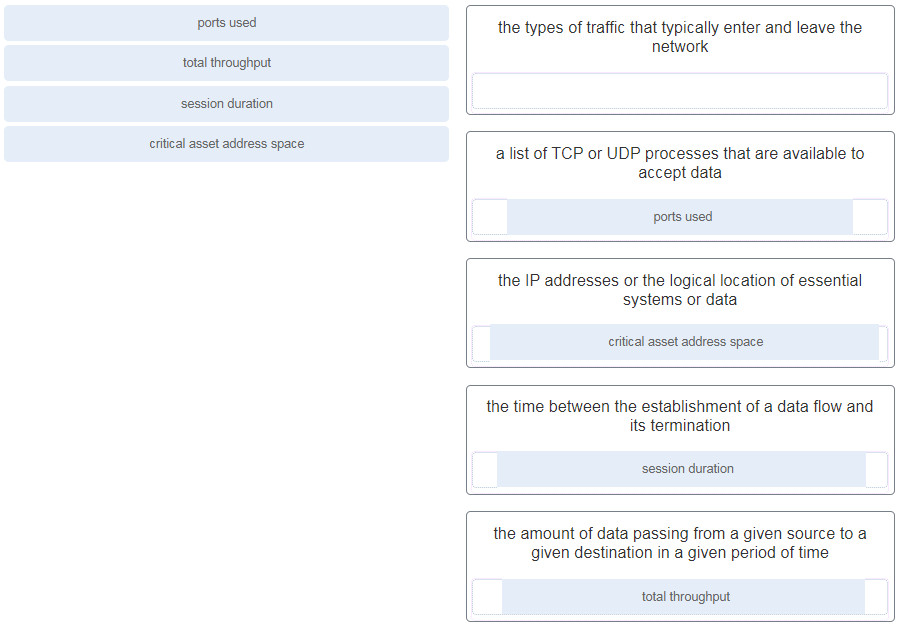
Explanation: Important elements of a network profile include:
- Total throughput – the amount of data passing from a given source to a given destination in a given period of time
- Session duration – the time between the establishment of a data flow and its termination
- Ports used – a list of TCP or UDP processes that are available to accept data
- Critical asset address space – the IP addresses or the logical location of essential systems or data
66. What information does the SIEM network security management tool provide to network administrators?
- real time reporting and analysis of security events
- detection of open TCP and UDP ports
- assessment of system security configurations
- a map of network systems and services
Explanation: SIEM, which is a combination of Security Information Management and Security Event Management products, is used for forensic analysis and provides real-time reporting of security events.
67. Which action should be included in a plan element that is part of a computer security incident response capability (CSIRC)?
- Detail how incidents should be handled based on the mission and functions of an organization.
- Prioritize severity ratings of security incidents.
- Create an organizational structure and definition of roles, responsibilities, and levels of authority.
- Develop metrics for measuring the incident response capability and its effectiveness.
Explanation: NIST recommends creating policies, plans, and procedures for establishing and maintaining a CSIRC. A purpose of the plan element is to develop metrics for measuring the incident response capability and its effectiveness.
68. Which statement describes Trusted Automated Exchange of Indicator Information (TAXII)?
- It is a dynamic database of real-time vulnerabilities.
- It is a set of specifications for exchanging cyber threat information between organizations.
- It is a signature-less engine utilizing stateful attack analysis to detect zero-day threats.
- It is the specification for an application layer protocol that allows the communication of CTI over HTTPS.
Explanation: Trusted Automated Exchange of Indicator Information (TAXII) is the specification for an application layer protocol that allows the communication of CTI over HTTPS. TAXII is designed to support Structured Threat Information Expression (STIX).
69. What three tasks are accomplished by a comprehensive security policy? (Choose three.)
- sets rules for expected behavior
- defines legal consequences of violations
- gives security staff the backing of management
- vagueness
- useful for management
- is not legally binding
Explanation: The security policy of an organization accomplishes several tasks:
- It demonstrates the commitment to security by an organization.
- It sets the rules for expected behavior.
- It ensures consistency in system operations, and software and hardware acquisition use and maintenance.
- It defines the legal consequences of violations.
- It gives security staff the backing of management.
70. What type of security test uses simulated attacks to determine possible consequences of a real threat?
- penetration testing
- integrity checking
- vulnerability scanning
- network scanning
Explanation: There are many security tests that can be used to assess a network. Penetration testing is used to determine the possible consequences of successful attacks on the network. Integrity checking is used to detect and report changes made to systems. Vulnerability scanning is used to find weaknesses and misconfigurations on network systems. Network scanning is used to discover available resources on the network.
71. Which two types of controls are effective after a violation of a security policy occurs? (Choose two.)
- corrective
- recovery
- preventive
- deterrent
- compensative
Explanation: Organizations will implement corrective access controls after a system experiences a threat. Recovery security controls restore resources, functions and capabilities back to a normal state after a violation of a security policy.
72. Which type of evaluation includes the assessment of the likelihood of an attack, the type of threat actor likely to perpetrate such an attack, and what the consequences could be to the organization if the exploit is successful?
- risk analysis
- vulnerability identification
- penetration testing
- server profiling
Explanation: When evaluating a cyber security risk, the analyst takes into account the likelihood of an attack occurring, who the potential threat actors might be, as well as the consequences that might occur if the exploit is successful.
73. Which step in the Vulnerability Management Life Cycle performs inventory of all assets across the network and identifies host details, including operating system and open services?
- assess
- discover
- remediate
- prioritize assets
Explanation: The steps in the Vulnerability Management Life Cycle include these:
- Discover – inventory all assets across the network and identify host details, including operating systems and open services to identify vulnerabilities
- Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations
- Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification
- Report – measure the level of business risk associated with your assets according to your security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities
- Remediate – prioritize according to business risk and fix vulnerabilities in order of risk
- Verify – verify that threats have been eliminated through follow-up audits
74. What is a characteristic of CybOX?
- It is a set of specifications for exchanging cyberthreat information between organizations.
- It is the specification for an application layer protocol that allows the communication of CTI over HTTPS.
- It is a set of standardized schemata for specifying, capturing, characterizing, and communicating events and properties of network operations.
- It enables the real-time exchange of cyberthreat indicators between the U.S. Federal Government and the private sector.
Explanation: CybOX is an open standards set of standardized schemata for specifying, capturing, characterizing, and communicating events and properties of network operations that support many cybersecurity functions.
75. What network testing tool would an administrator use to assess and validate system configurations against security policies and compliance standards?
- Tripwire
- Nessus
- L0phtcrack
- Metasploit
Explanation: Tripwire – This tool assesses and validates IT configurations against internal policies, compliance standards, and security best practices.
76. Which meta-feature element in the Diamond Model describes information gained by the adversary?
- results
- direction
- resources
- methodology
Explanation: The meta-feature element results are used to delineate what the adversary gained from the intrusion event.
77. What are the steps in the vulnerability management life cycle?
- discover, prioritize assets, assess, report, remediate, verify
- detect, analyze, recover, respond
- identify, protect, detect, respond, recover
- plan, do, act, check
Explanation: There are six steps in the vulnerability management life cycle:
- Discover
- Prioritize assets
- Assess
- Report
- Remediate
- Verify
78. What is the function of the Cloud Security Alliance (CSA)?
- It audits the CIA Triad objectives.
- It provides security guidance to any organization that uses cloud computing.
- It ensures total compliance with the ISO 27000 standards.
- It produces a statement of applicability (SOA) which stipulates control objectives and audit controls to be implemented.
Explanation: The Cloud Security Alliance (CSA) provides security guidance to any organization that uses cloud computing or wants to assess the overall security risk of a cloud provider.





