Checkpoint Exam: Vulnerability Assessment and Risk Management – Cyber Threat Management (CyberTM) Module 1 – 5 Group Exam Answers
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
- Use content filtering.
- Disable CD and USB access.
- Provide security awareness training.
- Monitor all activity by the users.
- Change to thin clients.
- Implement disciplinary action.
Explanation: Users may be unaware of their actions if not educated in the reasons why their actions can cause a problem with the computer. By implementing several technical and nontechnical practices, the threat can be reduced.
2. Which threat is mitigated through user awareness training and tying security awareness to performance reviews?
- user-related threats
- physical threats
- device-related threats
- cloud-related threats
Explanation: Cybersecurity domains provide a framework for evaluating and implementing controls to protect the assets of an organization. Each domain has various countermeasures available to manage threats.
3. What is the workforce framework category that includes highly specialized review and evaluation of incoming cybersecurity information to determine if it is useful for intelligence?
- Analyze
- Oversight and Development
- Securely Provision
- Protect and Defend
Explanation: The “Analyze” category of the workforce framework includes specialty areas responsible for highly specialized review and evaluation of incoming cybersecurity information to determine its usefulness.
4. A breach occurs in a company that processes credit card information. Which industry specific law governs credit card data protection?
Explanation: The Payment Card Industry Data Security Standard (PCI DSS) governs how to protect credit card data as merchants and banks exchange transactions.
5. As part of HR policy in a company, an individual may opt-out of having information shared with any third party other than the employer. Which law protects the privacy of personal shared information?
Explanation: The Gramm-Leach-Bliley Act (GLBA) includes privacy provisions for individuals and provides opt-out methods to restrict information sharing with third-party firms.
6. What type of network security test can detect and report changes made to network systems?
- integrity checking
- network scanning
- penetration testing
- vulnerability scanning
Explanation: Integrity checking is used to detect and report changes made to systems. Vulnerability scanning is used to find weaknesses and misconfigurations on network systems. Network scanning is used to discover available resources on the network.
7. A security professional is asked to perform an analysis of the current state of a company network. What tool would the security professional use to scan the network only for security risks?
- pentest
- malware
- packet analyzer
- vulnerability scanner
Explanation: Vulnerability scanners are commonly used to scan for the following vulnerabilities:
Use of default passwords or common passwords
Missing patches
Open ports
Misconfiguration of operating systems and software
Active IP addresses
8. What information does the SIEM network security management tool provide to network administrators?
- real time reporting and analysis of security events
- a map of network systems and services
- assessment of system security configurations
- detection of open TCP and UDP ports
Explanation: SIEM, which is a combination of Security Information Management and Security Event Management products, is used for forensic analysis and provides real-time reporting of security events.
9. What type of network security test uses simulated attacks to determine the feasibility of an attack as well as the possible consequences if the attack occurs?
- integrity checking
- penetration testing
- vulnerability scanning
- network scanning
Explanation: There are many tests that are used by security specialists to assess the status of a system. They include the following:
– penetration testing to determine the feasibility of attacks
– network scanning to scan for and identify open TCP ports
– integrity checking to check for changes that have occurred in the system
– vulnerability scanning to detect potential weaknesses in systems
10. What network testing tool would an administrator use to assess and validate system configurations against security policies and compliance standards?
- Nessus
- Tripwire
- L0phtcrack
- Metasploit
Explanation: Tripwire – This tool assesses and validates IT configurations against internal policies, compliance standards, and security best practices.
11. Which statement describes Trusted Automated Exchange of Indicator Information (TAXII)?
- It is a dynamic database of real-time vulnerabilities.
- It is a signature-less engine utilizing stateful attack analysis to detect zero-day threats.
- It is the specification for an application layer protocol that allows the communication of CTI over HTTPS.
- It is a set of specifications for exchanging cyber threat information between organizations.
Explanation: Trusted Automated Exchange of Indicator Information (TAXII) is the specification for an application layer protocol that allows the communication of CTI over HTTPS. TAXII is designed to support Structured Threat Information Expression (STIX).
12. How does AIS address a newly discovered threat?
- by creating response strategies against the new threat
- by enabling real-time exchange of cyberthreat indicators with U.S. Federal Government and the private sector
- by mitigating the attack with active response defense mechanisms
- by advising the U.S. Federal Government to publish internal response strategies
Explanation: AIS responds to a new threat as soon as it is recognized by immediately sharing it with U.S. Federal Government and the private sector to help them protect their networks against that particular threat.
13. Which organization defines unique CVE Identifiers for publicly known information-security vulnerabilities that make it easier to share data?
- FireEye
- DHS
- Cisco Talos
- MITRE
Explanation: The United States government sponsored the MITRE Corporation to create and maintain a catalog of known security threats called Common Vulnerabilities and Exposures (CVE). The CVE serves as a dictionary of common names (i.e., CVE Identifiers) for publicly known cybersecurity vulnerabilities.
14. In addressing an identified risk, which strategy aims to decrease the risk by taking measures to reduce vulnerability?
- risk sharing
- risk retention
- risk reduction
- risk avoidance
Explanation: There are four potential strategies for responding to risks that have been identified:
Risk avoidance – Stop performing the activities that create risk.
Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
Risk sharing – Shift some of the risk to other parties.
Risk retention – Accept the risk and its consequences.
15. Which step in the Vulnerability Management Life Cycle determines a baseline risk profile to eliminate risks based on asset criticality, vulnerability threat, and asset classification?
- verify
- assess
- discover
- prioritize assets
Explanation: The steps in the Vulnerability Management Life Cycle include these:Discover – inventory all assets across the network and identify host details, including operating systems and open services, to identify vulnerabilities
Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations
Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification
Report – measure the level of business risk associated with assets according to security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities.
Remediate – prioritize according to business risk and fix vulnerabilities in order of risk
Verify – verify that threats have been eliminated through follow-up audits
16. When establishing a network profile for an organization, which element describes the time between the establishment of a data flow and its termination?
- total throughput
- bandwidth of the Internet connection
- routing protocol convergence
- session duration
Explanation: A network profile should include some important elements, such as the following:
Total throughput – the amount of data passing from a given source to a given destination in a given period of time
Session duration – the time between the establishment of a data flow and its termination
Ports used – a list of TCP or UDP processes that are available to accept data
Critical asset address space – the IP addresses or the logical location of essential systems or data
17. Which security management plan specifies a component that involves tracking the location and configuration of networked devices and software across an enterprise?
- asset management
- patch management
- vulnerability management
- risk management
Explanation: Asset management involves tracking the location and configuration of networked devices and software across an enterprise.
18. A security analyst is investigating a cyber attack that began by compromising one file system through a vulnerability in a custom software application. The attack now appears to be affecting additional file systems under the control of another security authority. Which CVSS v3.0 base exploitability metric score is increased by this attack characteristic?
- user interaction
- privileges required
- attack complexity
- scope
Explanation: The scope metric is impacted by an exploited vulnerability that can affect resources beyond the authorized privileges of the vulnerable component or that are managed by a different security authority.
19. What are the steps in the vulnerability management life cycle?
- plan, do, act, check
- identify, protect, detect, respond, recover
- detect, analyze, recover, respond
- discover, prioritize assets, assess, report, remediate, verify
Explanation: There are six steps in the vulnerability management life cycle:
Discover
Prioritize assets
Assess
Report
Remediate
Verify
20. Why would an organization perform a quantitative risk analysis for network security threats?
- so that management has documentation about the number of security attacks that have occurred within a particular time period
- so that management can determine the number of network devices needed to inspect, analyze, and protect the corporate resources
- so that the organization knows the top areas where network security holes exist
- so that the organization can focus resources where they are most needed
Explanation: Quantitative risk analysis takes the top threats, assigns a cost value to each threat if it actually occurred, and orders the list from most expensive to least expensive. This priority list allows management to determine where to apply current resources to the threat or threats that would cost the most to the organization. The quantitative risk analysis is based on cost, but this should not be the only criterion applied when, for example, evaluating a system that provides or involves national security.
21. The team is in the process of performing a risk analysis on the database services. The information collected includes the initial value of these assets, the threats to the assets and the impact of the threats. What type of risk analysis is the team performing by calculating the annual loss expectancy?
- protection analysis
- qualitative analysis
- loss analysis
- quantitative analysis
Explanation: A qualitative or quantitative risk analysis is used to identify and prioritize threats to the organization.
22. Based on the risk management process, what should the cybersecurity team do as the next step when a cybersecurity risk is identified?
- Frame the risk.
- Monitor the risk.
- Respond to the risk.
- Assess the risk.
Explanation: Risk management is a formal process that reduces the impact of threats and vulnerabilities. The process involves four general steps:
– Frame the risk – Identify the threats throughout the organization that increase risk.
– Assess the risk – Once a risk has been identified, it is assessed and analyzed to determine the severity that the threat poses.
– Respond to the risk – Develop an action plan to reduce overall organization risk exposure. Management should rank and prioritize threats and a team determines how to respond to each threat.
– Monitor the risk – Continuously review risk reductions due to elimination, mitigation and transfer actions.
23. In which situation would a detective control be warranted?
- after the organization has experienced a breach in order to restore everything back to a normal state
- when the organization needs to repair damage
- when the organization needs to look for prohibited activity
- when the organization cannot use a guard dog, so it is necessary to consider an alternative
Explanation: Access control prevents an unauthorized user from gaining access to sensitive data and networked systems. There are several technologies used to implement effective access control strategies.
24. Which risk mitigation strategies include outsourcing services and purchasing insurance?
- transfer
- acceptance
- reduction
- avoidance
Explanation: Risk mitigation lessens the exposure of an organization to threats and vulnerabilities by transferring, accepting, avoiding, or taking an action to reduce risk.
25. In quantitative risk analysis, what term is used to represent the degree of destruction that would occur if an event took place?
- exposure factor
- single loss expectancy
- annualized rate of occurrence
- annualized loss expectancy
Explanation: Of the formulas used in quantitative risk analysis, exposure factor is used to estimate the degree of destruction that could occur from an event such as flooding or data entry error.
26. Which two values are required to calculate annual loss expectancy? (Choose two.)
- annual rate of occurrence
- asset value
- frequency factor
- exposure factor
- single loss expectancy
- quantitative loss value
Explanation: Single loss expectancy, annualized rate of occurrence, and annualized loss expectancy are used in a quantitative risk analysis
27. What are the three impact metrics contained in the CVSS 3.0 Base Metric Group? (Choose three.)
- confidentiality
- remediation level
- integrity
- attack vector
- exploit
- availability
Explanation: The Common Vulnerability Scoring System (CVSS) is a vendor-neutral, industry standard, open framework for weighing the risks of a vulnerability using a variety of metrics. CVSS uses three groups of metrics to assess vulnerability, the Base Metric Group, Temporal Metric Group, and Environmental Metric Group. The Base Metric Group has two classes of metrics (exploitability and impact). The impact metrics are rooted in the following areas: confidentiality, integrity, and availability.
28. Match the network profile element to the description.
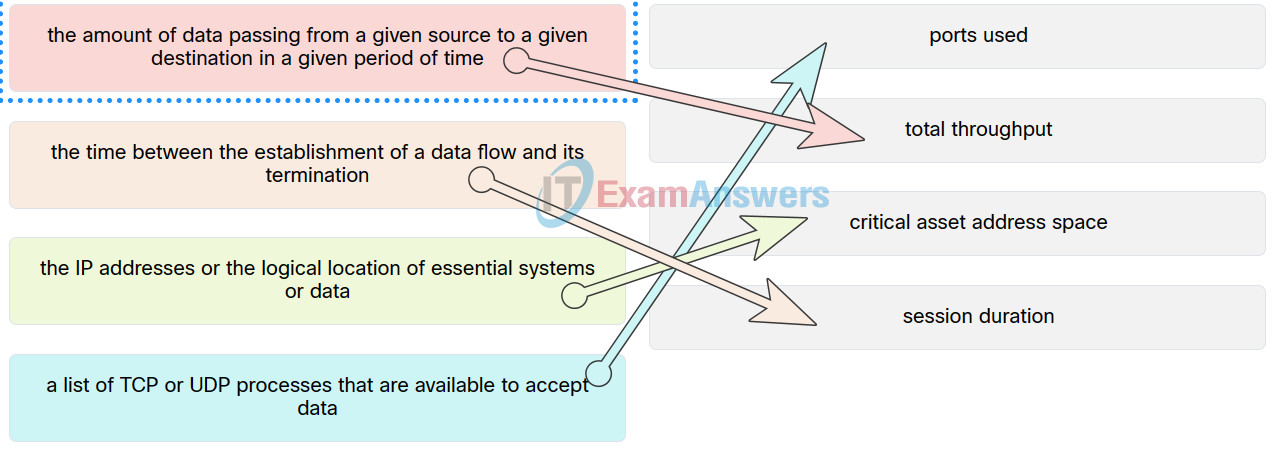
Checkpoint Exam: Vulnerability Assessment and Risk Management
Explanation: Place the options in the following order:
| a list of TCP or UDP processes that are available to accept data |
ports used |
| the IP addresses or the logical location of essential systems or data |
critical asset address space |
| the time between the establishment of a data flow and its termination |
session duration |
| the amount of data passing from a given source to a given destination in a given period of time |
total throughput |
29. Which two values are required to calculate annual loss expectancy? (Choose two.)
- asset value
- quantitative loss value
- single loss expectancy
- exposure factor
- annual rate of occurrence
- frequency factor
Explanation: The single loss expectation, the annual frequency rate and the annual loss expectation are used in a quantitative risk analysis


The team is in the process of performing a risk analysis on the database services. The information collected includes the initial value of these assets, the threats to the assets and the impact of the threats. What type of risk analysis is the team performing by calculating the annual loss expectancy?
*** quantitative analysis
loss analysis
qualitative analysis
protection analysis
What are the three impact metrics contained in the CVSS 3.0 Base Metric Group? (Choose three.)
*** confidentiality
*** integrity
*** availability
remediation level
exploit
attack vector
Which two values are required to calculate annual loss expectancy? (Choose two.)
asset value
quantitative loss value
single loss expectancy
exposure factor
annual rate of occurrence
frequency factor