4.4.2 Endpoint Vulnerability Quiz Answers
4.4.2 Endpoint Vulnerability Quiz. Cyber Threat Management Module 4 Quiz Answers
1. In profiling a server, what defines what an application is allowed to do or run on a server?
- user accounts
- listening ports
- service accounts
- software environment
Explanation: The service accounts element of a server profile defines the type of service that an application is allowed to run on a given host.
2. In network security assessments, which type of test is used to evaluate the risk posed by vulnerabilities to a specific organization including assessment of the likelihood of attacks and the impact of successful exploits on the organization?
- risk analysis
- port scanning
- penetration testing
- vulnerability assessment
Explanation: In risk analysis, security analysts evaluate the risk posed by vulnerabilities to a specific organization. A risk analysis includes assessment of the likelihood of attacks, identifies types of likely threat actors, and evaluates the impact of successful exploits on the organization.
3. When a network baseline is being established for an organization, which network profile element indicates the time between the establishment of a data flow and its termination?
- ports used
- total throughput
- session duration
- critical asset address space
Explanation: Important elements of a network profile include:
- Total throughput – the amount of data passing from a given source to a given destination in a given period of time
- Session duration – the time between the establishment of a data flow and its termination
- Ports used – a list of TCP or UDP processes that are available to accept data
- Critical asset address space – the IP addresses or the logical location of essential systems or data
4. Match the server profile element to the description.
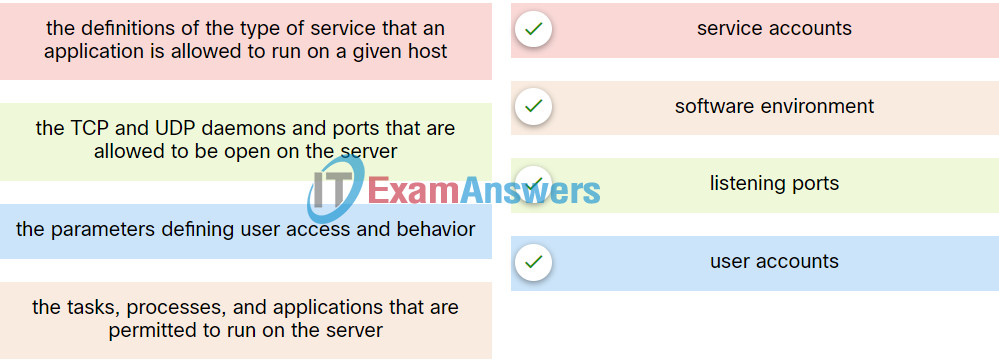
Explanation: Place the options in the following order:
| the parameters defining user access and behavior |
user accounts |
| the TCP and UDP daemons and ports that are allowed to be open on the server |
listening ports |
| the tasks, processes, and applications that are permitted to run on the server |
software environment |
| the definitions of the type of service that an application is allowed to run on a given host |
service accounts |
5. Which type of evaluation includes the assessment of the likelihood of an attack, the type of threat actor likely to perpetrate such an attack, and what the consequences could be to the organization if the exploit is successful?
- risk analysis
- vulnerability identification
- penetration testing
- server profiling
Explanation: When evaluating a cyber security risk, the analyst takes into account the likelihood of an attack occurring, who the potential threat actors might be, as well as the consequences that might occur if the exploit is successful.
6. A cybersecurity analyst is performing a CVSS assessment on an attack where a web link was sent to several employees. Once clicked, an internal attack was launched. Which CVSS Base Metric Group Exploitability metric is used to document that the user had to click on the link in order for the attack to occur?
- availability requirement
- integrity requirement
- scope
- user interaction
Explanation: The CVSS Base Metric Group has the following metrics: attack vector, attack complexity, privileges required, user interaction, and scope. The user interaction metric expresses the presence or absence of the requirement for user interaction in order for an exploit to be successful.
7. Which metric class in the CVSS Basic Metric Group identifies the impacts on confidentiality, integrity, and availability?
- Impact
- Exploitability
- Modified Base
- Exploit Code Maturity
Explanation: The Base Metric Group of CVSS represents the characteristics of a vulnerability that are constant over time and across contexts. It contains two classes of metrics:
- Exploitability metrics – features of the exploit such as the vector, complexity, and user interaction required by the exploit
- Impact metrics – the impacts of the exploit rooted in the CIA triad of confidentiality, integrity, and availability
8. Which metric in the CVSS Base Metric Group is used with an attack vector?
- the proximity of the threat actor to the vulnerability
- the determination whether the initial authority changes to a second authority during the exploit
- the presence or absence of the requirement for user interaction in order for an exploit to be successful
- the number of components, software, hardware, or networks, that are beyond the control of the attacker and that must be present in order for a vulnerability to be successfully exploited
Explanation: The attack vector is one of several metrics defined in the Common Vulnerability Scoring System (CVSS) Base Metric Group Exploitability metrics. The attack vector is how close the threat actor is to the vulnerable component. The farther away the threat actor is to the component, the higher the severity because threat actors close to the network are easier to detect and mitigate.
9. Which statement describes the threat-vulnerability (T-V) pairing?
- It is the advisory notice from a vulnerability research center.
- It is the comparison between known malware and system risks.
- It is the detection of malware against a central vulnerability research center.
- It is the identification of threats and vulnerabilities and the matching of threats with vulnerabilities.
Explanation: A mandatory activity in risk assessment is the identification of threats and vulnerabilities and the matching of threats with vulnerabilities, also called threat-vulnerability (T-V) pairing.
10. In addressing an identified risk, which strategy aims to shift some of the risk to other parties?
- risk sharing
- risk retention
- risk reduction
- risk avoidance
Explanation: There are four potential strategies for responding to risks that have been identified:
- Risk avoidance – Stop performing the activities that create risk.
- Risk reduction – Decrease the risk by taking measures to reduce vulnerability.
- Risk sharing – Shift some of the risk to other parties.
- Risk retention – Accept the risk and its consequences.
11. Which step in the Vulnerability Management Life Cycle categorizes assets into groups or business units, and assigns a business value to asset groups based on their criticality to business operations?
- report
- assess
- remediate
- prioritize assets
Explanation: The steps in the Vulnerability Management Life Cycle include these:
- Discover – inventory all assets across the network and identify host details, including operating systems and open services to identify vulnerabilities
- Prioritize assets – categorize assets into groups or business units, and assign a business value to asset groups based on their criticality to business operations
- Assess – determine a baseline risk profile to eliminate risks based on asset criticality, vulnerability threats, and asset classification
- Report – measure the level of business risk associated with your assets according to your security policies. Document a security plan, monitor suspicious activity, and describe known vulnerabilities
- Remediate – prioritize according to business risk and fix vulnerabilities in order of risk
- Verify – verify that threats have been eliminated through follow-up audits
12. What is an action that should be taken in the discovery step of the vulnerability management life cycle?
- assigning business value to assets
- determining a risk profile
- developing a network baseline
- documenting the security plan
Explanation: During the discovery step of the vulnerability management life cycle, an inventory of all network assets is made. A network baseline is developed, and security vulnerabilities are identified.

