6.3.2 Network Security Infrastructure Quiz Answers
1. What is the purpose of a personal firewall on a computer?
- to protect the computer from viruses and malware
- to increase the speed of the Internet connection
- to protect the hardware against fire hazard
- to filter the traffic that is moving in and out of the PC
2. What is the main difference between the implementation of IDS and IPS devices?
- An IDS can negatively impact the packet flow, whereas an IPS can not.
- An IDS uses signature-based technology to detect malicious packets, whereas an IPS uses profile-based technology.
- An IDS would allow malicious traffic to pass before it is addressed, whereas an IPS stops it immediately.
- An IDS needs to be deployed together with a firewall device, whereas an IPS can replace a firewall.
3. Which protocol provides authentication, integrity, and confidentiality services and is a type of VPN?
- SP
- IPsec
- MD5
- AES
4. What is a feature of the TACACS+ protocol?
- It combines authentication and authorization as one process.
- It encrypts the entire body of the packet for more secure communications.
- It hides passwords during transmission using PAP and sends the rest of the packet in plaintext.
- It utilizes UDP to provide more efficient packet transfer.
5. Which firewall feature is used to ensure that packets coming into a network are legitimate responses to requests initiated from internal hosts?
- packet filtering
- application filtering
- stateful packet inspection
- URL filtering
6. Refer to the exhibit. The network “A” contains multiple corporate servers that are accessed by hosts from the Internet for information about the corporation. What term is used to describe the network marked as “A”?
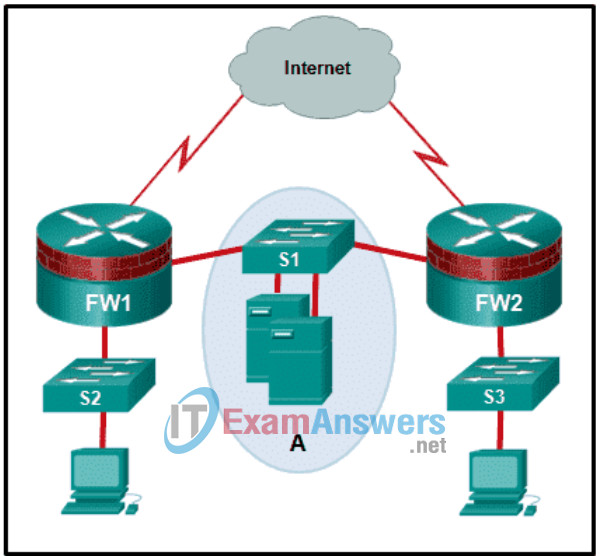
- internal network
- perimeter security boundary
- untrusted network
- DMZ
7. Which statement describes the Cisco Cloud Web Security?
- It is a security appliance that provides an all-in-one solution for securing and controlling web traffic.
- It is an advanced firewall solution to guard web servers against security threats.
- It is a secure web server specifically designed for cloud computing.
- It is a cloud-based security service to scan traffic for malware and policy enforcement.
8. Which two statements are true about NTP servers in an enterprise network? (Choose two.)
- There can only be one NTP server on an enterprise network.
- NTP servers ensure an accurate time stamp on logging and debugging information.
- All NTP servers synchronize directly to a stratum 1 time source.
- NTP servers control the mean time between failures (MTBF) for key network devices.
- NTP servers at stratum 1 are directly connected to an authoritative time source.
9. How is a source IP address used in a standard ACL?
- It is the address to be used by a router to determine the best path to forward packets.
- It is used to determine the default gateway of the router that has the ACL applied.
- It is the criterion that is used to filter traffic.
- It is the address that is unknown, so the ACL must be placed on the interface closest to the source address.
10. Which network service allows administrators to monitor and manage network devices?
- SNMP
- NTP
- NetFlow
- syslog
11. What is a function of a proxy firewall?
- connects to remote servers on behalf of clients
- drops or forwards traffic based on packet header information
- filters IP traffic between bridged interfaces
- uses signatures to detect patterns in network traffic
12. What network monitoring technology enables a switch to copy and forward traffic sent and received on multiple interfaces out another interface toward a network analysis device?
- NetFlow
- network tap
- port mirroring
- SNMP
