Lab Objective:
The objective of this lab exercise is for you to learn and understand how to create and apply extended access control lists to restrict Telnet access to a router or switch.
Lab Purpose:
Configuring and applying extended ACLs to restrict Telnet access is a fundamental skill. Extended ACLs filter based on source and destination address, as well as Layer 4 protocols TCP and UDP. Extended ACLs should be applied as close to the source as possible. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to restrict inbound Telnet traffic to the router or switch using ACLs.
Certification Level:
This lab is suitable for CCENT and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 8/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 20 minutes.
Lab Topology:
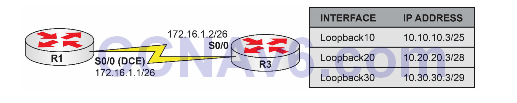
Please use the following topology to complete this lab exercise:
Task 1:
Configure the hostnames on routers R1 and R3 as illustrated in the topology.
Task 2:
Configure R1 S0/0, which is a DCE, to provide a clock rate of 2 Mbps to R3. Configure the IP addresses on the Serial interfaces of R1 and R3 as illustrated in the topology.
Task 3:
Configure a static default route on R1 pointing to R3 over the Serial connection between the two routers. Next, configure the Loopback interfaces specified in the diagram on R3. Finally, configure R1 to allow Telnet sessions. Use the password CISCO for Telnet login.
Task 4:
To test connectivity, ping R1 from R3 Loopback10, Loopback20, and Loopback30 interfaces.
Task 5:
Create an extended named ACL called TELNET-IN on R1. This ACL should permit Telnet traffic from host 10.10.10.3 to any IP address on R1; deny Telnet from host 10.20.20.3 to any IP address on R1; permit Telnet from host 10.30.30.3 to any IP address on R1. Apply this ACL to the Telnet lines on R1 for inbound traffic.
Task 6:
To test your ACL configuration, telnet to R1 from R3 Loopback10, Loopback20, and Loopback30 interfaces using the telnet <ip_address> /source-interface <interface> command. If your ACL configuration is correct, only Telnet from R3 Loopback10 and Loopback20 should work. Verify matches against your ACL.
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring IP addresses and clock rates, please refer to earlier labs.
Task 3:
R1#config t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#ip route 0.0.0.0 0.0.0.0 serial0/0 172.16.1.2 R1(config)#line vty 0 4 R1(config-line)#password CISCO R1(config-line)#login R1(config-line)#end R1# R3#conf t Enter configuration commands, one per line. End with CTRL/Z. R3(config)#int loop10 R3(config-if)#ip address 10.10.10.3 255.255.255.128 R3(config-if)#exit R3(config)#int loop20 R3(config-if)#ip address 10.20.20.3 255.255.255.240 R3(config-if)#exit R3(config)#int loop30 R3(config-if)#ip address 10.30.30.3 255.255.255.248 R3(config-if)#exit R3(config)#line vty 0 4 R3(config-line)#password CISCO R3(config-line)#login R3(config-line)#end R3#
Task 4:
R1#ping 10.10.10.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.10.3, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms R1#ping 10.20.20.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.20.20.3, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms R1#ping 10.30.30.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.30.30.3, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Task 5:
R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#ip access-list extended TELNET-IN R1(config-ext-nacl)#remark “Permit Telnet From Host 10.10.10.3” R1(config-ext-nacl)#permit tcp host 10.10.10.3 any eq 23 R1(config-ext-nacl)#remark “Deny Telnet From Host 10.20.20.3” R1(config-ext-nacl)#deny tcp host 10.20.20.3 any eq 23 R1(config-ext-nacl)#remark “Permit Telnet From Host 10.30.30.3” R1(config-ext-nacl)#permit tcp host 10.30.30.3 any eq 23 R1(config-ext-nacl)#exit R1(config)#line vty 0 4 R1(config-line)#access-class TELNET-IN in R1(config-line)#end R1#
Of course, we would permit all other IP traffic normally in an ACL but we are just testing out the block Telnet feature for this example.
Task 6:
R3#telnet 172.16.1.1 /source-interface loopback10 Trying 172.16.1.1 ... Open User Access Verification Password: R1# R3#telnet 172.16.1.1 /source-interface loopback20 Trying 172.16.1.1 ... % Connection refused by remote host R3#telnet 172.16.1.1 /source-interface loopback30 Trying 172.16.1.1 ... Open User Access Verification Password: R1#
NOTE: The access-class command is used to apply ACLs to the router or switch VTY lines to prevent inbound Telnet and/or SSH sessions from reaching the device. This is not the same as using ACLs that are applied to interfaces to prevent Telnet and/or SSH sessions from reaching the device. Make a mental note of this.
Based on our example above, we can see matches to the ACL rules as follows:
R1#sh ip access-lists TELNET-IN Extended IP access list TELNET-IN 10 permit tcp host 10.10.10.3 any eq telnet (2 matches) 20 deny tcp host 10.20.20.3 any eq telnet (1 match) 30 permit tcp host 10.30.30.3 any eq telnet (2 matches)
