How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
Network Defense – My Knowledge Check Answers
1. In a hierarchical CA topology, where can a subordinate CA obtain a certificate for itself?
- from the root CA only
- from the root CA or from self-generation
- from the root CA or another subordinate CA at the same level
- from the root CA or another subordinate CA at a higher level
- from the root CA or another subordinate CA anywhere in the tree
Explanation: In a hierarchical CA topology, CAs can issue certificates to end users and to subordinate CAs, which in turn issue their certificates to end users, other lower level CAs, or both. In this way, a tree of CAs and end users is built in which every CA can issue certificates to lower level CAs and end users. Only the root CA can issue a self-signing certificate in a hierarchical CA topology.
2. What single access list statement matches all of the following networks?
192.168.16.0
192.168.17.0
192.168.18.0
192.168.19.0
- access-list 10 permit 192.168.16.0 0.0.3.255
- access-list 10 permit 192.168.16.0 0.0.0.255
- access-list 10 permit 192.168.16.0 0.0.15.255
- access-list 10 permit 192.168.0.0 0.0.15.255
Explanation: The ACL statement access-list 10 permit 192.168.16.0 0.0.3.255 will match all four network prefixes. All four prefixes have the same 22 high order bits. These 22 high order bits are matched by the network prefix and wildcard mask of 192.168.16.0 0.0.3.255.
3. What Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?
- Event Viewer security log
- Local Security Policy tool
- Active Directory Security tool
- Computer Management
Explanation: A technician must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities. A Windows Domain Security Policy is used and applied when a user logs in to a computer that is on a corporate network. A Windows Local Security Policy is used for stand-alone computers to enforce security settings.
4. An administrator of a small data center wants a flexible, secure method of remotely connecting to servers. Which protocol would be best to use?
- Telnet
- Remote Desktop
- Secure Copy
- Secure Shell
Explanation: Because hackers sniffing traffic can read clear text passwords, any connection needs to be encrypted. Additionally, a solution should not be operating system-dependent.
5. Which network service synchronizes the time across all devices on the network?
Explanation: There are two methods that can be used to set date and time settings on network devices. Manual configuration and automatically using the Network Time Protocol (NTP). NTP keeps the time across all devices synchronized by using a hierarchical system of sources.
6. Which technique can be used to leverage virtual network topologies to run smaller and more isolated networks without incurring additional hardware costs?
- shadow IT
- fog computing
- edge computing
- microsegmentation
Explanation: Microsegmentation (also referred to as hypersegregation) leverages virtual network topologies to run smaller and more isolated networks without incurring additional hardware costs. Microsegmentation techniques allow for more granular control of security for traffic and workflows within the cloud.
7. What is the purpose of mobile device management (MDM) software?
- It is used to create a security policy.
- It is used by threat actors to penetrate the system.
- It is used to identify potential mobile device vulnerabilities.
- It is used to implement security policies, setting, and software configurations on mobile devices.
Explanation: Mobile device management (MDM) software is used with mobile devices so that corporate IT personnel can track the devices, implement security settings, as well as control software configurations.
8. Which network monitoring tool is in the category of network protocol analyzers?
Explanation: Wireshark is a network protocol analyzer used to capture network traffic. The traffic captured by Wireshark is saved in PCAP files and includes interface information and timestamps.
9. What is a characteristic of a layered defense-in-depth security approach?
- Three or more devices are used.
- Routers are replaced with firewalls.
- When one device fails, another one takes over.
- One safeguard failure does not affect the effectiveness of other safeguards.
Explanation: When a layered defense-in-depth security approach is used, layers of security are placed through the organization-at the edge, within the network, and on endpoints. The layers work together to create the security architecture. In this environment, a failure of one safeguard does not affect the effectiveness of other safeguards.
10. A user was hired by a company to provide a highly available network infrastructure. The user wants to build redundancy into the network in case of a switch failure, but wants to prevent Layer 2 looping. What would the user implement in the network?
- HSRP
- VRRP
- Spanning Tree Protocol
- GLBP
Explanation: Loops and duplicate frames cause poor performance in a switched network. The Spanning Tree Protocol (STP) provides a loop-free path through the switch network.
11. A user has created a new program and wants to distribute it to everyone in the company. The user wants to ensure that when the program is downloaded that the program is not changed while in transit. What can the user do to ensure that the program is not changed when downloaded?
- Distribute the program on a thumb drive.
- Install the program on individual computers.
- Create a hash of the program file that can be used to verify the integrity of the file after it is downloaded.
- Turn off antivirus on all the computers.
- Encrypt the program and require a password after it is downloaded.
Explanation: Hashing is a method to ensure integrity and ensures that the data is not changed.
12. Which cloud security domain describes controls related to securing the data itself?
- Application Security
- Security as a Service
- Infrastructure Security
- Data Security and Encryption
Explanation: The Security Guidance for Critical Areas of Focus in Cloud Computing v4 document developed by the Cloud Security Alliance (CSA) covers 14 domains of cloud security. Some of these domains are:
- Infrastructure Security – describes cloud-specific aspects of infrastructure security and the foundation for operating securely in the cloud.
- Data Security and Encryption – describes those controls related to securing the data itself, of which encryption is one of the most important.
- Application Security – provides guidance on how to securely build and deploy applications in cloud computing environments, specifically for PaaS and IaaS.
- Security as a Service – covers the continually evolving security services delivered from the cloud.
13. Which type of firewall is commonly part of a router firewall and allows or blocks traffic based on Layer 3 and Layer 4 information?
- stateless firewall
- stateful firewall
- proxy firewall
- application gateway firewall
Explanation: A stateless firewall uses a simple policy table look-up that filters traffic based on specific criteria. These firewalls are usually part of a router firewall. They permit or deny traffic based on Layer 3 and Layer 4 information.
14. What is a key difference between the data captured by NetFlow and data captured by Wireshark?
- NetFlow provides transaction data whereas Wireshark provides session data.
- NetFlow data is analyzed by tcpdump whereas Wireshark data is analyzed by nfdump.
- NetFlow collects metadata from a network flow whereas Wireshark captures full data packets.
- NetFlow data shows network flow contents whereas Wireshark data shows network flow statistics.
Explanation: Wireshark captures the entire contents of a packet. NetFlow does not. Instead, NetFlow collects metadata, or data about the flow.
15. An IT enterprise is recommending the use of PKI applications to securely exchange information between the employees. In which two cases might an organization use PKI applications to securely exchange information between users? (Choose two.)
- 802.1x authentication
- FTP transfers
- HTTPS web service
- local NTP server
- file and directory access permission
Explanation: The Public Key Infrastructure (PKI) is a third party-system referred to as a certificate authority or CA. The PKI is the framework used to securely exchange information between parties. Common PKI applications are as follows:
SSL/TLS certificate-based peer authentication
Secure network traffic using IPsec VPNs
HTTPS Web traffic
Control access to the network using 802.1x authentication
Secure email using the S/MIME protocol
Secure instant messaging
Approve and authorize applications with Code Signing
Protect user data with the Encryption File System (EFS)
Implement two-factor authentication with smart cards
Securing USB storage devices
16. What are two uses of an access control list? (Choose two.)
- ACLs assist the router in determining the best path to a destination.
- Standard ACLs can restrict access to specific applications and ports.
- ACLs provide a basic level of security for network access.
- ACLs can permit or deny traffic based upon the MAC address originating on the router.
- ACLs can control which areas a host can access on a network.
Explanation: ACLs can be used for the following:Limit network traffic in order to provide adequate network performance
Restrict the delivery of routing updates
Provide a basic level of security
Filter traffic based on the type of traffic being sent
Filter traffic based on IP addressing
17. What is a purpose of implementing VLANs on a network?
- They can separate user traffic.
- They prevent Layer 2 loops.
- They eliminate network collisions.
- They allow switches to forward Layer 3 packets without a router.
Explanation: VLANs are used on a network to separate user traffic based on factors such as function, project team, or application, without regard for the physical location of the user or device.
18. A company has a file server that shares a folder named Public. The network security policy specifies that the Public folder is assigned Read-Only rights to anyone who can log into the server while the Edit rights are assigned only to the network admin group. Which component is addressed in the AAA network service framework?
- accounting
- automation
- authorization
- authentication
Explanation: After a user is successfully authenticated (logged into the server), the authorization is the process of determining what network resources the user can access and what operations (such as read or edit) the user can perform.
19. Which two application layer protocols manage the exchange of messages between a client with a web browser and a remote web server? (Choose two.)
Explanation: Hypertext Transfer Protocol (HTTP) and HTTP Secure (HTTPS) are two application layer protocols that manage the content requests from clients and the responses from the web server. HTML (Hypertext Mark-up Language) is the encoding language that describes the content and display features of a web page. DNS is for domain name to IP address resolution. DHCP manages and provides dynamic IP configurations to clients.
20. Which tool can be used to gather information about the different types of traffic that exist in a network?
- RTP
- application server
- QoS
- protocol analyzer
Explanation: As part of planning to grow a small network, it is important for a network administrator to survey the network to determine the different traffic types and the amount of traffic in a network. A protocol analyzer is a tool that can be used to gather this information. RTP is a protocol used in voice and video communication. QoS is a mechanism used to manage congestion and prioritize traffic. An application server is used to host applications.
21. What are the two classes of encryption algorithms? (Choose two.)
- open
- symmetric
- classic
- asymmetric
- advanced
Explanation: That’s not right.
Encryption algorithms belong to one of two classes, symmetric and asymmetric. Symmetric algorithms use a pre-shared key which is the same for sender and receiver. Asymmetric algorithms use two keys, one for encrypting and one for decrypting.
22. Which hashing technology requires keys to be exchanged?
Explanation: The difference between HMAC and hashing is the use of keys.
23. Which operator is used in an ACL statement to match packets of a specific application?
Explanation: An example of an ACL that filters for FTP is as follows:
access-list 105 permit tcp any host 10.0.54.5 eq 20
access-list 105 permit tcp any host 10.0.54.5 eq 21
The operator (eq) toward the end of the ACL lines is used to match a specific port/service that is specified immediately following the eq operator.
24. A large retail company uses EAP-based authentication in conjunction with 802.1X. When the client first initiates communication on the wireless network, which type of authentication method is used by the client to associate with the AP?
- WPA2
- WPA
- Open Authentication
- WPA3
Explanation: When 802.1X is used in conjunction with EAP for authentication, a wireless device first uses Open Authentication to associate with the AP. Then, the wireless controller becomes the middleman in the authentication process between the end device and the authentication server. The wireless client cannot pass data onto the wireless network until successful authentication with the authentication server has occurred.
25. Which type of server daemon accepts messages sent by network devices to create a collection of log entries?
Explanation: Syslog is important to security monitoring because network devices send periodic messages to the syslog server. These logs can be examined to detect inconsistencies and issues within the network.
26. A company is developing a security policy for secure communication. In the exchange of critical messages between a headquarters office and a branch office, a hash value should only be recalculated with a predetermined code, thus ensuring the validity of data source. Which aspect of secure communications is addressed?
- data integrity
- non-repudiation
- data confidentiality
- origin authentication
Explanation: Secure communications consists of four elements:
- Data confidentiality – guarantees that only authorized users can read the message
- Data integrity – guarantees that the message was not altered
- Origin authentication – guarantees that the message is not a forgery and does actually come from whom it states
- Data nonrepudiation – guarantees that the sender cannot repudiate, or refute, the validity of a message sent
27. What wild card mask will match networks 172.16.0.0 through 172.19.0.0?
- 0.0.3.255
- 0.0.255.255
- 0.252.255.255
- 0.3.255.255
Explanation: A network administrator will use the ipv6 traffic-filter command within interface configuration mode to apply an IPv6 ACL.
28. What are two physical security precautions that a business can take to protect its computers and systems? (Choose two.)
- Perform daily data backups.
- Implement biometric authentication.
- Lock doors to telecommunications rooms.
- Replace software firewalls with hardware firewalls.
- Ensure that all operating system and antivirus software is up to date.
Explanation: Firewalls (software and hardware), up to date software, and backing up data are all security measures designed to protect data. However, these are not physical security precautions. Physical security precautions prevent theft, damage, or unauthorized access to physical computer equipment.
29. Match the security concept to the description.
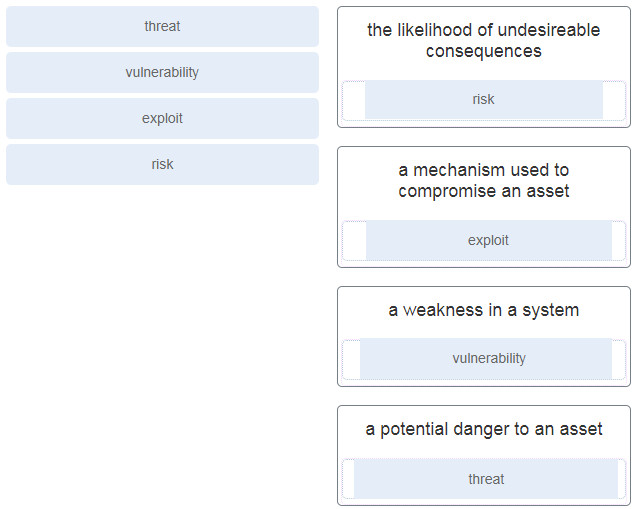
Explanation: Place the options in the following order:
| the likelihood of undesireable consequences |
risk |
| a mechanism used to compromise an asset |
exploit |
| a weakness in a system |
vulnerability |
| a potential danger to an asset |
threat |
30. Passwords, passphrases, and PINs are examples of which security term?
- identification
- authorization
- authentication
- access
Explanation: Authentication methods are used to strengthen access control systems. It is important to understand the available authentication methods.
31. Which technique is necessary to ensure a private transfer of data using a VPN?
- authorization
- encryption
- scalability
- virtualization
Explanation: Confidential and secure transfers of data with VPNs require data encryption.
32. What is one benefit of using a next-generation firewall rather than a stateful firewall?
- integrated use of an intrusion prevention system (IPS)
- support of TCP-based packet filtering
- reactive protection against Internet threats
- support of logging
Explanation: Stateful firewalls and next-generation firewalls provide better log information than a packet filtering firewall, both defend against spoofing, and both filter unwanted traffic. Next-generation firewalls provide the following benefits over stateful firewalls:
- Granularity control within applications
- Website and application traffic filtering based on site reputation
- Proactive rather than reactive protection from Internet threats
- Enforcement of security policies based on multiple criteria including user, device, role, application, and threat profile
- Improved performance with NAT, VPN, and stateful inspections
- Integrated IPS
33. Which tool included in Security Onion is an interactive dashboard interface to Elasticsearch data?
- Zeek
- Kibana
- Sguil
- Wireshark
Explanation: Kibana is an interactive dashboard interface to Elasticsearch data. It allows querying of NSM data and provides flexible visualizations of that data. It provides data exploration and machine learning data analysis features.
34. A threat actor has successfully breached the network firewall without being detected by the IDS system. What condition describes the lack of alert?
- false negative
- false positive
- true positive
- true negative
Explanation: A false negative is where no alert exists and exploits are not being detected by the security systems that are in place.
35. In which way does the use of HTTPS increase the security monitoring challenges within enterprise networks?
- HTTPS traffic is much faster than HTTP traffic.
- HTTPS traffic enables end-to-end encryption.
- HTTPS traffic does not require authentication.
- HTTPS traffic can carry a much larger data payload than HTTP can carry.
Explanation: HTTPS enables end-to-end encrypted network communication, which adds further challenges for network administrators to monitor the content of packets to catch malicious attacks.
36. What method is used to apply an IPv6 ACL to a router interface?
- the use of the access-class command
- the use of the ip access-group command
- the use of the ipv6 traffic-filter command
- the use of the ipv6 access-list command
Explanation: A network administrator will use the ipv6 traffic-filter command within interface configuration mode to apply an IPv6 ACL.
37. A company wants to implement biometric access to its data center. The company is concerned with people being able to circumvent the system by being falsely accepted as legitimate users. What type of error is false acceptance?
- Type I
- Type II
- false rejection
- CER
Explanation: There are two types of errors that biometrics can have: false acceptance and false rejection. False acceptance is a Type II error. The two types can intersect at a point called the crossover error rate.
38. What technology has a function of using trusted third-party protocols to issue credentials that are accepted as an authoritative identity?
- PKI certificates
- symmetric keys
- hashing algorithms
- digital signatures
Explanation: Digital certificates are used to prove the authenticity and integrity of PKI certificates, but a PKI Certificate Authority is a trusted third-party entity that issues PKI certificates. PKI certificates are public information and are used to provide authenticity, confidentiality, integrity, and nonrepudiation services that can scale to large requirements.
39. What device would be used as the third line of defense in a defense-in-depth approach?
- firewall
- edge router
- internal router
- host
Explanation: In a defense-in-depth approach, the edge router would form the first line of defense. The firewall would be the second line of defense followed by the internal router making up the third line of defense.
40. Which key component of virtualization allows for running multiple independent operating systems on one physical computing system?
- VM
- VDI
- container
- hypervisor
Explanation: A hypervisor is a software or hardware program that builds a virtualization environment to support multiple independent virtual machines on one physical system. It is a key component of virtualization.
41. Which technology would be used to create the server logs generated by network devices and reviewed by an entry level network person who works the night shift at a data center?
Explanation: Syslog is a daemon or service run on a server that accepts messages sent by network devices. These logs are frequently examined to detect inconsistencies and issues within the network.
42. What is one limitation of a stateful firewall?
- poor log information
- weak user authentication
- cannot filter unnecessary traffic
- not as effective with UDP- or ICMP-based traffic
Explanation: Limitations of stateful firewalls include the following:
Stateful firewalls cannot prevent application layer attacks.
Protocols such as UDP and ICMP are not stateful and do not generate information needed for a state table.
An entire range of ports must sometimes be opened in order to support specific applications that open multiple ports.
Stateful firewalls lack user authentication.
43. What is the purpose of the network security authentication function?
- to require users to prove who they are
- to determine which resources a user can access
- to keep track of the actions of a user
- to provide challenge and response questions
Explanation: Authentication, authorization, and accounting are network services collectively known as AAA. Authentication requires users to prove who they are. Authorization determines which resources the user can access. Accounting keeps track of the actions of the user.
44. A network administrator is setting up a web server for a small advertising office and is concerned with data availability. The administrator wishes to implement disk fault tolerance using the minimum number of disks required. Which RAID level should the administrator choose?
- RAID 0
- RAID 1
- RAID 5
- RAID 6
Explanation: Both RAID 0 and RAID 1 require at least 2 disks. However, RAID 0 does not provide fault tolerance. The minimum numbers of disks for RAID 5 and RAID 6 are 3 and 4 respectively.
45. Which access control model assigns security privileges based on the position, responsibilities, or job classification of an individual or group within an organization?
- discretionary
- role-based
- mandatory
- rule-based
Explanation: Role-based access control models assign privileges based on position, responsibilities, or job classification. Users and groups with the same responsibilities or job classification share the same assigned privileges. This type of access control is also referred to as nondiscretionary access control.
46. When a Cisco IOS zone-based policy firewall is being configured, which three actions can be applied to a traffic class? (Choose three.)
- drop
- inspect
- pass
- reroute
- queue
- shape
Explanation: The inspect CCP action is similar to the classic firewall ip inspect command in that it inspects traffic going through the firewall and allowing return traffic that is part of the same flow to pass through the firewall. The drop action is similar to the deny parameter in an ACL. This action drops whatever traffic fits the defined policy. The pass action is similar to a permit ACL statement–traffic is allowed to pass through because it met the criteria of the defined policy statement.
47. A company is developing an internet store website. Which protocol should be used to transfer credit card information from customers to the company web server?
Explanation: Hypertext Transfer Protocol (HTTP) provides web connectivity and website services. HTTP does not use encryption when transmitting content, leaving the data in transit vulnerable to monitoring and attack. HTTPS uses SSL/TLS to encrypt communication between the client and the server, thus providing confidentiality and preventing eavesdropping and tampering.
48. What is an example of the implementation of physical security?
- establishing personal firewalls on each computer
- encrypting all sensitive data that is stored on the servers
- requiring employees to use a card key when entering a secure area
- ensuring that all operating system and antivirus software is up to date
Explanation: Encrypting data, keeping software up to date, and the use of personal firewalls are all security precautions, but will not restrict physical access to secure areas by only authorized people.
49. Which two statements describe the effect of the access control list wildcard mask 0.0.0.15? (Choose two.)
- The first 28 bits of a supplied IP address will be ignored.
- The last four bits of a supplied IP address will be ignored.
- The first 32 bits of a supplied IP address will be matched.
- The first 28 bits of a supplied IP address will be matched.
- The last five bits of a supplied IP address will be ignored.
- The last four bits of a supplied IP address will be matched.
Explanation: A wildcard mask uses 0s to indicate that bits must match. 0s in the first three octets represent 24 bits and four more zeros in the last octet, represent a total of 28 bits that must match. The four 1s represented by the decimal value of 15 represents the four bits to ignore.
50. What are two recommended steps to protect and secure a wireless network? (Choose two.)
- Update firmware.
- Use WPA2-AES encryption.
- Locate the wireless router where it is accessible to users.
- Use the default SSID.
- Enable remote management.
Explanation: Two best practices for securing wireless networks are to encrypt the wireless traffic with WPA2 encryption and to keep the wireless router firmware updated. This prevents data from being readable by an attacker and fixes any known bugs and vulnerabilities in the router.
51. What is the purpose of the DH algorithm?
- to provide nonrepudiation support
- to support email data confidentiality
- to encrypt data traffic after a VPN is established
- to generate a shared secret between two hosts that have not communicated before
Explanation: DH is an asymmetric mathematical algorithm that allows two computers to generate an identical shared secret, without having communicated before. Asymmetric key systems are extremely slow for any sort of bulk encryption. It is common to encrypt the bulk of the traffic using a symmetric algorithm such as DES, 3DES, or AES, and use the DH algorithm to create keys that will be used by the symmetric encryption algorithm.
52. Refer to the exhibit. Which statement describes the function of the ACEs?
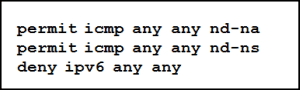
- These ACEs allow for IPv6 neighbor discovery traffic.
- These ACEs must be manually added to the end of every IPv6 ACL to allow IPv6 routing to occur.
- These ACEs automatically appear at the end of every IPv6 ACL to allow IPv6 routing to occur.
- These are optional ACEs that can be added to the end of an IPv6 ACL to allow ICMP messages that are defined in object groups named nd-na and nd-ns.
Explanation: The ICMP protocol is used for neighbor discovery. The two permit statements allow neighbor advertisement and neighbor solicitation messages between IPv6 devices.
53. How do cybercriminals make use of a malicious iFrame?
- The iFrame allows the browser to load a web page from another source.
- The attacker embeds malicious content in business appropriate files.
- The attacker redirects traffic to an incorrect DNS server.
- The iFrame allows multiple DNS subdomains to be used.
Explanation: An inline frame or iFrame is an HTML element that allows the browser to load a different web page from another source.
54. What is the result in the self zone if a router is the source or destination of traffic?
- No traffic is permitted.
- All traffic is permitted.
- Only traffic that originates in the router is permitted.
- Only traffic that is destined for the router is permitted.
Explanation: All traffic is permitted in the self zone if the traffic originates from, or is destined for, the router.
55. Which type of analysis relies on predefined conditions and can analyze applications that only use well-known fixed ports?
- probabilistic
- deterministic
- statistical
- log
Explanation: Deterministic analysis uses predefined conditions to analyze applications that conform to specification standards, such as performing a port-based analysis.