2.3.3.4 Lab – Configuring a Switch Management Address (Instructor Version)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only.
Topology

Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| S1 | VLAN 1 | 192.168.1.2 | 255.255.255.0 |
| PC-A | NIC | 192.168.1.10 | 255.255.255.0 |
Objectives
Part 1: Configure a Basic Network Device
Part 2: Verify and Test Network Connectivity
Background / Scenario
Cisco switches have a special interface, known as a switch virtual interface (SVI). The SVI can be configured with an IP address, commonly referred to as the management address. The management address is used for remote access to the switch to display or configure settings.
In this lab, you will build a simple network using Ethernet LAN cabling and access a Cisco switch using the console and remote access methods. You will configure basic switch settings, IP addressing, and demonstrate the use of a management IP address for remote switch management. The topology consists of one switch and one host using only Ethernet and console ports.
Note: The switches used are Cisco Catalyst 2960s with Cisco IOS Release 15.0(2) (lanbasek9 image). Other switches and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the available commands and output produced might vary from what is shown in the labs.
Note: Make sure that the switch has been erased and has no startup configuration. If you are unsure, contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 1 Switch (Cisco 2960 with Cisco IOS Release 15.0(2) lanbasek9 image or comparable)
- 1 PC (Windows 7 or 8 with terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Part 1: Configure a Basic Network Device
In Part 1, you will set up the network and configure basic settings, such as hostnames, interface IP addresses, and passwords.
Step 1: Cable the network.
a. Cable the network as shown in the topology.
b. Establish a console connection to the switch from PC-A.
Step 2: Configure basic switch settings.
In this step, you will configure basic switch settings, such as hostname, and configure an IP address for the SVI. Assigning an IP address on the switch is only the first step. As the network administrator, you must specify how the switch will be managed. Telnet and SSH are two of the most common management methods. However, Telnet is a very insecure protocol. All information flowing between the two devices is sent in plaintext. Passwords and other sensitive information can be easily viewed if captured by packet sniffer.
a. Assuming the switch did not have a configuration file stored in NVRAM, you will be at the user EXEC mode prompt on the switch. The prompt will be Switch>. Enter privileged EXEC mode.
Switch> enable Switch#
b. Use the privileged EXEC show running-config command to verify a clean configuration file. If a configuration file was previously saved, it will have to be removed. Depending on the switch model and IOS version, your configuration may look slightly different. However, there should not be any configured passwords or IP address set. If your switch does not have a default configuration, ask your instructor for help.
c. Enter global configuration mode and assign the switch hostname.
Switch# configure terminal Switch(config)# hostname S1 S1(config)#
d. Configure the switch password access.
S1(config)# enable secret class S1(config)#
e. Prevent unwanted DNS lookups.
S1(config)# no ip domain-lookup S1(config)#
f. Configure a login MOTD banner.
S1(config)# banner motd # Enter Text message. End with the character ‘#’. Unauthorized access is strictly prohibited. #
g. Verify your access setting by moving between modes.
S1(config)# exit S1# S1# exit Unauthorized access is strictly prohibited. S1>
What shortcut keys are used to go directly from global configuration mode to privileged EXEC mode?
Ctrl+Z
h. Return to privileged EXEC mode from user EXEC mode.
S1> enable Password: class S1#
Note: The password will not show up on the screen when entering.
i. Enter global configuration mode to set the SVI IP address to allow remote switch management.
S1# config t S1#(config)# interface vlan 1 S1(config-if)# ip address 192.168.1.2 255.255.255.0 S1(config-if)# no shut S1(config-if)# exit S1(config)#
j. Restrict console port access. The default configuration is to allow all console connections with no password needed.
S1(config)# line con 0 S1(config-line)# password cisco S1(config-line)# login S1(config-line)# exit S1(config)#
k. Configure the VTY line for the switch to allow Telnet access. If you do not configure a VTY password, you will not be able to telnet to the switch.
S1(config)# line vty 0 4 S1(config-line)# password cisco S1(config-line)# login S1(config-line)# end S1# *Mar 1 00:06:11.590: %SYS-5-CONFIG_I: Configured from console by console
Step 3: Configure an IP address on PC-A.
a. Assign the IP address and subnet mask to the PC, as shown in the Addressing Table. The procedure for assigning an IP address on a PC running Windows 7 is described below:
1) Click the Windows Start icon > Control Panel.
2) Click View By: > Category.
3) Choose View network status and tasks > Change adapter settings.
4) Right-click Local Area Network Connection and select Properties.
5) Choose Internet Protocol Version 4 (TCP/IPv4), click Properties > OK.
6) Click the Use the following IP address radio button and enter the IP address and subnet mask.
Part 2: Verify and Test Network Connectivity
You will now verify and document the switch configuration, test end-to-end connectivity between PC-A and S1, and test the remote management capability of the switch.
Step 1: Display the S1 device configuration.
a. Return to your console connection using Tera Term on PC-A. Issue the show run command to display and verify your switch configuration. A sample configuration is shown below. The settings you configured are highlighted in yellow. The other configuration settings are IOS defaults.
S1# show run Building configuration... Current configuration : 1508 bytes ! ! Last configuration change at 00:06:11 UTC Mon Mar 1 1993 ! version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model system mtu routing 1500 ! ! no ip domain-lookup ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 <output omitted> interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 ip address 192.168.1.2 255.255.255.0 ! ip http server ip http secure-server ! banner motd ^C Unauthorized access is strictly prohibited. ^C ! line con 0 password cisco login line vty 0 4 password cisco login line vty 5 15 login ! end
b. Verify the status of your SVI management interface. Your VLAN 1 interface should be up/up and have an IP address assigned. Notice that switch port F0/6 is also up because PC-A is connected to it. Because all switch ports are initially in VLAN 1, by default, you can communicate with the switch using the IP address you configured for VLAN 1.
S1# show ip interface brief Interface IP-Address OK? Method Status Protocol Vlan1 192.168.1.2 YES manual up up FastEthernet0/1 unassigned YES unset down down FastEthernet0/2 unassigned YES unset down down FastEthernet0/3 unassigned YES unset down down FastEthernet0/4 unassigned YES unset down down FastEthernet0/5 unassigned YES unset down down FastEthernet0/6 unassigned YES unset up up FastEthernet0/7 unassigned YES unset down down FastEthernet0/8 unassigned YES unset down down FastEthernet0/9 unassigned YES unset down down FastEthernet0/10 unassigned YES unset down down FastEthernet0/11 unassigned YES unset down down FastEthernet0/12 unassigned YES unset down down FastEthernet0/13 unassigned YES unset down down FastEthernet0/14 unassigned YES unset down down FastEthernet0/15 unassigned YES unset down down FastEthernet0/16 unassigned YES unset down down FastEthernet0/17 unassigned YES unset down down FastEthernet0/18 unassigned YES unset down down FastEthernet0/19 unassigned YES unset down down FastEthernet0/20 unassigned YES unset down down FastEthernet0/21 unassigned YES unset down down FastEthernet0/22 unassigned YES unset down down FastEthernet0/23 unassigned YES unset down down FastEthernet0/24 unassigned YES unset down down GigabitEthernet0/1 unassigned YES unset down down GigabitEthernet0/2 unassigned YES unset down down
Step 2: Test end-to-end connectivity.
Open a command prompt window (cmd.exe) on PC-A by clicking the Windows Start icon and entering cmd into the Search for programs and files field. Verify the IP address of PC-A by using the ipconfig /all command. This command displays the PC hostname and the IPv4 address information. Ping PC-A’s address and the management address of S1.
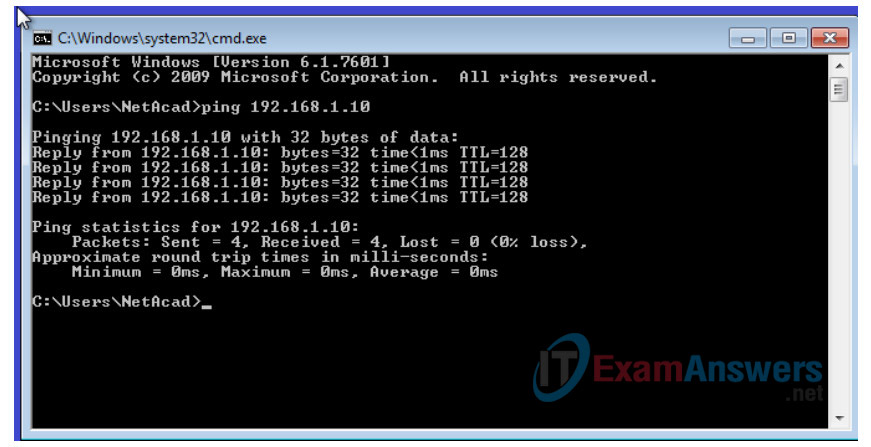
a. Ping the PC-A address first.
C:\Users\NetAcad> ping 192.168.1.10
Your output should be similar to the following screen:
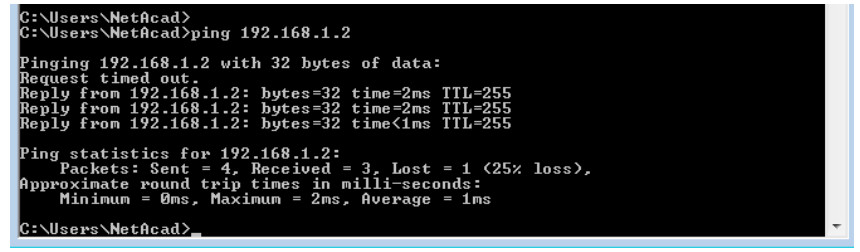
b. Ping the SVI management address of S1.
C:\Users\NetAcad> ping 192.168.1.2
Your output should be similar to the following screen. If ping results are not successful, troubleshoot the basic device configurations. You should check both the physical cabling and IP addressing if necessary.
Step 3: Test and verify the remote management of S1.
You will now use Telnet to remotely access the switch S1 using the SVI management address. In this lab, PC-A and S1 reside side by side. In a production network, the switch could be in a wiring closet on the top floor while your management PC is located on the ground floor. Telnet is not a secure protocol. However, you will use it in this lab to test remote access. All information sent by Telnet, including passwords and commands, is sent across the session in plaintext. In subsequent labs, you will use SSH to remotely access network devices.
Note: Windows 7 does not natively support Telnet. The administrator must enable this protocol. To install the Telnet client, open a command prompt window and type pkgmgr /iu:“TelnetClient”.
C:\Users\NetAcad> pkgmgr /iu:”TelnetClient”
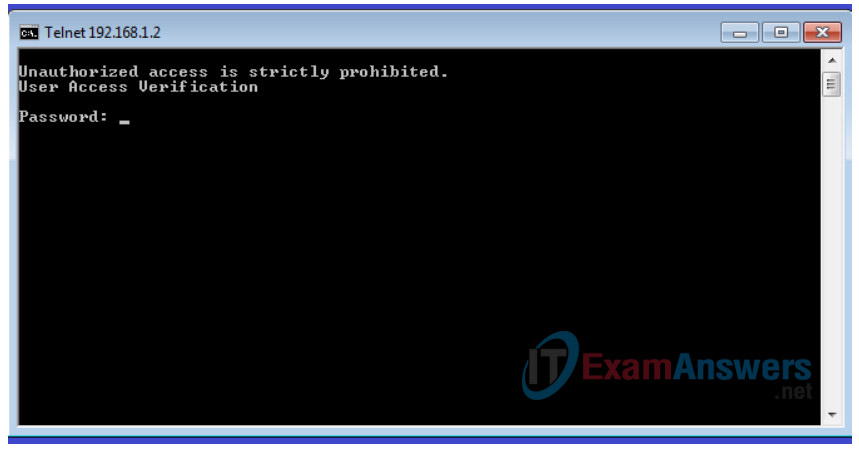
a. With the command prompt window still open on PC-A, issue a Telnet command to connect to S1 via the SVI management address. The password is cisco.
C:\Users\NetAcad> telnet 192.168.1.2
Your output should be similar to the following screen:
b. After entering the cisco password, you will be at the user EXEC mode prompt. Type enable at the prompt. Enter the class password to enter privileged EXEC mode and issue a show run command.
Step 4: Save the configuration file.
a. From your Telnet session, issue the copy run start command at the prompt.
S1# copy run start Destination filename [startup-config]? [Enter] Building configuration .. S1#
b. Exit the Telnet session by typing quit. You will be returned to the Windows 7 command prompt.
Reflection
Why must you use a console connection to initially configure the switch? Why not connect to the switch via Telnet or SSH?
No IP addressing parameters are configured yet. Initially, a switch has no networking configured.
Device Configs
Switch S1(Complete)
S1#show run Building configuration... ! Current configuration : 1508 bytes ! version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model system mtu routing 1500 ! ! no ip domain-lookup ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 ip address 192.168.1.2 255.255.255.0 ! ip http server ip http secure-server ! banner motd ^C Unauthorized access is strictly prohibited. ^C ! line con 0 password cisco login line vty 0 4 password class login line vty 5 15 login ! end
