2.2.2.5 Lab – Troubleshooting Inter-VLAN Routing (Instructor Version)
Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only.
Topology
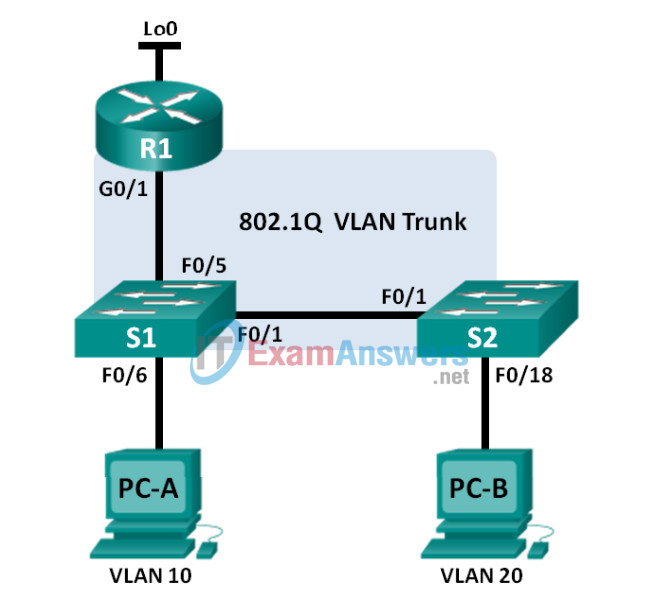
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | G0/1.1 | 192.168.1.1 | 255.255.255.0 | N/A |
| G0/1.10 | 192.168.10.1 | 255.255.255.0 | N/A | |
| G0/1.20 | 192.168.20.1 | 255.255.255.0 | N/A | |
| Lo0 | 209.165.200.225 | 255.255.255.224 | N/A | |
| S1 | VLAN 1 | 192.168.1.11 | 255.255.255.0 | 192.168.1.1 |
| S2 | VLAN 1 | 192.168.1.12 | 255.255.255.0 | 192.168.1.1 |
| PC-A | NIC | 192.168.10.3 | 255.255.255.0 | 192.168.10.1 |
| PC-B | NIC | 192.168.20.3 | 255.255.255.0 | 192.168.20.1 |
Switch Port Assignment Specifications
| Ports | Assignment | Network |
|---|---|---|
| S1 F0/1 | 802.1Q Trunk | N/A |
| S2 F0/1 | 802.1Q Trunk | N/A |
| S1 F0/5 | 802.1Q Trunk | N/A |
| S1 F0/6 | VLAN 10 – R&D | 192.168.10.0/24 |
| S2 F0/18 | VLAN 20 – Engineering | 192.168.20.0/24 |
Objectives
Part 1: Build the Network and Load Device Configurations
Part 2: Troubleshoot the Inter-VLAN Routing Configuration
Part 3: Verify VLAN Configuration, Port Assignment, and Trunking
Part 4: Test Layer 3 Connectivity
Background / Scenario
The network has been designed and configured to support three VLANs. Inter-VLAN routing is provided by an external router using an 802.1Q trunk, also known as router-on-a-stick. Routing to a remote web server, which is simulated by Lo0, is also provided by R1. However, it is not working as designed, and user complaints have not given much insight into the source of the problems.
In this lab, you must first define what is not working as expected, and then analyze the existing configurations to determine and correct the source of the problems. This lab is complete when you can demonstrate IP connectivity between each of the user VLANs and the external web server network, and between the switch management VLAN and the web server network.
Note: The routers used with CCNA hands-on labs are Cisco 1941 Integrated Services Routers (ISRs) with Cisco IOS Release 15.2(4)M3 (universalk9 image). The switches used are Cisco Catalyst 2960s with Cisco IOS Release 15.0(2) (lanbasek9 image). Other routers, switches, and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and output produced might vary from what is shown in the labs. Refer to the Router Interface Summary Table at the end of this lab for the correct interface identifiers.
Note: Make sure that the routers and switches have been erased and have no startup configurations. If you are unsure, contact your instructor.
Instructor Note: Refer to the Instructor Lab Manual for the procedures to initialize and reload devices.
Required Resources
- 1 Router (Cisco 1941 with Cisco IOS Release 15.2(4)M3 universal image or comparable)
- 2 Switches (Cisco 2960 with Cisco IOS Release 15.0(2) lanbasek9 image or comparable)
- 2 PCs (Microsoft Windows with terminal emulation program, such as Tera Term)
- Console cables to configure the Cisco IOS devices via the console ports
- Ethernet cables as shown in the topology
Part 1: Build the Network and Load Device Configurations
In Part 1, you will set up the network topology and configure basic settings on the PC hosts, switches, and router.
Step 1: Cable the network as shown in the topology.
Step 2: Configure PC hosts.
Refer to the Addressing Table for PC host address information.
Step 3: Load router and switch configurations.
Load the following configurations into the appropriate router or switch. All devices have the same passwords; the enable password is class, and the line password is cisco.
Router R1 Configuration:
hostname R1 enable secret class no ip domain lookup line con 0 password cisco login logging synchronous line vty 0 4 password cisco login interface loopback0 ip address 209.165.200.225 255.255.255.224 interface gigabitEthernet0/1 no ip address ! no shutdown interface gigabitEthernet0/1.1 encapsulation dot1q 11 ! encapsulation dot1q 1 ip address 192.168.1.1 255.255.255.0 interface gigabitEthernet0/1.10 encapsulation dot1q 10 ip address 192.168.11.1 255.255.255.0 ! ip address 192.168.10.1 255.255.255.0 interface gigabitEthernet0/1.20 encapsulation dot1q 20 ip address 192.168.20.1 255.255.255.0 end
Switch S1 Configuration:
hostname S1 enable secret class no ip domain-lookup line con 0 password cisco login logging synchronous line vty 0 15 password cisco login vlan 10 name R&D exit !vlan 20 ! name Engineering ! exit interface fastethernet0/1 switchport mode access ! switchport mode trunk interface fastethernet0/5 switchport mode trunk !interface fastethernet0/6 ! switchport access vlan 10 ! switchport mode access interface vlan1 ip address 192.168.1.11 255.255.255.0 ip default-gateway 192.168.1.1 end
Switch S2 Configuration:
hostname S2 enable secret class no ip domain-lookup line con 0 password cisco login logging synchronous line vty 0 15 password cisco login !vlan 10 ! name R&D ! exit vlan 20 name Engineering exit interface fastethernet0/1 switchport mode trunk interface fastethernet0/18 switchport access vlan 10 switchport mode access ! switchport access vlan 20 interface vlan1 ip address 192.168.1.12 255.255.255.0 ip default-gateway 192.168.1.1 end
Step 4: Save the running configuration to the startup configuration.
Part 2: Troubleshoot the Inter-VLAN Routing Configuration
In Part 2, you will verify the inter-VLAN routing configuration.
a. On R1, enter the show ip route command to view the routing table.
R1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is not set 209.165.200.0/24 is variably subnetted, 2 subnets, 2 masks C 209.165.200.224/27 is directly connected, Loopback0 L 209.165.200.225/32 is directly connected, Loopback0
Which networks are listed?
___________________________________________________
Only the 209.165.200.224 network.
Are there any networks missing in the routing table? If so, which networks?
___________________________________________________
192.168.1.0, 192.168.10.0, 192.168.20.0
What is one possible reason that a route would be missing from the routing table?
___________________________________________________
Interface administratively down, no ip address
b. On R1, issue the show ip interface brief command.
R1# show ip interface brief Interface IP-Address OK? Method Status Protocol Embedded-Service-Engine0/0 unassigned YES unset administratively down down GigabitEthernet0/0 unassigned YES unset administratively down down GigabitEthernet0/1 unassigned YES unset administratively down down GigabitEthernet0/1.1 192.168.1.1 YES manual administratively down down GigabitEthernet0/1.10 192.168.11.1 YES manual administratively down down GigabitEthernet0/1.20 192.168.20.1 YES manual administratively down down Serial0/0/0 unassigned YES unset administratively down down Serial0/0/1 unassigned YES unset administratively down down Loopback0 209.165.200.225 YES manual up up
Based on the output, are there any interface issues on the router? If so, what commands would resolve the issues?
____________________________________________________
R1(config)# interface g0/1
R1(config-if)# no shutdown
R1(config-if)# interface g0/1.10
R1(configs-if) ip address 192.168.10.1 255.255.255.0
c. On R1, re-issue the show ip route command.
R1# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is not set 192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.1.0/24 is directly connected, GigabitEthernet0/1.1 L 192.168.1.1/32 is directly connected, GigabitEthernet0/1.1 192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.11.0/24 is directly connected, GigabitEthernet0/1.10 L 192.168.11.1/32 is directly connected, GigabitEthernet0/1.10 192.168.20.0/24 is variably subnetted, 2 subnets, 2 masks C 192.168.20.0/24 is directly connected, GigabitEthernet0/1.20 L 192.168.20.1/32 is directly connected, GigabitEthernet0/1.20 209.165.200.0/24 is variably subnetted, 2 subnets, 2 masks C 209.165.200.224/27 is directly connected, Loopback0 L 209.165.200.225/32 is directly connected, Loopback0
Verify that all networks are available in the routing table. If not, continue to troubleshoot until all networks are present.
Part 3: Verify VLAN Configuration, Port Assignment, and Trunking
In Part 3, you will verify that the correct VLANs exist on both S1 and S2 and that trunking is configured correctly.
Step 1: Verify VLAN configuration and port assignments.
a. On S1, enter the show vlan brief command to view the VLAN database.
S1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 Fa0/6, Fa0/7, Fa0/8, Fa0/9 Fa0/10, Fa0/11, Fa0/12, Fa0/13 Fa0/14, Fa0/15, Fa0/16, Fa0/17 Fa0/18, Fa0/19, Fa0/20, Fa0/21 Fa0/22, Fa0/23, Fa0/24, Gi0/1 Gi0/2 10 R&D active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup
Which VLANs are listed? Ignore VLANs 1002 to 1005.
___________________________________________________
VLAN 1, VLAN 10
Are there any VLANs numbers or names missing in the output? If so, list them.
___________________________________________________
VLAN 20 name Engineering
Are the access ports assigned to the correct VLANs? If not, list the missing or incorrect assignments.
___________________________________________________
Fa0/6 needs to be assigned to the VLAN 10
If required, what commands would resolve the VLAN issues?
____________________________________________________
S1(config)# vlan 20
S1(config-vlan)# name Engineering
S1(config-vlan)# exit
S1(config)# interface fa0/6
S1(config-if)# switchport mode access
S1(config-if)# switchport access vlan 10
b. On S1, re-issue the show vlan brief command to verify configuration.
S1# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 Fa0/7, Fa0/8, Fa0/9, Fa0/10 Fa0/11, Fa0/12, Fa0/13, Fa0/14 Fa0/15, Fa0/16, Fa0/17, Fa0/18 Fa0/19, Fa0/20, Fa0/21, Fa0/22 Fa0/23, Fa0/24, Gi0/1, Gi0/2 10 R&D active Fa0/6 20 Engineering active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup
c. On S2, enter the show vlan brief command to view the VLAN database.
S2# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5 Fa0/6, Fa0/7, Fa0/8, Fa0/9 Fa0/10, Fa0/11, Fa0/12, Fa0/13 Fa0/14, Fa0/15, Fa0/16, Fa0/17 Fa0/19, Fa0/20, Fa0/21, Fa0/22 Fa0/23, Fa0/24, Gi0/1, Gi0/2 10 VLAN0010 active Fa0/18 20 Engineering active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup
Which VLANs are listed? Ignore VLANs 1002 to 1005.
___________________________________________________
VLAN 1, VLAN 10, VLAN 20
Are there any VLANs numbers or names missing in the output? If so, list them.
___________________________________________________
VLAN 10 missing name R&D
Are the access ports assigned to the correct VLANs? If not, list the missing or incorrect assignments.
___________________________________________________
F0/18 needs to be assigned to the VLAN 20 instead of 10
If required, what commands would resolve the VLAN issues?
___________________________________________________
S2(config)# vlan 10
S2(config-vlan)# name R&D
S2(config-vlan)# exit
S2(config)# interface fa0/18
S2(config-if)# switchport access vlan 20
d. On S2, re-issue the show vlan brief command to verify any configuration changes.
S2# show vlan brief VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5 Fa0/6, Fa0/7, Fa0/8, Fa0/9 Fa0/10, Fa0/11, Fa0/12, Fa0/13 Fa0/14, Fa0/15, Fa0/16, Fa0/17 Fa0/19, Fa0/20, Fa0/21, Fa0/22 Fa0/23, Fa0/24, Gi0/1, Gi0/2 10 R&D active 20 Engineering active Fa0/18 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup
Step 2: Verify trunking interfaces.
a. On S1, enter the show interface trunk command to view the trunking interfaces.
S1# show interface trunk Port Mode Encapsulation Status Native vlan Fa0/5 on 802.1q trunking 1 Port Vlans allowed on trunk Fa0/5 1-4094 Port Vlans allowed and active in management domain Fa0/5 1,10,20 Port Vlans in spanning tree forwarding state and not pruned Fa0/5 1,10,20
Which ports are in trunking mode?
_____________________________________________________
F0/5
Are there any ports missing in the output? If so, list them.
_____________________________________________________
F0/1
If required, what commands would resolve the port trunking issues?
_____________________________________________________
S1(config)# interface fa0/1
S1(configs-if)# switchport mode trunk
b. On S1, re-issue the show interface trunk command to verify any configuration changes.
S1# show interface trunk Port Mode Encapsulation Status Native vlan Fa0/1 on 802.1q trunking 1 Fa0/5 on 802.1q trunking 1 Port Vlans allowed on trunk Fa0/1 1-4094 Fa0/5 1-4094 Port Vlans allowed and active in management domain Fa0/1 1,10,20 Fa0/5 1,10,20 Port Vlans in spanning tree forwarding state and not pruned Fa0/1 none Fa0/5 1,10,20
c. On S2, enter the show interface trunk command to view the trunking interfaces.
S2# show interface trunk Port Mode Encapsulation Status Native vlan Fa0/1 on 802.1q trunking 1 Port Vlans allowed on trunk Fa0/1 1-4094 Port Vlans allowed and active in management domain Fa0/1 1,10,20 Port Vlans in spanning tree forwarding state and not pruned Fa0/1 1,10,20
Which ports are in trunking mode?
___________________________________________________
F0/1
Are there any ports missing in the output? If so, list them.
___________________________________________________
None
If required, what commands would resolve the port trunking issues?
___________________________________________________
All trunk ports configured correctly
Part 4: Test Layer 3 Connectivity
a. Now that you have corrected multiple configuration issues, let’s test connectivity.
From PC-A, is it possible to ping the default gateway for VLAN 10? ____Yes.
From PC-A, is it possible to ping PC-B?____Yes.
From PC-A, is it possible to ping Lo0? ____Yes.
If the answer is no to any of these questions, troubleshoot the configurations and correct the error.
Note: It may be necessary to disable the PC firewall for pings between PCs to be successful.
From PC-A, is it possible to ping S1? _____No.
From PC-A, is it possible to ping S2? _____No.
List some of the issues that could still be preventing successful pings to the switches.
______________________________________________________
Incorrect VLAN assignment on router subinterface, incorrect IP address on switch, no default gateway on switch
b. One way to help resolve where the error is occurring is to do a tracert from PC-A to S1.
C:\Users\User1> tracert 192.168.1.11 Tracing route to 192.168.1.11 over a maximum of 30 hops 1 <1 ms <1 ms <1 ms 192.168.10.1 2 * * * Request timed out. 3 * * * Request timed out. <output omitted>
This output shows that the request from PC-A is reaching the default gateway on R1 g0/1.10, but the packet stops at the router.
c. You have already verified the routing table entries for R1, now execute the show run | section interface command to verify VLAN configuration. List any configuration errors.
____________________________________________________
Interface g0/1.1 is assigned to VLAN 11 instead of VLAN 1
R1# show run | section interface interface Loopback0 ip address 209.165.200.225 255.255.255.224 interface Embedded-Service-Engine0/0 no ip address shutdown interface GigabitEthernet0/0 no ip address shutdown duplex auto speed auto interface GigabitEthernet0/1 no ip address duplex auto speed auto interface GigabitEthernet0/1.1 encapsulation dot1Q 11 ip address 192.168.1.1 255.255.255.0 interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 192.168.10.1 255.255.255.0 interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 192.168.20.1 255.255.255.0 interface Serial0/0/0 no ip address shutdown clock rate 2000000 interface Serial0/0/1 no ip address shutdown
What commands would resolve any issues found?
_____________________________________________________
R1(config)# interface g0/1.1
R1(config-if)# encapsulation dot1q 1
d. Verify that that pings from PC-A now reach both S1 and S2.
From PC-A, is it possible to ping S1? _____Yes.
From PC-A, is it possible to ping S2? _____Yes.
Reflection
What are the advantages of viewing the routing table for troubleshooting purposes?_______________________________________________________
All configured interfaces and subinterfaces are listed and can be easily examined for errors.
Router Interface Summary Table
| Router Interface Summary | ||||
|---|---|---|---|---|
| Router Model | Ethernet Interface #1 | Ethernet Interface #2 | Serial Interface #1 | Serial Interface #2 |
| 1800 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 1900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2801 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/1/0 (S0/1/0) | Serial 0/1/1 (S0/1/1) |
| 2811 | Fast Ethernet 0/0 (F0/0) | Fast Ethernet 0/1 (F0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| 2900 | Gigabit Ethernet 0/0 (G0/0) | Gigabit Ethernet 0/1 (G0/1) | Serial 0/0/0 (S0/0/0) | Serial 0/0/1 (S0/0/1) |
| Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combinations of Ethernet and Serial interfaces in the device. The table does not include any other type of interface, even though a specific router may contain one. An example of this might be an ISDN BRI interface. The string in parenthesis is the legal abbreviation that can be used in Cisco IOS commands to represent the interface. | ||||
Device Configs
Instructor Note: The VLANs configured do not display in the switch running configuration but are stored in the vlan.dat file.
Router R1
R1# show run Building configuration... Current configuration : 1522 bytes ! version 15.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R1 ! boot-start-marker boot-end-marker ! ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model memory-size iomem 15 ! ip cef ! ! ! ! ! ! no ip domain lookup no ipv6 cef multilink bundle-name authenticated ! ! ! ! ! ! ! ! ! ! ! interface Loopback0 ip address 209.165.200.225 255.255.255.224 ! interface Embedded-Service-Engine0/0 no ip address shutdown ! interface GigabitEthernet0/0 no ip address shutdown duplex auto speed auto ! interface GigabitEthernet0/1 no ip address duplex auto speed auto ! interface GigabitEthernet0/1.1 encapsulation dot1Q 1 ip address 192.168.1.1 255.255.255.0 ! interface GigabitEthernet0/1.10 encapsulation dot1Q 10 ip address 192.168.10.1 255.255.255.0 ! interface GigabitEthernet0/1.20 encapsulation dot1Q 20 ip address 192.168.20.1 255.255.255.0 ! interface Serial0/0/0 no ip address shutdown clock rate 2000000 ! interface Serial0/0/1 no ip address shutdown ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ! ! ! ! control-plane ! ! ! line con 0 password cisco logging synchronous login line aux 0 line 2 no activation-character no exec transport preferred none transport input all transport output pad telnet rlogin lapb-ta mop udptn v120 ssh stopbits 1 line vty 0 4 password cisco login transport input all ! scheduler allocate 20000 1000 ! end
Switch S1
S1# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/7, Fa0/8, Fa0/9, Fa0/10
Fa0/11, Fa0/12, Fa0/13, Fa0/14
Fa0/15, Fa0/16, Fa0/17, Fa0/18
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/23, Fa0/24, Gi0/1, Gi0/2
10 R&D active Fa0/6
20 Engineering active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
S1# show run
Building configuration...
Current configuration : 1453 bytes
!
!
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname S1
!
boot-start-marker
boot-end-marker
!
enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2
!
no aaa new-model
system mtu routing 1500
!
!
no ip domain-lookup
!
!
!
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface FastEthernet0/1
switchport mode trunk
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
switchport mode trunk
!
interface FastEthernet0/6
switchport access vlan 10
switchport mode access
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
!
interface FastEthernet0/24
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
ip address 192.168.1.11 255.255.255.0
!
ip default-gateway 192.168.1.1
ip http server
ip http secure-server
!
!
!
line con 0
password cisco
logging synchronous
login
line vty 0 4
password cisco
login
line vty 5 15
password cisco
login
!
end
Switch S2
S2# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5
Fa0/6, Fa0/7, Fa0/8, Fa0/9
Fa0/10, Fa0/11, Fa0/12, Fa0/13
Fa0/14, Fa0/15, Fa0/16, Fa0/17
Fa0/19, Fa0/20, Fa0/21, Fa0/22
Fa0/23, Fa0/24, Gi0/1, Gi0/2
10 R&D active
20 Engineering active Fa0/18
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
S2# show run
Building configuration...
Current configuration : 1458 bytes
!
!
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname S2
!
boot-start-marker
boot-end-marker
!
enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2
!
no aaa new-model
system mtu routing 1500
!
!
no ip domain-lookup
!
!
!
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface FastEthernet0/1
switchport mode trunk
!
interface FastEthernet0/2
!
interface FastEthernet0/3
!
interface FastEthernet0/4
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
!
interface FastEthernet0/8
!
interface FastEthernet0/9
!
interface FastEthernet0/10
!
interface FastEthernet0/11
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
interface FastEthernet0/14
!
interface FastEthernet0/15
!
interface FastEthernet0/16
!
interface FastEthernet0/17
!
interface FastEthernet0/18
switchport access vlan 20
switchport mode access
!
interface FastEthernet0/19
!
interface FastEthernet0/20
!
interface FastEthernet0/21
!
interface FastEthernet0/22
!
interface FastEthernet0/23
!
interface FastEthernet0/24
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface Vlan1
ip address 192.168.1.12 255.255.255.0
!
ip default-gateway 192.168.1.1
ip http server
ip http secure-server
!
!
line con 0
password cisco
logging synchronous
login
line vty 0 4
password cisco
login
line vty 5 15
password cisco
login
!
end
