Final-Exam: Network Addressing and Basic Troubleshooting Final Exam Answers (Course Final Exam)
1. Match each item to the type of topology diagram on which it is typically identified.
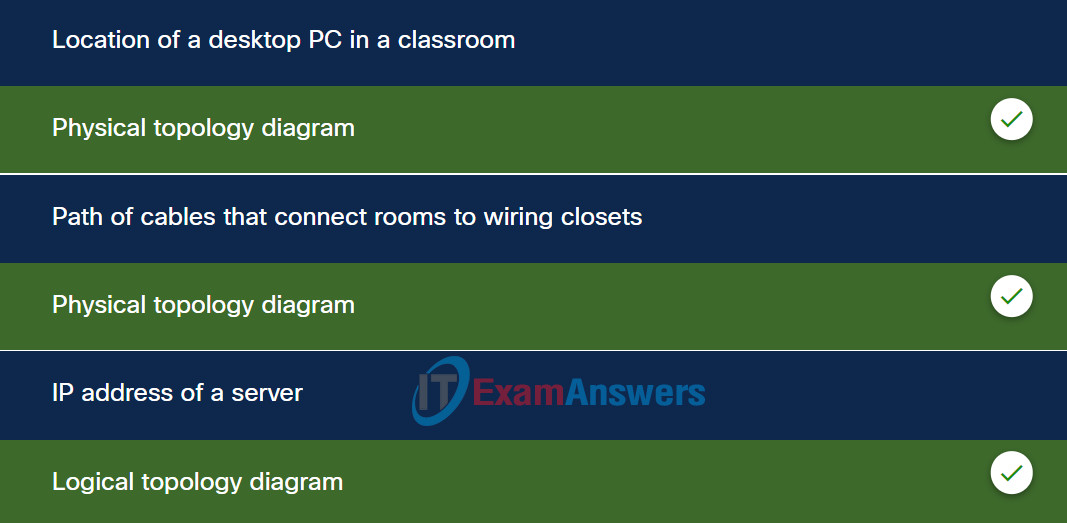
Explanation: Place the options in the following order:
| location of a desktop PC in a classroom |
physical topology diagram |
| path of cables that connect rooms to wiring closets |
physical topology diagram |
| IP address of a server |
logical topology diagram |
2. Refer to the exhibit. The IP address of which device interface should be used as the default gateway setting of host H1?
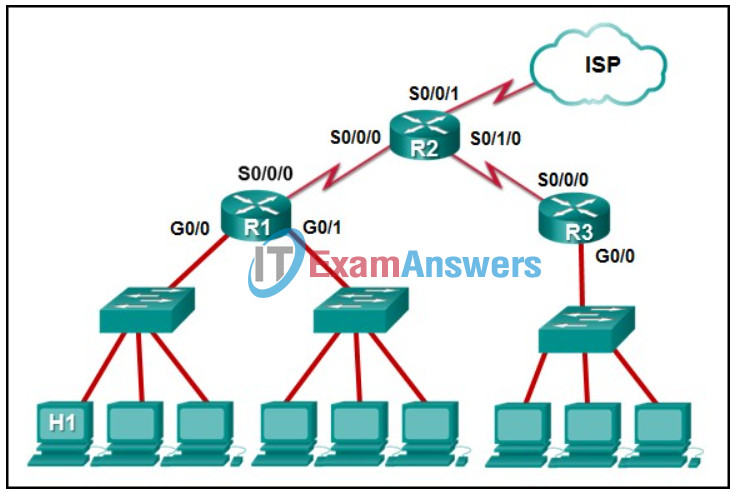
- R1: G0/0
- R2: S0/0/1
- R2: S0/0/0
- R1: S0/0/0
Explanation: The default gateway for host H1 is the router interface that is attached to the LAN that H1 is a member of. In this case, that is the G0/0 interface of R1. H1 should be configured with the IP address of that interface in its addressing settings. R1 will provide routing services to packets from H1 that need to be forwarded to remote networks.
3. What are two advantages of using fiber-optic cabling to interconnect devices? (Choose two.)
- Fiber-optic cables can extend several miles.
- Fiber-optic cable is immune from EMI and RFI.
- Fiber-optic cables are easy to install..
- Fiber-optic cables are commonly found in both homes and small businesses.
- Fiber-optic cables use extra shielding to protect copper wires.
Explanation: Fiber-optic cables provide immunity to both EMI and RFI and a single cable can extend for several miles before regeneration is needed.
4. Which statement is true about the CSMA/CD access method that is used in Ethernet?
- When a device hears a carrier signal and transmits, a collision cannot occur.
- All network devices must listen before transmitting.
- A jamming signal causes only devices that caused the collision to execute a backoff algorithm.
- Devices involved in a collision get priority to transmit after the backoff period.
Explanation: Legacy bus-topology Ethernet LAN uses CSMA/CD as network media access control protocol. It works by detecting a collision in the medium and backing off (after transmitting a jam signal) as necessary. When one host wants to transmit a frame, it listens on the medium to check if the medium is busy. After it senses that no one else is transmitting, the host starts transmitting the frame, it also monitors the current level to detect a collision. If it detects a collision, it transmits a special jam signal so that all other hosts can know there was a collision. The other host will receive this jam signal and stop transmitting. After this, both hosts enter an exponential backoff phase and retry transmission.
5. Which two characteristics describe the use of a logical topology? (Choose two.)
- showing the physical connections of end devices
- identifying the interconnection of routers and switches
- describing the infrastructure
- identifying the virtual connections between devices
- identifying the type of media access control used
- identifying cable length requirements
Explanation: Physical topology refers to the physical connection and how hosts, switches, and routers are physically connected. Logical topology refers to how nodes transfer frames through virtual connections and how the upper layers perceive the network.
6. Which command can be used on a Windows host to display the routing table?
- show ip route
- tracert
- netstat –r
- netstat –s
Explanation: On a Windows host, either the route print or netstat -r commands can be used to display the host routing table. The show ip route command is used on a router to display its routing table. The netstat –s command is used to display per-protocol statistics. The tracert command is used to display the path that a packet travels to its destination.
7. Refer to the exhibit. Consider the IP address configuration shown from PC1. What is a description of the default gateway address?
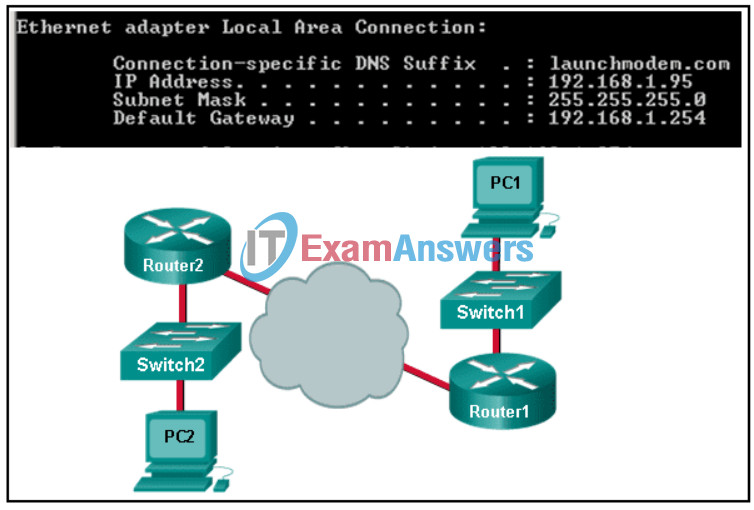
- It is the IP address of the Router1 interface that connects the PC1 LAN to Router1.
- It is the IP address of the Router1 interface that connects the company to the Internet.
- It is the IP address of Switch1 that connects PC1 to other devices on the same LAN.
- It is the IP address of the ISP network device located in the cloud.
Explanation: The default gateway is used to route packets destined for remote networks. The default gateway IP address is the address of the first Layer 3 device (the router interface) that connects to the same network.
8. Match the characteristics to the correct type of fiber.
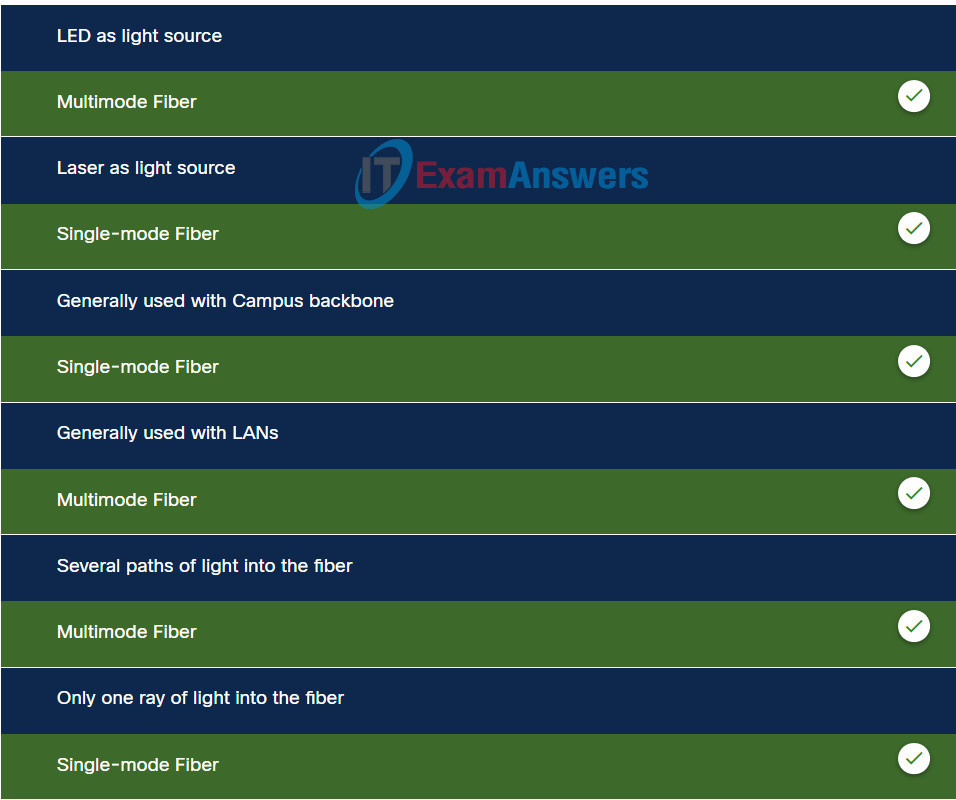
Explanation: Options matched to the correct selection.
| Multimode Fiber |
Single-mode Fiber |
| LED as light source |
only one ray of light into the fiber |
| several paths of light into the fiber |
generally used with Campus backbone |
| generally used with LANs |
laser as light source |
9. A user can access a file share resource on a server located in the same office but cannot access the internet. What is the possible cause?
- The IPv4 address and subnet mask are misconfigured on the PC.
- The default gateway address is misconfigured on the PC.
- The switch is malfunctioning.
- The DHCP server is disconnected.
Explanation: The fact that the user can access a file share resource but not the internet indicates the issue might be caused by default gateway misconfiguration. If no default gateway is configured in the host TCP/IP settings, or if the wrong default gateway is specified, messages addressed to hosts on the internet cannot be delivered.
10. Which statement describes the operation of devices accessing an Ethernet network?
- Each device monitors the media and sends a notification for its intention to send data first.
- To send data, each device waits for a token to be available.
- Each device monitors the media and sends data when the media is free.
- Each device in turn receives a frame. If the frame is not intended for the device, the device passes it along.
Explanation: Ethernet uses CSMA/CD as the access control method. With CSMA/CD, each end device monitors the media for the presence of a data signal. If the media is free, the device can transmit data immediately. The other options are operations with CSMA/CA and Token passing.
11. A PC has sent an RS message to an IPv6 router attached to the same network. Which two pieces of information will the router send to the client? (Choose two.)
- subnet mask in dotted decimal notation
- administrative distance
- domain name
- prefix length
- DNS server IP address
- prefix
Explanation: A router interface that has been configured with IPv6 addressing information responds to a router solicitation (RS) message with a router advertisement (RA) message. The RA message is used in the IPv6 stateless address autoconfiguration (SLAAC) process and the message contains the local prefix and prefix length of the local segment such as 2001:db8:acad:1::/64.
12. Which two types of messages are used in place of ARP for address resolution in IPv6? (Choose two.)
- echo reply
- neighbor solicitation
- broadcast
- neighbor advertisement
- anycast
- echo request
Explanation: IPv6 does not use ARP. Instead, ICMPv6 neighbor discovery is used by sending neighbor solicitation and neighbor advertisement messages.
13. A site administrator has been told that a particular network at the site must accommodate 126 hosts. Which subnet mask would be used that contains the required number of host bits?
- 255.255.255.240
- 255.255.255.0
- 255.255.255.224
- 255.255.255.128
Explanation: The subnet mask of 255.255.255.0 has 8 host bits. The mask of 255.255.255.128 results in 7 host bits. The mask of 255.255.255.224 has 5 host bits. Finally, 255.255.255.240 represents 4 host bits.
14. An IPv6 enabled device sends a data packet with the destination address of FF02::1. What is the target of this packet?
- only IPv6 configured routers
- only IPv6 DHCP servers
- all IPv6 enabled devices on the local link or network
- the one IPv6 device on the link that has been uniquely configured with this address
Explanation: This address is one of the assigned IPv6 multicast addresses. Packets addressed to FF02::1 are for all IPv6 enabled devices on the link or network. FF02::2 is for all IPv6 routers that exist on the network.
15. What are two services provided by IPv6 neighbor discovery protocol? (Choose two.)
- maximum IPv6 packet size for end-to-end transmission
- IPv6 dynamic routing
- domain name resolving
- router discovery
- address resolution
Explanation: IPv6 Neighbor Discovery protocol, also referred to as ND or NDP, provides address resolution, router discovery, and redirection services for IPv6 using ICMPv6.
16. Match the ICMPv6 messages to the description.
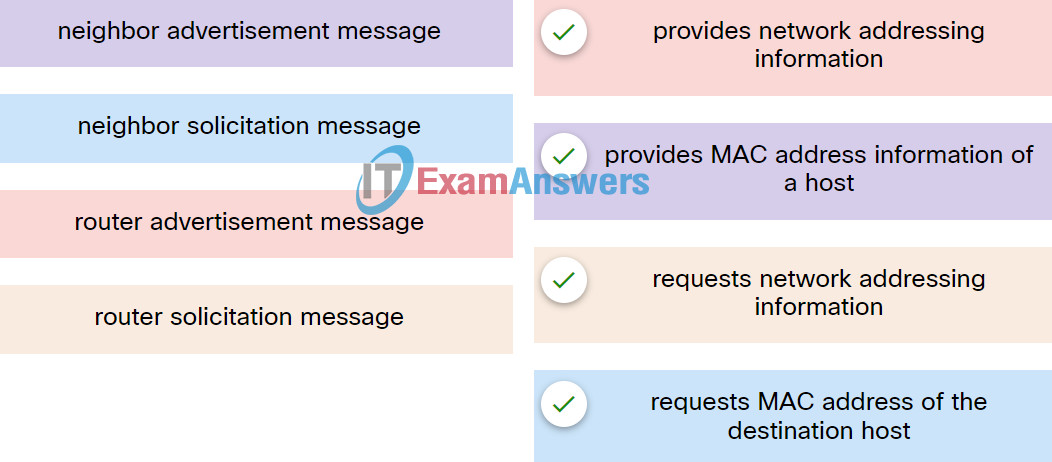
Explanation: Place the options in the following order:
| router advertisement message |
provides network addressing information |
| neighbor advertisement message |
provides MAC address information of a host |
| router solicitation message |
requests network addressing information |
| neighbor solicitation message |
requests MAC address of the destination host |
17. A network administrator is assigned the 172.16.0.0/24 block of addresses to use in designing an IP addressing scheme. The administrator submits this design for approval:
- 172.16.0.0/26
- 172.16.0.64/27
- 172.16.0.96/26
- 172.16.0.128/27
What should be the response from the senior network engineer regarding this design?
- This design is flawed because the 172.16.0.96/26 network is not a valid block of addresses.
- This design is flawed because the 172.16.0.96/26 network overlaps with other addresses.
- This design is flawed because no design could have two networks that use a /26 mask and are not consecutive blocks of addresses.
- This design is flawed because the 172.16.0.128/27 network number is invalid.
- This design will work for the branch office.
Explanation: The valid numbers that can be used with a /26 mask include 172.16.0.0/26, 172.16.0.64/26, 172.16.0.128/26, and 172.16.0.192/26.
18. What is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15:A
- 2001:DB8:BC15:A:1
- 2001:DB8:BC15:A:12
- 2001:DB8:BC15
Explanation: The network portion, or prefix, of an IPv6 address is identified through the prefix length. A /64 prefix length indicates that the first 64 bits of the IPv6 address is the network portion. Hence the prefix is 2001:DB8:BC15:A.
19. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network.
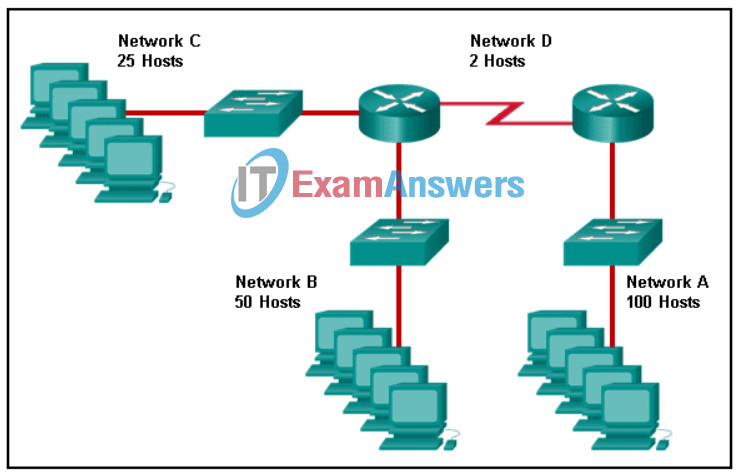

Explanation: Place the options in the following order:
| Network C |
192.168.0.96 /27 |
| Network A |
192.168.0.128 /25 |
| Network D |
192.168.0.80 /30 |
| Network B |
192.168.0.0 /26 |
20. IPv6 host A is communicating with a remote IPv6 host B. Which device would send ICMPv6 redirect messages to inform that a better next-hop device should be used?
- Host A
- a router in the traffic path
- the switch connected to Host A
- Host B
- the switch connected to Host B
Explanation: When a router receives a data packet, it may analyze the best gateway device that the host should use. When there are multiple gateway devices available on a network, an IPv6 router will send ICMPv6 redirect messages to the sending host if it determines that there is a more efficient path for the transmissions.
21. Which two statements correctly describe the components of a router? (Choose two.)
- ROM contains diagnostics executed on hardware modules.
- NVRAM stores a backup copy of the IOS used during the boot sequence.
- Flash memory does not lose its contents during a reboot.
- RAM permanently stores the configuration file used during the boot sequence.
- ROM contains the most current and most complete version of the IOS.
- Flash contains boot system commands to identify the location of the IOS.
Explanation: A router contains four types of memory:
RAM – volatile memory used to store the running IOS, running configuration file, routing table, ARP table, as well as serve as a packet buffer
ROM – nonvolatile memory used to hold a limited version of the IOS, bootup instructions, and basic diagnostic software
NVRAM – nonvolatile memory used to hold the startup configuration file
Flash – nonvolatile memory used to hold the IOS and other system files
22. Match the phases to the functions during the boot up process of a Cisco router.
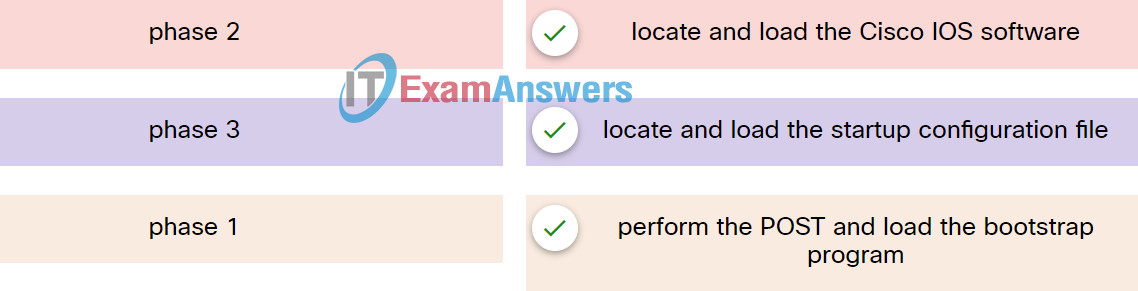
Explanation: Place the options in the following order:
| phase 2 |
locate and load the Cisco IOS software |
| phase 3 |
locate and load the startup configuration file |
| phase 1 |
perform the POST and load the bootstrap program |
23. A workstation connected to an Ethernet switch port is experiencing connectivity problems. The network technician chooses to use the bottom-up troubleshooting method to identify the issue. What are two possible causes of physical layer network problems that the technician should check? (Choose two.)
- logical addressing issues
- incorrect MAC address assigned
- cables plugged into wrong ports
- incorrect subnet mask on an interface
- improperly terminated cables
- packets received out of sequence
Explanation: Physical problems are concerned mainly with the hardware aspects of computers and networking devices, and the cables that interconnect them. Physical problems do not include the logical (software) configuration of devices.
24. A production switch is reloaded and finishes with a Switch> prompt. What two facts can be determined? (Choose two.)
- The switch did not locate the Cisco IOS in flash, so it defaulted to ROM.
- The boot process was interrupted.
- A full version of the Cisco IOS was located and loaded.
- There is not enough RAM or flash on this router.
- POST occurred normally.
Explanation: A switch booting to the Switch> prompt indicates that the switch booted normally. This means a the switch successfully completed POST full version of the Cisco IOS was loaded.
25. A user is complaining that an external web page is taking longer than normal to load.The web page does eventually load on the user machine. Which tool should the technician use with administrator privileges in order to locate where the issue is in the network?
- tracert
- nslookup
- ipconfig /displaydns
- ping
Explanation: The Command Prompt command tracert will map the path from the PC to the web server and measure transit delays of packets across the network.
26. What are two characteristics of RAM on a Cisco device? (Choose two.)
- RAM is able to store multiple versions of IOS and configuration files.
- The configuration that is actively running on the device is stored in RAM.
- The contents of RAM are lost during a power cycle.
- RAM provides nonvolatile storage.
- RAM is a component in Cisco switches but not in Cisco routers.
Explanation: RAM stores data that is used by the device to support network operations. The running configuration is stored in RAM. This type of memory is considered volatile memory because data is lost during a power cycle. Flash memory stores the IOS and delivers a copy of the IOS into RAM when a device is powered on. Flash memory is nonvolatile since it retains stored contents during a loss of power.
27. An ISP help desk technician receives a call from a customer who reports that no one at their business can reach any websites or get their e-mail. After testing the communication line and finding everything fine, the technician instructs the customer to run nslookup from the command prompt. What does the technician suspect is causing the customer’s problem?
- improper IP address configuration on the host
- failure of DNS to resolve names to IP addresses
- hardware failure of the ISR used to connect the customer to the ISP
- bad cables or connections at the customer site
Explanation: The nslookup command can be used to troubleshoot name resolution issues and to verify the current status of the name servers. The nslookup output identifies the default DNS server that is configured on the host. The utility has many options available for testing and verification of the DNS process.
28. Which information does the show startup-config command display?
- the contents of the current running configuration file in the RAM
- the IOS image copied into RAM
- the bootstrap program in the ROM
- the contents of the saved configuration file in the NVRAM
Explanation: The show startup-config command displays the saved configuration located in NVRAM. The show running-config command displays the contents of the currently running configuration file located in RAM.
29. What is true concerning physical and logical topologies?
- Physical topologies are concerned with how a network transfers frames.
- The logical topology is always the same as the physical topology.
- Physical topologies display the IP addressing scheme of each network.
- Logical topologies refer to how a network transfers data between devices.
Explanation: Physical topologies show the physical interconnection of devices. Logical topologies show the way the network will transfer data between connected nodes.
30. After making configuration changes on a Cisco switch, a network administrator issues a copy running-config startup-config command. What is the result of issuing this command?
- The configuration changes will be removed and the original configuration will be restored.
- The new configuration will be stored in flash memory.
- The current IOS file will be replaced with the newly configured file.
- The new configuration will be loaded if the switch is restarted.
Explanation: With the copy running-config startup-config command, the content of the current operating configuration replaces the startup configuration file stored in NVRAM. The configuration file saved in NVRAM will be loaded when the device is restarted.
31. In the OSI model, what three functional areas are addressed by physical layer standards? (Choose three.)
- frame encapsulation
- error detection and retransmission
- encoding
- physical components
- signaling
- media access control
Explanation: The physical layer standards address three functional areas: physical components, encoding, and signaling. Frame encapsulation, media access control, and error detection and retransmission are services provided by the data link layer.
32. Which two types of signal interference are reduced more by STP than by UTP? (Choose two.)
- dispersion
- MDF
- RFI
- EMI
- white noise
Explanation: RFI, EMI, and crosstalk cause interference to the electrical signals that are transmitted through copper cables. Both UTP and STP use twisted pairs of wires that help protect against crosstalk. However, STP provides greater protection against RFI and EMI than UTP provides.
33. An IPv6 host receives an ICMPv6 message requesting MAC address resolution. Which message should the host return to provide the MAC address?
- neighbor solicitation message
- neighbor advertisement message
- router advertisement message
- router solicitation message
Explanation: When an IPv6 host receives an ICMPv6 neighbor solicitation message for MAC address resolution, the host would return a neighbor advertisement message to provide the MAC address.
34. A technician must accommodate at least 500 subnets from address 172.16.0.0/16. What is an appropriate subnet mask and corresponding number of available host IP addresses per subnet to meet the requirement?
- 255.255.255.192 and 126 hosts
- 255.255.255.0 and 128 hosts
- 255.255.255.128 and 126 hosts
- 255.255.255.224 and 128 hosts
Explanation: The network address 172.16.0.0 has a default mask of 255.255.0.0 (/16). This address has 16 bits in the network portion and 16 bits in the host portion. To have at least 500 subnets, you need to borrow 9 bits (subnets) from the host portion (2^9 = 512 subnets), leaving 7 bits to create hosts. Thus the resulting netmask is 255.255.255.128, and the number of hosts per subnet is 2^7 = 128 – 2 = 126 hosts.
35. What is the interface ID of the IPv6 address 2001:DB8::1000:A9CD:47FF:FE57:FE94/64?
- 47FF:FE57:FE94
- FE57:FE94
- A9CD:47FF:FE57:FE94
- 1000:A9CD:47FF:FE57:FE94
- FE94
Explanation: The interface ID of an IPv6 address is the rightmost 64 bits, or last four hextets, of the address if no interface ID bits have been used for subnets.
36. What would be the interface ID of an IPv6 enabled interface with a MAC address of 1C-6F-65-C2-BD-F8 when the interface ID is generated by using the EUI-64 process?
- 1E6F:65FF:FEC2:BDF8
- C16F:65FF:FEC2:BDF8
- 0C6F:65FF:FEC2:BDF8
- 106F:65FF:FEC2:BDF8
Explanation: To derive the EUI-64 interface ID by using the MAC address 1C-6F-65-C2-BD-F8, three steps are taken.
- Change the seventh bit of the MAC address from a binary 0 to a binary 1 which changes the hex C, into a hex E.
- Insert hex digits FFFE into the middle of the address.
- Rewrite the address in IPv6 format.
The three steps, when complete, give the interface ID of 1E6F:65FF:FEC2:BDF8.
37. Which troubleshooting tool can be used to determine the current TCP open connections on a PC?
- tracrt
- nslookup
- netstat
- ping
- ipconfig
Explanation: The netstat command displays active TCP connections that are open and running on a networked host. The netstat command lists the protocol in use, the local address and port number, the foreign address and port number, and the state of the connection.
38. A group of Windows PCs in a new subnet has been added to an Ethernet network. When testing the connectivity, a technician finds that these PCs can access local network resources but not the Internet resources. To troubleshoot the problem, the technician wants to initially confirm the IP address and DNS configurations on the PCs, and also verify connectivity to the local router. Which three Windows CLI commands and utilities will provide the necessary information? (Choose three.)
- netsh interface ipv6 show neighbor
- tracert
- nslookup
- ping
- arp -a
- ipconfig
- telnet
Explanation: The ipconfig and nslookup commands will provide initial IP address and DNS configuration information to the technicians and determine if DHCP is assigning correct information to the PCs. The ping utility would be used to verify, or not, connectivity to the default gateway (router) using the configured default gateway address, or using the known correct default gateway address if these are found to be different. The arp -a or netsh interface ipv6 show neighbor commands could be used if the problem is then suspected to be an IP address to MAC address mapping issue. The telnet and tracert utilities could be used to determine where the problem was located in the network if the default gateway configuration was found to be correct.
39. Refer to the exhibit. PC1 is unable to access PC2. To troubleshoot this problem, the technician needs to confirm that the next hop interface is operational. Which default gateway address should the technician ping from PC1 to confirm this?
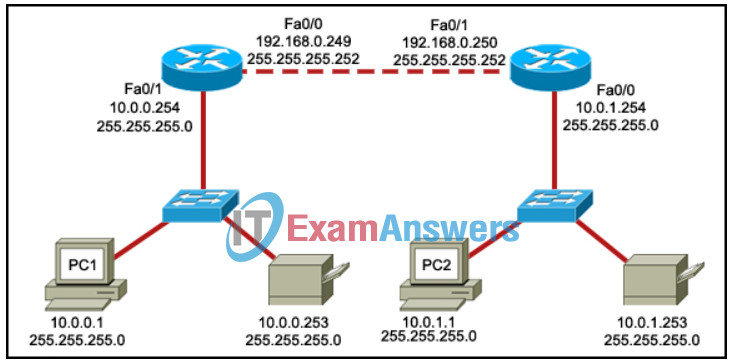
- 10.0.0.254
- 10.0.1.254
- 192.168.0.250
- 192.168.0.249
Explanation: A successful ping to the default gateway assigned to a PC is an indicator that the PC can communicate across the network. The default gateway must be on the same IP network as the PC, and is usually the IP address of the router interface connected to the same physical network as the PC.
40. Refer to the exhibit. An IT consulting firm is helping a mid-sized marketing and advertising company for updating the campus network. Which three network design features are covered in the diagram? (Choose three.)
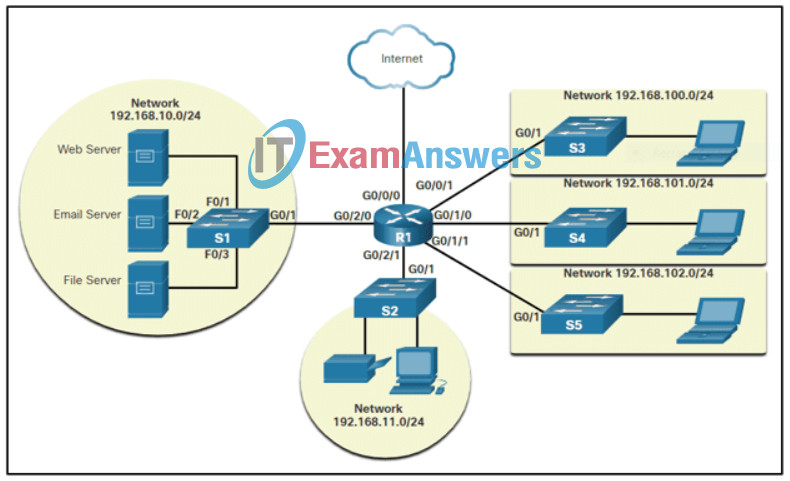
- flow of information in the network including addressing
- network devices that might be needed
- network segmentation
- data packet routing and protocol needs
- IP network subnetting consideration
- locations of network devices in the company
Explanation: The exhibit shows a logical topology diagram for the network design. The network design features shown in this diagram includes flow of information in the network including addressing, network devices that might be needed, and network segmentation provisioned through a router. The suggested IP address blocks are with the default subnet mask, no subnetting is required. While network devices are grouped logically in the diagram, the locations are not determined or indicated. Routing will be required, but there is no indication of which routing protocol should be used.
41. Refer to the exhibit. Using VLSM, what is the largest and smallest subnet mask required on this network, including the links between routers, in order to minimize address waste?
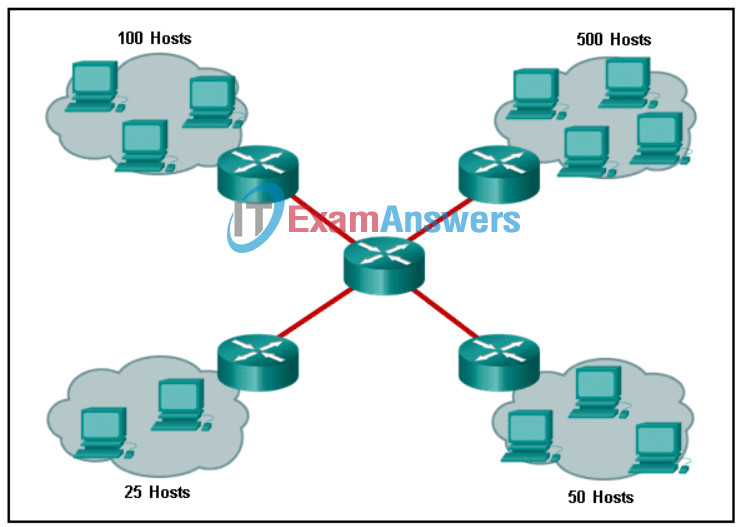
- 255.255.255.0 and 255.255.255.252
- 255.255.254.0 and 255.255.255.252
- 255.255.255.128 and 255.255.255.224
- 255.255.254.0 and 255.255.255.224
Explanation: The largest subnet requires 500 hosts addresses, so the most efficient subnet would be a /23 with the mask 255.255.254.0. The smallest subnet, the links between the routers, requires two addresses each, so a /30 subnet with the mask 255.255.255.252 is required.
42. IPv6 host A is sending a neighbor solicitation message to IPv6 host B on the same Ethernet network. Which statement describes the destination MAC address host A uses to build the Ethernet frame of the neighbor solicitation message?
- It maps the special braodcast address reserved for neighbor discovery protocol.
- It maps the special solicited-node multicast address of the destination IPv6 address.
- It maps the special IPv6 unicast address reserved for neighbor discovery protocol.
- It maps the special address from the router advertisement message.
Explanation: When an IPv6 host sends a neighbor solicitation message to another IPv6 host on the same Ethernet network, the sending host creates an Ethernet frame and add a multicast MAC address in the Destination MAC address field. This multicast MAC address maps the special solicited-node multicast address derived from the destination IPv6 address.
43. Refer to the exhibit. Considering the addresses already used and having to remain within the 10.16.10.0/24 network range, which subnet address could be assigned to the network containing 25 hosts?
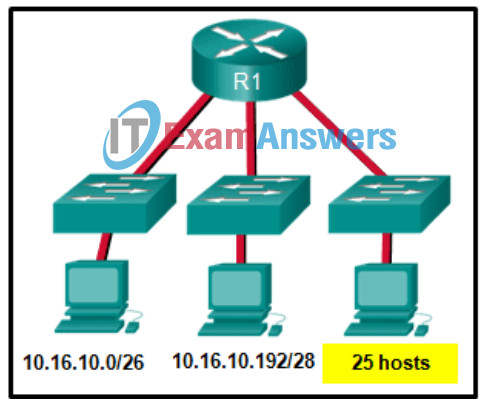
- 10.16.10.240/28
- 10.16.10.240/27
- 10.16.10.160/26
- 10.16.10.64/27
- 10.16.10.128/28
- 10.16.10.224/26
Explanation: Addresses 10.16.10.0 through 10.16.10.63 are taken for the leftmost network. Addresses 10.16.10.192 through 10.16.10.207 are used by the center network.The address space from 208-255 assumes a /28 mask, which does not allow enough host bits to accommodate 25 host addresses.The address ranges that are available include 10.16.10.64/26 and10.16.10.128/26. To accommodate 25 hosts, 5 host bits are needed, so a /27 mask is necessary. Four possible /27 subnets could be created from the available addresses between 10.16.10.64 and 10.16.10.191:
10.16.10.64/27
10.16.10.96/27
10.16.10.128/27
10.16.10.160/27
44. Which IPv6 prefix is reserved for communication between devices on the same link?
- FE80::/10
- 2001::/32
- FDFF::/7
- FC00::/7
Explanation: IPv6 link-local unicast addresses are in the FE80::/10 prefix range and are not routable. They are used only for communications between devices on the same link.
45. Refer to the exhibit. A user has configured a NIC on the PC as shown but finds that the PC is unable to access the Internet. What is the problem?
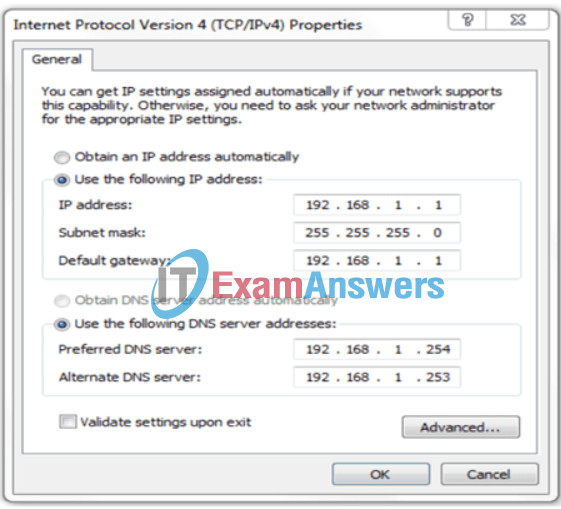
- There should not be an alternate DNS server.
- The preferred DNS address is incorrect.
- The default gateway address is incorrect.
- The settings were not validated upon exit.
Explanation: In order for a computer to communicate outside its network, it must have a valid default gateway configured.This address cannot be the same as the IP address of the computer.
46. Which type of static route creates a gateway of last resort?
- standard static route
- floating static route
- summary static route
- default static route
Explanation: There are four basic types of static routes. Floating static routes are backup routes that are placed into the routing table if a primary route is lost. A summary static route aggregates several routes into one, reducing the size of the routing table. Standard static routes are entered manually into the routing table. Default static routes create a gateway of last resort.
47. Refer to the exhibit. The PC is connected to the console port of the switch. All the other connections are made through FastEthernet links. Which types of UTP cables can be used to connect the devices?
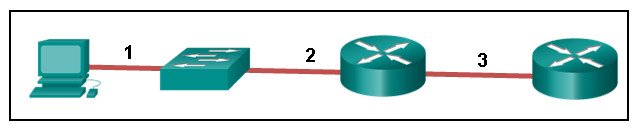
1 – rollover, 2 – crossover, 3 – straight-through
1 – rollover, 2 – straight-through, 3 – crossover
1 – crossover, 2 – rollover, 3 – straight-through
1 – crossover, 2 – straight-through, 3 – rollover
Explanation: A straight-through cable is commonly used to interconnect a host to a switch and a switch to a router. A crossover cable is used to interconnect similar devices together like switch to a switch, a host to a host, or a router to a router. If a switch has the MDIX capability, a crossover could be used to connect the switch to the router; however, that option is not available. A rollover cable is used to connect to a router or switch console port.
48. Consider the following command:
ip route 192.168.10.0 255.255.255.0 10.10.10.2 5
Which route would have to go down in order for this static route to appear in the routing table?
- a default route
- a static route to the 192.168.10.0/24 network
- an EIGRP-learned route to the 192.168.10.0/24 network
- an OSPF-learned route to the 192.168.10.0/24 network
Explanation: The administrative distance of 5 added to the end of the static route creates a floating static situation for a static route that goes down. Static routes have a default administrative distance of 1. This route that has an administrative distance of 5 will not be placed into the routing table unless the previously entered static route to the 192.168.10.0/24 goes down or was never entered. The administrative distance of 5 added to the end of the static route configuration creates a floating static route that will be placed in the routing table when the primary route to the same destination network goes down. By default, a static route to the 192.168.10.0/24 network has an administrative distance of 1. Therefore, the floating route with an administrative distance of 5 will not be placed into the routing table unless the previously entered static route to the 192.168.10.0/24 goes down or was never entered. Because the floating route has an administrative distance of 5, the route is preferred to an OSPF-learned route (with the administrative distance of 110) or an EIGRP-learned route (with the administrative distance of 110) to the same destination network.
49. A technician has been asked to develop a physical topology for a network that provides a high level of availability. Which physical topology requires that every node is attached to every other node on the network?
- hierarchical
- bus
- ring
- mesh
- star
Explanation: The mesh topology provides high availability because every node is connected to all other nodes. Mesh topologies can be found in WANs. A partial mesh topology can also be used where some, but not all, end points connect to one another.
50. What type of communication rule would best describe CSMA/CD?
- message encoding
- flow control
- access method
- message encapsulation
Explanation: Carrier sense multiple access collision detection (CSMA/CD) is the access method used with Ethernet. The access method rule of communication dictates how a network device is able to place a signal on the carrier. CSMA/CD dictates those rules on an Ethernet network and CSMA/CA dictates those rules on an 802.11 wireless LAN.
51. What are three parts of an IPv6 global unicast address? (Choose three.)
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- a subnet ID that is used to identify networks inside of the local enterprise site
- an interface ID that is used to identify the local host on the network
Explanation: There are three elements that make up an IPv6 global unicast address. A global routing prefix which is provided by an ISP, a subnet ID which is determined by the organization, and an interface ID which uniquely identifies the interface interface of a host.
52. Match the characteristic with the appropriate copper media.
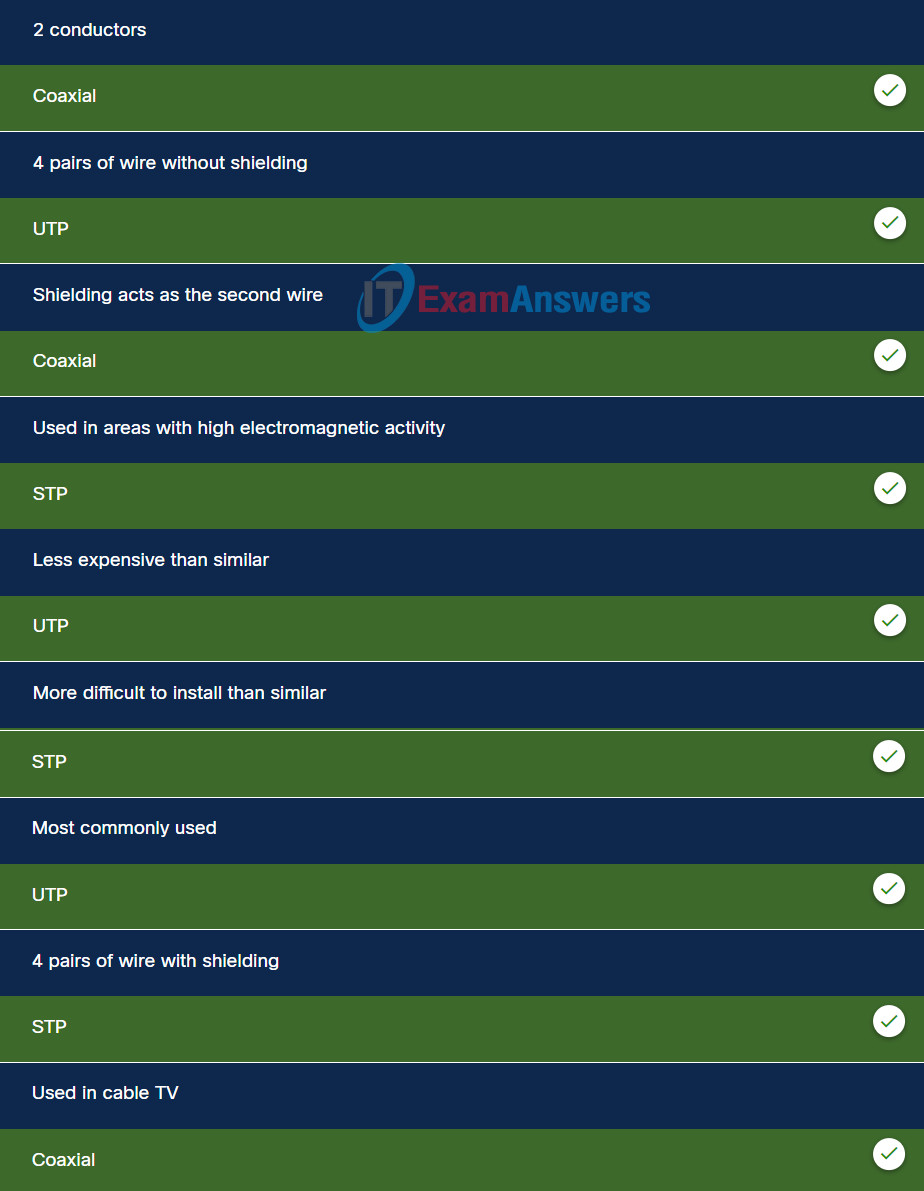
Explanation: Options matched to the correct selection.
| coaxial |
UTP |
STP |
| 2 conductors |
4 pairs of wire without shielding |
4 pairs of wire with shielding |
| used in cable TV |
less expensive than similar |
used in areas with high electromagnetic activity |
| shielding acts as the second wire |
most commonly used |
more difficult to install than similar |















