Lab Objective:
The objective of this lab exercise is for you to learn and understand how to configure pool-based PAT.
Lab Purpose:
PAT configuration is a fundamental skill. PAT provides many-to-one translation using random port numbers. This means that multiple inside hosts can use the same outside address to communicate with external devices, while hiding their private IP addresses. Like dynamic NAT, PAT works in one direction only: from the inside to the outside. Pool-based PAT translates all private IP addresses to the outside interface on the router. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to configure pool-based Port Address Translation.
Certification Level:
This lab is suitable for CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 8/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 10 minutes.
Lab Topology:
Please use the following topology to complete this lab exercise:
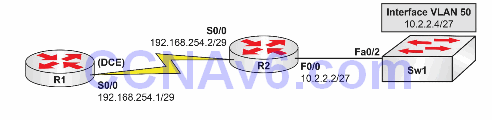
Task 1:
Configure the hostnames on R1, R2, and Sw1 as illustrated in the topology.
Task 2:
Configure R1 S0/0, which is a DCE, to provide a clock rate of 256 Kbps to R2. Configure the IP addresses on the Serial interfaces of R1 and R2 as illustrated in the topology.
Task 3:
Configure VLAN50, named NAT_VLAN, on Sw1. Assign the FastEthernet0/2 interface on Sw1 to this VLAN. Also, configure R1 to allow Telnet access using the password CISCO.
Task 4:
Configure interface VLAN50 on Sw1 and assign it the IP address illustrated in the topology. The default gateway on Sw1 should be 10.2.2.2. Next, configure interface FastEthernet0/0 on R2 and assign it the IP address illustrated in the topology.
Task 5:
Test connectivity by pinging from R1 to R2 and pinging from R2 to Sw1. These should all be successful. However, since R1 does not know about the 10.2.2.0/27 subnet, Sw1 will not be able to ping R1, or vice versa.
Task 6:
Create an ACL to permit all IP traffic from the 10.2.2.0/27 subnet to the 192.168.254.0/29 subnet. You can create either a named or numbered ACL to complete this task.
Task 7:
Configure R2 F0/0 as the inside interface for NAT and S0/0 as the outside interface for NAT. Next, configure a pool called PAT-POOL to be used for PAT translation. This pool should have both a single starting and ending IP address of 192.168.254.4. Use the same subnet mask as that of S0/0 for this pool.
Task 8:
Configure PAT on R2 to translate traffic specified in the ACL configured in Task 6 to the pool named PAT-POOL. Telnet from Sw1 to R1. If you have configured PAT correctly, this should work. The same applies for pings from Sw1 or the Fa0/0 interface of R2 to R1.
Task 9:
Check the NAT translation table on R2 using the show ip nat translations command.
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring DCE clocking and IP addressing, please refer to earlier labs.
Task 3:
For reference information on configuring and verifying VLANs and Telnet, please refer to earlier labs.
Task 4:
For reference information on configuring IP interfaces, please refer to earlier labs.
Task 5:
For reference information on configuring pinging, please refer to earlier labs.
Task 6:
R2#config t Enter configuration commands, one per line. End with CTRL/Z. R2(config)#ip access-list extended NAT-ACL R2(config-ext-nacl)#remark “NAT Traffic from 10.2.2.0/27 To 192.168.254.0/29” R2(config-ext-nacl)#permit ip 10.2.2.0 0.0.0.31 192.168.254.0 0.0.0.7 R2(config-ext-nacl)#^Z R2#
Task 7:
R2#conf t Enter configuration commands, one per line. End with CTRL/Z. R2(config)#int fa0/0 R2(config-if)#ip nat inside R2(config-if)#exit R2(config)#int s0/0 R2(config-if)#ip nat outside R2(config-if)#exit R2(config)#ip nat pool PAT-POOL 192.168.254.4 192.168.254.4 netmask 255.255.255.240 R2(config)#end R2#
Task 8:
R2#conf t Enter configuration commands, one per line. End with CTRL/Z. R2(config)#ip nat inside source list NAT-ACL pool PAT-POOL overload R2(config)#end R2#
NOTE: Again, do not forget to issue the overload keyword when configuring NAT overload/PAT.
Sw1#ping 192.168.254.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.254.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 8/8/12 ms Sw1#telnet 192.168.254.1 Trying 192.168.254.1 ... Open User Access Verification Password: R1#
Task 9:
R2#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 192.168.254.2:4813 10.2.2.4:4813 192.168.254.1:4813 192.168.254.1:4813
icmp 192.168.254.2:4814 10.2.2.4:4814 192.168.254.1:4814 192.168.254.1:4814
icmp 192.168.254.2:4815 10.2.2.4:4815 192.168.254.1:4815 192.168.254.1:4815
icmp 192.168.254.2:4816 10.2.2.4:4816 192.168.254.1:4816 192.168.254.1:4816
icmp 192.168.254.2:4817 10.2.2.4:4817 192.168.254.1:4817 192.168.254.1:4817
tcp 192.168.254.2:12801 10.2.2.4:12801 192.168.254.1:23 192.168.254.1:23
R2#
R2#show ip nat statistics
Total active translations: 6 (0 static, 6 dynamic; 6 extended)
Outside interfaces:
Serial0/0
Inside interfaces:
FastEthernet0/0
Hits: 250 Misses: 40
Expired translations: 32
Dynamic mappings:
-- Inside Source
[Id: 3] access-list 140 interface Serial0/0 refcount 6
[Id: 4] access-list NAT-ACL pool PAT-POOL refcount 0
pool PAT-POOL: netmask 255.255.255.248
start 192.168.254.4 end 192.168.254.4
type generic, total addresses 1, allocated 0 (0%), misses 0

/29 CIDR does not have a subnet mask of 255.255.255.240. Its 255.255.255.248.