Network Support and Security Final Exam Answers
1. Refer to the exhibit. A technician is attempting to map the local network using CDP. According to the output shown, which two statements are true about router Branch01? (Choose two.)
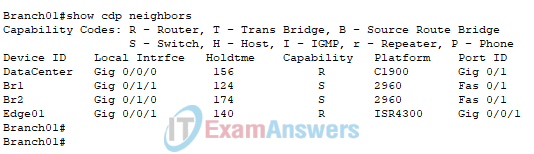
- Router Branch01 is directly connected to port Gi0/1/0 on device BR2.
- Router Branch01 is directly connected to three Cisco switches.
- Router Branch01 is directly connected to another router named DataCenter.
- Router Branch01 port Gi0/0/0 is directly connected to a Layer 2 switch.
- Router Branch01 is directly connected to port Fa0/1 on device BR1.
Explanation: The output of the show CDP neighbors command on Branch01 indicates that DataCenter is connected to the Gi0/0/0 port on router Branch01 and that the Fa0/1 port on switch BR1 is connected to the Gi0/1/1 port on router Branch01. Two Cisco switches are attached to router Branch01, as indicated by the two S capability codes in the Capability column. The Local Interface column displays the port on Branch01 connected to the device, and the PortID column indicates the port on the connected device.
2. A technician receives a trouble ticket from a user reporting that a website is no longer accessible. What two questions would the technician ask to narrow down the potential problem? (Choose two.)
- Could you access this web site previously from this device?
- What model computer are you using to access this site?
- What operating system is installed on your computer?
- Do you remember your password to this web site?
- Can you access other web sites from this computer browser?
Explanation: To narrow down the problem, the technician asks if the computer was previously able to access the website and if other websites are accessible. If the answer is yes to both questions, the technician has narrowed the issue to problems with the single website on this day.
3. Which type of cloud service is a user accessing when using Google Sheets to create a financial report?
Explanation: Google Sheets is an example of SaaS, or software as a service. The software that powers Google Sheet functionality is located on cloud servers managed by Google. PaaS is a platform and service used primarily by software developers to develop and test new applications. IaaS is an infrastructure service in which servers and other network devices, such as firewalls, are deployed in the cloud. FaaS functions as a service that provides dynamically allocated servers when a request is made for specific application services, such as providing a web service when a web page is requested.
4. What security benefit is provided by SSH?
- protection from threat actors deciphering remote access session data.
- protection from viruses and malware for endpoints.
- protection from malicious data reaching servers and clients.
- protection from DoS attacks against routers and Layer 3 switches.
Explanation: Internet Protocol Security (IPsec) protects sensitive data and secures VPNs. IPsec tunneling encrypts all data sent between tunnel endpoints. IPsec also can be used to authenticate data originating from an authorized sender.
5. A network administrator needs to segment the local area network to isolate traffic from different departments so that network permissions unique to each department can be implemented. Which network topology provides a solution to achieve the objective?
Explanation: Implementing VLANs on a local area network allows an administrator to segment and isolate traffic for administrative purposes. Ports on a switch can be grouped in VLANs, and traffic in each VLANs is kept separate from other VLANs by the switch. This allows the administrator to apply different network permissions to the isolated traffic on the VLANs.
6. Which output of a ping command can determine two important pieces of information? (Choose two.)
- the round-trip time for the request to reach the destination and the response to return
- the IP address of the gateway router that connects the source device to the internet
- the number of domains that the packet travels through from the source to the destination
- which network device is causing delays in delivering the packet to the destination IP address
- whether or not the destination IP address is reachable through the network
Explanation: A successful ping command confirms that the destination IP address is reachable through the network. The ping command output also displays the average round-trip time for the ping request to reach the destination and the ping response to return.
7. Which troubleshooting method involves swapping a device suspected of having issues with a known good device to see if the problem is solved?
- comparison
- substitution
- educated guess
- divide-and-conquer
Explanation: With the substitution troubleshooting method, a know suitable device is used to replace a suspected bad device. If this fixes the problem, then the problem was with the removed device. If the issue remains, the cause resides someplace else, and the troubleshooting continues.
8. What information can a technician obtain by running the tracert command on a Windows PC?
- the available routes in the PC routing table to reach a destination.
- the available bandwidth between the PC and a destination.
- the verification of Layer 2 connectivity between the PC and a destination.
- layer 3 hops a packet crosses as it travels to a destination.
Explanation: The tracert command in Windows can help a technician locate Layer 3 problems by returning a list of hops a packet takes as it is routed through a network. This helps verify Layer 3 connectivity and identify the point along the path where a problem can be found if there is no end-to-end connectivity.
9. What are the two characteristics of a site-to-site VPN? (Choose two.)
- The client initiates the VPN connection.
- Traffic between clients and the VPN gateway is automatically encrypted.
- A VPN gateway device is needed at both ends of the tunnel.
- The VPN is established between the client PC and a VPN gateway.
- Clients have no awareness of the VPN.
Explanation: A site-to-site VPN is created between two VPN gateways to establish a secure tunnel. The VPN traffic is only encrypted between the two gateway devices and not between the client and the gateway. The client host will have no knowledge that a VPN is being used.
10. What type of connection is used when a teleworker must have secure access to devices and services located on an enterprise network?
Explanation: A VPN connection between the teleworker and the enterprise provides a secure connection to the enterprise network. All communications between the entities are encrypted. HTTP and FTP are not secure protocols. RDP provides remote access to a single Windows computer.
11. The IT department of a high school is developing cybersecurity policies. One policy item regulates the blocking of obtaining movies and sounds through peer-to-peer networks on school computers. Which two user threats does this policy address? (Choose two.)
- data theft
- unauthorized downloads and media
- no awareness of security
- poorly enforced security policies
- unauthorized websites
Explanation: Network and device infections and attacks can be traced back to users who have downloaded unauthorized emails, photos, music, games, apps, or videos to their computers, networks, or storage devices. Most movies and music recordings downloaded from peer-to-peer networks are distributed illegally.
12. A penetration test carried out by an organization identified a backdoor on the network. What action should the organization take to find out if their systems have been compromised?
- Look for policy changes in Event Viewer.
- Look for unauthorized accounts.
- Scan the systems for viruses.
- Look for usernames that do not have passwords.
Explanation: If a penetration test is successful, the corporation should check to locate vulnerabilities in the network and also check to see if there are new unauthorized accounts.
13. What non-technical method could a cybercriminal use to gather sensitive information from an organization?
- ransomware
- pharming
- social engineering
- man-in-the-middle
Explanation: Social engineering is a very effective way to get personal or sensitive corpoate information from an employee. Cybercriminals may try to get to know an employee and then use trust or familiarity to gather the needed information.
14. What type of attack occurs when data goes beyond the memory areas allocated to an application?
- SQL injection
- RAM spoofing
- Buffer overflow
- RAM injection
Explanation: A buffer overflow occurs when data is written beyond the limits of a buffer. By changing data beyond the boundaries of a buffer, the application can access memory allocated to other processes. This can lead to a system crash or data compromise, or provide escalation of privileges.
15. Match the examples of cyber threat to the description.
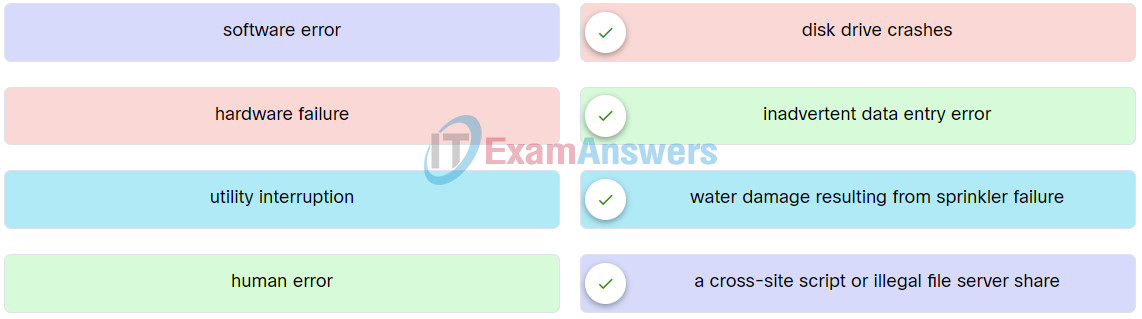
Network Support and Security Final Exam Q15
Explanation: Place the options in the following order:
| hardware failure |
disk drive crashes |
| human error |
inadvertent data entry error |
| utility interruption |
water damage resulting from sprinkler failure |
| software error |
a cross-site script or illegal file server share |
16. Employees in an organization report that they cannot access the customer database on the main server. Further investigation reveals that the database file is now encrypted. Shortly afterward, the organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- trojan horse
- ransomware
- DoS attack
- man-in-the-middle attack
Explanation: In a ransomware attack, the attacker compromises the victum computer and encrypts the hard drive so that data can no longer be accessed by the user. The attacker then demands payment from the user to decrypt the drive.
17. All employees in an organization receive an email stating that their account password will expire immediately and that they should reset their password within five minutes. Which of the following statements best describes this email?
- It is a DDoS attack.
- It is an impersonation attack.
- It is a hoax.
- It is a piggyback attack.
Explanation: A hoax is an act intended to deceive or trick someone. This type of email can cause unnecessary disruption, extra work, and fear.
18. Which statement describes an advanced persistent threat (APT)?
- an attack that modifies the operating system through malware and creates a backdoor on the infected system.
- an attack that takes advantage of algorithms in a piece of legitimate software to generate unintended behaviors.
- an attack by threat actors performing unauthorized network probing and port scanning on the targeted network.
- a continuous attack that uses elaborated espionage tactics involving multiple threat actors and sophisticated malware to gain access to the targeted network.
Explanation: An advanced persistent threat (APT) is a continuous attack that uses elaborate espionage tactics involving multiple actors and sophisticated malware to gain access to the targeted network.
19. Which attack takes control over a user’s mobile device and instructs the device to exfiltrate user-sensitive information and send it to threat actors?
- MitMo
- SMiShing
- Bluejacking
- Grayware
Explanation: Man-in-the-Mobile (MitMo) is a variation of a man-in-the-middle attack. It is used to take control over the mobile device of a user. When infected, the mobile device is instructed to exfiltrate user-sensitive information and send it to the attackers.
20. What do you call an impersonation attack that takes advantage of a trusted relationship between two systems?
- man-in-the-middle
- sniffing
- spoofing
- spamming
Explanation: In spoofing attacks, hackers can disguise their devices by using a valid address from the network and therefore bypass authentication processes. MAC addresses and IP addresses can be spoofed and can also be used to spoof ARP relationships.
21. Match the type of firewall to the description.
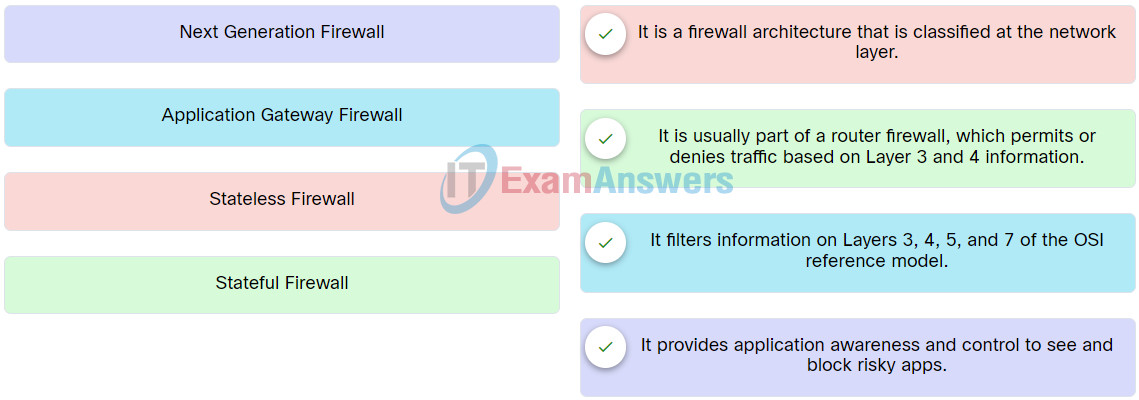
Network Support and Security Course Final Exam Q21
Explanation: Place the options in the following order:
| Stateless Firewall |
It is a firewall architecture that is classified at the network layer. |
| Stateful Firewall |
It is usually part of a router firewall, which permits or denies traffic based on Layer 3 and 4 information. |
| Application Gateway Firewall |
It filters information on Layers 3, 4, 5, and 7 of the OSI reference model. |
| Next Generation Firewall |
It provides application awareness and control to see and block risky apps. |
22. What is one of the safeguards according to the third dimension of the cybersecurity cube?
- accountability
- confidentiality
- integrity
- technology
Explanation: The third dimension of the cybersecurity cube defines the pillars on which we need to base our cybersecurity defenses to protect data and infrastructure in the digital realm. These are technology , policy, and practices , and improving people’s education, training, and awareness.
23. Refer to the exhibit. The image shows a firewall filtering network traffic based on information at highlighted OSI model Layers. Which type of firewall is represented?
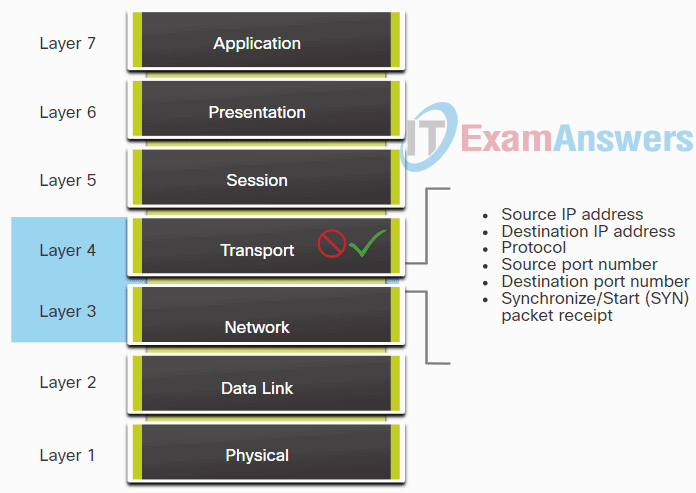
Network Support and Security Course Final Exam Q23
- Next Generation
- Application Gateway
- Stateful
- Packet filtering (stateless)
Explanation: Packet filtering firewalls are usually part of a router firewall, which permits or denies traffic based on Layer 3 and 4 information. Stateless firewalls use a simple policy table look-up that filters traffic based on specific criteria.
24. Match the authentication method to description.
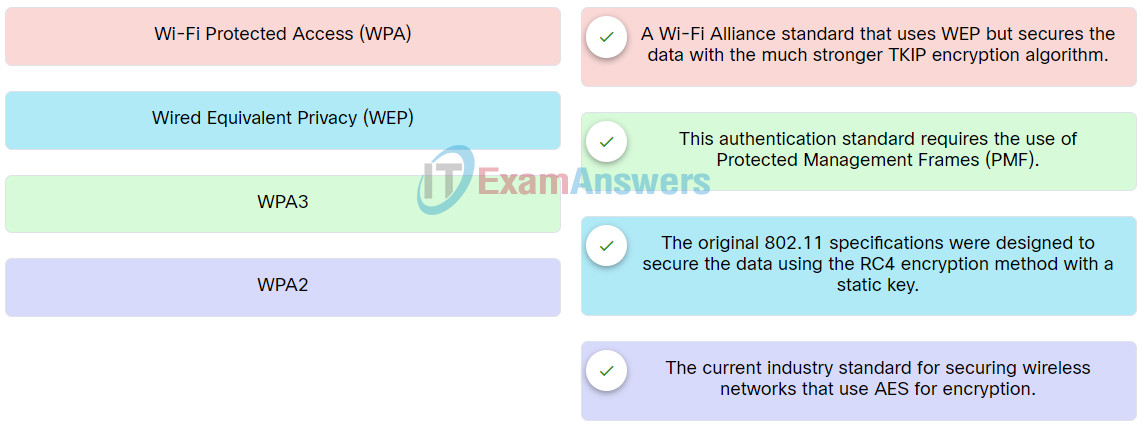
Network Support and Security Course Final Exam Q24
Explanation: Place the options in the following order:
| Wi-Fi Protected Access (WPA) |
A Wi-Fi Alliance standard that uses WEP but secures the data with the much stronger TKIP encryption algorithm. |
| WPA3 |
This authentication standard requires the use of Protected Management Frames (PMF). |
| Wired Equivalent Privacy (WEP) |
The original 802.11 specifications were designed to secure the data using the RC4 encryption method with a static key. |
| WPA2 |
The current industry standard for securing wireless networks that use AES for encryption. |
25. To which component of the CIA triad security information principle does tokenization apply?
- availability
- authorization
- confidentiality
- integrity
Explanation: To accomplish confidentiality without encryption, tokenization is a substitution technique that can isolate data elements from exposure to other data systems.
26. Which statement describes the principle of availability in the CIA information security triad?
- Cryptographic encryption algorithms such as AES may be required to encrypt and decrypt data.
- Data must be protected from unauthorized alteration.
- Only authorized individuals, entities, or processes can access sensitive information.
- Redundant services, gateways, and links must be implemented.
Explanation: According to the CIA information security triad, the principle of availability means that authorized users must have uninterrupted access to important resources and data. It requires implementing redundant services, gateways, and links.
27. Match the host-based security solution to the description.
Explanation: Place the options in the following order:
| Host-based firewall |
It runs on a device to restrict incoming and outcoming network activity for that device. It can allow or deny traffic between the device and the network. |
| Host intrusion detection system |
It is installed on a device or server to monitor suspicious activity. It can also monitor configuration information about the device held in the system registry. |
| Host intrusion prevention system |
It monitors a device for known attacks and anomalies (deviations in bandwidth, protocols, and ports) or finds red flags by assessing the protocols in packets. |
| Endpoint detection and response |
It is an integrated security solution that continuously monitors and collects data from an endpoint device. It then analyzes the data and responds to any threats it detects. |
| Data loss prevention |
The tools provide a centralized way to ensure that sensitive data is not lost, misused or accessed by unauthorized users. |
| Next-generation firewall |
It is a network security device that combines a traditional firewall with other network-device-filtering functions. |
28. Which Apple security feature ensures that only authentic, digitally-signed software that an Apple-notarized software developer has created is permitted to be installed?
- XProtect
- MRT
- Security-focused hardware
- Gatekeeper
Explanation: Gatekeeper, an Apple macOS security feature, ensures that only authentic, digitally-signed software that an Apple-notarized software developer has created can be installed.
29. Which is an example of a behavioral characteristic?
- voice
- ear features
- face
- DNA
Explanation: There are two types of biometric identifiers:
- Physical characteristics: fingerprints, DNA, face, hands, retina, or ear features.
- Behavioral characteristics: behavior patterns such as gestures, voice, gait, or typing rhythm.
30. What is the limitation of using a stateful firewall in a network?
- Less information is provided in the logs compared to a packet-filtering firewall.
- No defense against spoofing and DoS attacks.
- Weak packet filtering.
- Difficult to defend against dynamic port negotiation.
Explanation: The limitations of a stateful firewall are:
- No Application Layer inspection
- Limited tracking of stateless protocols
- Difficult to defend against dynamic port negotiation
- No authentication support
31. Which Windows utility would a technician use to discover which user was logged in to the system when a critical problem occurred?
- Event Viewer
- Device Manager
- Task Manager
- Users and Groups MMC
Explanation: When a critical issue arises, technicians can investigate the system using the Windows Event Viewer. Windows Event Viewer logs contain information about events affecting the system, including when a user logs into the system.
32. Which protocol is used by network management systems to collect data from network devices?
Explanation: Many network management systems use SNMP to collect data from networking devices. SMTP is used to send emails between email servers. RDP is the protocol used to access desktop computers remotely. TFTP is an insecure protocol used to transfer files between devices.
33. Which type of cyber threat would cause electrical power outages?
- human error
- hardware failure
- sabotage
- utility interruption
Explanation: Utility interruption is a cyber threat that can cause Electrical power outages and water damage resulting from sprinkler failure.
34. A secretary receives a phone call from someone claiming that their manager is about to give an important presentation but the presentation files are corrupted.
The caller sternly asks that the secretary email the presentation right away to a personal email address. The caller also states that the secretary is being held personally responsible for the success of this presentation.
What type of social engineering tactic is the caller using?
- intimidation
- familiarity
- urgency
- trusted partners
Explanation: Intimidation is a tactic that cybercriminals will often use to bully a victim into taking an action that compromises security.
35. The awareness and identification of vulnerabilities is a critical function of a cybersecurity specialist. Which of the following resources can they use to identify specific details about vulnerabilities?
- ISO/IEC 27000 model
- Infragard
- NIST/NICE framework
- CVE national database
Explanation: The United States Computer Emergency Readiness Team (US-CERT) and the U.S. Department of Homeland Security sponsor a dictionary of common vulnerabilities and exposures (CVE).
Each CVE entry contains a standard identifier number, a brief description of the security vulnerability and any important references to related vulnerability reports. The CVE list is maintained by a not-for-profit, the MITRE Corporation, on its public website.
36. Which three security services are part of the concept of administrative access controls?
- data in transit, data at rest, and data in process
- confidentiality, integrity, and availability
- technology, policy and practices, and people
- authentication, authorization, and accounting
Explanation: Administrative access controls involve three security services: authentication, authorization, and accounting (AAA).
37. What is the purpose of using the Windows BitLocker tool?
- to encrypt only memory
- to encrypt only temporary files
- to encrypt the entire hard drive
- to encrypt only folders
Explanation: Microsoft Windows uses BitLocker to encrypt a drive’s contents (including temporary files and memory).
38. Which cybersecurity solution should an organization implement to support employees who travel and use public Wi-Fi networks to access corporate information?
- site-to-site VPN
- remote access VPN
- intrusion detection application
- firewall
Explanation: There are several measures that organizations and users need to implement to defend against wireless and mobile device attacks, including:
- Take advantage of basic wireless security features such as authentication and encryption by changing the default configuration settings.
- Restrict access point placement by placing these devices outside the firewall or within a demilitarized zone — a perimeter network that protects an organization’s LAN from untrusted devices.
- Use WLAN tools such as NetStumbler to detect rogue access points or unauthorized workstations.
- Develop a policy for secure guest access to an organization’s Wi-Fi network.
- Employees in an organization should use a remote access VPN for WLAN access when on public Wi-Fi networks.
39. An administrator wishes to create a security policy document for end-users to protect against known unsafe websites and to warn the user about the dangers and handling of suspicious emails. What type of malware attack is being prevented?
- phishing
- DDoS
- adware protection
- trusted/untrusted sources verification
Explanation: Phishing is a type of malware attack where threat actors use unsafe websites and suspicious emails to entice users to give away personal information.





