1. What does a rootkit modify?
- operating system
- programs
- screen savers
- Notepad
- Microsoft Word
Explanation: A rootkit commonly modifies an operating system to create a backdoor to bypass normal authentication mechanisms.
2. An attacker is sitting in front of a store and wirelessly copies emails and contact lists from nearby unsuspecting user devices. What type of attack is this?
- bluesnarfing
- smishing
- RF jamming
- bluejacking
Explanation: Blusnarfing is the copying of user information through unauthorized Bluetooth transmissions.
3. What type of attack targets an SQL database using the input field of a user?
- XML injection
- Cross-site scripting
- SQL injection
- buffer overflow
Explanation: A criminal can insert a malicious SQL statement in an entry field on a website where the system does not filter the user input correctly.
4. What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization?
- man-in-the-middle
- ransomeware
- social engineering
- pharming
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
5. The employees in a company receive an email stating that the account password will expire immediately and requires a password reset within 5 minutes. Which statement would classify this email?
- It is a hoax.
- It is an impersonation attack.
- It is a piggy-back attack.
- It is a DDoS attack.
Explanation: Social engineering uses several different tactics to gain information from victims.
6. What three best practices can help defend against social engineering attacks? (Choose three.)
- Deploy well-designed firewall appliances.
- Educate employees regarding policies.
- Add more security guards.
- Do not provide password resets in a chat window.
- Enable a policy that states that the IT department should supply information over the phone only to managers.
- Resist the urge to click on enticing web links.
Explanation: A cybersecurity specialist must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities.
7. What is the term used when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source?
- phishing
- vishing
- backdoor
- Trojan
Explanation: Phishing is used by malicious parties who create fraudulent messages that attempt to trick a user into either sharing sensitive information or installing malware.
8. Users report that a database file on the main server cannot be accessed. A database administrator verifies the issue and notices that the database file is now encrypted. The organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- DoS attack
- man-in-the-middle attack
- ransomware
- Trojan horse
Explanation: In a ransomware attack, the attacker compromises the victum computer and encrypts the hard drive so that data can no longer be accessed by the user. The attacker then demands payment from the user to decrypt the drive.
9. A cyber criminal sends a series of maliciously formatted packets to the database server. The server cannot parse the packets and the event causes the server to crash. What is the type of attack the cyber criminal launches?
- packet Injection
- SQL injection
- DoS
- man-in-the-middle
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
10. Employees in an organization report that the network access is slow. Further investigation reveals that one employee downloaded a third-party scanning program for the printer. What type of malware may have been introduced?
- trojan horse
- spam
- worm
- phishing
Explanation: Worms are malicious code that replicates by independently exploiting vulnerabilities in networks. Worms usually slow down networks. Whereas a virus requires a host program to run, worms can run by themselves. Other than the initial infection, worms no longer require user participation. After a worm affects a host, it is able to spread very quickly over the network. Worms share similar patterns. They all have an enabling vulnerability, a way to propagate themselves, and they all contain a payload.
11. An organization adds an “external” tag to incoming emails from outside the domain to warn the internal users that such emails are from outside. Which deception method is used by a cyber attack to trick employees into believing that the organization sent a malicious email by removing the “external” tag?
- watering hole attack
- typosquatting
- prepending
- invoice scam
Explanation: In prepending deception method, attackers can remove the “external” email tag used by organizations to warn the recipient that an email has originated from an external source. This method tricks individuals into believing that the organization sent the malicious email.
12. Netbus belongs to which malware type?
- backdoor
- logic bomb
- keylogger
- grayware
Explanation: Netbus is a backdoor program used by cybercriminals to gain unauthorized access to a system by bypassing the standard authentication procedures. A logic bomb is a malicious program that waits for a trigger, such as a specified date or database entry, to set off the malicious code. Keyboard logging refers to recording or logging every key struck on a computer’s keyboard. Grayware is any unwanted application that behaves in an annoying or undesirable manner. It may not carry any recognizable malware, but it may still pose a risk to the user by tracking your location or delivering unwanted advertising.
13. By having narrow viewing angles, an ATM mitigates what kind of attacks?
- dumpster diving
- shoulder surfing
- quid pro quo
- identity fraud
Explanation: Shoulder surfing is a simple attack that involves observing or looking over a shoulder of a target to gain valuable information such as PINs, access codes, or credit card details. As a result, ATM screens are only visible at certain angles. These types of safeguards make shoulder surfing much more difficult.
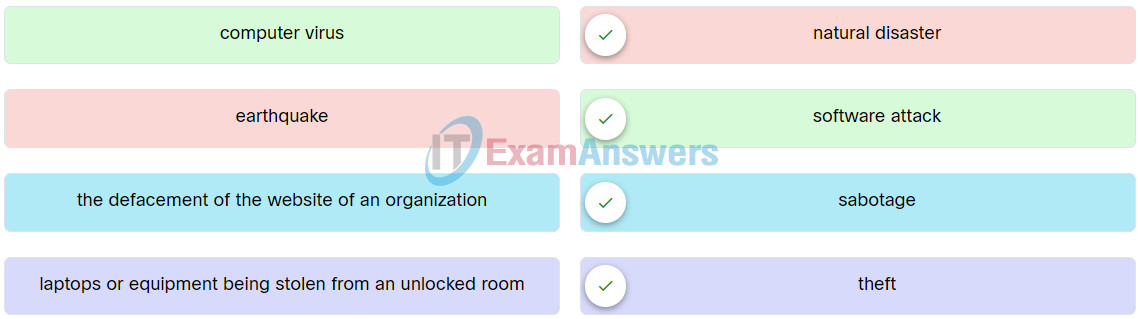
14. Match the examples of cyber threat to the description.
15. A user complains about frequently receiving messages on the smartphone that urges the user to visit different insurance websites. If the user clicks the link to visit, a user login message will pop up and ask the user to register first. Which wireless and mobile device attack has the user experienced?
- Grayware
- SMiShing
- Bluejacking
- Bluesnarfing
Explanation: Short message service phishing or SMiShing is a tactic used by attackers to trick mobile device users. Fake text messages prompt the user to visit a malicious website or call a fraudulent phone number, which may result in malware being downloaded onto the device or personal information being shared.

