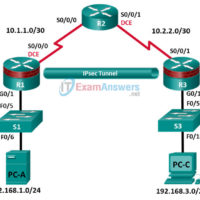
8.4.1.3 Lab – Configure Site-to-Site VPN using Cisco IOS (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. IP Addressing Table Device Interface IP Address Subnet …
7.5.1.2 Lab – Exploring Encryption Methods (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Decipher a Pre-Encrypted Message Using the Vigenère Cipher Use an encrypted message, a cipher key, and the Vigenère cipher square …
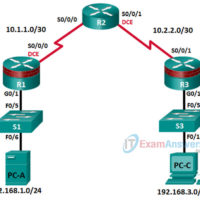
6.3.1.1 Lab – Securing Layer 2 Switches (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. IP Addressing Table Device Interface IP Address Subnet Mask Default …
5.4.1.1 Lab – Configure an Intrusion Prevention System (IPS) (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 …
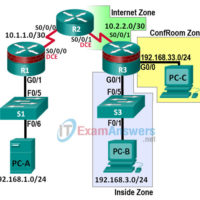
4.4.1.2 Lab – Configuring Zone-Based Policy Firewalls (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices have Fast Ethernet interfaces instead of Gigabit Ethernet Interfaces. NETLAB+ Note: PC-B is actually connected to port …
3.6.1.1 Lab – Securing Administrative Access Using AAA and RADIUS (Instructor Version) Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A …
2.6.1.2 Lab – Securing the Router for Administrative Access (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. IP Addressing Table Device Interface IP Address Subnet …
1.4.1.1 Lab – Researching Network Attacks and Security Audit Tools (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Researching Network Attacks Research network attacks that have occurred. Select a network attack and develop a …
1.2.4.12 Lab – Social Engineering (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objective In this lab, you will research examples of social engineering and identify ways to recognize and prevent it. Resources Computer with Internet Access …
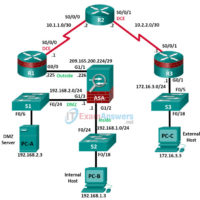
0.0.0.0 Lab – Instructor Lab Using ASA 5506-X (Instructor Version) Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0 209.165.200.225 255.255.255.248 N/A ASA G1/1 R1 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A …