1. What is the only attribute used by standard access control lists to identify traffic?
- source MAC address
- source IP address
- source TCP port
- protocol type
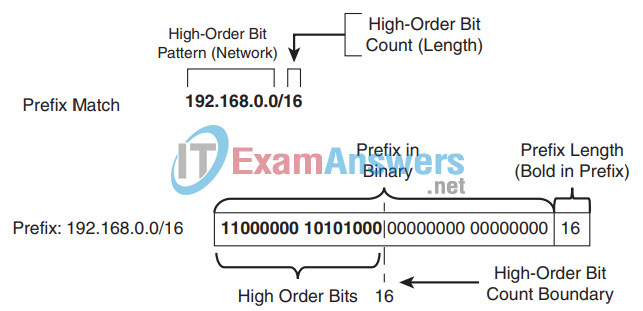
2. Which network prefix matches the prefix match pattern 10.0.0.0/8 ge 16 le 24?
- 10.42.0.0/18
- 10.16.0.0/12
- 10.123.77.128/25
- 10.0.0.0/32
3. What is the function of the continue keyword when applied to a sequence in a route map?
- It allows the route map to process the next sequence after a match is made.
- It allows the route map to process all sequences in the route map.
- It allows the route map to apply multiple match statements within a sequence.
- It allows the route map to apply multiple set actions within a sequence.
4. Which network and wildcard mask should be configured on an ACE entry to match any IP address?
- 0.0.0.0 0.0.0.0
- 0.0.0.0 255.255.255.255
- 255.255.255.255 255.255.255.255
- 255.255.255.255 0.0.0.0
5. What is the purpose of configuring local PBR?
- to modify the next-hop address on traffic sourced from a router
- to examine packets as they enter a router interface
- to place next-hop addresses in the routing table
- to forward packets to next-hop addresses that are not in the routing table
6. An administrator is configuring an extended ACL for BGP route selection. Which ACE command should the administrator issue to permit only 192.168.0.x networks with a /24 through /32 prefix length?
- permit ip 192.168.0.0 0.0.0.255 255.255.255.0 0.0.0.255
- permit ip 192.168.0.0 0.0.255.255 255.255.255.0 0.0.0.255
- permit ip 192.168.0.0 0.0.0.255 0.0.0.255 255.255.255.0
- permit ip 192.168.0.0 255.255.255.255 255.255.255.0 0.0.0.255
7. Which network prefix matches the prefix match pattern 2001:db8:cafe::/48 ge 48 le 56?
- 2001:db8:cafe:1001::/48
- 2001:db8:cafe:12::/64
- 2001:db8:feed::/52
- 2001:db8::/52
8. Which is a characteristic of standard ACLs?
- They match packets based on source IP address only.
- They use a numbered entry of 100-199 or 2000-2699.
- They match packets based on source or destination IP address.
- They can only be applied in the inbound direction on an interface.
9. What is the default auto-increment sequence number value of a prefix list if none is specified?
- 1
- 5
- 10
- 20
10. Which network prefix matches the prefix match pattern 10.0.0.0/10 ge 16?
- 10.1.5.0/16
- 10.1.0.0/8
- 10.128.0.0/32
- 10.64.0.0/24
11. Which two rules apply to route map statements? (Choose two.)
- Sequence numbers increment by 10 automatically if not provided.
- An implied all prefixes statement is applied if no matching statement is given.
- A default value of deny is used if there is no processing action defined.
- After a matching criterion, processing continues until all match criteria are checked.
- Boolean logic “and” is used if multiple variables are configured for a specific route map sequence.
12. What is the final step when configuring policy-based routing?
- Define access lists.
- Configure policy with the use of the
route-mapcommand. - Apply policy to an interface using
ip policy route-mapcommand. - Apply
matchcommands.
“Do I Know This Already?” Quiz Answers:
1. True or false: An extended ACL that is used to match routes changes behavior if the routing protocol is an IGP rather than BGP.
- True
- False
2. Which network prefixes match the prefix match pattern 10.168.0.0/13 ge 24? (Choose two.)
- 10.168.0.0/13
- 10.168.0.0/24
- 10.173.1.0/28
- 10.104.0.0/24
3. What happens when the route map route-map QUESTION deny 30 does not contain a conditional match statement?
- Any remaining routes are discarded.
- Any remaining routes are accepted.
- All routes are discarded.
- All routes are accepted.
4. What happens to a route that does not match the PrefixRFC1918 prefix list when using the following route map?
route-map QUESTION deny 10 match ip address prefix-list PrefixRFC1918 route-map QUESTION permit 20 set metric 200
- The route is allowed, and the metric is set to 200.
- The route is denied.
- The route is allowed.
- The route is allowed, and the default metric is set to 100.
5. True or false: When there are multiple conditional matches of the same type, only one must be met for the prefix to match.
- True
- False
6. True or false: Policy-based routing will modify a router’s routing table.
- True
- False