14. What is a function of the GRE protocol?
- to configure the set of encryption and hashing algorithms that will be used to transform the data sent through the IPsec tunnel
- to encapsulate multiple OSI Layer 3 protocol packet types inside an IP tunnel
- to configure the IPsec tunnel lifetime
- to provide encryption through the IPsec tunnel
Explanation: The transform set is the set of encryption and hashing algorithms that will be used to transform the data sent through the IPsec tunnel. GRE supports multiprotocol tunneling. It can encapsulate multiple OSI Layer 3 protocol packet types inside an IP tunnel. Routing protocols that are used across the tunnel enable dynamic exchange of routing information in the virtual network. GRE does not provide encryption.
15. Refer to the exhibit. A tunnel was implemented between routers R1 and R2. Which two conclusions can be drawn from the R1 command output? (Choose two.)
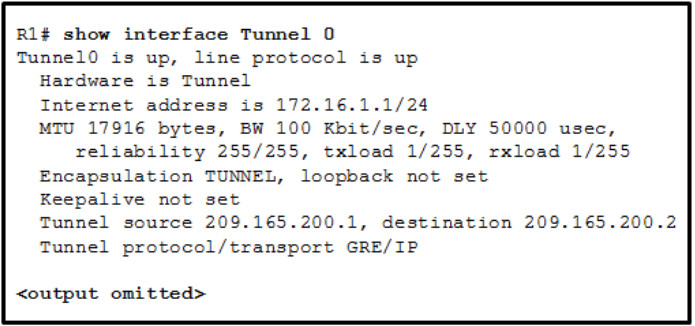
- This tunnel mode is not the default tunnel interface mode for Cisco IOS software.
- This tunnel mode provides encryption.
- The data that is sent across this tunnel is not secure.
- This tunnel mode does not support IP multicast tunneling.
- A GRE tunnel is being used.
Explanation: According to the R1 output, a GRE tunnel mode was specified as the tunnel interface mode. GRE is the default tunnel interface mode for Cisco IOS software. GRE does not provide encryption or any other security mechanisms. Therefore, data that is sent across a GRE tunnel is not secure. GRE supports IP multicast tunneling.
16. For a VPN, which technology provides secure remote access over broadband?
Explanation: The IPsec (IP Security) applies security at the network layer of the OSI model and is used to secure VPN communication.
17. What is the purpose of LISP?
- It authenticates vSmart controllers and SDWAN routers.
- It is an architecture created to address routing scalability problems.
- It provides a permanent control plane connection over a DTLS tunnel.
- It performs load balancing of SD-WAN routers across vSmart controllers.
Explanation: Locator/Identifier Separation Protocol (LISP) is used by Internet providers, data centers, branch networks, and campus networks to address routing scalability problems and provide an overlay tunneling technology.
18. Which two protocols must be allowed for an IPsec VPN tunnel is operate properly? (Choose two.)
Explanation: ESP uses protocol 50. AH uses protocol 51. ISAKMP uses UDP port 500.
19. What is the purpose of a VXLAN?
- It provides site-to-site VPNs between cloud providers.
- It is an architecture created to address routing scalability problems.
- It provides Layer 2 and Layer 3 overlay networks across a Layer 3 underlay network.
- It encapsulates a variety of network layer protocols inside virtual point-to-point links.
Explanation: A virtual extensible local-area network (VXLAN) helps when virtualization is used and with Layer 2 problems that have arisen as a result. VXLAN extends Layer 2 and Layer 3 overlay networks over a Layer 3 underlay network using MAC-in IP/UDP tunneling.
20. What are the two peer authentication methods used by IPsec? (Choose two.)
- PSK
- GRE
- HMAC
- MD5
- RSA signatures
Explanation: IPsec can use pre-shared keys (PSK) and RSA signatures for peer authentication. GRE (Generic Routing Encapsulation) is a mechanism to implement a VPN. HMAC and MD5 relate to hashing algorithms not authentication processes.
21. When GRE is configured on a router, what do the tunnel source and tunnel destination addresses on the tunnel interface refer to?
- the IP addresses of the two LANs that are being connected together by the VPN
- the IP address of host on the LAN that is being extended virtually
- the IP addresses at each end of the WAN link between the routers
- the IP addresses of tunnel interfaces on intermediate routers between the connected routers
vA site-to-site VPN is established with a GRE tunnel. It does not link two LANs, but rather it extends the reach of a single LAN across a WAN. Tunnel interfaces are configured on routers at each end of the VPN, not in the intermediate routers.[/alert-success]
22. How does LISP resolve an EID into an RLOC?
- by using DNS
- by sending a map request to the MR
- by tunneling data from the interior routing protocol
- by encapsulating the EID packet and adding an outer header with the RLOC IP address
Explanation: The map resolver (MR) is a device such as a router that consults with the map server (MS) to locate and communicate with the proper tunnel router. This router then sends a map reply message to the originating router that includes the endpoint identifier (EID) to routing locator (RLOC) mapping.
23. Which algorithm is an asymmetrical key cryptosystem?
Explanation: RSA is a cryptosystem for asymmetrical keys. AES, DES, and 3DES are all symmetric key cryptosystems.
24. Which remote access implementation scenario will support the use of generic routing encapsulation tunneling?
- a mobile user who connects to a router at a central site
- a branch office that connects securely to a central site
- a mobile user who connects to a SOHO site
- a central site that connects to a SOHO site without encryption
Explanation: The GRE tunneling protocol is used for site-to-site VPNs, not for remote access VPNs for mobile users. GRE alone does not provide any encryption, so the traffic is not secure between the endpoints.
25. Which UDP port number is assigned to VXLAN by IANA?
Explanation: Linux servers use UDP port number 8472 for VXVLAN by default, but the IANA-issued port number is 4789. Port 4341 and 4342 are used with LISP.
“Do I Know This Already?” Quiz Answers:
1. Which of the following commands are optional for GRE configuration? (Choose two.)
- tunnel source {ip-address | interface-id}
- tunnel destination ip-address
- tunnel mode gre {ip | ipv6}
- keepalive
Explanation: When configuring a tunnel interface, the default mode is GRE, so there is no need to specify the tunnel mode with the command tunnel mode gre {ip | ipv6}. The command is useful when the tunnel mode is changed to another type (such as IPsec) and there is a need to change the tunnel mode back to GRE.
The keepalive command is also optional. It is used to make sure the other end of the tunnel is operational. This command does not need to be configured on both ends of the tunnel in order to work.
2. True or false: GRE was originally created to provide transport for non-routable legacy protocols.
Explanation: GRE was originally created to provide transport for non-routable legacy protocols such as Internetwork Packet Exchange (IPX) across an IP network, and it is now more commonly used as an overlay for IPv4 and IPv6.
3. Which of the following should not be dynamically advertised via an IGP into a GRE tunnel?
- Loopback interfaces
- The GRE tunnel source interface or source IP address
- Connected interfaces
- The GRE tunnel IP address
Explanation: The tunnel source interface or source IP address should not be advertised into a GRE tunnel because it would cause recursive routing issues.
4. Which of the following are modes of packet transport supported by IPsec? (Choose two.)
- Tunnel mode
- Transparent mode
- Transport mode
- Crypto mode
Explanation: Traditional IPsec provides two modes of packet transport: tunnel mode and transport mode.
5. Which of the following are encryption protocols that should be avoided? (Choose two.)
Explanation: DES and 3DES are weak encryption protocols that are no longer recommended for use.
6. Which of the following is the message exchange mode used to establish an IKEv1 IPsec SA?
- Main mode
- Aggressive mode
- Quick mode
- CREATE_CHILD_SA
Explanation: The message exchange method used to establish an IPsec SA for IKEv1 is known as quick mode. Main mode and aggressive mode are IKEv1 methods used to establish IKE SAs. For IKEv2, IKE_Auth creates an IPsec SA. If additional IPsec SAs are needed, a CREATE_CHILD_SA exchange is used to establish them.
7. LISP separates IP addresses into which of the following? (Choose two.)
- RLOCs
- LISP entities
- Subnets and hosts
- EIDs
Explanation: LISP separates IP addresses into endpoint identifiers (EIDs) and routing locators (RLOCs).
8. What is the destination UDP port used by the LISP data plane?
Explanation: The destination UDP port used by the LISP data plane is 4341. UDP port 4342 is used for LISP’s control plane messages.
9. True or false: ETRs are the only devices responsible for responding to map requests originated by ITRs.
Explanation: An ETR may also request that the MS answer map requests on its behalf by setting the proxy map reply flag (P-bit) in the map register message.
10. Which of the following UDP ports is the UDP port officially assigned by the IANA for VXLAN?
Explanation: The IANA’s assigned VXLAN UDP destination port is 4789, while for Linux it is port 8472. The reason for this discrepancy is that when VXLAN was first implemented in Linux, the VXLAN UDP destination port had not yet been officially assigned, and Linux decided to use port 8472 because many vendors at the time were using that value.
11. True or false: The VXLAN specification defines a data plane and a control plane for VXLAN.
Explanation: The VXLAN specification defines VXLAN as a data plane protocol, but it does not define a VXLAN control plane, which was left open to be used with any control plane.

