Lab Objective:
The objective of this lab exercise is for you to learn and understand how to create and apply extended named access control lists.
Lab Purpose:
Configuring and applying extended ACLs is a fundamental skill. Extended ACLs filter based on source and destination address, as well as Layer 4 protocols TCP and UDP. Extended ACLs should be applied as close to the source as possible. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to create and apply extended named ACLs.
Certification Level:
This lab is suitable for CCENT and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 8/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 20 minutes.
Lab Topology:
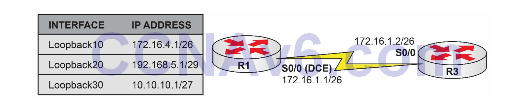
Please use the following topology to complete this lab exercise:
Task 1:
Configure the hostnames on routers R1 and R3 as illustrated in the topology.
Task 2:
Configure R1 S0/0, which is a DCE, to provide a clock rate of 768 Kbps to R3. Configure the IP addresses on the Serial interfaces of R1 and R3 as illustrated in the topology. Configure the Loopback interfaces on R1.
Task 3:
Configure RIPv2 on R1 and R3 for Serial0/0 on both routers and the 172.16.4.0/26 Loopback10 on R1. Configure EIGRP using AS 10 on R1 and R3 for Serial0/0 on both routers and the 192.168.5.0/29 Loopback20 on R1. Configure OSPF using process 10 and area 0 on R1 and R3 Serial0/0 on both routers and the 10.10.10.0/27 Loopback30 on R1. I know we haven’t covered these yet but just copy my commands as we need to test the ACL.
Task 4:
Verify your configuration using the show ip route command on R3 to ensure that all three routes are seen via the different configured routing protocols. To test connectivity, ping the three Loopback interfaces on R1 from R3. These should all be reachable.
Task 5:
Configure a named extended ACL on R3 called ROUTING-ACL. This ACL should deny RIPv2, allow EIGRP, deny OSPF, and allow all other IP traffic. Apply this ACL inbound on R3 Serial0/0.
Task 6:
Issue the clear ip route * command followed by the show ip route command on R3 and look at the routing table again. If you have configured this ACL correctly, you should only have the EIGRP route in the routing table.
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
R1#conf t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#int s0/0 R1(config-if)#no shutdown R1(config-if)#clock rate 768000 R1(config-if)#ip add 172.16.1.1 255.255.255.192 R1(config-if)#exit R1(config)#int lo10 R1(config-if)#ip address 172.16.4.1 255.255.255.192 R1(config-if)#exit R1(config)#int lo20 R1(config-if)#ip address 192.168.5.1 255.255.255.248 R1(config-if)#exit R1(config)#int lo30 R1(config-if)#ip address 10.10.10.1 255.255.255.224 R1(config-if)#exit R1# R3#config term Enter configuration commands, one per line. End with CTRL/Z. R3(config)#int s0/0 R3(config-if)#ip address 172.16.1.2 255.255.255.192 R3(config-if)#no shut R3(config-if)#end R3#
Task 3:
R1#conf t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#router rip R1(config-router)#version 2 R1(config-router)#network 172.16.1.0 R1(config-router)#network 172.16.4.0 R1(config-router)#no auto-summary R1(config-router)#exit R1(config)#router eigrp 10 R1(config-router)#network 172.16.1.0 0.0.0.63 R1(config-router)#network 192.168.5.0 R1(config-router)#no auto-summary R1(config-router)#exit R1(config)#router ospf 10 R1(config-router)#network 172.16.1.0 0.0.0.63 area 0 R1(config-router)#network 10.10.10.0 0.0.0.31 area 0 R1(config-router)#end R1# R3#conf t Enter configuration commands, one per line. End with CTRL/Z. R3(config)#router rip R3(config-router)#ver 2 R3(config-router)#net 172.16.1.0 R3(config-router)#no auto-sum R3(config-router)#exit R3(config)#router eigrp 10 R3(config-router)#network 172.16.1.0 R3(config-router)#no auto-summary *Mar 1 03:18:45.296: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 10: Neighbor 172.16.1.1 (Serial0/0) is up: new adjacency R3(config)#router ospf 10 R3(config-router)#network 172.16.1.0 0.0.0.63 area 0 R3(config-router)#end *Mar 1 03:19:08.550: %OSPF-5-ADJCHG: Process 10, Nbr 192.168.5.1 on Serial0/0 from LOADING to FULL, Loading Done
Task 4:
R3#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B – BGP,
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area,
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2,
E1 - OSPF external type 1, E2 - OSPF external type 2,
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1,
L2 - IS-IS level-2, ia - IS-IS inter area,
* - candidate default, U - per-user static route, o - ODR,
P - periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/26 is subnetted, 2 subnets
R 172.16.4.0 [120/1] via 172.16.1.1, 00:00:06, Serial0/0
C 172.16.1.0 is directly connected, Serial0/0
192.168.5.0/29 is subnetted, 1 subnets
D 192.168.5.0 [90/2297856] via 172.16.1.1, 00:03:16, Serial0/0
10.0.0.0/32 is subnetted, 1 subnets
O 10.10.10.1 [110/65] via 172.16.1.1, 00:07:53, Serial0/0
R3#ping 172.16.4.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.4.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/16 ms
R3#ping 192.168.5.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.5.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
R3#ping 10.10.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
Task 5:
R3#conf t Enter configuration commands, one per line. End with CTRL/Z. R3(config)#ip access-list extended ROUTING-ACL R3(config-ext-nacl)#remark “Deny RIP (UDP Port 520)” R3(config-ext-nacl)#deny udp any any eq 520 R3(config-ext-nacl)#remark “Permit EIGRP (IP Protocol 88)” R3(config-ext-nacl)#permit 88 any any R3(config-ext-nacl)#remark “Deny OSPF (IP Protocol 89)” R3(config-ext-nacl)#deny 89 any any R3(config-ext-nacl)#remark “Permit All Other IP Traffic” R3(config-ext-nacl)#permit ip any any R3(config-ext-nacl)#exit R3(config)#int s0/0 R3(config-if)#ip access-group ROUTING-ACL in R3(config-if)#^Z R3#
NOTE: Notice that I used the IP protocol numbers 88 and 89 for EIGRP and OSPF, respectively, instead of the keywords eigrp and ospf. Even though I did so, Cisco IOS converted these to their common names, which is what you will see when you issue the show access-lists command.
Task 6:
R3#clear ip route *
R3#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B – BGP,
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area,
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2,
E1 - OSPF external type 1, E2 - OSPF external type 2,
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1,
L2 - IS-IS level-2, ia - IS-IS inter area,
* - candidate default, U - per-user static route, o - ODR,
P - periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/26 is subnetted, 1 subnets
C 172.16.1.0 is directly connected, Serial0/0
192.168.5.0/29 is subnetted, 1 subnets
D 192.168.5.0 [90/2297856] via 172.16.1.1, 00:00:03, Serial0/0
NOTE: You may be wondering why the OSPF neighbor did not immediately go down when you applied the ACL inbound. This is because the adjacency is only removed when the OSPF dead timer expires. Therefore, after a few seconds, you should see the following message on your console:
*Mar 1 03:34:01.683: %OSPF-5-ADJCHG: Process 10, Nbr 192.168.5.1 on Serial0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
The reason we need to issue the clear ip route * command is because RIP routes only get removed from the routing tables after the timers expire. This will be a few minutes. Therefore, if you ever see a RIP route that is older than 30 seconds, RIP holddown timers have kicked in, as illustrated in the following output:
R3#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B – BGP,
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area,
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2,
E1 - OSPF external type 1, E2 - OSPF external type 2,
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1,
L2 - IS-IS level-2, ia - IS-IS inter area,
* - candidate default, U - per-user static route, o - ODR,
P - periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/26 is subnetted, 2 subnets
R 172.16.4.0 [120/1] via 172.16.1.1, 00:03:05, Serial0/0
Based on the configuration tasks, we know that the ACL is working because we can ping R3 from R1 and the ACL on R3 shows matches for configured rules, as follows:
R1#ping 172.16.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms R3#show ip access-lists ROUTING-ACL Extended IP access list ROUTING-ACL 10 deny udp any any eq rip (80 matches) 20 permit eigrp any any (453 matches) 30 deny ospf any any (135 matches) 40 permit ip any any (15 matches)
