Lab Objective:
The objective of this lab exercise is to configure basic switch security to prevent MAC address flooding on switchports. This is accomplished by limiting the number of MAC entries that are allowed to be learned on a port. By default, there is no limit on MAC addresses that can be learned on a port.
Lab Purpose:
Port security is a fundamental skill. A common Denial of Service technique used to cripple switched networks is MAC flooding. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to configure port security to mitigate MAC flooding attacks.
Certification Level:
This lab is suitable for CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 8/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 15 minutes.
Lab Topology:
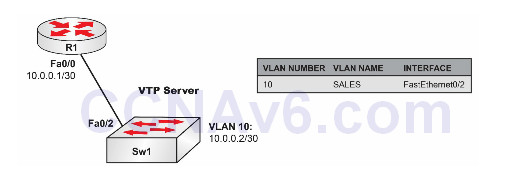
Please use the following topology to complete this lab exercise:
Task 1:
Configure hostnames on Sw1 and R1 as illustrated in the topology.
Task 2:
Create VLAN10 on Sw1 and assign port FastEthernet0/2 to this VLAN as an access port.
Task 3:
Configure IP address 10.0.0.1/30 on R1’s FastEthernet0/0 interface and IP address 10.0.0.2/30 on Sw2’s VLAN10 interface. Verify that R1 can ping Sw1, and vice versa.
Task 4:
Configure port security on port FastEthernet0/2 on Sw1 so that only one MAC address is allowed to be learned on that interface. In the event of port security configuration violations, where more than one MAC address is observed on that interface, the switch should shut the interface down. Verify your configuration with port-security commands in Cisco IOS.
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring VLANs, please refer to earlier labs. The port can’t be dynamic if you intend to add port security. It must be manually set to trunk or access.
Task 3:
For reference information on configuring router IP interfaces, please refer to earlier labs.
Sw1(config)#int vlan10 %LINK-5-CHANGED: Interface Vlan10, changed state to up Sw1(config-if)#ip add 10.0.0.2 255.255.255.252 Sw1(config-if)#no shut Sw1(config-if)#end Sw1#ping 10.0.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
Task 4:
Sw1#conf t Enter configuration commands, one per line. End with CTRL/Z. Sw1(config)#interface fastethernet 0/2 Sw1(config-if)#switchport port-security Sw1(config-if)#switchport port-security maximum 1 Sw1(config-if)#switchport port-security violation shutdown Sw1(config-if)#end Sw1#show port-security Secure Port MaxSecureAddr CurrentAddr SecurityViolation Sec Action (Count) (Count) (Count) ---------------------------------------------------------------------- Fa0/2 1 0 0 Shutdown ---------------------------------------------------------------------- Total Addresses in System : 0 Max Addresses limit in System : 1024 [Output Truncated]
NOTE: If you wanted to test your port security configuration, you could simply change the MAC address of FastEthernet0/0 on R1 to 000a.bc01.2300, and then you would see a port security violation. For example:
R1#conf t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#interface fastethernet0/0 R1(config-if)#mac-address 000a.bc01.2300 R1(config)#end R1# Sw1#show port-security Secure Port MaxSecureAddr CurrentAddr SecurityViolation Sec Action (Count) (Count) (Count) ---------------------------------------------------------------------- Fa0/2 1 0 1 Shutdown ---------------------------------------------------------------------- Total Addresses in System : 0 Max Addresses limit in System : 1024 Sw1#show interfaces fastethernet 0/2 FastEthernet0/2 is down, line protocol is down (errdisabled)
As can be seen in the output above, the violation counter has incremented and the interface is now in an errdisabled mode, which basically means it has been shut down due to a port security violation. To bring this interface back up, you need to issue a shutdown command and then a no shutdown command under the interface.
