Lab Objective:
The objective of this lab exercise is for you to learn how to configure 802.1x in your switch infrastructure.
Lab Purpose:
Understanding how to enable and configure 802.1x in your switch infrastructure is a core security topic when you think about security in Layer 2 of your network. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to configure 802.1x.
Certification Level:
This lab is suitable for ICND2 and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 6/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 10 minutes.
Lab Topology:
Please use the following topology to complete this lab exercise. This lab will not work on Packet Tracer, so you will need a live switch that supports 802.1x:
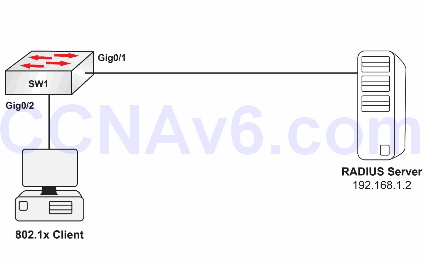
Note: We will only focus on the switch side of the configuration (the server and clients are already configured).
Task 1:
Configure the hostnames on Switch1 as illustrated in the topology.
Task 2:
Enable AAA authentication on Sw1 and configure the RADIUS server using 1812 and 1813 for authentication and accounting, respectively (use CCNA as the key between the server and the switch).
Task 3:
Configure AAA authentication for 802.1x using the RADIUS server already defined (use default as the authentication method list).
Task 4:
Enable 8021.x globally, and then make sure that the Gigabit0/2 interface runs EAPoL (802.1x).
Task 5:
Make sure that the configuration is up and working by running the command below after a user connects to the Gigabit0/2 port on Sw1.
show dot1x interface gig0/2
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
SW1(config)#aaa new-model SW1(config)#radius-server host 192.168.1.2 auth-port 1812 acct-port 1813 key CCNA SW1(config)#exit
Task 3:
SW1(config)#aaa authentication dot1x default group radius
Task 4:
SW1(config)#dot1x system-auth-control SW1(config)#interface gig0/2 SW1(config-if)#switchport mode access SW1(config-if)#dot1x port-control auto
Task 5:
SW1#show dot1x interface gig0/2 Dot1x Info for GigabitEthernet0/2 --------------------------------- PAE = AUTHENTICATOR PortControl = AUTO ControlDirection = In HostMode = SINGLE HOST ReAuthentication = Disabled QuietPeriod = 60 ServerTimeout = 30 SuppTimeout = 30 ReAuthPeriod = 3600 (Locally configured) ReAuthMax = 2 MaxReq = 2 TxPeriod = 30 RateLimitPeriod = 0
Your output may differ from mine slightly.
