Lab Objective:
The objective of this lab exercise is for you to learn how to configure IPv6 access filters in your network.
Lab Purpose:
At this point, you should already be aware of how access control lists work in an IPv4 environment, but in this lab, we are going to show you how to do the same for IPv6. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to implement IPv6 traffic filters in your network.
Certification Level:
This lab is suitable for ICND2 and CCNA certification exam preparation.
Lab Difficulty:
This lab has a difficulty rating of 7/10.
Readiness Assessment:
When you are ready for your certification exam, you should complete this lab in no more than 20 minutes.
Lab Topology:
Please use the following topology to complete this lab exercise:
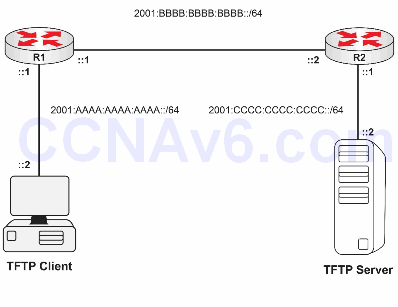
Interfaces’ IP assignment:
R1 Gig0/0 = 2001:BBBB:BBBB:BBBB::1/64 R1 Gig0/1 = 2001:AAAA:AAAA:AAAA::1/64 R2 Gig0/0 = 2001:BBBB:BBBB:BBBB::2/64 R2 Gig0/1 = 2001:CCCC:CCCC:CCCC::1/64
Or use FastEthernet interfaces if you wish.
Task 1:
Configure hostnames on R1 and R2 as illustrated in the topology.
Task 2:
Configure each router with its respective IPv6 addresses in both of their Gigabit interfaces.
Task 3:
Configure on each IPv6 router an IPv6 route to the non-directly connected networks.
Task 4:
Configure R2 with a traffic filter named Inbound_ACL ,allowing only TFTP traffic from the TFTP client to the TFTP server. Make sure you apply this ACL to Gig0/0 on R2.
Testing the ACL can be a little tricky but there is a traffic generator in Packet Tracer, or you can try to telnet to the remote TFTP server using the following router command:
R1#telnet 2001:cccc:cccc:cccc::2 69
Configuration and Verification
Task 1:
For reference information on configuring hostnames, please refer to earlier labs.
Task 2:
For reference information on configuring IP addressing, please refer to earlier labs.
Task 3:
R1(config)#ipv6 route 2001:CCCC:CCCC:CCCC::/64 2001:BBBB:BBBB:BBBB::2 R2(config)#ipv6 route 2001:AAAA:AAAA:AAAA::/64 2001:BBBB:BBBB:BBBB::1
Task 4:
R2(config)#ipv6 access-list Inbound_ACL R2(config-ipv6-acl)#permit udp 2001:AAAA:AAAA:AAAA::2/64 2001:CCCC:CCCC:CCCC::2/64 eq tftp R2(config)#int gig 0/0 R1(config-if)#ipv6 traffic-filter Inbound_ACL in
Testing this ACL can be a bit tricky. In Packet Tracer, you can use a traffic generator on the PC to send TFTP traffic, which will be allowed, and then ping (for example) to see if it’s blocked. On live equipment, you can copy tftp from a router acting as a host to the remote device. You can specify a port to telnet on and a source interface, but I haven’t tested this yet with a sniffer to see what is actually sent. Try it for yourself:
R1#telnet 2001:CCCC:CCCC:CCCC::2 69 /source-interface loopback0
