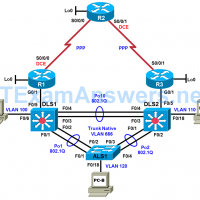
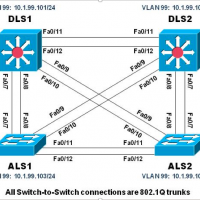
Physical Topology Logical Topology Objectives Load the trouble ticket device configuration files for each trouble ticket. Diagnose and resolve problems related to switch virtual interfaces and multilayer switching. Diagnose and resolve problems related to First Hop Redundancy Protocols. Document troubleshooting progress, configuration changes, and problem resolution. Background Multilayer …
1. Which statement describes an operational characteristic of NetFlow? NetFlow collects metadata about the packet flow, not the flow data itself. 2. What is the purpose of Tor? to allow users to browse the Internet anonymously 3. Threat actors may attack the infrastructure in order to corrupt …
1. If an asymmetric algorithm uses a public key to encrypt data, what is used to decrypt it? a private key 2. Which IETF standard defines the PKI digital certificate format? X.509 3. Which statement describes the use of hashing? Hashing can be used to detect accidental changes, …
1. Which monitoring technology mirrors traffic flowing through a switch to an analysis device connected to another switch port? NetFlow SNMP SIEM SPAN 2. Which network technology uses a passive splitting device that forwards all traffic, including Layer 1 errors, to an analysis device? NetFlow network tap SNMP …
1. Which network service synchronizes the time across all devices on the network? NTP SNMP NetFlow syslog 2. Fill in the blank. The distribution layer of the three-layer network design model aggregates data from the access layer. 3. Which network service allows administrators to monitor and manage network …
1. Fill in the blank. A Linux administrator will use either the CLI or the GUI when communicating with the operating system. 2. What is the outcome when a Linux administrator enters the man man command? The man man command configures the network interface with a manual address …
1. After a security incident is verified in a SOC, an incident responder reviews the incident but cannot identify the source of the incident and form an effective mitigation procedure. To whom should the incident ticket be escalated? a SME for further investigation a cyberoperations analyst for help …
1. Which NIST-defined incident response stakeholder is responsible for coordinating incident response with other stakeholders and minimizing the damage of an incident? human resources IT support the legal department management 2. What is defined in the policy element of the NIST incident response plan? how to handle incidents …