7.1.10 Lab – View ARP Traffic in Wireshark
Objectives
Part 1: Capture and Analyze ARP Data in Wireshark
- Start and stop data capture of ping traffic to remote hosts.
- Locate the IPv4 and MAC address information in captured PDUs.
- Analyze the content of the ARP messages exchanged between devices on the LAN.
Part 2: View the ARP cache entries on the PC
- Access the Windows Command Prompt.
- Use the Windows arp command to view the local ARP table cache on the PC.
Background / Scenario
Address Resolution Protocol (ARP) is used by TCP/IP to map a Layer 3 IPv4 address to a Layer 2 MAC address. When an Ethernet frame is transmitted on the network, it must have a destination MAC address. To dynamically discover the MAC address of a known destination, the source device broadcasts an ARP request on the local network. The device that is configured with the destination IPv4 address responds to the request with an ARP reply and the MAC address is recorded in the ARP cache.
Every device on the LAN maintains its own ARP cache. The ARP cache is a small area in RAM that holds the ARP responses. Viewing an ARP cache on a PC displays the IPv4 address and the MAC address of each device on the LAN with which the PC has exchanged ARP messages.
Wireshark is a software protocol analyzer, or “packet sniffer” application, used for network troubleshooting, analysis, software and protocol development, and education. As data streams travel back and forth over the network, the sniffer “captures” each protocol data unit (PDU) and can decode and analyze its content according to the appropriate protocol specifications.
Wireshark is a useful tool for anyone working with networks and can be used with most labs in the Cisco courses for data analysis and troubleshooting. This lab provides instructions for downloading and installing Wireshark, although it may already be installed. In this lab, you will use Wireshark to capture ARP exchanges on the local network.
Required Resources
- 1 PC (Choice of operating system with Wireshark installed)
- Additional PC(s) or mobile devices on a local-area network (LAN) can be used to reply to ping requests. If no additional devices are on the LAN, the default gateway address can be used to reply to the ping requests.
Instructions
Part 1: Capture and Analyze Local ARP Data in Wireshark
In this part, you will ping another PC on the LAN and capture ARP requests and replies in Wireshark. You will also look inside the frames captured for specific information. This analysis should help to clarify how packet headers are used to transport data to their destination.
Note: The instructions are written for PCs running Windows OS for your reference.
Step 1: Retrieve your PC’s interface addresses.
For this lab, you will need to retrieve your PC’s IPv4 address and the MAC address. (The command ifconfig for Linux and MAC OS can give you similar results.)
a. Navigate to a Command Prompt window, type ipconfig /all at the prompt.
b. Note which network adapter that the PC is using to access the network. Record your PC interface’s IPv4 address and MAC address (Physical Address).
C:\Users\Student> ipconfig /all <output omitted> Wireless LAN adapter Wireless Network Connection: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Intel(R) Centrino(R) Advanced-N 6205 Physical Address. . . . . . . . . : A4-AE-31-AD-78-4C DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::f9e7:e41d:a772:f993%11(Preferred) IPv4 Address. . . . . . . . . . . : 192.168.1.8(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Thursday, August 04, 2016 05:35:35 PM Lease Expires . . . . . . . . . . : Friday, August 05, 2016 05:35:35 PM Default Gateway . . . . . . . . . : 192.168.1.1 DHCP Server . . . . . . . . . . . : 192.168.1.1 DHCPv6 IAID . . . . . . . . . . . : 245648945 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-1B-87-BF-52-A4-4E-31-AD-78-4C DNS Servers . . . . . . . . . . . : 192.168.1.1 NetBIOS over Tcpip. . . . . . . . : Disabled
c. At the command prompt of the other PC, enter the command ipconfig.
Record the IPv4 addresses of the default gateway and the other PCs on the LAN.
Answers will vary. In this example, the default gateway is 192.168.1.1 and the IPv4 address for this PC is 192.168.1.8.
Note: If you are using a mobile device to ping request reply, search for the directions to find the IP address and Wi-Fi MAC address for your mobile device.
Note: If you only have one device, the IP address of the other PC can be the default gateway.
Step 2: Start Wireshark and begin capturing data.
a. On your PC, start Wireshark.
Note: Alternatively, your installation of Wireshark may also provide a Wireshark Legacy option. This displays Wireshark in the older but widely recognized GUI. The remainder of this lab was completed using the newer GUI.
b. After Wireshark starts, select the network interface that you identified with the ipconfig command. Enter arp in the filter box. This selection configures Wireshark to only display packets that are part of the ARP exchanges between the devices on the local network. Right-click the interface and click Start capture to begin the data capture.
Information will start scrolling down the top section in Wireshark. Each line represents a message being sent between a source and destination device on the network.
c. In a Command Prompt window, ping the default gateway to test the connectivity to the default gateway address that was identified in the previous step. (For Linux and MAC OS, use the command ping -c 4 192.168.1.1 in this example.)
C:\Users\Student> ping 192.168.1.1
Pinging 192.168.1.1 with 32 bytes of data:
Reply from 192.168.1.1: bytes=32 time=7ms TTL=64
Reply from 192.168.1.1: bytes=32 time=2ms TTL=64
Reply from 192.168.1.1: bytes=32 time=1ms TTL=64
Reply from 192.168.1.1: bytes=32 time=6ms TTL=64
Ping statistics for 192.168.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 7ms, Average = 4ms
d. Ping the IPv4 addresses of other PCs or mobile devices on the LAN that you recorded in the previous step.
Note: If your other device does not reply to your pings, the firewall may be blocking these requests. Search for unblock firewall for your operating system on the internet.
e. Stop capturing data by clicking Stop Capture (red square icon) on the toolbar.
Step 3: Examine the captured data.
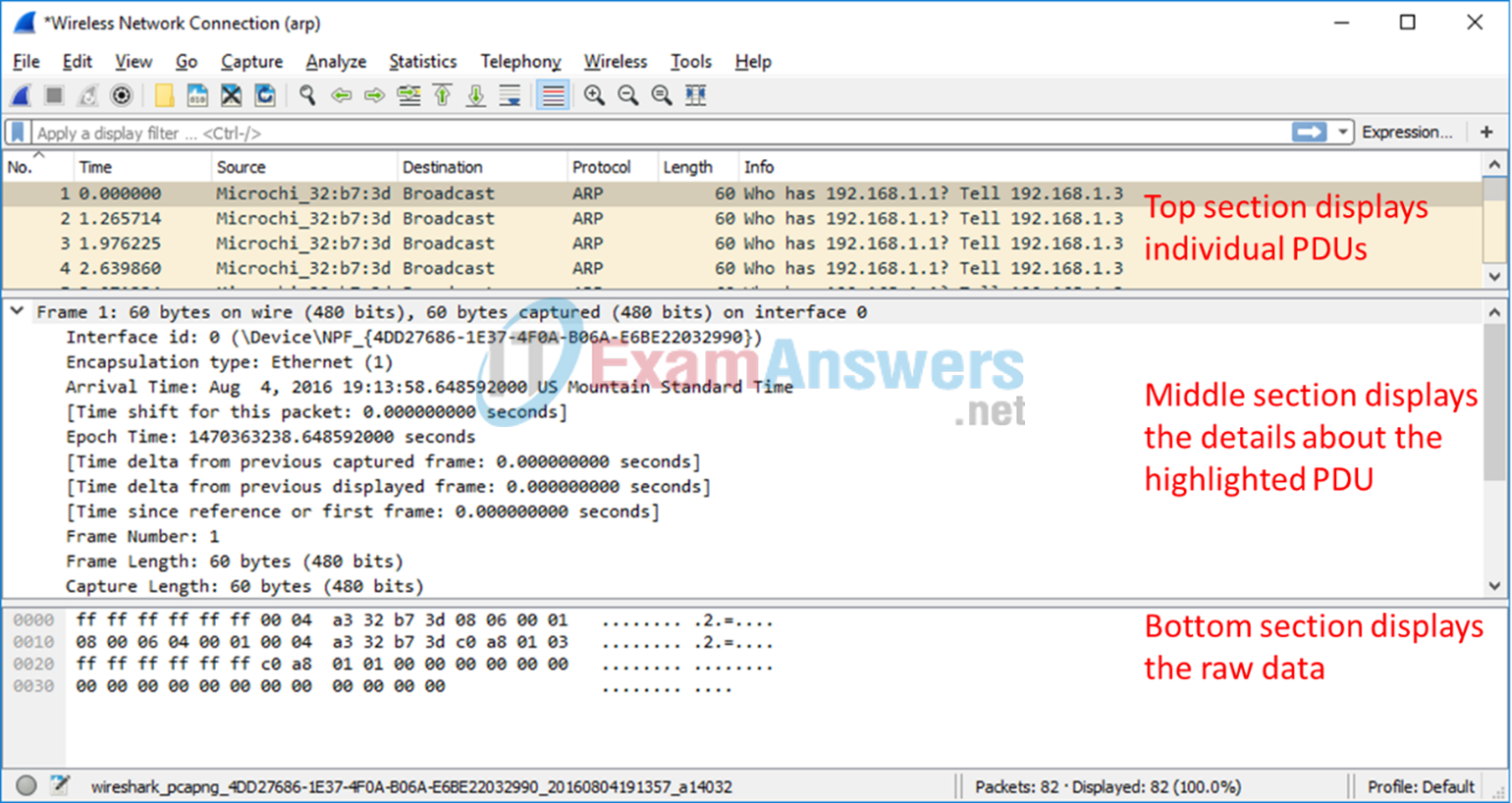
In this step, examine the data that was generated by the ping requests of your team member’s PC. Wireshark data is displayed in three sections:
1) The top section displays the list of PDU frames captured with a summary of the IPv4 packet information listed.
2) The middle section lists PDU information for the frame selected in the top part of the screen and separates a captured PDU frame by its protocol layers.
3) The bottom section displays the raw data of each layer. The raw data is displayed in both hexadecimal and decimal form.
b. Click one of the ARP frames in the top section that has your PC MAC address as the source address in the frame and “broadcast” as the destination of the frame.
c. With this PDU frame still selected in the top section, navigate to the middle section. Click the arrow to the left of the Ethernet II row to view the Destination and Source MAC addresses.
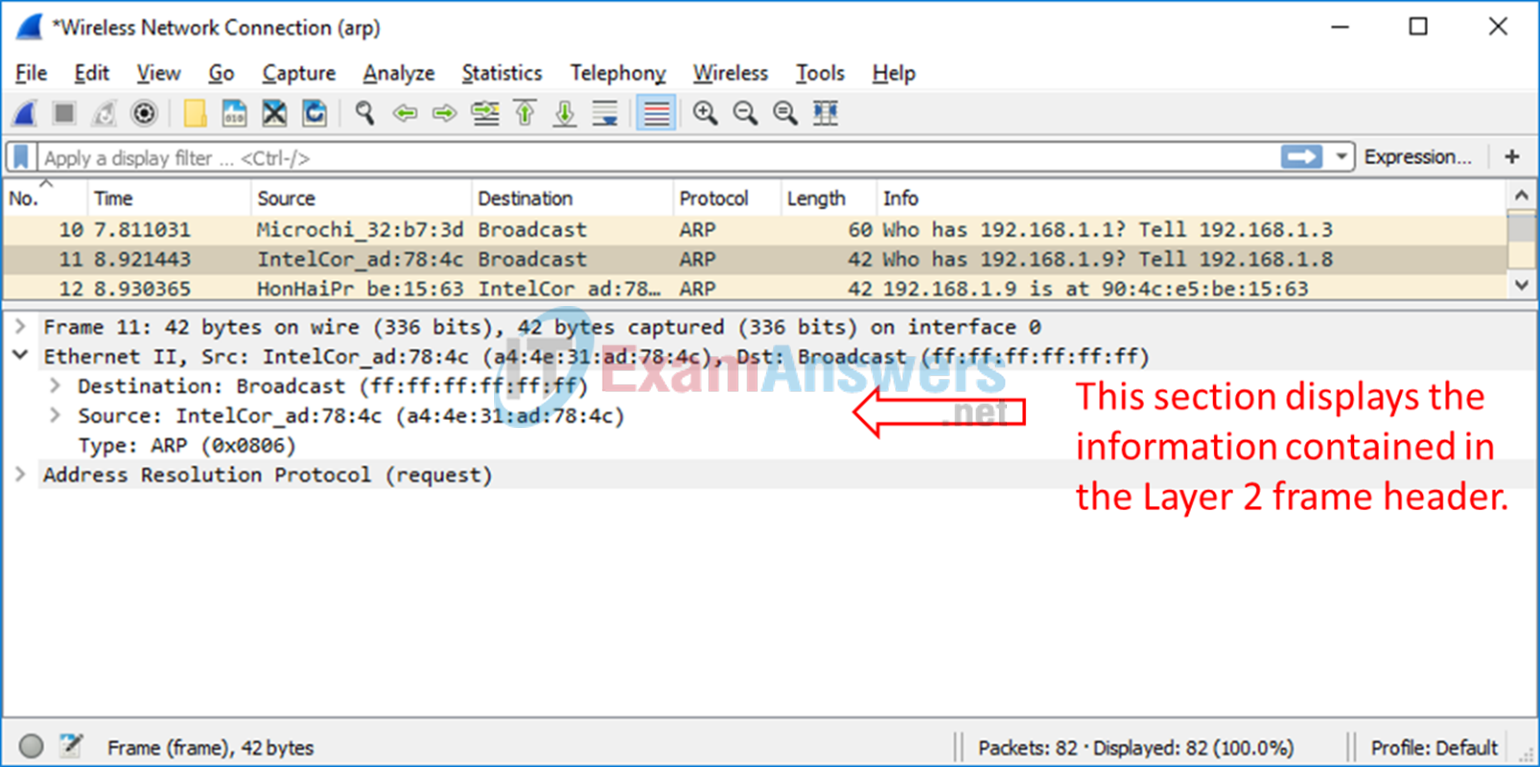
Does the Source MAC address match your PC’s interface?
Yes.
d. Click the arrow to the left of the Address Resolution Protocol (request) row to view the content of the ARP request.
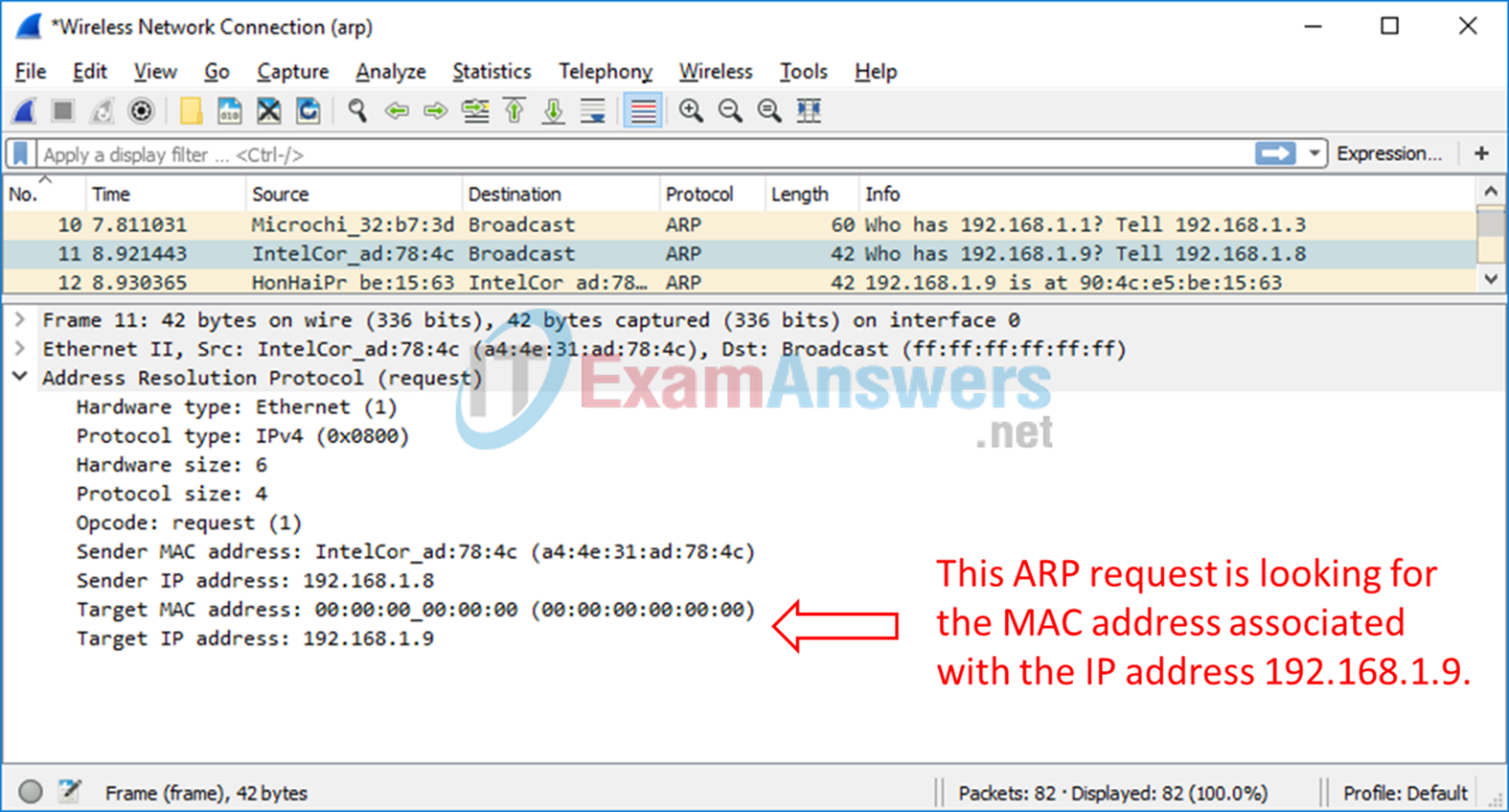
Step 4: Locate the ARP response frame that corresponds to the ARP request that you highlighted.
a. Using the Target IPv4 address in the ARP request, locate the ARP response frame in the upper section of the Wireshark capture screen.
What is the IPv4 address of the Target device in your ARP request?
Answers will vary but is 192.168.1.9 in this example.
b. Highlight the response frame in the upper section of the Wireshark output. You may have to scroll the window to find the response frame that matches the Target IPv4 address identified in the previous step. Expand the Ethernet II and Address Resolution Protocol (response) rows in the middle section of the screen.
Is the ARP response frame a broadcast frame?
No.
What is the destination MAC address of the frame?
Answers will vary but the destination MAC address would be a4:4e:31:ad:78:4c in this example.
Is this the MAC address of your PC?
Yes.
What MAC address is the source of the frame?
The device that is replying to the ping request.
c. Verify that MAC address matches the MAC address of the device that you have selected for reply to ping requests.
Part 2: Examine the ARP cache entries on the PC.
After the ARP reply is received by the PC, the MAC Address to IPv4 address association is stored in cache memory on the PC. These entries will stay in memory for a short period of time (from 15 to 45 seconds), then, if they are not used within that time, they will be removed from cache. (Note: Search on the internet to find the ARP related commands for a PC running Linux or MAC operating system.)
a. Open a command prompt window on the PC. At the prompt, enter arp –a and press enter.
C:\Users\Student> arp -a Interface: 192.168.1.8 --- 0xb Internet Address Physical Address Type 192.168.1.1 00-37-73-ea-b1-7a dynamic 192.168.1.9 90-4c-e5-be-15-63 dynamic 192.168.1.13 a4-4e-31-ad-78-4c dynamic 224.0.0.5 01-00-5e-00-00-05 static 224.0.0.6 01-00-5e-00-00-06 static 224.0.0.22 01-00-5e-00-00-16 static 224.0.0.252 01-00-5e-00-00-fc static 224.0.0.253 01-00-5e-00-00-fd static 239.255.255.250 01-00-5e-7f-ff-fa static 255.255.255.255 ff-ff-ff-ff-ff-ff static
The output of the arp –a command displays the entries that are in the cache on the PC. In the example, the PC has entries for the default gateway (192.168.1.1) and for two PCs that are located on the same LAN (192.168.1.9 and 192.168.1.13).
What is the result of executing the arp –a command on your PC?
The command lists the known MAC to IPv4 address bindings.
b. The arp command on the Windows PC has another functionality. Enter arp /? at the command prompt and press enter. The arp command options enable you to view, add and remove ARP table entries if necessary.
Which option deletes an entry from the ARP cache?
arp -d
c. What would be the result of issuing the arp –d * command?
It would delete the current address bindings in the ARP cache. This command requires administrative privileges in Windows 10.
Reflection
1. What is a benefit of keeping ARP cache entries in memory on the source computer?
Your computer always checks its local cache before requesting information from other devices on the network. The ARP cache retains dynamically learned address bindings for a short period of time. When traffic is exchanged often between source and destination, the ARP cache prevents the host from needlessly broadcasting ARP requests.
2. If the destination IPv4 address is not located on the same network as the source host, what MAC address will be used as the destination target MAC address in the frame?
The computer will use the MAC address of the default gateway.
