Time limit: 0
Quiz-summary
0 of 23 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
Information
Networking Devices and Initial Configuration Module 10 - 12 Checkpoint Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 23 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- Answered
- Review
-
Question 1 of 23
1. Question
1 pointsWhich Cisco IOS mode displays a prompt of Router#?Correct
Incorrect
Hint
Cisco IOS uses different command modes for operational needs. The privileged EXEC mode is identified by a prompt that ends with the # symbol after the device name. The user EXEC mode is identified by a prompt that ends with the > symbol after the device name. The global configuration mode is identified by a prompt that ends with (config)# after the device name. -
Question 2 of 23
2. Question
1 pointsRefer to the exhibit. An administrator is trying to configure the switch but receives the error message that is displayed in the exhibit. What is the problem? Correct
Correct
Incorrect
Hint
In order to enter global configuration mode, the command configure terminal, or a shortened version such as config t, must be entered from privileged EXEC mode. In this scenario the administrator is in user EXEC mode, as indicated by the > symbol after the hostname. The administrator would need to use the enable command to move into privileged EXEC mode before entering the configure terminal command. -
Question 3 of 23
3. Question
1 pointsWhich switch command would a network administrator use to determine if there are encapsulation or media errors on an interface?Correct
Incorrect
Hint
The show interfaces command is useful to detect media errors, to see if packets are being sent and received, and to determine if any runts, giants, CRCs, interface resets, or other errors have occurred. The show ip interface command is useful in seeing whether the interface is “up and up”. The output of the show line command displays parameters for active lines that are in use such as the vty line used for Telnet. The show arp command shows the contents of the Address Resolution Protocol (ARP) table. -
Question 4 of 23
4. Question
1 pointsTo save time, IOS commands may be partially entered and then completed by typing which key or key combination?Correct
Incorrect
Hint
The IOS CLI provides hot keys and shortcuts that make configuring, monitoring, and troubleshooting easier. Some keys or key combinations shift between characters and entire commands. The tab key is used to complete a command that has been partially entered into the command line. -
Question 5 of 23
5. Question
1 pointsAn administrator uses the Ctrl-Shift-6 key combination on a switch after issuing the ping command. What is the purpose of using these keystrokes?Correct
Incorrect
Hint
To interrupt an IOS process such as ping or traceroute, a user enters the Ctrl-Shift-6 key combination. Tab completes the remainder of parameters or arguments within a command. To exit from configuration mode to privileged mode use the Ctrl-Z keystroke. CTRL-R will redisplay the line just typed, thus making it easier for the user to press Enter and reissue the ping command. -
Question 6 of 23
6. Question
1 pointsRefer to the exhibit. Which element of IOS syntax is the expression MainOffice? Correct
Correct
Incorrect
Hint
An argument of a CLI command is generally not a predefined word, but rather is a value defined by the user. Keywords, however, describe specific parameters of a command that are predefined words that are known to the command interpreter. -
Question 7 of 23
7. Question
1 pointsWhat does the letter C mean next to an entry in the output of the show ip route command?Correct
Incorrect
Hint
In a routing table, the label C identifies a network that is directly connected to an interface on the device. This entry is added to the routing table when an interface is configured with an IP address and activated. -
Question 8 of 23
8. Question
1 pointsWhich interface is the default SVI on a Cisco switch?Correct
Incorrect
Hint
An SVI is a virtual interface and VLAN 1 is enabled by default on Cisco switches. VLAN 99 must be configured to be used. FastEthernet 0/1 and GigabitEthernet 0/1 are physical interfaces. -
Question 9 of 23
9. Question
1 pointsA network administrator enters the service password-encryption command into the configuration mode of a router. What does this command accomplish?Correct
Incorrect
Hint
The startup-config and running-config files display most passwords in plaintext. Use the service password-encryption global config command to encrypt all plaintext passwords in these files. -
Question 10 of 23
10. Question
1 pointsRefer to the exhibit. A network technician is statically assigning an IP address to a PC. The default gateway is correct. What would be a valid IP address to assign to the host?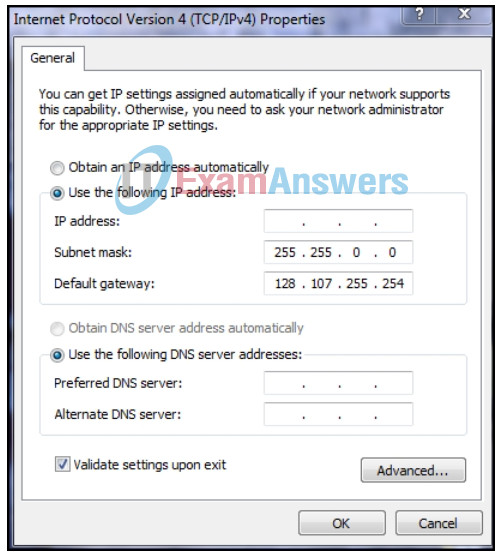 Correct
Correct
Incorrect
Hint
In data communication, the default gateway device is involved only when a host needs to communicate with other hosts on another network. The default gateway address identifies a network device used by hosts to communicate with devices on remote networks. The IP address of the host and the default gateway address must be in the same network. With the default subnet mask, valid host IP addresses range from 128.107.0.1 to 128.107.255.254. -
Question 11 of 23
11. Question
1 pointsWhen configuring SSH on a router to implement secure network management, a network engineer has issued the login local and transport input ssh line vty commands. What three additional configuration actions have to be performed to complete the SSH configuration? (Choose three.)Correct
Incorrect
Hint
SSH is automatically enabled after the RSA keys are generated. Setting user privilege levels and configuring role-based CLI access are good security practices but are not a requirement of implementing SSH. -
Question 12 of 23
12. Question
1 pointsMatch the command with the device mode at which the command is entered.Correct
Incorrect
Hint
Place the options in the following order:service password-encryption R1(config)# enable R1> copy running-config startup-config R1# login R1(config-line)# ip address 192.168.4.4 255.255.255.0 R1(config-if)# -
Question 13 of 23
13. Question
1 pointsPasswords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)Correct
Incorrect
Hint
Access to the VTY and console interfaces can be restricted using passwords. Out-of-band management of the router can be restricted in both user EXEC and privileged EXEC modes. -
Question 14 of 23
14. Question
1 pointsMatch the type of password on a Cisco device to the function.Correct
Incorrect
Hint
Place the options in the following order:enable password limits access to the privileged EXEC mode vty password limits access to the device through an SSH connection console password limits access to the device through an out-of-band connection enable secret encrypted and restricts access to the privileged EXEC mode -
Question 15 of 23
15. Question
1 pointsWhat is the purpose of ICMP messages?Correct
Incorrect
Hint
The purpose of ICMP messages is to provide feedback about issues that are related to the processing of IP packets. -
Question 16 of 23
16. Question
1 pointsOpen the PT Activity. Perform the tasks in the activity instructions and then answer the question. What are the three IPv6 addresses displayed when the route from PC1 to PC2 is traced? (Choose three.)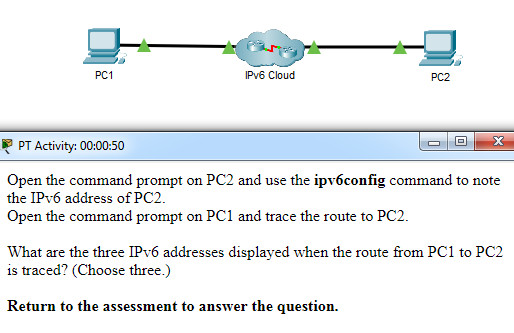 Correct
Correct
Incorrect
Hint
Using the ipv6config command on PC2 displays the IPv6 address of PC2, which is 2001:DB8:1:4::A. The IPV6 link-local address, FE80::260:70FF:FE34:6930, is not used in route tracing. Using the tracert 2001:DB8:1:4::A command on PC1 displays four addresses: 2001:DB8:1:1::1, 2001:DB8:1:2::1 , 2001:DB8:1:3::2, and 2001:DB8:1:4::A. -
Question 17 of 23
17. Question
1 pointsA user calls to report that a PC cannot access the internet. The network technician asks the user to issue the command ping 127.0.0.1 in a command prompt window. The user reports that the result is four positive replies. What conclusion can be drawn based on this connectivity test?Correct
Incorrect
Hint
The ping 127.0.0.1 command is used to verify that the TCP/IP stack is functional. It verifies the proper operation of the protocol stack from the network layer to physical layer, without sending a signal on the media. That is, this test does not go beyond the PC itself. For example, it does not detect whether a cable is connected to the PC or not. -
Question 18 of 23
18. Question
1 pointsWhich utility uses the Internet Control Messaging Protocol (ICMP)?Correct
Incorrect
Hint
ICMP is used by network devices to send error messages. -
Question 19 of 23
19. Question
1 pointsA user issues a ping 198.51.100.5 command and receives a response that includes a code of 3. What does this code represent?Correct
Incorrect
Hint
When a host or gateway receives a packet that it cannot deliver, it can use an ICMP Destination Unreachable message to notify the source that the destination or service is unreachable. The message will include a code that indicates why the packet could not be delivered. These are some of the Destination Unreachable codes for ICMPv4: 0 : net unreachable 1 : host unreachable 2 : protocol unreachable 3 : port unreachable -
Question 20 of 23
20. Question
1 pointsWhich ICMPv6 message is sent when the IPv6 hop limit field of a packet is decremented to zero and the packet cannot be forwarded?Correct
Incorrect
Hint
ICMPv6 uses the hop limit field in the IPv6 packet header to determine if the packet has expired. If the hop limit field has reached zero, a router will send a time exceeded message back towards the source indicating that the router cannot forward the packet. -
Question 21 of 23
21. Question
1 pointsWhich command can be used to verify connectivity between two host devices?Correct
Incorrect
Hint
The ping command can be used to test end-to-end connectivity between two host devices. It measures the round-trip time for a message to get from source to destination. -
Question 22 of 23
22. Question
1 pointsA network administrator establishes a connection to a switch via SSH. What characteristic uniquely describes the SSH connection?Correct
Incorrect
Hint
SSH provides a secure remote login through a virtual interface. SSH provides a stronger password authentication than Telnet. SSH also encrypts the data during the session. -
Question 23 of 23
23. Question
1 pointsWhich ICMP message is used by the traceroute utility during the process of finding the path between two end hosts?Correct
Incorrect
Hint
Traceroute progressively increments the TTL (IPv4) or hop limit (IPv6) field (1, 2, 3, 4…) for sending sequence of ping commands. When a router senses that the TTL or hop limit is 0, it will discard the packet and send a time exceeded message to the source of the traceroute. The returned message contains the IP address of the router that discarded the packet. Hence the traceroute utility learns the address of the router. This process continues and provides the trace with the address of each hop (router) as the packets continue traveling through routers to reach the destination.
